Micro-segmentation of networks in examples: how this cleverly twisted thing reacts to different attacks

Previously, when it was necessary to differentiate something (for example, servers with payment processing and terminals of office users), they simply built two independent networks with a firewall bridge in the middle. It is simple, reliable, but expensive and not always convenient.
Later, other types of segmentation appeared, in particular, rights based on a transaction card. In parallel, role schemes developed, where a machine, person, or service is assigned its specific rights. The next logical round is micro-segmentation in virtual infrastructures, when DMZ is placed around each machine.
In Russia, there are still few implementations of such defensive constructions, but soon there will definitely be more of them. And then we, perhaps, will not even understand how it was possible to live without it. Let's look at the attack scenarios for such a network and how it reacts to it.
What is microsegmentation
Microsegmentation is a security method that allows you to assign security policies to data center applications down to the level of workload. In a more applied application, it is a data center security model. Network security policies are enforced by firewalls integrated into hypervisors that are already present in the data center. This provides ubiquitous protection. In addition, security policies can be conveniently changed, including automatically, and dynamically adapted to suit changing workloads.
As it was before
Here is the “stone age" of modern networks - unmanaged networks:
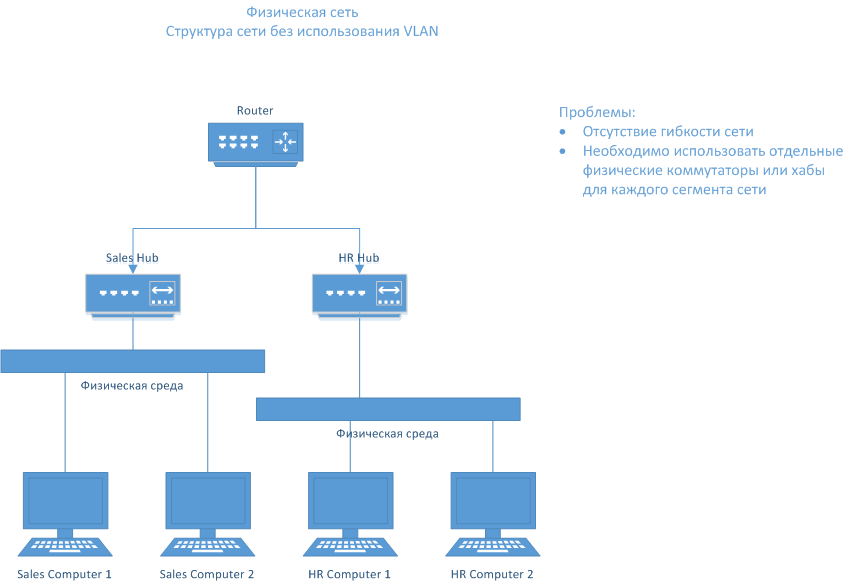
More precisely, it would be a stone age if the networks were generally physically separated by the absence of links. But here they are connected by a router and protected by hardware firewalls at the intersection. This is a good option exactly as long as you do not get into the real world.
Here's the next round of security evolution:
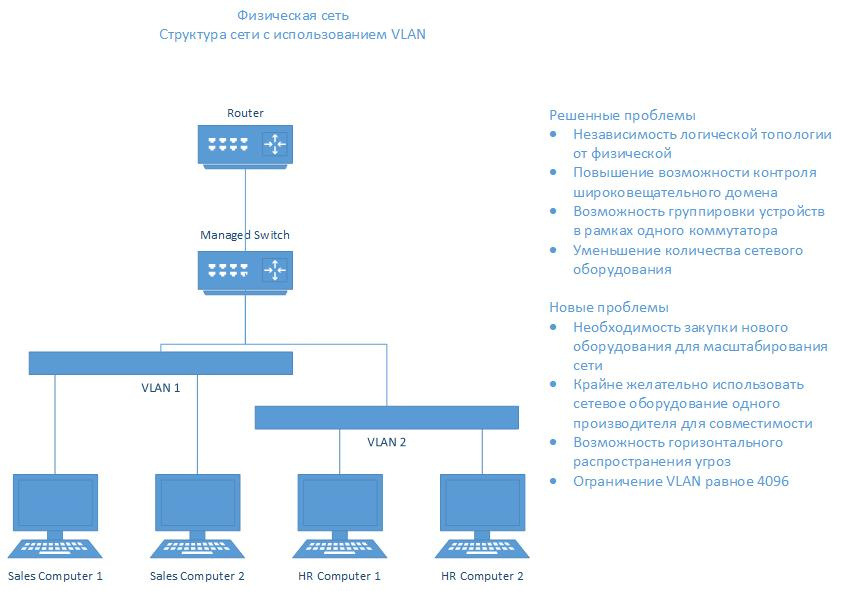
Today, most companies use server clusters to twist their infrastructure as a whole. Here is an example of Aeroexpress- there, in fact, one cluster and two virtual subnets - for sales offices (ordinary users) and for banking, that is, ticket calculations. Before the introduction, there was only one network, and in theory, the cashier could banally feed the server with the issuance of tickets. The next logical step after this separation is even greater virtualization and the construction of microsegments, but not at the iron level, but at the level of flexible services rights. This greatly simplifies administration compared to the classic task of fine-grained separation of 2-3 machines and greatly simplifies life in terms of reliability of protection in the cluster. Each microsegment looks at the neighboring one as an outside world, and not as a deliberately trusted one.
This is one of the simplest schemes where, depending on the tasks, intersections of different perimeters are used. This may look like the diagram below.
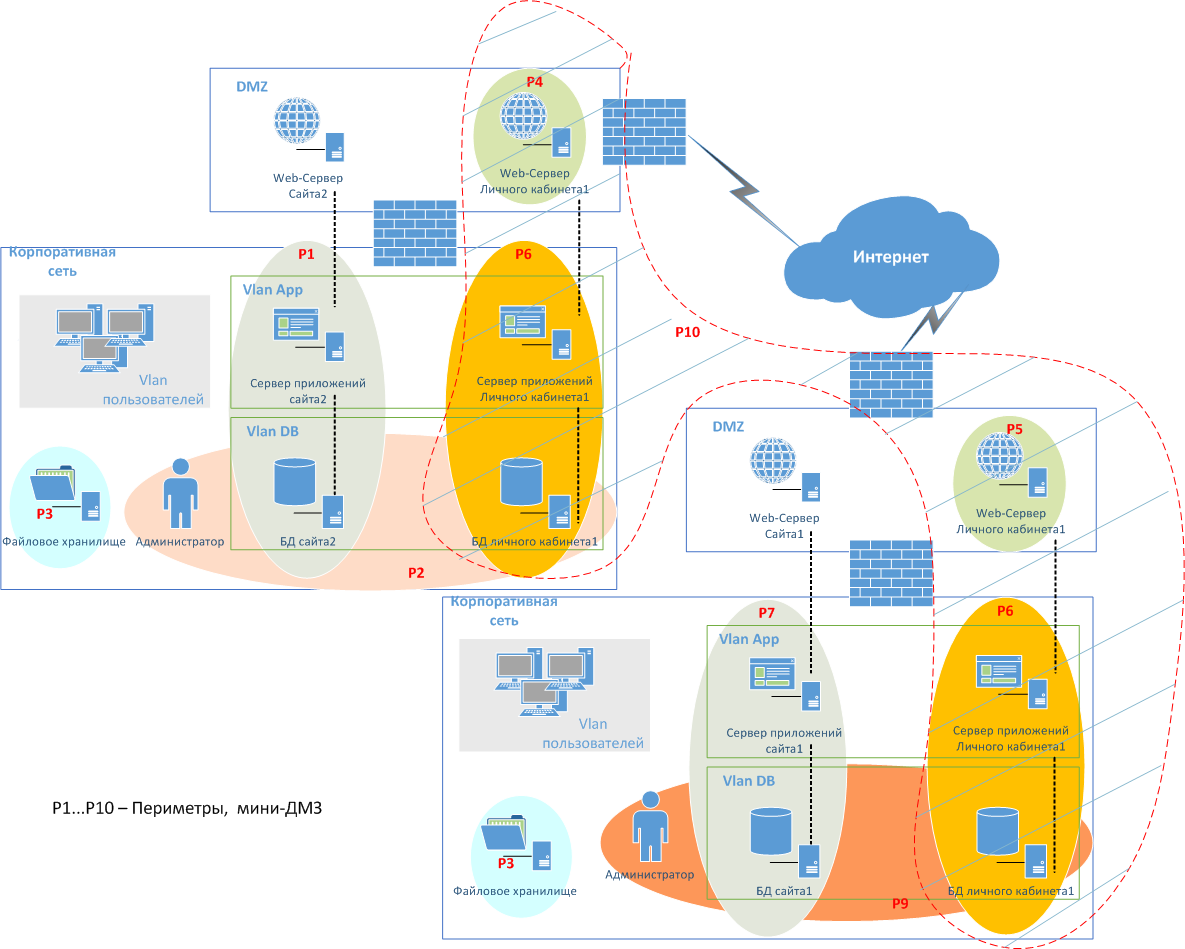
In this diagram, as you see, the solved problems of scaling network components (performed by deploying new VMs), it is possible to use any network equipment, it is possible to control the horizontal distribution of VM traffic, VLANs are replaced by VxLANs, the limit of which is about 16 million interfaces. Moreover, if you look at the color scheme of the scheme, using the example of My Account - 1, you can see the following scenarios:
- Application servers located on different physical sites are located in the same logical network P6 (orange ovals);
- Moreover, the Web servers of the same Personal Account - 1 are already in different logical networks (green ovals P4 and P5);
- All servers implementing the Personal Account - 1, in turn, are located in a single logical network P10 (a zone marked with a dashed line).
Perhaps you already understood everything and now want to find out how difficult it is to maintain. So, in new versions of hypervisors such structures are supported “out of the box”.
The main theme of such microsegmentation implementations is the protection of critical services in the context of cluster and personal cloud technologies.
Example: There is an accountant’s working machine, on which, during normal daily work, policies like “Workstation of Accountancy” are applied, under which you can access the Internet and to general infrastructure services. When a client-bank is launched, politicians will immediately take priority to process the rules associated with the bank-client’s traffic, and its traffic will be transmitted only to the bank’s IP / DNS server, and it is mandatory to pass such traffic through additional means of information protection (for example, DPI server). The client bank is closed - it becomes "AWP Accounting" again.
What does one of the NSX microsegmentation platforms consist of?
Here are the main components:
Commutation | Layer 2 logical overlay is provided across the entire Layer 3 switched fabric inside and outside the data center. VXLAN-based overlay support. |
Routing | Dynamic routing between virtual networks is performed by the kernel of the hypervisor in a distributed manner; horizontal scaling is supported with failover of the active-active type to physical routers. Static and dynamic routing protocols (OSPF, BGP) are supported. |
Distributed firewall | Stateful distributed firewall services built into the core of the hypervisor with a throughput of up to 20 Gb / s to the hypervisor server. Active Directory support and action monitoring. In addition, NSX provides a vertical firewall with NSX Edge. |
Load balancing | Load balancing for layers |
VPN | Remote access via VPN and a medium-to-medium VPN connection, an unmanaged VPN for cloud gateway services. |
NSX Gateway | Bridging between VXLANs and VLANs provides optimal connectivity to physical workloads. This component is built into the NSX platform and is also supported by rack switches provided by ecosystem partners. |
NSX API | REST-based APIs are supported for integration with any cloud management or user platform |
And now we consider the scenarios of various threatening events, so that it becomes completely clear.
Scenario 1: Malwara
The routes of entry and infection in large companies are approximately the same: phishing, targeted attacks, “travel apples” in the form of thrown flash drives. As a rule, a malware infects one of the automated workstations (for example, when it comes with a letter), and then inside the perimeter it can do anything until it is detected. Recently I saw a situation in a bank. I must say that they have serious people and serious security, but the situation inside the network was such that a deployed test malware (without payload) “broke through” the test environment and infected several branches until it was seen by the protection system. For some, the user segment is not separated from the critical one at all, and users happily hang malware on 1C servers, on machines with financial transactions, on web servers, update servers, and so on.
In our paradigm, protection is as follows: micro-segmentation at the level of servers, services, and users. Separate each group with perimeters (as in the picture above). As a rule, one virtual machine is infected, which is detected by an antivirus running from the height of the hypervisor. A machine with atypical activity will immediately be automatically quarantined - a special segment where all those who do something not quite ordinary fall into.
Standard measures can be fastened to this, for example, a typical sandbox.
Modern malware calms down on a single workstation, sends a very small signal to the management server, or deploys the second block, which already carries a “useful” load. In which case, it is the second generation of the malware that is detected - the first "silent" remains in the system. The antivirus may detect and kill even both blocks if you are lucky, but most likely it will happen at the edge of the networks, and after that you will have to do a lot of work to track the damage. And the integration of antivirus itself without a hypervisor level is somewhat more complicated.
On March 17, 2017, Kaspersky updated Agentless Protection for NSX.
Scenario 2: targeted attack on a critical service
The attack on especially critical computers and servers (bookkeeping, machines with access to SWIFT, processing servers) most often begins as DDoS, and continues to be carried by the malware “silently”. It is solved simply: one more (two, three, as needed) DMZ is created inside your server group for a complete cut-off. Of course, we must think about this in advance.
A normal administrator, of course, has separate networks, it’s more difficult to maintain it without holes for many years. Well, without centralization. And when transferring a network or virtual machine, holes may appear, and in the case of micro-segmentation, the probability is much less.
Scenario 3: random incorrect migration or simplified network initialization
Only a third of data loss is associated with the actions of attackers. The rest is a banal oversight or just idiocy. A vivid example is the very often occurring changes in the network, for example, the migration of a machine or a group of machines from one subnet to another (from a more secure to a less secure one, which makes the migrated machine “naked” in front of threats).
The solution is micro-segmentation and profile assignment to a machine or group of machines. Thus, the security settings and all the necessary firewalls (implemented by the hypervisor) will remain on the VM, regardless of how and where it migrates.
My favorite example is that in one retail chain the risks were incorrectly assessed. Ticket offices migrated to the user zone (more precisely, user rights changed after six months). Someone forgot something during the next patch - and they were put out with a naked database out.
Scenario 4: particularly successful pentest
This is really a separate scenario, because for such jambs it is very painful to beat hands. Especially in the financial sector. I saw a very simple story: a bank ordered penetration of a specific VM group (in a test environment). Pentesters took the flag, but got a little carried away, picked a test environment, went into the main segment and put the ABS server on for a day. This is just a paragraph!
In general, microsegmentation helps to make sure that networks do not “physically” see each other, as if they were not connected at all. They still won’t get to the level of the hypervisor (well, at least without a world-class 0-day). If suddenly something gets admin rights and spreads, the hypervisor will catch it. And virtual machines are much easier to roll back.
Scenario 5: attack on an outward looking service leading to internal network problems
There is a web server in retail. There is a front and open ports between the front and the web.
They brought him up, and at the same time, the checkout line also went down. Admin is looking for a new job the very next day. In general, the essence of the attack is that an attacker exploits the vulnerability of an application server or a web server accessible from the Internet and gains access to critical servers and databases inside the corporate infrastructure. Well, or just puts everything inside the didosomes.
The paradigm assumes micro-segmentation of each service server in such a way that for each server that performs its role, there will be certain security settings. Configurable using profiles.
Other scenarios
In general, other scenarios are being worked out in approximately the same way. For example, from our point of view, an insider is just an infected AWP. And it doesn’t matter if he acts, or if he just got an account. Atypical activity - quarantine - proceedings and subsequent rollback of the affected VM.
How to go
Let's talk about one of the practical cases:
- Conducted a survey. The survey recorded network topology, virtual infrastructure architecture, types of deployed systems and services. At this stage, all information flows (user, service, management traffic, monitoring and update traffic) are determined and recorded.
- The analysis and design of changes to the virtual infrastructure, including the network, is carried out taking into account the criticality groups and provided functions identified at the stage of the survey.
- The initial configuration of profiles (VM groups, roles, security settings, ITU settings, user group access settings) for the VM test group is performed.
- The generated profiles are applied, the work is monitored. If necessary, adjustments are made. The “zero-trust” model is in place when implementing micro-segmentation. With this model, we initially do not trust anything, but allow only verified and trusted interaction.
- The solution scales to the entire infrastructure.
Further, the entire infrastructure is maintained and managed centrally from a single console with a minimum number of personnel involved. Groups and profiles are formed, their purpose is fast enough. Assigned profiles work everywhere within the same virtual infrastructure. In addition to managing ITU and security settings, the processes of migration, updating, commissioning and decommissioning of servers and services are also centrally managed.
Important points specifically for the NSX solution mentioned:
- Need to replace the Cisco ASA 5520 Firewall.
- The ability to split the data center into separate segments, regardless of subnet and VLAN.
- Apply the policy to the VM in accordance with the OS and its name.
- Support for IPsec solution for communication with remote branches.
There was such a network:
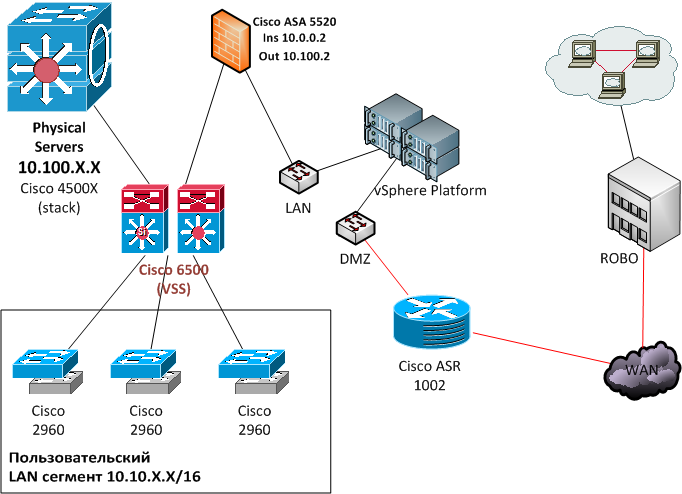
Before the implementation, we conducted an audit to understand how the traffic in the virtual data center “walks” using the VMware vRealize Network Insight utility. It just helps to set up microsegmentation rules. It turns out something like this:
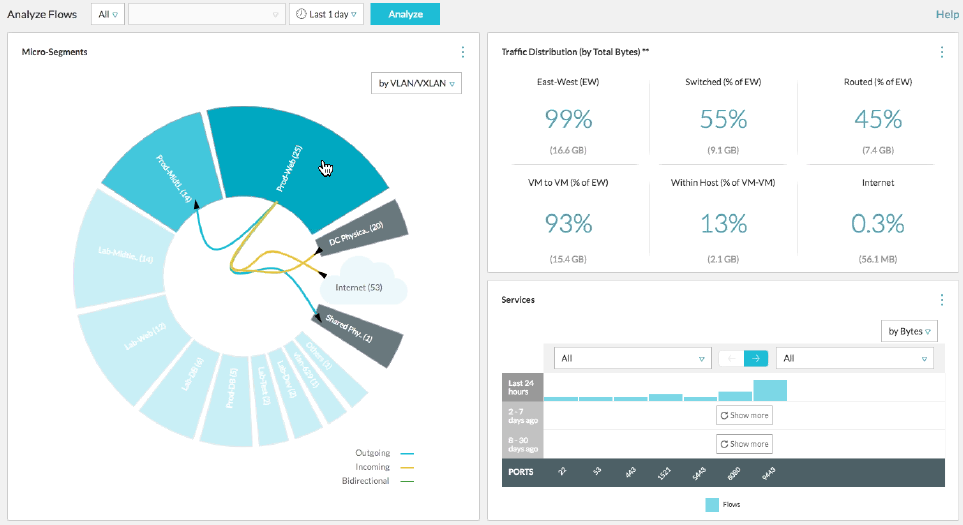
Source
And compared the parameters of interest to the customer (so, one of the tasks was replacing the VPN):
Cisco ASA 5520 | Cisco ASA | Cisco ASA 1000V | Cisco ASA | VMware NSX Edge | |
A type | Physical device | Physical device | Virtual machine | Physical device | Virtual machine |
Maximum Firewall Throughput (Max.) | 0.4 Gbps | 1.2 Gbps | 1.2 Gbps | 4 Gbps | 9 Gbps |
Maximum concurrent sessions | 280,000 | 245,000 | 200,000 | 1,000,000 | 1,000,000 |
Maximum connections per second | N / a | 6000 | 10,000 | 50,000 | 131,000 |
VPN bandwidth | 250 Mbps | 250 Mbps | 200 Mbps | 700 Mbps | 2 gbps |
Maximum IPsec Tunnels | 750 | 250 | 750 | 5,000 | 6,000 |
Maximum SSL Tunnels | 750 | 250 | 750 | 5,000 | 6,000 |
In parallel, we built a network diagram of physical equipment. The key for us is to understand the movement of traffic within the data center to configure policies. It was removed, applicable immediately. If something will be cut - just add later. A week or two is enough to build a good map and determine all the services.
We had a fairly simple installation, and we placed it on 2 blades. Expenses:
Component | Qty | ∑ RAM (GB) | ∑vCPU | ∑HDD (GB) |
NSX Manager | 1 | 16 | 4 | 60 |
NSX Controller | 3 | 12 | 12 | 60 |
NSX DLR | 2 | 4 | 8 | 3 |
NSX EDGE | 1 | 2 | 4 | 2 |
The customer already had a VMware vSphere virtualization environment, so we just bought licenses for NSX. At that time, there were no NSX editions, they appeared almost a month after the purchase of licenses. The product itself is licensed on sockets.
We divided the machines into groups and assigned tags to them, transferred the firewall rules from the ASA to the distributed firewall, and checked vRealize Network Insight again, that we correctly indicated the traffic flows and did not forget anything.
PROFIT!
References
- Official
- Integration with Kaspersky Anti-Virus Product
- A very good English article on what VMware NSX consists of and how it works.
- Likbez about not-so-well-known solutions for protecting the IT infrastructure of a business
- My mail for questions is afeoktistov@croc.ru
