WannaCry: analysis, indicators of compromise and recommendations for prevention
Last Friday, exactly at the end of the day, when all the administrators and security experts gathered around their homes and summer cottages, the world spread the news of the start of an unprecedented attack by WannaCry. After a couple of days, it can already be said that the name of this attack is associated with Keith Urban’s song “Tonight I Wanna Cry” (“Today I Want to Cry”). Its scope turned out to be quite ominous - at the time of writing, the number of victims exceeded 230 thousand, and this number can grow when many return from weekends and holidays and turn on their home and work computers. We, in our Cisco Talos division, published our research on this malicious program on Friday and would like to share some key points with Habr users.

WannyCry is a cryptographic worm, a distinctive feature of which is the self-propagation function, which is usually absent in classic cryptographers. This means that for infection you do not need to click anywhere, press nothing and open nothing. It is enough to have just a vulnerable, unpatched and connected to the Internet (including through other computers, for example, on the local network) computer based on the Windows platform to become a victim of WannaCry. After the computer is infected, the victim sees an offer to pay a certain amount of money (different variations of WannaCry require different amounts - from 300 to 600 dollars) for returning access to files. The offer is displayed in different languages, including Russian. An interesting point - the ransom message is not just a text file, picture or HTA file, as is usually the case with encryptors, but an executable file.
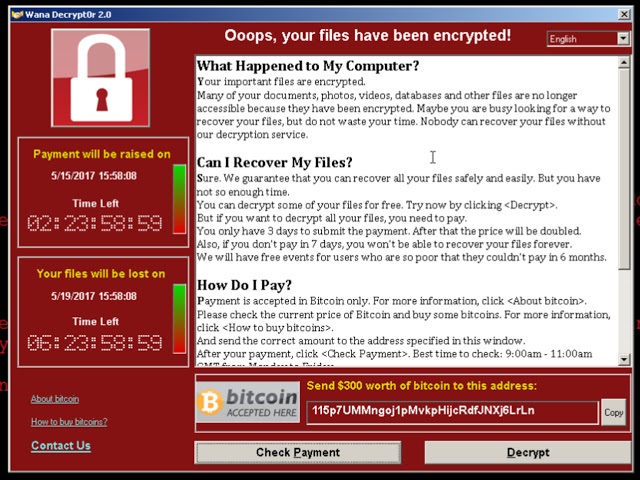
Pay attention to this point - no response is required from the user ! What made this possible? Everything is simple here - the authors of WannaCry took advantage of a leak from ShadowBrokers, as a result of which the world became aware of many previously unknown vulnerabilities and methods of conducting attacks. Among them was the ETERNALBLUE vulnerability and the DOUBLEPULSAR backdoor associated with it. The first allowed through a vulnerable SMB to gain remote access to a computer and quietly install software on it. And so the WannyCry ransomware is installed. Microsoft in March releasedan appropriate patch for this vulnerability, but, as experience shows, many administrators for various reasons did not bother to install it on their computers. The ETERNALBLUE vulnerability is present on all versions of Windows, excluding Windows 10. Given the large number of Windows family operating systems (Windows XP, Windows 8, Windows Server 2003) and the scale of the attack, Microsoft took an unprecedented step and released patches for these OS.
Please note that if you have the appropriate patch installed or otherwise block the use of this vulnerability, for example, using IPS), this does not mean that you are not subject to WannaCry. In this case, the ransomware will be able to be launched, but this will require a user reaction, familiar to the work of classic ransomware lockers. Installing the Microsoft patch only blocks remote infection and the spread of malicious code.
The malicious program WannaCry searches for vulnerable computers by scanning the open TCP port 445 (Server Message Block / SMB). Therefore, a good idea (if your processes allow this) would be to block access on this port (as well as on the 139th) from the Internet on your firewall or router. For Cisco routers, the appropriate ACL might look like this:
access-list 110 deny tcp any any eq 445
access-list 110 deny tcp any any eq 139
However, blocking these ports from the outside does not mean complete protection against internal infection. If any of your users brings a home laptop containing WannaCry and connects it to the internal local network (and we have already received requests from some customers whose CEOs arrived with their infected computers on weekends, calling “ carpet ”and IT staff), then WannaCry will begin to search for new victims within the organization.
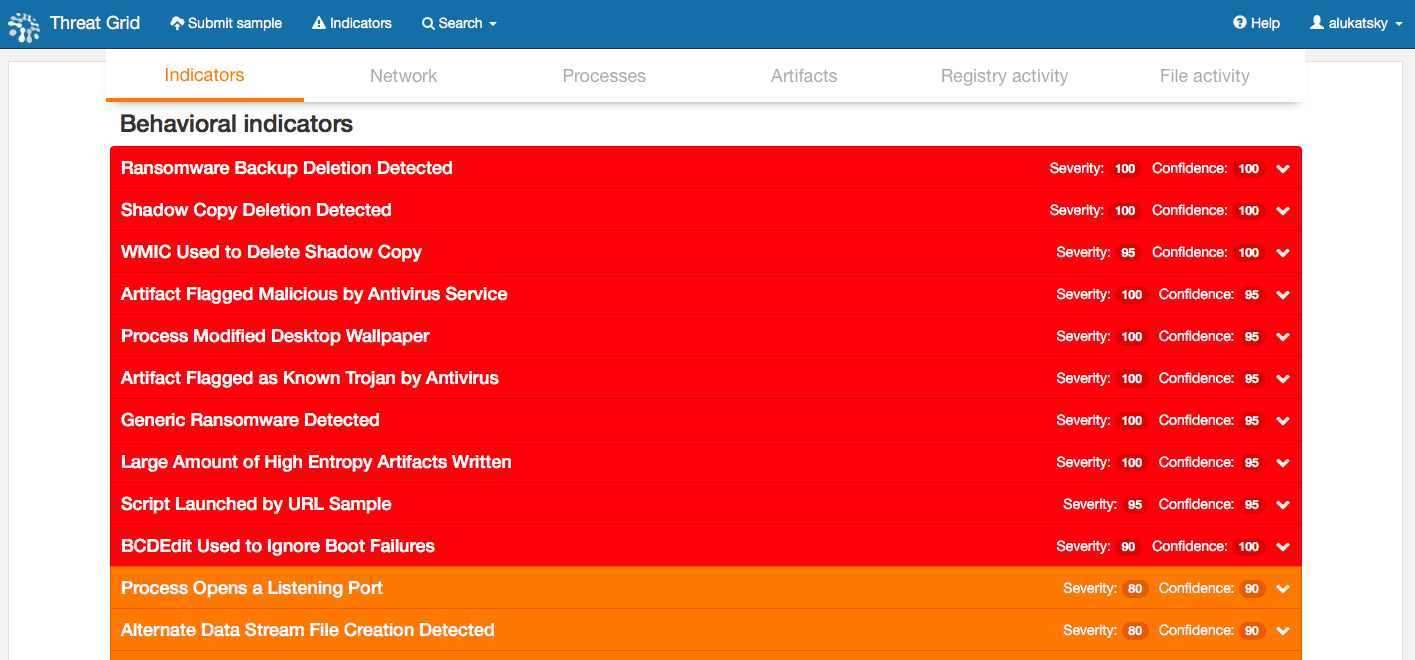
Our analysis shows that, along with the ETERNALBLUE vulnerability, the DOUBLEPULSAR backdoor from the ShadowBrokers leak also works, which allows remote access and arbitrary code execution on a previously compromised machine. Usually, after successful exploitation of the ETERNALBLUE vulnerability, the DOUBLEPULSAR backdoor is installed and the encryptor is installed with its help. If ETERNALBLUE cannot be successfully exploited, but at the same time there is a copy of DOUBLEPULSAR on the attacked node, then the encryption code is set through it.
After successfully installing and encrypting files, WannaCry tries to establish a connection with the nodes of the Tor network to transfer traffic through it and try to hide its true "hosts". The following Tor hosts IP addresses have been discovered by Cisco Talos, but this is not the final list. Our colleagues from other companies have lists of used Tor nodes that have different addresses. Moreover, their analysis shows that most of them have an old history and have already been used in certain malicious activities. In addition, it is worth remembering that the indicated addresses will not be used constantly - their lifespan for the current version of WannaCry will be several weeks. Therefore, you should regularly monitor information about this threat and update the relevant indicators of compromise.
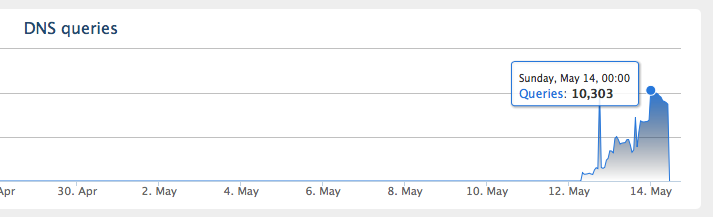
Despite the fact that only a couple of days have passed since the start of the epidemic and several hundred thousand computers have already been damaged, the attackers managed to release several new versions of their malicious creations, mainly in the part of the ransomware. The current version of WannaCry contains the “kill switch” function, that is, checking for the presence of a specific domain on the Internet, upon detection of which malicious code was not installed on the victim’s computer. This domain - iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea [.] Com (other domains are also possible in the new WannaCry modifications) was identified by one of the researchers and registered by him for “intercepting” malware control. As analysis of calls to this domain using the Cisco OpenDNS Investigate service showed, about 200 thousand computers were saved from infection over the past two days.
So far no WannaCry modifications have been discovered without the kill switch function (although attempts have been made, but so far unsuccessful), but this does not mean that it cannot be. In any case, the story is not over yet. On Monday, many will turn on their computers after holidays and weekends, and the number of victims of this malware may increase further. Moreover, our analysis shows that the architecture of WannaCry is modular and can be used to deliver and use other malicious modules.
It is worth noting that at the time of writing the note, it was not yet possible to find a way to decrypt the encrypted files. This means that if a user is infected and does not have a backup copy of his data, the probability of returning access to his files is not high (even in the case of a ransom payment, which does not guarantee that he will receive a decryption key). For encryption, a 2048-bit RSA key is used, and files with the following extensions fall under the distribution:
.der, .pfx, .key, .crt, .csr, .p12, .pem, .odt, .sxw, .stw, .3ds, .max, .3dm, .ods, .sxc, .stc, .dif .slk, .wb2, .odp, .sxd, .std, .sxm, .sqlite3, .sqlitedb, .sql, .accdb, .mdb, .dbf, .odb, .mdf, .ldf, .cpp,. pas, .asm, .cmd, .bat, .vbs, .sch, .jsp, .php, .asp, .java, .jar, .class, .mp3, .wav, .swf, .fla, .wmv, .mpg, .vob, .mpeg, .asf, .avi, .mov, .mp4, .mkv, .flv, .wma, .mid, .m3u, .m4u, .svg, .psd, .tiff, .tif .raw, .gif, .png, .bmp, .jpg, .jpeg, .iso, .backup, .zip, .rar, .tgz, .tar, .bak, .arc, .vmdk, .vdi,. sldm, .sldx, .sti, .sxi, .dwg, .pdf, .wk1, .wks, .rtf, .csv, .txt, .msg, .pst, .ppsx, .ppsm, .pps, .pot, .pptm, .pptx, .ppt, .xltm, .xltx, .xlc, .xlm, .xlt, .xlw, .xlsb, .xlsm, .xlsx, .xls, .dotm, .dot, .docm, .docx .doc
As you can see, office files Excel, Word, PowerPoint, Open Office, music and video files, archives, e-mail messages and mail archives / databases, MS SQL, MS Access database files, MS Visio, Photoshop graphic files are encrypted, as well as virtual machines and others.
Now it’s too early to put an end to the story with WannaCry and a more detailed analysis of this malicious program awaits us. In the meantime, we can give a number of recommendations for protection against it:
For those users who use Cisco cybersecurity solutions, we can say that all our solutions can deal with this threat:
Snort users should be aware that rules 42329-42332, 42340, and 41978, which are available as part of the service pack on Snort.org, help fight this threat . For users of Cisco Legacy IPS, the IPS Signature Pack S982 has been prepared, in which the 7958-0 and 7958-1 are fighting with WannaCry.
In addition, we want to specify indicators for compromise WannaCry, which we have identified as part of our analysis:
File names :
d5e0e8694ddc0548d8e6b87c83d50f4ab85c1debadb106d6a6a794c3e746f4fa b.wnry
055c7760512c98c8d51e4427227fe2a7ea3b34ee63178fe78631fa8aa6d15622 c.wnry
402751fa49e0cb68fe052cb3db87b05e71c1d950984d339940cf6b29409f2a7c r.wnry
e18fdd912dfe5b45776e68d578c3af3547886cf1353d7086c8bee037436dff4b s.wnry
Taskdl.exe 4a468603fdcb7a2eb5770705898cf9ef37aade532a7964642ecd705a74794b79
2ca2d550e603d74dedda03156023135b38da3630cb014e3d00b1263358c5f00d taskse.exe
97ebce49b14c46bebc9ec2448d00e1e397123b256e2be9eba5140688e7bc0ae6 t.wnry
b9c5d4339809e0ad9a00d4d3dd26fdf44a32819a54abf846bb9b560d81391c25 u.wnry
Observed IP-addresses :
188 166 23 127 443 - Tor Exit Node [.] [ .] [.]
193 23 244 [[.] [.] .] 244: 443 - Tor Exit Node
2 [.] 3 [.] 69 [.] 209: 9001 - Tor Exit Node
146 [.] 0 [.] 32 [.] 144: 9001 - Tor Exit Node
50 [. ] 7 [.] 161 [.] 218: 9001 - Tor Exit Node
128.31.0 [.] 39 - Tor Exit Node
213.61.66 [.] 116 - Tor Exit Node
212.47.232 [.] 237 - Tor Exit Node
81.30 .158 [.] 223 - Tor Exit Node
[.] 79.172.193 32 - the Tor the Exit the Node
the Tor C2 :
xxlvbrloxvriy2c5.onion
cwwnhwhlz52maqm7.onion
gx7ekbenv2riucmf.onion
57g7spgrzlojinas.onion
76jdd2ir2embyv47.onion
List observed in the framework of WannaCry hashes :
ed01ebfbc9eb5bbea545af4d01bf5f1071661840480439c6e5babe8e080e41aa
c365ddaa345cfcaff3d629505572a484cff5221933d68e4a52130b8bb7badaf9
09a46b3e1be080745a6d8d88d6b5bd351b1c7586ae0dc94d0c238ee36421cafa
0a73291ab5607aef7db23863cf8e72f55bcb3c273bb47f00edf011515aeb5894
428f22a9afd2797ede7c0583d34a052c32693cbb55f567a60298587b6e675c6f
5c1f4f69c45cff9725d9969f9ffcf79d07bd0f624e06cfa5bcbacd2211046ed6
62d828ee000e44f670ba322644c2351fe31af5b88a98f2b2ce27e423dcf1d1b1
72af12d8139a80f317e851a60027fdf208871ed334c12637f49d819ab4b033dd
85ce324b8f78021ecfc9b811c748f19b82e61bb093ff64f2eab457f9ef19b186
a1d9cd6f189beff28a0a49b10f8fe4510128471f004b3e4283ddc7f78594906b
a93ee7ea13238bd038bcbec635f39619db566145498fe6e0ea60e6e76d614bd3
b43b234012b8233b3df6adb7c0a3b2b13cc2354dd6de27e092873bf58af2693c
eb47cd6a937221411bb8daf35900a9897fb234160087089a064066a65f42bcd4
24d004a104d4d54034dbcffc2a4b19a11f39008a575aa614ea04703480b1022c
2c2d8bc91564050cf073745f1b117f4ffdd6470e87166abdfcd10ecdff040a2e
7a828afd2abf153d840938090d498072b7e507c7021e4cdd8c6baf727cafc545
a897345b68191fd36f8cefb52e6a77acb2367432abb648b9ae0a9d708406de5b
fb0b6044347e972e21b6c376e37e1115dab494a2c6b9fb28b92b1e45b45d0ebc
9588f2ef06b7e1c8509f32d8eddfa18041a9cc15b1c90d6da484a39f8dcdf967
b43b234012b8233b3df6adb7c0a3b2b13cc2354dd6de27e092873bf58af2693c
4186675cb6706f9d51167fb0f14cd3f8fcfb0065093f62b10a15f7d9a6c8d982
09a46b3e1be080745a6d8d88d6b5bd351b1c7586ae0dc94d0c238ee36421cafa
Additional information:
UPDATE: As new information on this malware appears, we will make changes to this text.

WannyCry is a cryptographic worm, a distinctive feature of which is the self-propagation function, which is usually absent in classic cryptographers. This means that for infection you do not need to click anywhere, press nothing and open nothing. It is enough to have just a vulnerable, unpatched and connected to the Internet (including through other computers, for example, on the local network) computer based on the Windows platform to become a victim of WannaCry. After the computer is infected, the victim sees an offer to pay a certain amount of money (different variations of WannaCry require different amounts - from 300 to 600 dollars) for returning access to files. The offer is displayed in different languages, including Russian. An interesting point - the ransom message is not just a text file, picture or HTA file, as is usually the case with encryptors, but an executable file.

Pay attention to this point - no response is required from the user ! What made this possible? Everything is simple here - the authors of WannaCry took advantage of a leak from ShadowBrokers, as a result of which the world became aware of many previously unknown vulnerabilities and methods of conducting attacks. Among them was the ETERNALBLUE vulnerability and the DOUBLEPULSAR backdoor associated with it. The first allowed through a vulnerable SMB to gain remote access to a computer and quietly install software on it. And so the WannyCry ransomware is installed. Microsoft in March releasedan appropriate patch for this vulnerability, but, as experience shows, many administrators for various reasons did not bother to install it on their computers. The ETERNALBLUE vulnerability is present on all versions of Windows, excluding Windows 10. Given the large number of Windows family operating systems (Windows XP, Windows 8, Windows Server 2003) and the scale of the attack, Microsoft took an unprecedented step and released patches for these OS.
Please note that if you have the appropriate patch installed or otherwise block the use of this vulnerability, for example, using IPS), this does not mean that you are not subject to WannaCry. In this case, the ransomware will be able to be launched, but this will require a user reaction, familiar to the work of classic ransomware lockers. Installing the Microsoft patch only blocks remote infection and the spread of malicious code.
The malicious program WannaCry searches for vulnerable computers by scanning the open TCP port 445 (Server Message Block / SMB). Therefore, a good idea (if your processes allow this) would be to block access on this port (as well as on the 139th) from the Internet on your firewall or router. For Cisco routers, the appropriate ACL might look like this:
access-list 110 deny tcp any any eq 445
access-list 110 deny tcp any any eq 139
However, blocking these ports from the outside does not mean complete protection against internal infection. If any of your users brings a home laptop containing WannaCry and connects it to the internal local network (and we have already received requests from some customers whose CEOs arrived with their infected computers on weekends, calling “ carpet ”and IT staff), then WannaCry will begin to search for new victims within the organization.
Our analysis shows that, along with the ETERNALBLUE vulnerability, the DOUBLEPULSAR backdoor from the ShadowBrokers leak also works, which allows remote access and arbitrary code execution on a previously compromised machine. Usually, after successful exploitation of the ETERNALBLUE vulnerability, the DOUBLEPULSAR backdoor is installed and the encryptor is installed with its help. If ETERNALBLUE cannot be successfully exploited, but at the same time there is a copy of DOUBLEPULSAR on the attacked node, then the encryption code is set through it.

After successfully installing and encrypting files, WannaCry tries to establish a connection with the nodes of the Tor network to transfer traffic through it and try to hide its true "hosts". The following Tor hosts IP addresses have been discovered by Cisco Talos, but this is not the final list. Our colleagues from other companies have lists of used Tor nodes that have different addresses. Moreover, their analysis shows that most of them have an old history and have already been used in certain malicious activities. In addition, it is worth remembering that the indicated addresses will not be used constantly - their lifespan for the current version of WannaCry will be several weeks. Therefore, you should regularly monitor information about this threat and update the relevant indicators of compromise.
Despite the fact that only a couple of days have passed since the start of the epidemic and several hundred thousand computers have already been damaged, the attackers managed to release several new versions of their malicious creations, mainly in the part of the ransomware. The current version of WannaCry contains the “kill switch” function, that is, checking for the presence of a specific domain on the Internet, upon detection of which malicious code was not installed on the victim’s computer. This domain - iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea [.] Com (other domains are also possible in the new WannaCry modifications) was identified by one of the researchers and registered by him for “intercepting” malware control. As analysis of calls to this domain using the Cisco OpenDNS Investigate service showed, about 200 thousand computers were saved from infection over the past two days.

So far no WannaCry modifications have been discovered without the kill switch function (although attempts have been made, but so far unsuccessful), but this does not mean that it cannot be. In any case, the story is not over yet. On Monday, many will turn on their computers after holidays and weekends, and the number of victims of this malware may increase further. Moreover, our analysis shows that the architecture of WannaCry is modular and can be used to deliver and use other malicious modules.
It is worth noting that at the time of writing the note, it was not yet possible to find a way to decrypt the encrypted files. This means that if a user is infected and does not have a backup copy of his data, the probability of returning access to his files is not high (even in the case of a ransom payment, which does not guarantee that he will receive a decryption key). For encryption, a 2048-bit RSA key is used, and files with the following extensions fall under the distribution:
.der, .pfx, .key, .crt, .csr, .p12, .pem, .odt, .sxw, .stw, .3ds, .max, .3dm, .ods, .sxc, .stc, .dif .slk, .wb2, .odp, .sxd, .std, .sxm, .sqlite3, .sqlitedb, .sql, .accdb, .mdb, .dbf, .odb, .mdf, .ldf, .cpp,. pas, .asm, .cmd, .bat, .vbs, .sch, .jsp, .php, .asp, .java, .jar, .class, .mp3, .wav, .swf, .fla, .wmv, .mpg, .vob, .mpeg, .asf, .avi, .mov, .mp4, .mkv, .flv, .wma, .mid, .m3u, .m4u, .svg, .psd, .tiff, .tif .raw, .gif, .png, .bmp, .jpg, .jpeg, .iso, .backup, .zip, .rar, .tgz, .tar, .bak, .arc, .vmdk, .vdi,. sldm, .sldx, .sti, .sxi, .dwg, .pdf, .wk1, .wks, .rtf, .csv, .txt, .msg, .pst, .ppsx, .ppsm, .pps, .pot, .pptm, .pptx, .ppt, .xltm, .xltx, .xlc, .xlm, .xlt, .xlw, .xlsb, .xlsm, .xlsx, .xls, .dotm, .dot, .docm, .docx .doc
As you can see, office files Excel, Word, PowerPoint, Open Office, music and video files, archives, e-mail messages and mail archives / databases, MS SQL, MS Access database files, MS Visio, Photoshop graphic files are encrypted, as well as virtual machines and others.
Now it’s too early to put an end to the story with WannaCry and a more detailed analysis of this malicious program awaits us. In the meantime, we can give a number of recommendations for protection against it:
- Install at least patch MS17-010, covering the ETERNALBLUE vulnerability in SMB. It is better to upgrade all your Windows computers. In industrial networks, where the installation of patches has its own characteristics, it is worth checking with the manufacturer of your automatic process control system whether the installation of this patch will affect the functioning of the system and the technological process. You can also completely block support for the SMB protocol, if this is acceptable on a particular network and for specific IT processes and applications.
- Block external connections from the Internet using the SMB / NetBIOS protocols - to do this, close the 137th, 139th and 445th TCP ports, as well as the 137th and 138th UDP ports.
- Enable backup systems (even copying important files to a regular USB flash drive or an external hard drive in manual mode will already be superfluous).
- Use current, supported OS versions for which security updates are being released.
- Use personal computer protection tools - from traditional antiviruses with regularly updated signature databases to next-generation protection tools (EDR, STAP, BDS, etc. names).
- Monitor and block traffic to the nodes of the Tor network, which are often used by encryptors and other malicious programs.
- Use Threat Intelligence services that let you keep abreast of the dynamically changing threat landscape and constantly update your defenses with new indicators of compromise.
For those users who use Cisco cybersecurity solutions, we can say that all our solutions can deal with this threat:
- Advanced Malware Protection (AMP), especially AMP for Endpoints, is ideal for detecting and preventing this malware.
- Cloud Web Security (CWS) and Web Security Appliance (WSA) detect access to malicious kill switch domains.
- Cisco Firepower NGIPS has up-to-date signatures to detect and block this threat.
- The Cisco Firepower NGFW (as well as the Cisco ASA) can block access to the 139th and 445th TCP ports, and it also has a regularly updated list of Tor hosts to track interaction with this network and block outgoing connections.
- AMP Threat Grid helped analyze the malicious behavior of WannaCry, and can also do this for new versions of this malicious program.
- OpenDNS Umbrella helps identify interactions with domains associated with this threat. You can take advantage of the free version of OpenDNS Home , which will increase the level of protection for home users.
- Stealthwatch detects network activity associated with scanning vulnerable sites, the spread of malicious code over the network, as well as interaction with command servers (C2 or CnC), including the Tor network.
- Identity Service Engine (ISE) can monitor unpatched hosts on the local network and block access or localize them by redirecting to the quarantine subnet. The integration of ISE with Qualys Security Scanner (TC-NAC) allows you to identify nodes that are vulnerable to ETERNALBLUE and also quarantine them.
Snort users should be aware that rules 42329-42332, 42340, and 41978, which are available as part of the service pack on Snort.org, help fight this threat . For users of Cisco Legacy IPS, the IPS Signature Pack S982 has been prepared, in which the 7958-0 and 7958-1 are fighting with WannaCry.
In addition, we want to specify indicators for compromise WannaCry, which we have identified as part of our analysis:
File names :
d5e0e8694ddc0548d8e6b87c83d50f4ab85c1debadb106d6a6a794c3e746f4fa b.wnry
055c7760512c98c8d51e4427227fe2a7ea3b34ee63178fe78631fa8aa6d15622 c.wnry
402751fa49e0cb68fe052cb3db87b05e71c1d950984d339940cf6b29409f2a7c r.wnry
e18fdd912dfe5b45776e68d578c3af3547886cf1353d7086c8bee037436dff4b s.wnry
Taskdl.exe 4a468603fdcb7a2eb5770705898cf9ef37aade532a7964642ecd705a74794b79
2ca2d550e603d74dedda03156023135b38da3630cb014e3d00b1263358c5f00d taskse.exe
97ebce49b14c46bebc9ec2448d00e1e397123b256e2be9eba5140688e7bc0ae6 t.wnry
b9c5d4339809e0ad9a00d4d3dd26fdf44a32819a54abf846bb9b560d81391c25 u.wnry
Observed IP-addresses :
188 166 23 127 443 - Tor Exit Node [.] [ .] [.]
193 23 244 [[.] [.] .] 244: 443 - Tor Exit Node
2 [.] 3 [.] 69 [.] 209: 9001 - Tor Exit Node
146 [.] 0 [.] 32 [.] 144: 9001 - Tor Exit Node
50 [. ] 7 [.] 161 [.] 218: 9001 - Tor Exit Node
128.31.0 [.] 39 - Tor Exit Node
213.61.66 [.] 116 - Tor Exit Node
212.47.232 [.] 237 - Tor Exit Node
81.30 .158 [.] 223 - Tor Exit Node
[.] 79.172.193 32 - the Tor the Exit the Node
the Tor C2 :
xxlvbrloxvriy2c5.onion
cwwnhwhlz52maqm7.onion
gx7ekbenv2riucmf.onion
57g7spgrzlojinas.onion
76jdd2ir2embyv47.onion
List observed in the framework of WannaCry hashes :
ed01ebfbc9eb5bbea545af4d01bf5f1071661840480439c6e5babe8e080e41aa
c365ddaa345cfcaff3d629505572a484cff5221933d68e4a52130b8bb7badaf9
09a46b3e1be080745a6d8d88d6b5bd351b1c7586ae0dc94d0c238ee36421cafa
0a73291ab5607aef7db23863cf8e72f55bcb3c273bb47f00edf011515aeb5894
428f22a9afd2797ede7c0583d34a052c32693cbb55f567a60298587b6e675c6f
5c1f4f69c45cff9725d9969f9ffcf79d07bd0f624e06cfa5bcbacd2211046ed6
62d828ee000e44f670ba322644c2351fe31af5b88a98f2b2ce27e423dcf1d1b1
72af12d8139a80f317e851a60027fdf208871ed334c12637f49d819ab4b033dd
85ce324b8f78021ecfc9b811c748f19b82e61bb093ff64f2eab457f9ef19b186
a1d9cd6f189beff28a0a49b10f8fe4510128471f004b3e4283ddc7f78594906b
a93ee7ea13238bd038bcbec635f39619db566145498fe6e0ea60e6e76d614bd3
b43b234012b8233b3df6adb7c0a3b2b13cc2354dd6de27e092873bf58af2693c
eb47cd6a937221411bb8daf35900a9897fb234160087089a064066a65f42bcd4
24d004a104d4d54034dbcffc2a4b19a11f39008a575aa614ea04703480b1022c
2c2d8bc91564050cf073745f1b117f4ffdd6470e87166abdfcd10ecdff040a2e
7a828afd2abf153d840938090d498072b7e507c7021e4cdd8c6baf727cafc545
a897345b68191fd36f8cefb52e6a77acb2367432abb648b9ae0a9d708406de5b
fb0b6044347e972e21b6c376e37e1115dab494a2c6b9fb28b92b1e45b45d0ebc
9588f2ef06b7e1c8509f32d8eddfa18041a9cc15b1c90d6da484a39f8dcdf967
b43b234012b8233b3df6adb7c0a3b2b13cc2354dd6de27e092873bf58af2693c
4186675cb6706f9d51167fb0f14cd3f8fcfb0065093f62b10a15f7d9a6c8d982
09a46b3e1be080745a6d8d88d6b5bd351b1c7586ae0dc94d0c238ee36421cafa
Additional information:
- A more complete WannaCry analysis (in English) on the Cisco Talos Blog .
- Description of the ETERNALBLUE vulnerability on the Cisco website .
- The influence of WannaCry on Cisco products.
UPDATE: As new information on this malware appears, we will make changes to this text.
