Investigation of security incidents with StaffCop Enterprise 4.4
Hello! My name is Roman Frank, I am a specialist in information security. Until recently, I worked in a large company in the security department (technical protection). I had 2 problems: there were no normal modern technical means of protection and money for security in the budget. But I had free time to study software solutions, about one of them - StaffCop Enterprise - I want to tell you in detail today.
Experience has shown me that 90% of the time I spent on identifying and investigating information leaks myself, with the program is solved in a few minutes. I was so absorbed in the technical details of the solution that I eventually left my company and now I work at StaffCop as a technical support specialist.

StaffCop Enterprise is a system for monitoring employee actions with DLP functionality.
The program is capable of:

In my opinion, a tangible advantage is the lack of the need to close on a local network with the inability to work via the Internet. Since it is now difficult to talk about the perimeter of information security (in any company there are remote branches or employees on freelance), gateway solutions are not as flexible and, often, require an agent at the user's workstation.
This task of full control of workstations outside the local network of StaffCop easily copes. The stack of technologies used in the development allows the system to be less demanding of resources and easy to integrate with other systems, and developers - if necessary, modify the functionality. Also, in the near future a distribution kit with a certificate of FSTEC will be released, which is suitable for protecting objects where protection class 4 and below is needed. All this allows the system to be profitable, reliable and useful to various specialists.
Let's start with the most important thing. How can the StaffCop system make life safer?Let us examine the main headaches of a person whose task is to prevent the explosion of powder barrels. The powder keg can be restricted access information that has become known outside the company. Accordingly, the main concern is not to leave. And, if left, then how to find the attacker and punish.
Staffcop controls all the main channels of information transfer from user PCs to Windows. The Linux agent is moving in the same direction, but for now there is a need for network monitoring.

Organizational measures are good exactly as long as they are carried out, in other cases, technical protection measures are a must.
Not always passive protection measures are a cheap substitute for active protective equipment. In our case, Staffcop is an active means of protection and allows you to monitor and close some channels of information leaks.
When investigating incidents, the evidence base is very important. Staffcop allows you to keep a history of all events that were committed by the user during monitoring.
I believe that StaffCop is the main tool in the hands of a security guard who will save time for security and money for company management.
Resource requirements can be found here .
Installation details .
And if you want to drive the system in test mode and see for yourself whether StaffCop is right for you, you can send a request here or through our partner .
Roman Frank,
StaffCop technical support specialist
Experience has shown me that 90% of the time I spent on identifying and investigating information leaks myself, with the program is solved in a few minutes. I was so absorbed in the technical details of the solution that I eventually left my company and now I work at StaffCop as a technical support specialist.

Let's look at StaffCop Enterprise
StaffCop Enterprise is a system for monitoring employee actions with DLP functionality.
The program is capable of:
- ensure information security in the company (detects information leaks and investigates incidents);
- monitor employee actions (keeps records of working time, evaluates employee productivity, conducts behavioral analysis, monitors business processes);
- conduct remote administration (administration of workplaces, inventory of computers).

In my opinion, a tangible advantage is the lack of the need to close on a local network with the inability to work via the Internet. Since it is now difficult to talk about the perimeter of information security (in any company there are remote branches or employees on freelance), gateway solutions are not as flexible and, often, require an agent at the user's workstation.
This task of full control of workstations outside the local network of StaffCop easily copes. The stack of technologies used in the development allows the system to be less demanding of resources and easy to integrate with other systems, and developers - if necessary, modify the functionality. Also, in the near future a distribution kit with a certificate of FSTEC will be released, which is suitable for protecting objects where protection class 4 and below is needed. All this allows the system to be profitable, reliable and useful to various specialists.
Let's start with the most important thing. How can the StaffCop system make life safer?Let us examine the main headaches of a person whose task is to prevent the explosion of powder barrels. The powder keg can be restricted access information that has become known outside the company. Accordingly, the main concern is not to leave. And, if left, then how to find the attacker and punish.
Confidential Information Control
Staffcop controls all the main channels of information transfer from user PCs to Windows. The Linux agent is moving in the same direction, but for now there is a need for network monitoring.
- Control file operations / special file control. If you have determined which files need to be protected from prying eyes, the settings allow you to intercept any operations with these files, including copying, printing, saving in another place, etc. If anyone makes changes to such files or to them title, a shadow copy of the document will be created. It is worth emphasizing that if an organization has a list of confidential information, employees must sign a non-disclosure agreement and, more importantly, this agreement should clarify that personal computers are company property and the data processed for these PCs can be copied, can be stored and processed by security personnel.
- Removable media control.A flash drive is the most popular way to merge information. Staffcop allows you to set up monitoring of USB devices. This means that as soon as someone uses a USB flash drive, the security technician in the event tape shows the fact of connecting a removable device. Moreover, any files sent to removable media will be intercepted. You can always restore a complete picture of how exactly the database was copied or other confidential information. If there is a need, and in large organizations it is always there, you can prohibit all devices, except for those that are allowed, on the white list. These settings allow you to work with locks on users' PCs, as well as on the users themselves. In addition, there is a control of device types, for example, you can unlock removable hard drives, and USB-carriers to block.
- Control network traffic / special control sites . StaffCop controls all user activity on the network. To control network traffic, a certificate substitution method is used, thanks to this substitution, all traffic that goes through an https connection is intercepted. By default, it is encrypted with the TLS protocol, but thanks to the substitution, it can be decrypted, intercepted the correspondence and thus closes one of the most important channels of information leakage - the Internet.
- Interception of mail. You can intercept the body of the letter, the mailing list, including a copy and a hidden copy, as well as all attachments. Mail control is implemented in several areas: web mail control, mail control that uses POP3, POP3S, SMTP, SMTPS, IMAP, IMAPS, MAPI protocols ... If you don’t have your option here, let us know!
- Control of instant messengers. The main feature of the interception, which allows you not to be attached to the sources of instant messengers - the binding of all events to each other. Accordingly, specifying the WhatsApp application, we will receive all the screenshots for this application and keyboard input. You can filter related events by time. Similarly with web messengers. I would also recommend setting up a special control of the sites of instant messengers, at which screenshots are made every few seconds if the user is on such a site.
- Application startup and installation control / special program control. You will always know what programs employees use. You can filter out those applications that are not valid in your organization and block them. StaffCop allows you to track users who install and run illegitimate software or, for example, work in AutoCAD or in other corporate software for personal purposes, executing orders from third-party customers. As well as for sites, you can configure selective enhanced control: if an employee launches a certain application, screenshots with an increased frequency will be taken, for example, every 2 seconds.
- Control printers. For you now will not be a secret where the paper goes. Events of sending documents to print are recorded, with shadow copy enabled, a shadow copy of printed documents will be made.

Search for potential leaks
Organizational measures are good exactly as long as they are carried out, in other cases, technical protection measures are a must.
- Do your colleagues use personal mail and cloud services to send work files? There is a special filter that allows you to track all mail that is not sent from the corporate domain. You can see that the person uses personal mail, intercept the message, notice leaks. Implemented interception of documents sent to the cloud. If an employee uploads a document there, his shadow copy is saved.
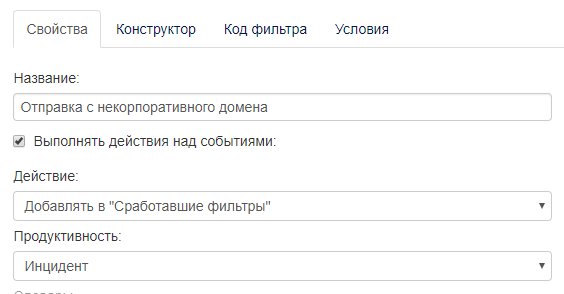
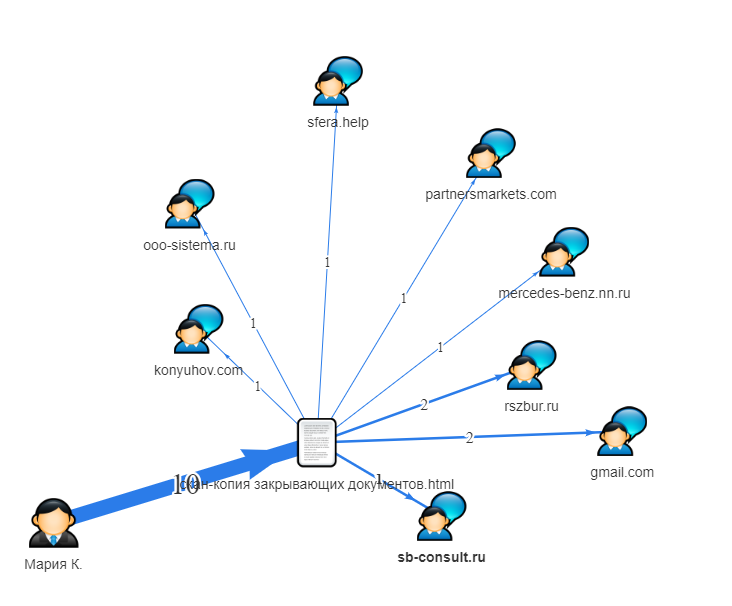
You can filter all users who sent messages not from corporate email. This is especially important because, as soon as the document went online, you no longer control it. It is important to remember that not all information sinks are committed by malicious intent. Banal user mistakes can cost a lot of money for the organization. - Do you know with whom your employees communicate during working hours? You have the right to know this if you warned them. There is a special graph that allows you to see the relationship between users via any channels of communication. The most popular case is confidential information. File names are known. Thanks to this column, you can always track who sent the documents to which addresses. As soon as the document has left the organization, it becomes clearly visible. Such a report is suitable for a manager who wants to see the result of the work of a security man and who does not want to understand all the filters, flows of information and data. He just needs some final report, preferably a small one, where you can see the file name, the sending channel, the external address.
- Dictionaries. You can set up sending notifications when using profanity, and thus track splashes of negativity and take action. Especially if users are working with customers - it is unacceptable that they use profanity in communication.

- Personal cards of employees. A personal card contains all the information for a specific user. For example, for which computer it works, top sites, top applications that it launches, search queries, intercepted files, recent screenshots. You can track the graph of communications - communication with other employees within the organization: with whom it communicates more often, through which channels of communication. This is a kind of dossier, a personal matter, from which you can get general information about the employee. Such cards can be created not only for people, but also for files, computers. Employee cards are well suited for investigating incidents. As an introduction to the user.

- A user behavior anomaly detector is used to detect leaks. Drastic change in employee behavior is a reason to pay attention. The StaffCop Enterprise detector is configured by default to exceed the average occurrence of an event by 10 times. The most popular case is an increase in copy operations. For example, there was a case of fixing copying a large number of documents to a USB-drive. Additionally, it was revealed that information was copied from a closed network segment, which is necessary for working with drawings marked “Confidential”. Further, physical information protection measures and security services come into force. Employee detained for further investigation. Anomaly detector will significantly reduce the time to detect incidents for which it is difficult or impossible to set up an automatic filter.

Closing holes
Not always passive protection measures are a cheap substitute for active protective equipment. In our case, Staffcop is an active means of protection and allows you to monitor and close some channels of information leaks.
- We block personal USB drives and CDs. The organization may prohibit the use of personal removable media. A so-called “white list” of allowed devices is introduced, and all other media that are not included in it will be blocked.

- We block visiting “unproductive” sites or allow only “productive” ones. You can set rules for blocking sites by address. Blocking rules work on a substring - it is not necessary to specify exact addresses and domains. You can do without the products that are used for blocking sites.
- Block the launch of applications. You can make a list of applications that can be blocked, or vice versa, use only allowed ones. When creating a closed software environment, you need to be very careful about the list of allowed applications. In case of an error, the login can be blocked.
- Configure alerts for malicious actions. For any events that we consider an incident, you can build a filter and set up an alert. The list of such events is determined independently by the customer at the testing stage. For example, copying to a USB-drive is considered malicious if, for some reason, it is impossible to set up a white list. Such events are recorded, the report is sent with a specified frequency, for example, every day or once a week. You can set up an immediate alert when a certain event occurs.
Incident Investigation
When investigating incidents, the evidence base is very important. Staffcop allows you to keep a history of all events that were committed by the user during monitoring.
- Incident or not incident? It is necessary to look in more detail. There is an event communication system and the construction of multidimensional reports, the “Drill-down” technique. All events are interrelated with each other, for example, interception of web forms is associated with site visits, when a person enters a username and password into a web form when entering a site, this information can be intercepted. If interception of this form is enabled, we will see not only what was in these forms, but also the site on which the form was entered. "Drill-down" is a failure, that is, you can detail the information on the event and see the related events.
StaffCop uses OLAP technology (multidimensional cube). Thanks to the use of a hybrid mode with two databases, the user gets excellent performance results. Reports that are formed in several systems in several hours, StaffCop Enterprise forms in a few (tens) seconds. From the report, you can clarify any information associated with a particular event. - Microphone recording, desktop video and screenshots are used to understand the context of events. For example, a specific filter worked, an event occurred, but its context is incomprehensible. Microphone recording and desktop video recording are two modules that are disabled by default. Sound is recorded in short lengths of 10 minutes (you can put more or less), while silence is not recorded. You can also record video. Each event is saved with a time stamp. If the desktop video recording module is turned on, everything that happens on the desktop is recorded. It should be understood that the storage of large amounts of information is expensive. This function can be used pointwise, for example, if a certain employee came under suspicion, you can put such a module on it and monitor everything that happens. Screenshots are used when special control of sites and programs is required. With the help of these modules, any event can be detailed in parts. Fine-tuning will allow to select for the investigation of incidents only those modules that will allow step by step to identify not only the fact of information leakage and causes, but also, possibly, additional involved persons and events.

- Fast reporting. The product uses a hybrid database PostgreSQL + ClickHouse, thanks to which, the construction of reports is very fast. Lack of ClickHouse - resource requirements. For example, the server must have at least 16 GB of RAM, 8 or 16 cores, so this solution is only used for systems with a large number of agents. In such systems, many events occur, and in order to quickly load them, ClickHouse is needed. If PostgreSQL is used, the problem arises: if there are several tens of millions of events in the database, then there is a delay in uploading to the web console up to 1 minute, but if you constantly refresh the page, then all new events will fall into the event lens.
Sometimes a hybrid mode is used when two databases are running at the same time. It should be noted that the StaffCop Enterprise system does not use cloud technologies, except ABBYY, a cloud service for text recognition.
I believe that StaffCop is the main tool in the hands of a security guard who will save time for security and money for company management.
Resource requirements can be found here .
Installation details .
And if you want to drive the system in test mode and see for yourself whether StaffCop is right for you, you can send a request here or through our partner .
Roman Frank,
StaffCop technical support specialist
