SafeNet Authentication Service - One-Time Password Management System
About a year ago, in the article “ eToken lived, eToken alive, eToken will live ” I mentioned a product like Gemalto Safenet Authentcation Service, it's time to talk more about it. This article is introductory, but there will be other, more technical ones, and I think even with real business cases.
IT professionals often face the issue of enhancing the security of a service. And the issue of user identification with authentication also plays a key role in the security of the service.
What to choose:
After all, the use of the decision should not complicate access to the service, otherwise it will lead to resistance from the end user. According to statistics, in most cases, a user is compromised at the authentication stage. Before you figure out what to use in practice, IT managers seriously evaluate various methods. Particular attention is paid when users from the so-called "untrusted environment" work.
Suppose, when working, a user from an untrusted environment enters his user data for identification and a password for authentication, while being at someone else's computer, say in an Internet cafe. In the meantime, attackers can intercept either network packets or keyboard input, which will allow them to use user data in the future. Also, all user input in an untrusted environment can be locally cached on the computer that he used.
Of course, the use of disposable media in the form of smart cards or USB tokens is much more reliable than the use of passwords. But what to do when there comes a special case when the user needs to use a smart card or USB token outside the office at the moment. Not to mention the fact that for each type of smart card and USB token, it is necessary to have specialized software (software) on the computer. There is no reason to hope for anything in the public zone and it is unlikely that it will be possible to establish it. It is also impossible to exclude the need for a free USB port, which can be blocked for connecting USB tokens or PC equipment with a reader for smart cards. And given the increased popularity among users to work on mobile devices,
Much easier to use one-time passwords - OTP - One-Time Password for a one-time user authentication procedure. Such a password is simpler and more convenient to use. It makes no sense to intercept a one-time password using a keylogger or to fear that it will be cached on a computer. It is useless to peek a one-time password or think that it can be intercepted in the form of network packets. Today it is the only type of tokens that do not require a connection to a personal computer, or the presence of specialized software on it, working with any platform in any environment. A large selection of the model range in the form of one-time password generators will allow enterprises to provide enhanced security in providing access to corporate resources, the portal (s) or the user's personal account,
What to do when we decided on the method of user authentication? To whom should I transfer the role of the person responsible for managing and maintaining the service? How to manage the life cycle of OTP tokens that are distributed to users? How to track their statuses? How to increase user support service? These, as well as many more questions may arise before IT managers.
The key role in solving these issues is played by the choice of a solution that will cope with the task of managing the life cycle of OTP tokens. Since the main task, after putting the tokens into operation and handing them over to users, is to provide timely services to the token users as soon as possible. Of course, there are a sufficient number of control systems on the market, but first of all, you should pay attention to the mono-vendor solutions. Nobody knows better than a vendor their tokens.
You can’t ignore the Gemalto-SafeNet solution - SafeNet Authentication Service, which is annually nominated for the “Best Multi-Factor Authentication Solution” by reputable publications and research companies.
Choosing the right authentication solution is of great importance in reducing business risks. Of course, the best solutions have the largest number of supported token models, and can protect both cloud and on-premises applications and services, as well as any network access from any device. But it’s not just about security, it’s also about how easy it is to deploy, manage and scale your authentication solution.
What is a SafeNet Authentication Service?
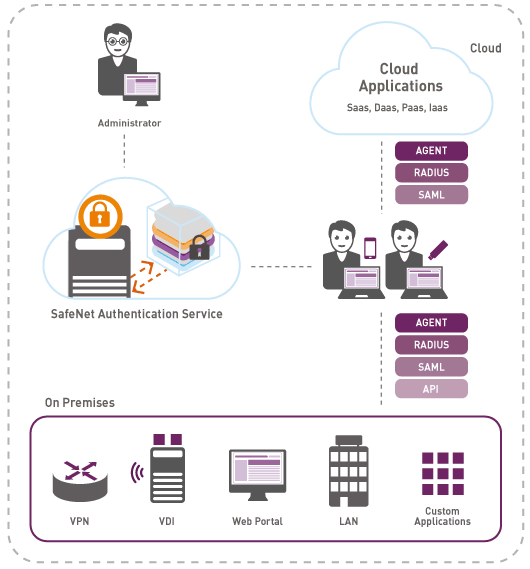
SafeNet Authentication Service is a fully automated multi-factor authentication service whose goal is to serve users with tokens. SafeNet Authentication Service is distributed in 2 types of editions. A local version that you can deploy yourself in your own enterprise infrastructure. And also in the form of a cloud edition - such a service has already been deployed and there is no need to ask a question: “where can I find resources for its deployment?”. SafeNet Authentication Service is managed in the admin browser console. The console has optimal conditions for managing processes: automatic preparation of users and user repository, for example, if you use an LDAP directory or a DBMS as the basis for users; setting up self-service users;
The SafeNet Authentication Service supports the following authentication methods and form factors:
Software tokens for SafeNet Authentication Service support a large number of platforms, including: MS Windows, Windows Mobile, MAC OS X, iOS, Android, and BlackBerry. The SafeNet Authentication Service supports various combinations of user profiles, which allow you to combine different authentication methods, taking into account the requirements of the enterprise security policy.
Hardware OTP tokens are used to create highly secure one-time passwords. A large selection of the model range of hardware tokens eToken PASS, eToken GOLD, KT-4, RB-1 allows users to log in to critical applications and data.
The SafeNet Authentication Service uses the Enterprise standard RADIUS and SAML protocols, which essentially means that the service can be integrated into any network and application, including solutions from all leading vendors. With SafeNet Authentication Service, you can protect any access to any application.
The SafeNet Authentication Service out of the box supports VPNs with enhanced authentication, both IPSec and SSL VPN, in other words, vendor-level compatibility from vendors such as Cisco, Checkpoint, Juniper, F5, Palo Alto, SonicWall, Citrix and WatchGuard. The expansion of strong authentication in the virtualization infrastructure (VDI) will help ensure authentication reliability on thin clients, mobile terminals and employee’s own devices (BYOD) in virtualization environments from Citrix, VMware and AWS (Amazon Web Services).
Not so long ago, the official distributor of Gemalto-SafeNet solutions in Russia TESSIS (Technologies, Systems and Solutions for Information Security) announced that the FSTEC certificate of conformity No. 3070 was extended until January 27, 2020. The solution can be used in information systems and personal data processing systems for security classes 3 and 4 with an actual threat of the absence of undeclared capabilities of type 3.
Cases, when and where can use the SAS solution?
Financial institutions and remote banking:
Telecom and telecom operators:
Medical and pharmaceutical organizations:
Corporate Security:
In conclusion, I would like to note that the choice towards enhanced authentication and the use of one-time passwords really protects user authentication. One-time passwords are convenient and easy to use for organizing access to corporate resources, portals and cloud services. The user does not have to remember passwords, since a one-time password is entered and forgotten. It is also important that, regardless of the workplace the user is working for, he does not need to install a driver for the token. And using the SafeNet Authentication Service, we get a complete solution for organizing access to various services and managing the life cycle of OTP tokens. The concept of SafeNet Authentication Service is to make multi-factor authentication public. And using the SafeNet Authentication Service proves
IT professionals often face the issue of enhancing the security of a service. And the issue of user identification with authentication also plays a key role in the security of the service.
What to choose:
- Use a bunch of Login & Password?
- Deploy PKI infrastructure and give out certificates to everyone?
- Strengthen authentication with one-time passwords?
After all, the use of the decision should not complicate access to the service, otherwise it will lead to resistance from the end user. According to statistics, in most cases, a user is compromised at the authentication stage. Before you figure out what to use in practice, IT managers seriously evaluate various methods. Particular attention is paid when users from the so-called "untrusted environment" work.
Suppose, when working, a user from an untrusted environment enters his user data for identification and a password for authentication, while being at someone else's computer, say in an Internet cafe. In the meantime, attackers can intercept either network packets or keyboard input, which will allow them to use user data in the future. Also, all user input in an untrusted environment can be locally cached on the computer that he used.
Of course, the use of disposable media in the form of smart cards or USB tokens is much more reliable than the use of passwords. But what to do when there comes a special case when the user needs to use a smart card or USB token outside the office at the moment. Not to mention the fact that for each type of smart card and USB token, it is necessary to have specialized software (software) on the computer. There is no reason to hope for anything in the public zone and it is unlikely that it will be possible to establish it. It is also impossible to exclude the need for a free USB port, which can be blocked for connecting USB tokens or PC equipment with a reader for smart cards. And given the increased popularity among users to work on mobile devices,
Much easier to use one-time passwords - OTP - One-Time Password for a one-time user authentication procedure. Such a password is simpler and more convenient to use. It makes no sense to intercept a one-time password using a keylogger or to fear that it will be cached on a computer. It is useless to peek a one-time password or think that it can be intercepted in the form of network packets. Today it is the only type of tokens that do not require a connection to a personal computer, or the presence of specialized software on it, working with any platform in any environment. A large selection of the model range in the form of one-time password generators will allow enterprises to provide enhanced security in providing access to corporate resources, the portal (s) or the user's personal account,
What to do when we decided on the method of user authentication? To whom should I transfer the role of the person responsible for managing and maintaining the service? How to manage the life cycle of OTP tokens that are distributed to users? How to track their statuses? How to increase user support service? These, as well as many more questions may arise before IT managers.
The key role in solving these issues is played by the choice of a solution that will cope with the task of managing the life cycle of OTP tokens. Since the main task, after putting the tokens into operation and handing them over to users, is to provide timely services to the token users as soon as possible. Of course, there are a sufficient number of control systems on the market, but first of all, you should pay attention to the mono-vendor solutions. Nobody knows better than a vendor their tokens.
You can’t ignore the Gemalto-SafeNet solution - SafeNet Authentication Service, which is annually nominated for the “Best Multi-Factor Authentication Solution” by reputable publications and research companies.
 |  |  |
Choosing the right authentication solution is of great importance in reducing business risks. Of course, the best solutions have the largest number of supported token models, and can protect both cloud and on-premises applications and services, as well as any network access from any device. But it’s not just about security, it’s also about how easy it is to deploy, manage and scale your authentication solution.
What is a SafeNet Authentication Service?
SafeNet Authentication Service is a fully automated multi-factor authentication service whose goal is to serve users with tokens. SafeNet Authentication Service is distributed in 2 types of editions. A local version that you can deploy yourself in your own enterprise infrastructure. And also in the form of a cloud edition - such a service has already been deployed and there is no need to ask a question: “where can I find resources for its deployment?”. SafeNet Authentication Service is managed in the admin browser console. The console has optimal conditions for managing processes: automatic preparation of users and user repository, for example, if you use an LDAP directory or a DBMS as the basis for users; setting up self-service users;
The SafeNet Authentication Service supports the following authentication methods and form factors:
- Authentication Methods:
- One Time Password (OTP)
- OOB by notification, via SMS and / or email
- - Template Matrix Authentication (GrIDsure)
- Available Form Factors:
- Hardware Tokens (OTP Token)
- Software Tokens (OTP Applications)
- - Phone-as-token
Software tokens for SafeNet Authentication Service support a large number of platforms, including: MS Windows, Windows Mobile, MAC OS X, iOS, Android, and BlackBerry. The SafeNet Authentication Service supports various combinations of user profiles, which allow you to combine different authentication methods, taking into account the requirements of the enterprise security policy.
Hardware OTP tokens are used to create highly secure one-time passwords. A large selection of the model range of hardware tokens eToken PASS, eToken GOLD, KT-4, RB-1 allows users to log in to critical applications and data.
The SafeNet Authentication Service uses the Enterprise standard RADIUS and SAML protocols, which essentially means that the service can be integrated into any network and application, including solutions from all leading vendors. With SafeNet Authentication Service, you can protect any access to any application.
 |
The SafeNet Authentication Service out of the box supports VPNs with enhanced authentication, both IPSec and SSL VPN, in other words, vendor-level compatibility from vendors such as Cisco, Checkpoint, Juniper, F5, Palo Alto, SonicWall, Citrix and WatchGuard. The expansion of strong authentication in the virtualization infrastructure (VDI) will help ensure authentication reliability on thin clients, mobile terminals and employee’s own devices (BYOD) in virtualization environments from Citrix, VMware and AWS (Amazon Web Services).
 |
Not so long ago, the official distributor of Gemalto-SafeNet solutions in Russia TESSIS (Technologies, Systems and Solutions for Information Security) announced that the FSTEC certificate of conformity No. 3070 was extended until January 27, 2020. The solution can be used in information systems and personal data processing systems for security classes 3 and 4 with an actual threat of the absence of undeclared capabilities of type 3.
Cases, when and where can use the SAS solution?
Financial institutions and remote banking:
- Use of strong authentication when checking an authorized user;
- Ensuring transaction integrity;
- Security coordination mechanisms in each use case to confirm user actions.
Telecom and telecom operators:
- Use of strong authentication when checking an authorized user;
- Ensuring the necessary level of efficiency and accessibility without compromising security;
- Access control of authorized users to the billing system;
- Increased access security for a wide range of services for customers;
Medical and pharmaceutical organizations:
- Use of strong authentication when checking an authorized user;
- Ensuring the necessary level of security when accessing the electronic patient filing cabinet / database for accounting for warehouse preparations, etc .;
- Integration with proprietary software environments;
Corporate Security:
- Providing security, enhanced security for the entire environment, covering remote access services, virtual private networks, web-portals, corporate networks and cloud applications;
- Policies for centralized management of authenticators and authorized users;
In conclusion, I would like to note that the choice towards enhanced authentication and the use of one-time passwords really protects user authentication. One-time passwords are convenient and easy to use for organizing access to corporate resources, portals and cloud services. The user does not have to remember passwords, since a one-time password is entered and forgotten. It is also important that, regardless of the workplace the user is working for, he does not need to install a driver for the token. And using the SafeNet Authentication Service, we get a complete solution for organizing access to various services and managing the life cycle of OTP tokens. The concept of SafeNet Authentication Service is to make multi-factor authentication public. And using the SafeNet Authentication Service proves
