Security Week 48: Black Friday Hacking
 The world holiday of consumption called “Black Friday”, fortunately, is over. It remains to find out whether you saved money or still lost. And this question is related not only to the usefulness and usefulness of the purchased goods. Sometimes, instead of buying, there is a leak of credit card information or a payment system account, and then a direct theft of money as a result of cybercriminals. The phenomenon of massive sales is of interest to those who protect payments online, so last week there was also enough research on security. Let's look at the most interesting.
The world holiday of consumption called “Black Friday”, fortunately, is over. It remains to find out whether you saved money or still lost. And this question is related not only to the usefulness and usefulness of the purchased goods. Sometimes, instead of buying, there is a leak of credit card information or a payment system account, and then a direct theft of money as a result of cybercriminals. The phenomenon of massive sales is of interest to those who protect payments online, so last week there was also enough research on security. Let's look at the most interesting.In today's release: attacks on users with the help of malware on personal computers and on mobile phones. Attacks on online stores with the subsequent theft of credit card data. And just fake websites that do not sell anything, but accept money from the public. And we will start with the Rotexy Android Trojan investigated by Kaspersky Lab.
Rotexy (short review in this news, full research) Is a malware for Android devices, first discovered in 2014. A feature of this family of Trojans was the use of three channels at once to communicate with the command server: via SMS, directly via the Internet or using the Google Cloud Messaging service. Trojan spreads via SMS with a link to an infected APK under the name AvitoPay.apk or similar. If you have ever placed an advertisement for the sale and received a strange SMS with the link “I am ready to pay, click here”, this was it (or something like that, there are many such programs). After installing and requesting administrator rights, Rotexy sends the device IMEI command to the command server. In response, a set of rules arrives that allow processing, for example, SMS from online banking. These rules look like this:
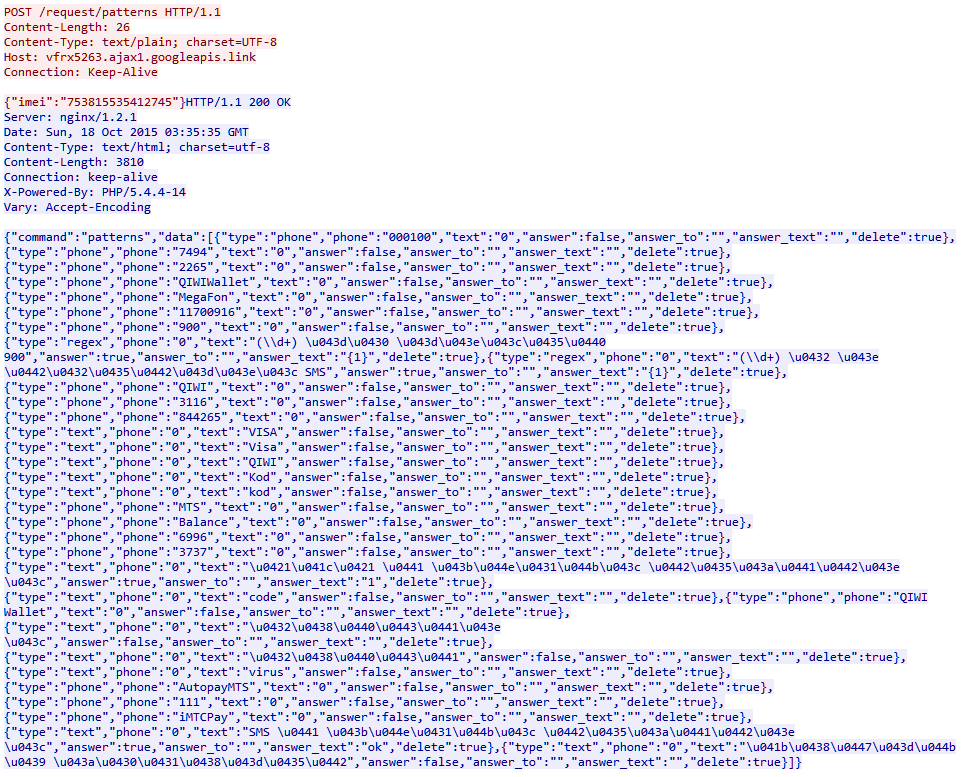
Initially, communication between the infected phone and the command server went completely clear, since 2015, encryption has appeared. In 2016, phishing was added to the typical set to steal money (sending SMS, intercepting and deleting response SMS from banks).
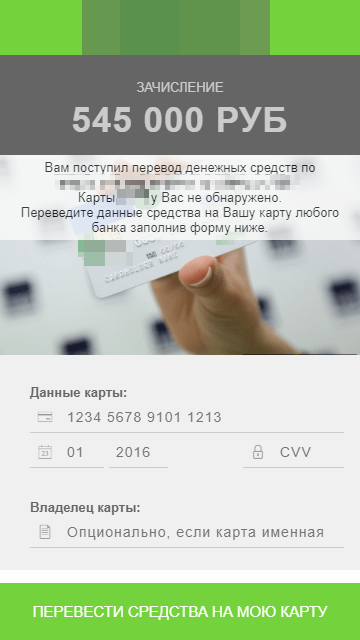
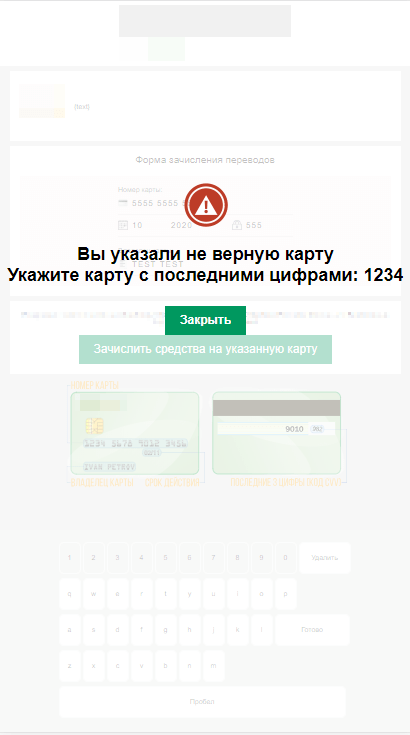
The most modern version of the malicious program, after requesting administrator rights, shows a stub - the application was allegedly unable to install. In fact, the program hides its icon from the list of installed applications. If the user rejects the request for administration rights, the application flashes the screen. After installation, when you try to stop the application, the phone is forced to restart. Depending on the command sent by the managing server, the Trojan can send itself to all contacts on the phone, update itself, transfer the list of contacts and messages to the attackers, pretend that the user has received an SMS message, display a phishing page or a page of allegedly blocked smartphone and then extort money . If the user enters card details,
More Trojans for computers and mobile phones are described in the Kaspersky Lab report for Black Friday ( short version in Russian, complete in English). The study provides an approximate breakdown by areas of interest of cybercriminals: in half of the cases, billing data of victims are intercepted during purchases in online retailers (independent stores selling, for example, clothes and jewelry, but not electronics). Online platforms such as eBay or Alibaba are “controlled” by malware much less frequently. Perhaps because the value for them is no longer credit card numbers, but user accounts. On the black market, PayPal accounts are most often offered, but Amazon and eBay accounts are often found.
Another way to dishonestly take money from the public is to create and promote fake websites that mimic popular online platforms. In a study by Group-IB ( news ) reported the discovery of at least 400 clones of only one site AliExpress. Last year's "Friday" study of Kaspersky Lab showedA significant increase in the share of purchases from mobile devices, where determining that you have a fake website, is even more difficult than when viewing the desktop version. Finally, to steal your payment details, it is not necessary to attack the end users. Since 2015, information security researchers have been monitoring the activities of the MageCart group, which got its name from attacks on CMS Magento. For example, a large ticket service Ticketmaster suffered from their hands this summer .
According to researcher Willem de Groot, competition began in November between the group members (or individual gangs) ( news , postin the blog of the researcher). On one of the sites, several malicious scripts were detected at once, sending data on credit card numbers to hackers. One of the scripts (more advanced) not only collected credit card numbers - it also interfered with the work of competitors: card numbers were sent to their server, in which one digit was replaced with the help of such a simple randomizer.
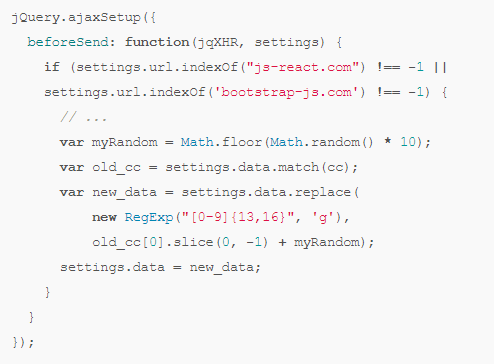
Thus, one criminal group also spoils the reputation of another. According to the same expert, over the past three months, malicious code, one way or another related to the MageCart campaign, was detected on more than five thousand sites. Over three years, 40,000 sites have been infected. One online store attacked 18 times in a row. On another, the attackers left a message to the administrators: say, stop deleting the scripts.
Recommendations to prevent theft of funds from credit cards and theft of accounts of payment systems, despite the development of methods of attack, remain the same. Protecting devices from malware, using for payment online separate cards with a limited budget, using two-factor authentication for accounts and for making payments. Well, returning to the story about the Android Trojan, you should not click on the links, even if they seem to be sent by a familiar person.
Disclaimer: The opinions expressed in this digest may not always coincide with the official position of Kaspersky Lab. Dear editors generally recommend to treat any opinions with healthy skepticism.
