Conference DEFCON 17. Laugh at your viruses! Part 2
- Transfer
Conference DEFCON 17. Laugh at your viruses! Part 1
Then you can load it into IDA and see that everything in the table of imported addresses looks fine, and we can follow the cross-references to set a pointer to the desired file. So we get exactly to the location of the dependent encryption code.
Thus, with just a few memory dump commands, we found the place where Coreflood hid. We disassembled, extracted and pasted the PE header, even without it, and got a fully restored address table in less than 20 seconds.
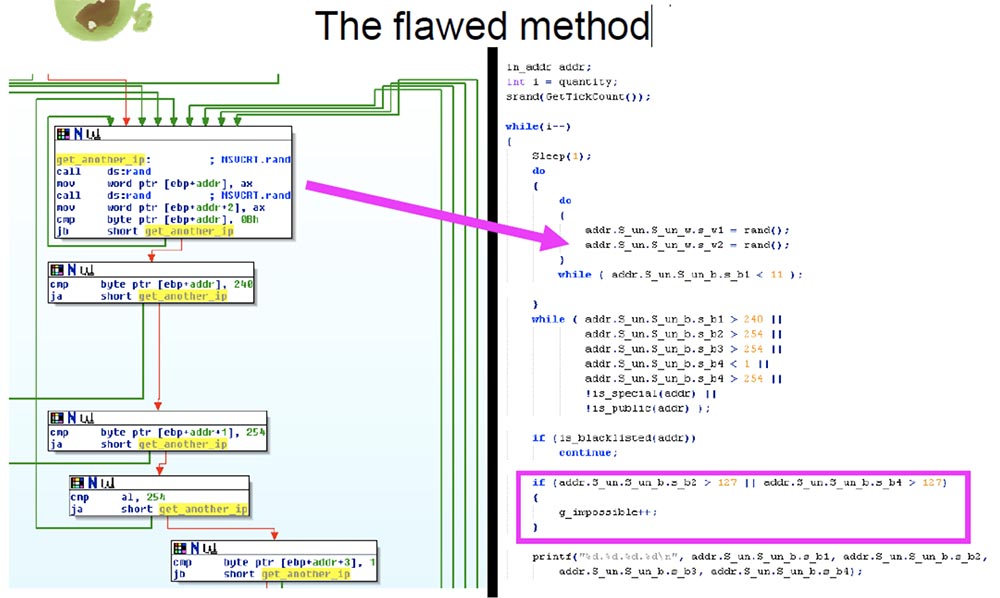
The next story is called “Honey, sorry for bothering you again - I have stung the internet!” This story tells that the defective IP generator Conficker.B scans only part of the Internet. Here we go back to the rand function. An important part of this function is the most recent instruction, which I marked with a green arrow - it performs any final value in EAX with a value of 7FFF. If you are not familiar with the principles of assembly and do not know what this instruction can do, here is a small demo about this.

We move the maximum value that EAX can contain into this registry and execute the final instruction. You can see that it “chops off” the upper half of the value and then subtracts 7FFF, which in the decimal system is converted to the number 32767. Apparently, the authors did not realize that this restriction that Windows starts does not return the whole number to the integer number . It "cuts off" it so that the value does not exceed 7FFF, so that one byte of 7F will never be greater than this value of 7F, that is, it will never be equal to 80 or something like that.
Further in the left part of the slide, which I called the “Vicious Method”, you see the code Conficker.B. Shown here is one rand call that initiates the first octet of an IP address, which is meant to be scanned after it returns from rand. The next rand system call initiates the third and fourth octets of the IP address, but because of the above, two of these octets will never be greater than 7F. Thus, most of the Internet will not be able to be scanned due to the fact that Conficker.B uses this algorithm.
In the right part of the slide is a part of the source code, which shows the work of the assembler. It is difficult to read on the screen, but this example is publicly available, and you can read it online if you are interested.
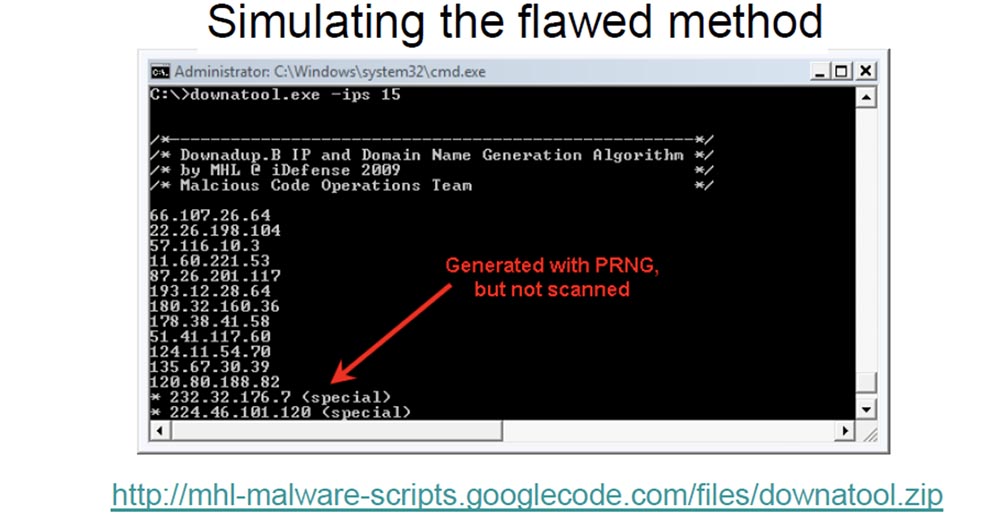
At the bottom of the next slide, entitled “Simulating the Perverse Method”, is a link to this tool. You also see that the IP address is generated from PRNG, but not scanned.
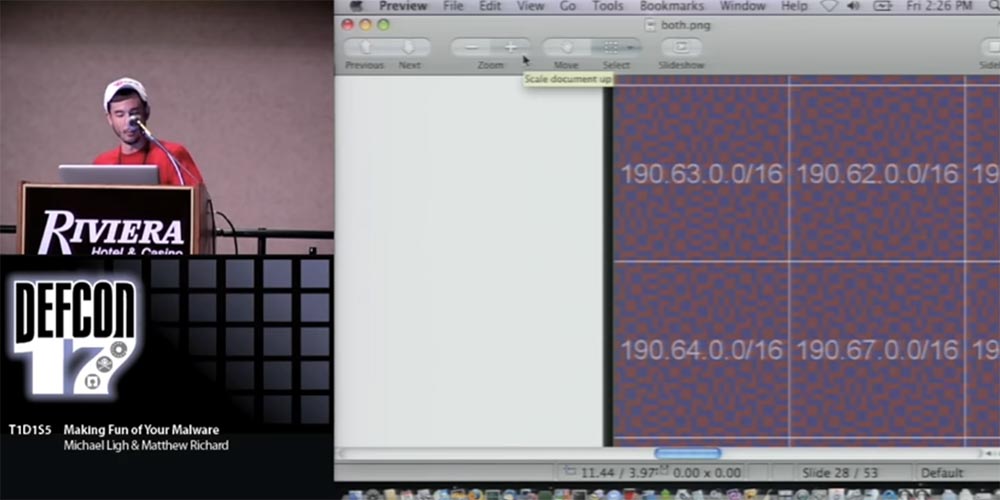
I want to say a big thank you to Brandon Enright, who made the graph on the next slide. This graph is called the “Hilbert curve,” and I’ll now enlarge the image so that you can see better on the screen. The blue color on the graph indicates the range of IP addresses that are not available for scanning by Conficker.B using this vicious algorithm. Dark red color indicates what can be scanned. You see that most parts of the graph are not dark red, but purple, and you will not see why this happens until you increase the corresponding rectangle.
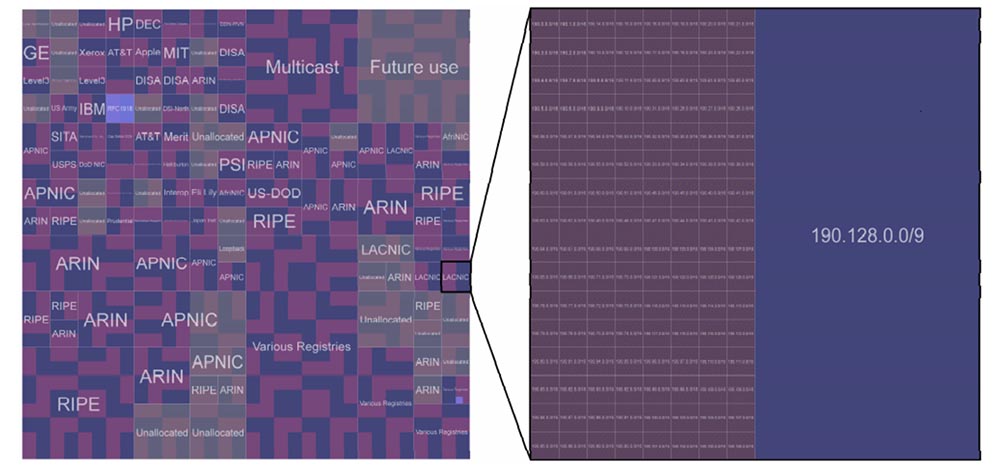
Even in this enlarged rectangle, in each block / 16, you see a lot of blue fragments that turn a dark red color into purple. These are the portions of addresses that Conficker.B is unable to scan.
This is quite interesting because many people believe that Conficker.B created “great minds”. Perhaps it is, but these minds were not aware of the limitations that rand () exists in Windows.
Matthew Richard: Let's go back to those guys who, as I said before, do not manage their viruses too well, so in cybercrime it is akin to the proverb “man is a wolf,” so these guys are not respected in their circles.
Let's talk about the hacker toolkit Neosploit, which “got” everyone. We can say that the motto of its developers was “Thank you for the cash, now it's time to run.” Neosploit is a set of tools for organizing web attacks, so the cybercrime guys will buy it and tune it against the guys on the server, hack the server, download codes, and so on.

The creators of Neosploit made a good investment by selling their instrument, but not allowing it to change, modify, or use its individual parts. The third version of this toolkit was released in April 2008, and most unique exploits are written in C, so this is not PHP or some kind of lame web application. Clients received a binary distribution with a set of CGI exploits.
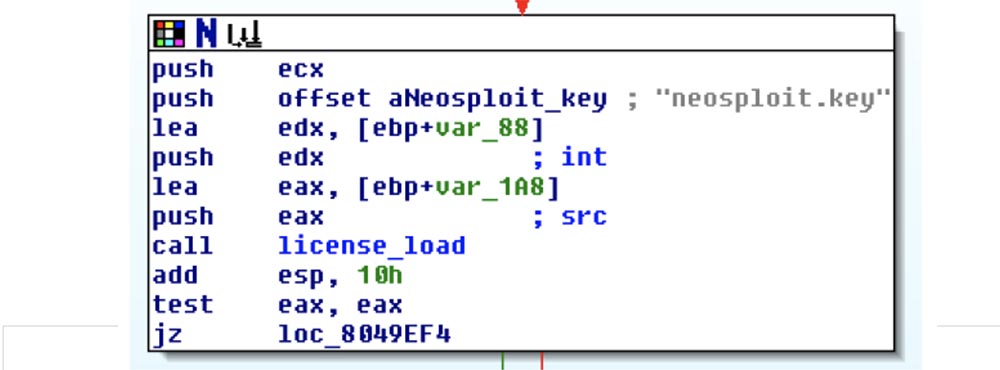
Neosploit has features that prevent clients from sharing or cutting exploits. To do this, all the exploits were presented in binary format, encrypted using XOR. The creators made it so that no one could cut, glue and create their own set of exploits based on Neosploit. There are 40-50-60 different types of web attacks, based on stolen and copied codes inserted into their own exploits, so the Neosploit guys turned out to be a little smarter by encrypting their exploits from the inside. In the screenshot you can see that they have a file with the key neosploit.key, so this is fully licensed software.
I have no doubt that they had a bunch of really good customers, on whom they made a lot of money. Their most famous customers were Torpig. I think you heard about the Mebroot rootkit, with which they compromised the system to create a botnet network. But the creators of Neosploit had many other customers. In May 2008, they released a fresh enhancement - the 3rd version of their toolkit. Customers were asked to make a prepayment of a package of exploits with all subsequent updates for $ 1000. Later, I’ll tell you more about this, for now I’ll notice that they were really worried about the pirates and were trying to protect their product from them as much as possible, so it was definitely a lot of fun.

Even the media wrote that these exploits are everywhere. So by itself, we will try to disassemble the code and show how Neosploit works.
The first fun thing they did after they vigorously unwound this set of exploits from April to July — this stopped its support from July 20, 2008. In the explanation that they just posted on their website, it was said: “Unfortunately , further product support is not feasible. We apologize for the inconvenience, but the business is a business, and the time spent on the project is not justified. We have tried to meet the requirements of our clients until the last months, but sometime the support had to stop. We have been with you for a year and a half and we hope that this was not the worst time for your business. Now we will not be near you, but, nevertheless, we wish your business to flourish for a very long time. ” In general, we received your money, you paid a subscription, so stay healthy!
However, they just joked and in August 2008 they returned again and released a completely new version 3.1, which they provided to their key customers, indicating that all other customers will receive an update after they pay for it. This update contains several new exploits for Adobe PDF, Shockwave Flash and Quicktime for Firefox.
Then they decided to be serious again and announced that they were actually stopping the release of updates, so everyone who made the prepayment for a subscription was screwed up.
So, let's move on to considering Neosploit, this pretty cool web-based attack kit. Since its developers fought against pirates and theft of exploits that could be copied and pasted into someone else's kits, they took each exploit and placed it in a CGI file, coding it in such a way that it was very difficult to get it out. Binary exploit files written in C were slightly different from PHP scripts.
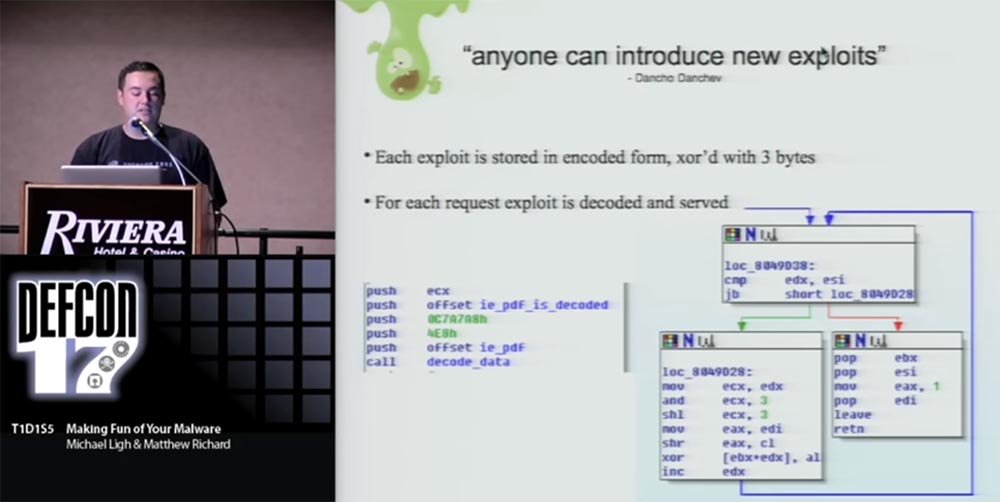
In the Neosploit blog, the phrase Dancho Danchev was posted that “anyone can create a new exploit”, but this is rather difficult. I decided to find out how difficult it is and started disassembling one of the exploits.
Each exploit was stored in encrypted form using a 3-byte XOR key. For each incoming request, the exploit was decrypted and made available to the user for work, and this cycle was constantly repeated.
So even if you could get through the memory, and removing the memory dump is still quite difficult, and getting all the exploits, still these buffers are cleared every time.
Fortunately, if you can copy and paste these exploits into the program you need, you can find the answer. It uses a very powerful decryption tool - IDA scripting. With it, you can comment or remove a dump of a certain area of memory, update exploits, it can be useful for working with malicious software that uses lines complicated by xor, base64, etc. I wrote an IDE script with which I tried to disassemble the captured memory dump of an encrypted exploit.

It goes through all the encrypted objects, searches for all calls to the decryption functions, captures the encrypted objects, decrypts them with XOR and then takes a dump. This is one way, but I think you could write your own script, an application that does the same. If you know how to add new exploits to Neosploit, then you can do something in this direction and of course, once you remove the dump, you will know the whole plaintext, you can “rip out” the instrumentation and resell it. New guys developing exploits just gave up because someone earned good money without worrying about their customers.
If anyone has heard of the great hip-hop philosopher Biggy Smalls from Notorius BIG, he knows his song called Ten crack commandments, “The Ten Commandments of Crack,” which contains great wisdom. If you are a drug dealer, then observe the 4 commandments: "Never sit on your own foolishness, which you are pushing." Probably the guy I called Peeper and who distributed his own malicious code never heard this song because I tested my product on myself.
His attack was as follows. He sent emails disguised as various government agencies and appealing to people by name: “Dear such-and-such, someone has filed a complaint with the Federal Trade Commission about your company, so click here to download the document, which details the essence” .
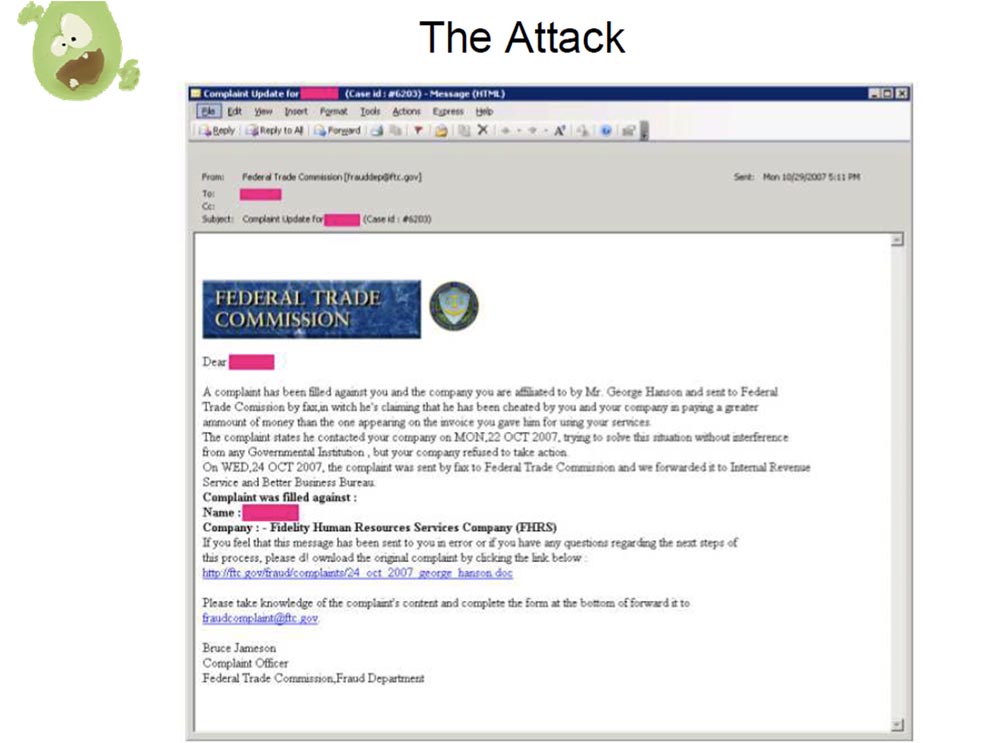
Then the user followed the link and tried to download this document, and it really was a Word document in .doc format. However, there was one very tricky feature. You had the opportunity to simply drag the executable files from the Word document and then rename them, but when you try to download the file, a message appears: “Microsoft Word detected a problem and the document could not be loaded. Please double click on the document icon to continue. ” Awesome idea!

Naturally, people clicked, they clicked 6 times to get this infected message, so this guy had a lot of victims. I liked this message: "They tried to deceive me, blah blah blah."
The next thing we found, tracking this guy, are the open directories of the Drop Directory, where he dumped the received information.
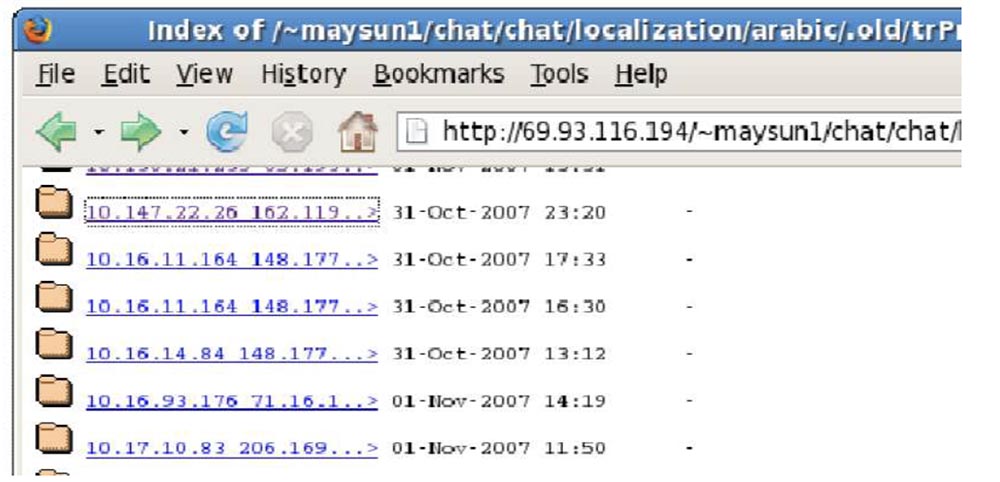
He may not have had his own tools for managing them or he thought that open directories are a good thing, but open directories are bad if you store a lot of information received from different people. Any server that he would have set up for his “landing” site had an open directory, and you could just go in there and view the lists of all its victims and each one individually.
In a sense, he was a good developer because he wrote quality code. But his disadvantage was that by addressing his code to the current server, he used his real IP address, and you would not last long using such things.
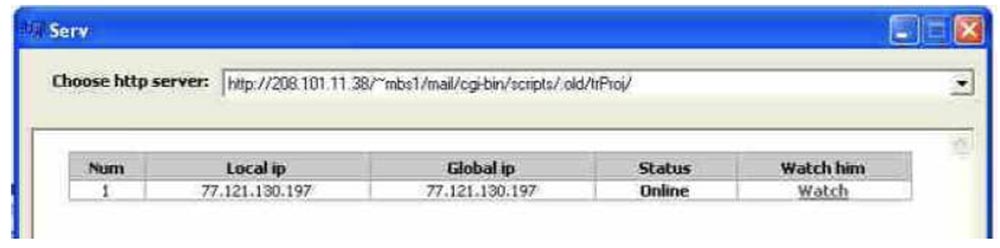
So in fact, he had a standard DSL modem that communicated from Ukraine, he tested all his code and malware, which has a good function called “watch me”, or “watch it”. This guy was involved in stealing banking information, but sometimes he just wanted to watch his victims to see what they were doing, so we called him Peeper, or “Observer.” He was not satisfied with the simple functionality of his software, he began to monitor himself. It looks rather strange, as if you opened VNC remote access windows on your own computer and looped them in to get smaller and smaller images. In fact, he did this many times, on many landing servers, in fact, it was very, very strange. So looking through these “landing” servers, one could say: “oh,
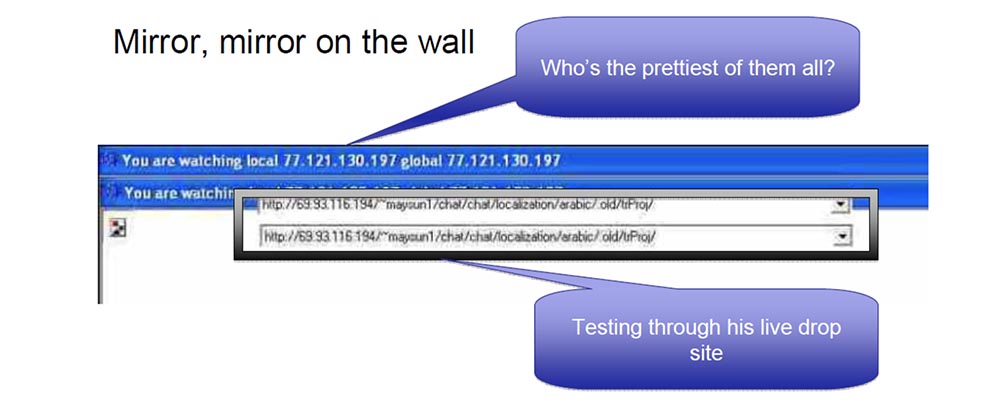
“My light, mirror, tell me, who is the kindest in the world”?
Most of all I liked what he did for himself. He used this “follow me” feature during code development. In fact, he wrote the code, watching himself, sending it all back to the command and control server. Thus, he gave the opportunity for the official to break through the back door, lay his face on the floor and confiscate his computer. In short, nothing helps to get rid of you, like the image of the source tree associated with your IP address.

The last piece of malware that we’ll look at will certainly interest people who are well acquainted with Internet Explorer 7. But don’t worry, Microsoft says that everything is under control, trust them!

So, Microsoft had a big problem with Internet Explorer 6, due to the fact that it was very easy to steal saved passwords from this browser. Usually you go to the site, you are asked if you want to save the password, a special form is called, you answer "yes", and it is saved in the registry. The problem with IE 6 was that if you log in as a user, you only need to make one CryptUnprotectData () system call to decrypt these passwords, which really do not have protection.
Therefore, malware running with the user's authority freely read these passwords and sent them to the attacker. Therefore, in IE 7, they installed a great “patch” - passwords were encrypted with a 128-bit key. Really no hackable solution!
If you look deeper, you can see the hash that is available on the site, I will explain this a little later, in which there is a binary file containing the username and password. I want to quote another great philosopher, John Travolta, from the Swordfish movie. My favorite passage is when he sits there and explains: "This cipher is so good that even I can't hack it." I think he meant 512-bit encryption, and he, the world's best cryptographer, why he was hired, says that even he cannot do it.
So, that's what Microsoft did. They encrypt the password, for which they will generate a 128-bit key based on the MD5 hash of the site for which they store this password. This seems pretty reasonable, so if you go to www.bank.com/login.spthey will take this string, make all the letters lowercase, then convert them to large characters and use the MD5 algorithm, turning this string into a key that will be used to encrypt the password in the registry for the user name.
Then, when you visit this site for which there is a saved password, they do the opposite: IE normalizes the URL, recodes the string and looks in the registry to see if there are any values stored for you. In detail this happens as follows:
This seems pretty reasonable, but if you think about it, there is a slight problem here. In fact, there is too little entropy here, and a hacker can easily handle it. This is not much more complicated than encrypting passwords in IE 6.
Hacking it is quite simple. To save the password, the user must visit the site, which can then be easily found in index.dat or in the “TypedURLS” registry key section. If we consider only the United States, then there are about 15,000 sites of banks and credit unions, and you can easily find them. You know the sites for which you want to find passwords, and each such site has login pages, so it is easy enough to collect a whole collection of keys. As you can see, the protection here is clearly insufficient.
Of course, if you're a bad guy, you probably know a lot of sites that need passwords: Facebook, Myspace or Twitter, or others with a login page, so you can just figure out such sites. You can use the Alexa service, which keeps a list of the most popular sites, collecting statistics on their attendance. The keys are really easy to decipher, you can make something like a Rainbow Table “rainbow table” based on these common sources, and then you will have all the keys for decrypting passwords.
For the bad guys, it's pretty simple, so the moral of the IE 7 story is: it's not as good as the developers try to convince.
Can you help in this situation? Honestly, no. Nobody dealt with this question properly. Michael and I looked at a whole bunch of applications, including Mozilla Firefox, and saw that almost everyone tried to write a password retrieval tool for them. Indeed, there is little that can protect you if you store passwords for websites, you probably know such a thing as the tool “Remember my password”. Almost all passwords can be extracted one way or another. Compared to other browsers, Firefox and IE 7 provide stronger protection, since you actually have to enter the password first, but even if you just entered the password without saving it, the guy may already be able to steal it.
Avoid hacking, do not save valuable passwords, if you are launching a site with a login form, do not allow users to save their data.
Finally, we will look at a Trojan called Laqma. This is a typical Trojan that steals confidential data and other pieces of information that it takes from cookies. It loads its cookies in some strange way, due to which it does not undergo data sanitization, the user becomes infected, the trojan steals the values of its cookies and sends it to command and control.
This trojan is loaded with a file that can have any name. If you emulate a trojan using your own code, you can specify any name, such as another PHP file, so you can simply upload your own PHP script to the bad guy's website, exploiting this vulnerability — the ability to download arbitrary files.
And now I give the floor to Michael for the last demo.
Michael Lai:I'm sorry this is not funny, but it is worth seeing because it is cool. Now I will try to present this demo in a convenient presentation format for you to see. The presentation is based on the Laqma rootkit that we installed. Imagine that you are investigating incidents or reverse engineering malware and encounter a computer infected with Laqma or any rootkit that throws hooks into the system service manager table. First of all, you will try to figure out which functions are hooked on the SSDT, and then you can try to restore a working kernel module if you test it with IDA or something like that.
So it's great that I wrote a plugin for the Volatility command line tool that automates all these tasks. I have already dumped the memory of a computer infected with Laqma, so I just use the SSDT plugin that Brendon Dolan Gavit developed, this is a terrific plugin. By default, it simply prints all the records from the SSDT, the module and the address pointed to by the SSDT function, and does this for all four SSDTs.

All these entries must be legally specified inside the TOS kernel, for the second table they must be specified inside win32k, and for the third and fourth tables this location is random, because it is not set by default. Therefore, I am going to use the Brandon Dolan Gavit SSDT script and just install a filter on the command line, so I will ignore everything that is specified inside the TOS kernel and inside win32k.
The result is four functions shown at the bottom of the screen that indicate the name of the module, the domain name, drv, .sys, lists the key values of hidden registry entries for hidden processes and information on system queries. As I said, this is the first stage. Next, you need to find out which SSDT functions are hooked. The next stage consists in removing the module dump and searching for registry keys and files hidden there.
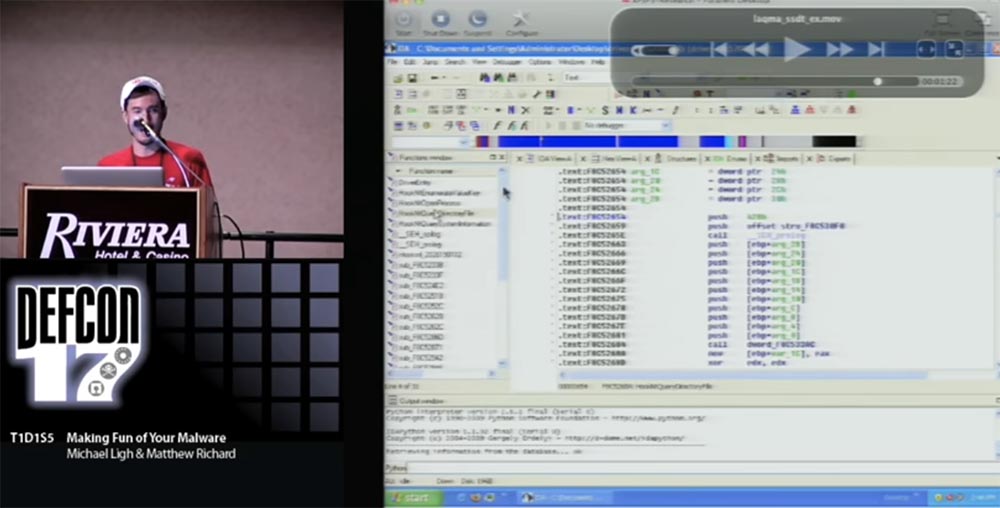
This process is a bit automated using the SSDT plugin. You can see how BSOD flashed on the screen, it worked IDA command line program. As a result of automatic processing, an IDB is created, this is some more automation, as a result of which IDB functions are labeled, corresponding to the "hooked" functions of SSDT.
Thus, using one small step, we learned what SSDT functions were associated with the dump that owns the IDB module created, and were able to call them in order to know exactly where to look in the IDB when I start to do reverse engineering.
Hope you had fun!
Thank you for staying with us. Do you like our articles? Want to see more interesting materials? Support us by placing an order or recommending to friends, 30% discount for Habr's users on a unique analogue of the entry-level servers that we invented for you: The whole truth about VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps from $ 20 or how to share the server? (Options are available with RAID1 and RAID10, up to 24 cores and up to 40GB DDR4).
VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps until December for free if you pay for a period of six months, you can order here .
Dell R730xd 2 times cheaper? Only we have 2 x Intel Dodeca-Core Xeon E5-2650v4 128GB DDR4 6x480GB SSD 1Gbps 100 TV from $ 249in the Netherlands and the USA! Read about How to build an infrastructure building. class c using servers Dell R730xd E5-2650 v4 worth 9000 euros for a penny?
Then you can load it into IDA and see that everything in the table of imported addresses looks fine, and we can follow the cross-references to set a pointer to the desired file. So we get exactly to the location of the dependent encryption code.

Thus, with just a few memory dump commands, we found the place where Coreflood hid. We disassembled, extracted and pasted the PE header, even without it, and got a fully restored address table in less than 20 seconds.
The next story is called “Honey, sorry for bothering you again - I have stung the internet!” This story tells that the defective IP generator Conficker.B scans only part of the Internet. Here we go back to the rand function. An important part of this function is the most recent instruction, which I marked with a green arrow - it performs any final value in EAX with a value of 7FFF. If you are not familiar with the principles of assembly and do not know what this instruction can do, here is a small demo about this.

We move the maximum value that EAX can contain into this registry and execute the final instruction. You can see that it “chops off” the upper half of the value and then subtracts 7FFF, which in the decimal system is converted to the number 32767. Apparently, the authors did not realize that this restriction that Windows starts does not return the whole number to the integer number . It "cuts off" it so that the value does not exceed 7FFF, so that one byte of 7F will never be greater than this value of 7F, that is, it will never be equal to 80 or something like that.
Further in the left part of the slide, which I called the “Vicious Method”, you see the code Conficker.B. Shown here is one rand call that initiates the first octet of an IP address, which is meant to be scanned after it returns from rand. The next rand system call initiates the third and fourth octets of the IP address, but because of the above, two of these octets will never be greater than 7F. Thus, most of the Internet will not be able to be scanned due to the fact that Conficker.B uses this algorithm.
In the right part of the slide is a part of the source code, which shows the work of the assembler. It is difficult to read on the screen, but this example is publicly available, and you can read it online if you are interested.

At the bottom of the next slide, entitled “Simulating the Perverse Method”, is a link to this tool. You also see that the IP address is generated from PRNG, but not scanned.

I want to say a big thank you to Brandon Enright, who made the graph on the next slide. This graph is called the “Hilbert curve,” and I’ll now enlarge the image so that you can see better on the screen. The blue color on the graph indicates the range of IP addresses that are not available for scanning by Conficker.B using this vicious algorithm. Dark red color indicates what can be scanned. You see that most parts of the graph are not dark red, but purple, and you will not see why this happens until you increase the corresponding rectangle.

Even in this enlarged rectangle, in each block / 16, you see a lot of blue fragments that turn a dark red color into purple. These are the portions of addresses that Conficker.B is unable to scan.

This is quite interesting because many people believe that Conficker.B created “great minds”. Perhaps it is, but these minds were not aware of the limitations that rand () exists in Windows.
Matthew Richard: Let's go back to those guys who, as I said before, do not manage their viruses too well, so in cybercrime it is akin to the proverb “man is a wolf,” so these guys are not respected in their circles.
Let's talk about the hacker toolkit Neosploit, which “got” everyone. We can say that the motto of its developers was “Thank you for the cash, now it's time to run.” Neosploit is a set of tools for organizing web attacks, so the cybercrime guys will buy it and tune it against the guys on the server, hack the server, download codes, and so on.

The creators of Neosploit made a good investment by selling their instrument, but not allowing it to change, modify, or use its individual parts. The third version of this toolkit was released in April 2008, and most unique exploits are written in C, so this is not PHP or some kind of lame web application. Clients received a binary distribution with a set of CGI exploits.
Neosploit has features that prevent clients from sharing or cutting exploits. To do this, all the exploits were presented in binary format, encrypted using XOR. The creators made it so that no one could cut, glue and create their own set of exploits based on Neosploit. There are 40-50-60 different types of web attacks, based on stolen and copied codes inserted into their own exploits, so the Neosploit guys turned out to be a little smarter by encrypting their exploits from the inside. In the screenshot you can see that they have a file with the key neosploit.key, so this is fully licensed software.

I have no doubt that they had a bunch of really good customers, on whom they made a lot of money. Their most famous customers were Torpig. I think you heard about the Mebroot rootkit, with which they compromised the system to create a botnet network. But the creators of Neosploit had many other customers. In May 2008, they released a fresh enhancement - the 3rd version of their toolkit. Customers were asked to make a prepayment of a package of exploits with all subsequent updates for $ 1000. Later, I’ll tell you more about this, for now I’ll notice that they were really worried about the pirates and were trying to protect their product from them as much as possible, so it was definitely a lot of fun.

Even the media wrote that these exploits are everywhere. So by itself, we will try to disassemble the code and show how Neosploit works.
The first fun thing they did after they vigorously unwound this set of exploits from April to July — this stopped its support from July 20, 2008. In the explanation that they just posted on their website, it was said: “Unfortunately , further product support is not feasible. We apologize for the inconvenience, but the business is a business, and the time spent on the project is not justified. We have tried to meet the requirements of our clients until the last months, but sometime the support had to stop. We have been with you for a year and a half and we hope that this was not the worst time for your business. Now we will not be near you, but, nevertheless, we wish your business to flourish for a very long time. ” In general, we received your money, you paid a subscription, so stay healthy!
However, they just joked and in August 2008 they returned again and released a completely new version 3.1, which they provided to their key customers, indicating that all other customers will receive an update after they pay for it. This update contains several new exploits for Adobe PDF, Shockwave Flash and Quicktime for Firefox.
Then they decided to be serious again and announced that they were actually stopping the release of updates, so everyone who made the prepayment for a subscription was screwed up.
So, let's move on to considering Neosploit, this pretty cool web-based attack kit. Since its developers fought against pirates and theft of exploits that could be copied and pasted into someone else's kits, they took each exploit and placed it in a CGI file, coding it in such a way that it was very difficult to get it out. Binary exploit files written in C were slightly different from PHP scripts.

In the Neosploit blog, the phrase Dancho Danchev was posted that “anyone can create a new exploit”, but this is rather difficult. I decided to find out how difficult it is and started disassembling one of the exploits.
Each exploit was stored in encrypted form using a 3-byte XOR key. For each incoming request, the exploit was decrypted and made available to the user for work, and this cycle was constantly repeated.

So even if you could get through the memory, and removing the memory dump is still quite difficult, and getting all the exploits, still these buffers are cleared every time.
Fortunately, if you can copy and paste these exploits into the program you need, you can find the answer. It uses a very powerful decryption tool - IDA scripting. With it, you can comment or remove a dump of a certain area of memory, update exploits, it can be useful for working with malicious software that uses lines complicated by xor, base64, etc. I wrote an IDE script with which I tried to disassemble the captured memory dump of an encrypted exploit.

It goes through all the encrypted objects, searches for all calls to the decryption functions, captures the encrypted objects, decrypts them with XOR and then takes a dump. This is one way, but I think you could write your own script, an application that does the same. If you know how to add new exploits to Neosploit, then you can do something in this direction and of course, once you remove the dump, you will know the whole plaintext, you can “rip out” the instrumentation and resell it. New guys developing exploits just gave up because someone earned good money without worrying about their customers.
If anyone has heard of the great hip-hop philosopher Biggy Smalls from Notorius BIG, he knows his song called Ten crack commandments, “The Ten Commandments of Crack,” which contains great wisdom. If you are a drug dealer, then observe the 4 commandments: "Never sit on your own foolishness, which you are pushing." Probably the guy I called Peeper and who distributed his own malicious code never heard this song because I tested my product on myself.
His attack was as follows. He sent emails disguised as various government agencies and appealing to people by name: “Dear such-and-such, someone has filed a complaint with the Federal Trade Commission about your company, so click here to download the document, which details the essence” .

Then the user followed the link and tried to download this document, and it really was a Word document in .doc format. However, there was one very tricky feature. You had the opportunity to simply drag the executable files from the Word document and then rename them, but when you try to download the file, a message appears: “Microsoft Word detected a problem and the document could not be loaded. Please double click on the document icon to continue. ” Awesome idea!

Naturally, people clicked, they clicked 6 times to get this infected message, so this guy had a lot of victims. I liked this message: "They tried to deceive me, blah blah blah."
The next thing we found, tracking this guy, are the open directories of the Drop Directory, where he dumped the received information.

He may not have had his own tools for managing them or he thought that open directories are a good thing, but open directories are bad if you store a lot of information received from different people. Any server that he would have set up for his “landing” site had an open directory, and you could just go in there and view the lists of all its victims and each one individually.
In a sense, he was a good developer because he wrote quality code. But his disadvantage was that by addressing his code to the current server, he used his real IP address, and you would not last long using such things.

So in fact, he had a standard DSL modem that communicated from Ukraine, he tested all his code and malware, which has a good function called “watch me”, or “watch it”. This guy was involved in stealing banking information, but sometimes he just wanted to watch his victims to see what they were doing, so we called him Peeper, or “Observer.” He was not satisfied with the simple functionality of his software, he began to monitor himself. It looks rather strange, as if you opened VNC remote access windows on your own computer and looped them in to get smaller and smaller images. In fact, he did this many times, on many landing servers, in fact, it was very, very strange. So looking through these “landing” servers, one could say: “oh,

“My light, mirror, tell me, who is the kindest in the world”?
Most of all I liked what he did for himself. He used this “follow me” feature during code development. In fact, he wrote the code, watching himself, sending it all back to the command and control server. Thus, he gave the opportunity for the official to break through the back door, lay his face on the floor and confiscate his computer. In short, nothing helps to get rid of you, like the image of the source tree associated with your IP address.

The last piece of malware that we’ll look at will certainly interest people who are well acquainted with Internet Explorer 7. But don’t worry, Microsoft says that everything is under control, trust them!

So, Microsoft had a big problem with Internet Explorer 6, due to the fact that it was very easy to steal saved passwords from this browser. Usually you go to the site, you are asked if you want to save the password, a special form is called, you answer "yes", and it is saved in the registry. The problem with IE 6 was that if you log in as a user, you only need to make one CryptUnprotectData () system call to decrypt these passwords, which really do not have protection.
Therefore, malware running with the user's authority freely read these passwords and sent them to the attacker. Therefore, in IE 7, they installed a great “patch” - passwords were encrypted with a 128-bit key. Really no hackable solution!
If you look deeper, you can see the hash that is available on the site, I will explain this a little later, in which there is a binary file containing the username and password. I want to quote another great philosopher, John Travolta, from the Swordfish movie. My favorite passage is when he sits there and explains: "This cipher is so good that even I can't hack it." I think he meant 512-bit encryption, and he, the world's best cryptographer, why he was hired, says that even he cannot do it.
So, that's what Microsoft did. They encrypt the password, for which they will generate a 128-bit key based on the MD5 hash of the site for which they store this password. This seems pretty reasonable, so if you go to www.bank.com/login.spthey will take this string, make all the letters lowercase, then convert them to large characters and use the MD5 algorithm, turning this string into a key that will be used to encrypt the password in the registry for the user name.
Then, when you visit this site for which there is a saved password, they do the opposite: IE normalizes the URL, recodes the string and looks in the registry to see if there are any values stored for you. In detail this happens as follows:
- read the register hash for each URL in index.dat;
- URL is converted to lower case;
- GET parameters are reduced;
- URL is converted to large characters;
- if the hash of the URL value is equal to any value in the register, the data is decrypted using this URL.
This seems pretty reasonable, but if you think about it, there is a slight problem here. In fact, there is too little entropy here, and a hacker can easily handle it. This is not much more complicated than encrypting passwords in IE 6.
Hacking it is quite simple. To save the password, the user must visit the site, which can then be easily found in index.dat or in the “TypedURLS” registry key section. If we consider only the United States, then there are about 15,000 sites of banks and credit unions, and you can easily find them. You know the sites for which you want to find passwords, and each such site has login pages, so it is easy enough to collect a whole collection of keys. As you can see, the protection here is clearly insufficient.
Of course, if you're a bad guy, you probably know a lot of sites that need passwords: Facebook, Myspace or Twitter, or others with a login page, so you can just figure out such sites. You can use the Alexa service, which keeps a list of the most popular sites, collecting statistics on their attendance. The keys are really easy to decipher, you can make something like a Rainbow Table “rainbow table” based on these common sources, and then you will have all the keys for decrypting passwords.
For the bad guys, it's pretty simple, so the moral of the IE 7 story is: it's not as good as the developers try to convince.
Can you help in this situation? Honestly, no. Nobody dealt with this question properly. Michael and I looked at a whole bunch of applications, including Mozilla Firefox, and saw that almost everyone tried to write a password retrieval tool for them. Indeed, there is little that can protect you if you store passwords for websites, you probably know such a thing as the tool “Remember my password”. Almost all passwords can be extracted one way or another. Compared to other browsers, Firefox and IE 7 provide stronger protection, since you actually have to enter the password first, but even if you just entered the password without saving it, the guy may already be able to steal it.
Avoid hacking, do not save valuable passwords, if you are launching a site with a login form, do not allow users to save their data.
Finally, we will look at a Trojan called Laqma. This is a typical Trojan that steals confidential data and other pieces of information that it takes from cookies. It loads its cookies in some strange way, due to which it does not undergo data sanitization, the user becomes infected, the trojan steals the values of its cookies and sends it to command and control.

This trojan is loaded with a file that can have any name. If you emulate a trojan using your own code, you can specify any name, such as another PHP file, so you can simply upload your own PHP script to the bad guy's website, exploiting this vulnerability — the ability to download arbitrary files.
And now I give the floor to Michael for the last demo.
Michael Lai:I'm sorry this is not funny, but it is worth seeing because it is cool. Now I will try to present this demo in a convenient presentation format for you to see. The presentation is based on the Laqma rootkit that we installed. Imagine that you are investigating incidents or reverse engineering malware and encounter a computer infected with Laqma or any rootkit that throws hooks into the system service manager table. First of all, you will try to figure out which functions are hooked on the SSDT, and then you can try to restore a working kernel module if you test it with IDA or something like that.
So it's great that I wrote a plugin for the Volatility command line tool that automates all these tasks. I have already dumped the memory of a computer infected with Laqma, so I just use the SSDT plugin that Brendon Dolan Gavit developed, this is a terrific plugin. By default, it simply prints all the records from the SSDT, the module and the address pointed to by the SSDT function, and does this for all four SSDTs.

All these entries must be legally specified inside the TOS kernel, for the second table they must be specified inside win32k, and for the third and fourth tables this location is random, because it is not set by default. Therefore, I am going to use the Brandon Dolan Gavit SSDT script and just install a filter on the command line, so I will ignore everything that is specified inside the TOS kernel and inside win32k.
The result is four functions shown at the bottom of the screen that indicate the name of the module, the domain name, drv, .sys, lists the key values of hidden registry entries for hidden processes and information on system queries. As I said, this is the first stage. Next, you need to find out which SSDT functions are hooked. The next stage consists in removing the module dump and searching for registry keys and files hidden there.

This process is a bit automated using the SSDT plugin. You can see how BSOD flashed on the screen, it worked IDA command line program. As a result of automatic processing, an IDB is created, this is some more automation, as a result of which IDB functions are labeled, corresponding to the "hooked" functions of SSDT.
Thus, using one small step, we learned what SSDT functions were associated with the dump that owns the IDB module created, and were able to call them in order to know exactly where to look in the IDB when I start to do reverse engineering.
Hope you had fun!
Thank you for staying with us. Do you like our articles? Want to see more interesting materials? Support us by placing an order or recommending to friends, 30% discount for Habr's users on a unique analogue of the entry-level servers that we invented for you: The whole truth about VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps from $ 20 or how to share the server? (Options are available with RAID1 and RAID10, up to 24 cores and up to 40GB DDR4).
VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps until December for free if you pay for a period of six months, you can order here .
Dell R730xd 2 times cheaper? Only we have 2 x Intel Dodeca-Core Xeon E5-2650v4 128GB DDR4 6x480GB SSD 1Gbps 100 TV from $ 249in the Netherlands and the USA! Read about How to build an infrastructure building. class c using servers Dell R730xd E5-2650 v4 worth 9000 euros for a penny?
