Loyalty system or how to live for free
Good day, habrovchane. In connection with the big panic of the previous article I will present you the second version. It's all simple, without snot. Loyalty system - one big hole. After some experiments, we came to the conclusion that a large number of sites that use such a system are completely devoid of logic when trying to use it.

Of course, someone could introduce at least a simple, but protection, and someone imagines the Internet in this form:

In general, many hacker attacks occur almost in this form. This is only in the movies you will be shown a bunch of gadgets of the future, the functionality of which does not make sense in the present.
Let's get down to business. For example, I will take several systems where there may be a massive karzh.
Let's start with OBI .
I will say right away that for me it has been little studied. Their vague rules about using bonuses put me in different doubts. First, they have several bonus programs. One of them can be paid only in three cities of Russia, on the other - in all. At the same time, bonuses do not apply to everything, but only up to 50% of the value of the goods. But at half the price to build a house is already good.
In general, OBI also has an application where you can log in our card and pay by generating a barcode.
Go to the registration page with a faint touch of a magic wand:

We get on the registration form isnot our card:
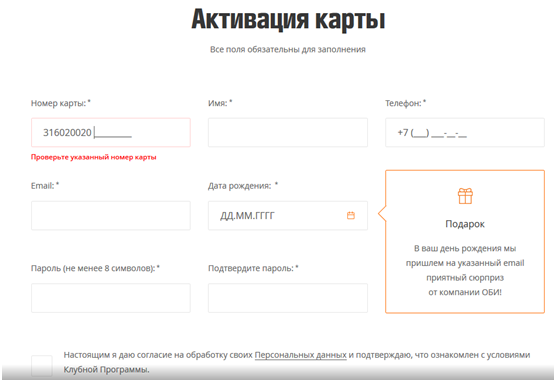
Well, fill it. By the way, here the system of calculating cards is the same as in the "Crossroads". In order to clearly express - Algorithm Moon . I filled out all the data, indicated a random card number. In the process through the sniffer caught the registration request.
I repeated it several hundred times in a cycle. There were no errors. The site is quite workable to process my requests and gave an answer in json:
The variable cardnum was the following text, which translated fromGreek Unicode means -
It is interesting that for all my requests from one IP there was no blocking. Moreover, the session lives for a very long time. Checked after a day - the answer was. Could at least cookie reset, enter the captcha, and then a solid "feyspalm." Write software is not difficult, only he will fall under the
Criminal Code. RF. v.273 , and this is already dangerous!
Well, the house we built. It would be necessary to fill our car and ride around the city. I could give an example here with the most popular gas stations, but in view of some considerations I will not do that. The system is the same for everyone, but the approach to it is different, so I will demonstrate it at the simplest, little-known gas station.
AZS-ETALON.RU. Attracted my attention to what is in my city. The principle of operation is similar - there is a loyalty card; there is a site where we register the card; There is an application through authorization in which you can pay at the checkout. Well, it's funny at all.
Moving to the card registration form - lk.azs-etalon.ru/registration.php
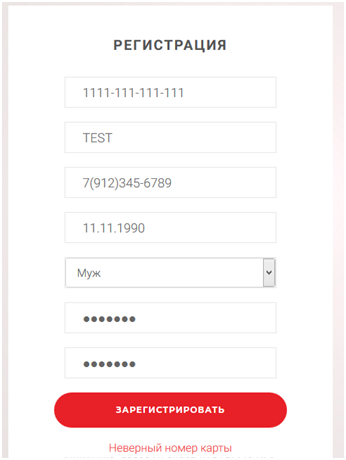
Fill in any data, click"Hack", "Register." We get the answer
- Automate?
- izi.
We catch the package for registration. We get the following
HTTP HEADERS:
POST-DATA:
We bring in a convenient type, we adjust under CURL, we hammer in a cycle and we put in a stream. The site will issue:German CP1251 -
There is no captcha, IP blocking for a large number of requests is not, there is not even a primary check for data entry by the client. Oh, okay. And so come down.
Let's go through one more beast. It is much larger than others, but still vulnerable.
Ribbon ... Just - TAPE
Go to the hetetepes lk.lenta.com/authentication/login/activate-card:
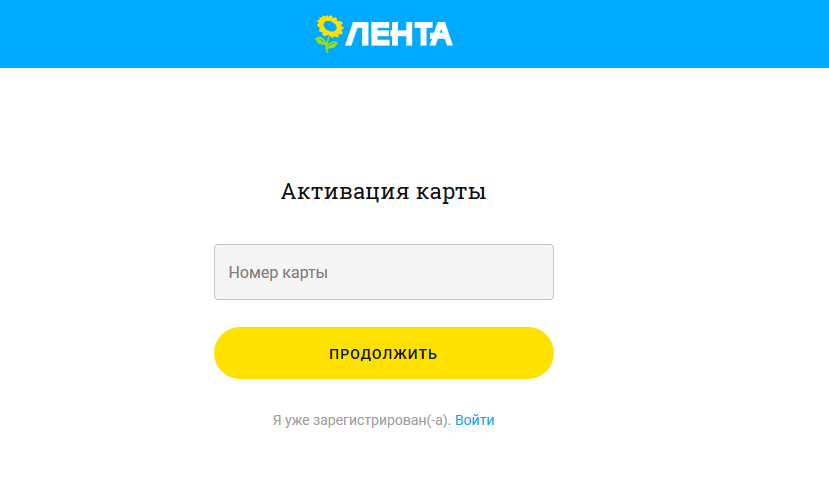
We assume that it was a pre-valid, non-activated card. We are asked to enter a phone number.
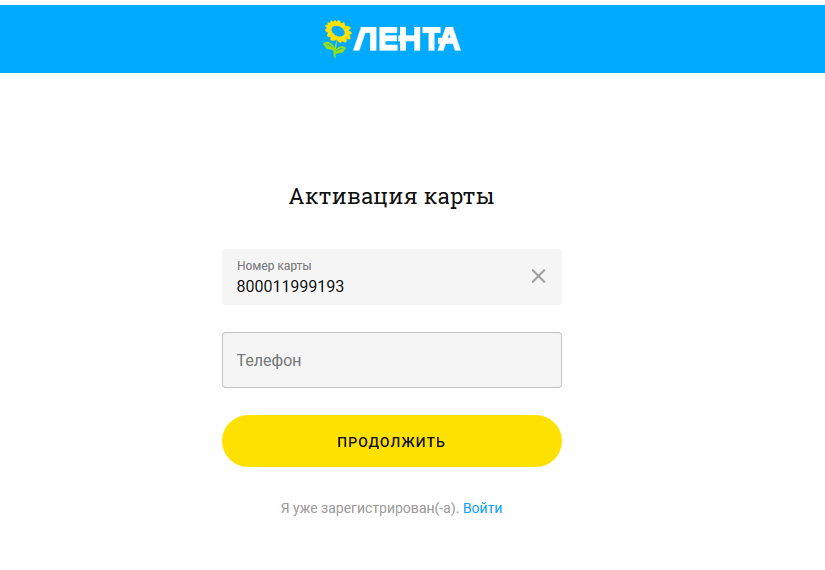
Well, we enter our mobile phone , then the rest of the data, including the password. All we are in the dashboard.
Here, as if everything is similar to previous systems. It is only important to catch the necessary requests, then repeat them in the right sequence.
But empirically some bad vulnerabilities were found. When you enter the wrong confirmation code - what was? Nothing, we were not allowed in the LC. This is logical guys.
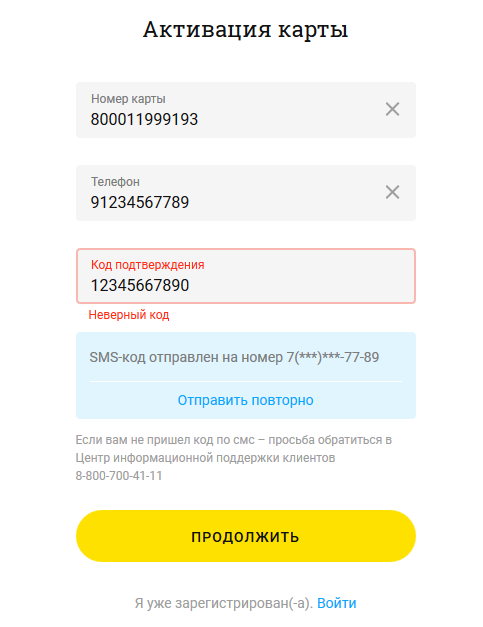
But by experiment, the following was verified! Were captured requests for confirmation code, in which all the parameters were in full view:
I will not chew on how I exploited this vulnerability, but I will say it briefly. With it, you can simply omit the code and we will always get into the LC without confirming the number. This means that we can indicate any number!
( With the support of the TAPE, I'm currently trying to contact )
Why all this? Let's summarize.
There are a lot of loyalty services. You can endlessly search for them and "brutal" points. If I tell you, is it possible for these points to also fly a plane?
In "Aeroflot" and "S7"there is also a bonus system. Miles are points. We can earn them from, for example, partners. Aeroflot, by the way, has about 2 thousand of them. Including, almost all top supermarkets, including our notorious X5 Retail Group. You can redeem points for miles directly in the LC of the same “Crossroads”. Well, and so almost all other services. By the way, this fact of stealing miles from the airline is officially fixed. A resounding business, not without victims.
In the end, things are not as simple as they seem. There are people who live off these points. Well, if these balls formally belong to you, then someone is sitting on your neck. Kulkhatskers can eat, dress, ride cars, fly around cities, and much more.
PS: Thank you for having several security officers from “X5” at once .contacted me. With one, there was more discussion about “whose scores are customers or Crossroads after all” than the issue of system security. But, I think they will fix it, since the whole of the Security Council is already aware. Promptly, then. They should pay tribute. The main thing is to fix it.
Well, here's a poll.

Of course, someone could introduce at least a simple, but protection, and someone imagines the Internet in this form:

In general, many hacker attacks occur almost in this form. This is only in the movies you will be shown a bunch of gadgets of the future, the functionality of which does not make sense in the present.
Let's get down to business. For example, I will take several systems where there may be a massive karzh.
Let's start with OBI .
I will say right away that for me it has been little studied. Their vague rules about using bonuses put me in different doubts. First, they have several bonus programs. One of them can be paid only in three cities of Russia, on the other - in all. At the same time, bonuses do not apply to everything, but only up to 50% of the value of the goods. But at half the price to build a house is already good.
In general, OBI also has an application where you can log in our card and pay by generating a barcode.
Go to the registration page with a faint touch of a magic wand:

We get on the registration form is

Well, fill it. By the way, here the system of calculating cards is the same as in the "Crossroads". In order to clearly express - Algorithm Moon . I filled out all the data, indicated a random card number. In the process through the sniffer caught the registration request.
I repeated it several hundred times in a cycle. There were no errors. The site is quite workable to process my requests and gave an answer in json:
"data":{"registration":null},"errors":[{"message":"\u041e\u0448\u0438\u0431\u043a\u0430 \u043f\u0440\u0438 \u0437\u0430\u043f\u043e\u043b\u043d\u0435\u043d\u0438\u0438 \u0444\u043e\u0440\u043c\u044b.","type":"validation","locations":{"path":"\/work\/obiclub.ru\/app\/GraphQL\/Mutation\/Frontend\/RegistrationMutation.php","line":109},"safe":true,"validation":{"cardnum":["\u041d\u0435\u043f\u0440\u0430\u0432\u0438\u043b\u044c\u043d\u044b\u0439 \u043d\u043e\u043c\u0435\u0440 \u043a\u0430\u0440\u0442\u044b. \u041f\u0440\u043e\u0432\u0435\u0440\u044c\u0442\u0435 \u043a\u043e\u0440\u0440\u0435\u043a\u0442\u043d\u043e\u0441\u0442\u044c \u0432\u0432\u0435\u0434\u0435\u043d\u043d\u044b\u0445 \u0434\u0430\u043d\u043d\u044b\u0445."]}}]}The variable cardnum was the following text, which translated from
“Invalid card number. Check the correctness of the entered data »
It is interesting that for all my requests from one IP there was no blocking. Moreover, the session lives for a very long time. Checked after a day - the answer was. Could at least cookie reset, enter the captcha, and then a solid "feyspalm." Write software is not difficult, only he will fall under the
Criminal Code. RF. v.273 , and this is already dangerous!
Well, the house we built. It would be necessary to fill our car and ride around the city. I could give an example here with the most popular gas stations, but in view of some considerations I will not do that. The system is the same for everyone, but the approach to it is different, so I will demonstrate it at the simplest, little-known gas station.
AZS-ETALON.RU. Attracted my attention to what is in my city. The principle of operation is similar - there is a loyalty card; there is a site where we register the card; There is an application through authorization in which you can pay at the checkout. Well, it's funny at all.
Moving to the card registration form - lk.azs-etalon.ru/registration.php

Fill in any data, click
"Invalid card number"This means that we will enter the next number on the account, and so on, until we find free fuel for our four-wheel friend.
- Automate?
- izi.
We catch the package for registration. We get the following
HTTP HEADERS:
Spoiler header
Host: lk.azs-etalon.ru
User-Agent: Mozilla/5.0 (Windows NT 6.3; WOW64; rv:41.0) Gecko/20100101 Firefox/41.0
Accept: */*
Accept-Language: ru-RU,ru;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
X-Requested-With: XMLHttpRequest
Referer: lk.azs-etalon.ru/registration.php
Content-Length: 174
Cookie: _ym_uid=10265171001178589; _ym_d=1214095619; _ym_visorc191282814=w; _ym_isad=2; PHPSESSID=u0vp19oks8iman1hi8m8j1n105
Connection: keep-alive
Pragma: no-cache
Cache-Control: no-cache
If-Modified-Since: *
User-Agent: Mozilla/5.0 (Windows NT 6.3; WOW64; rv:41.0) Gecko/20100101 Firefox/41.0
Accept: */*
Accept-Language: ru-RU,ru;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
X-Requested-With: XMLHttpRequest
Referer: lk.azs-etalon.ru/registration.php
Content-Length: 174
Cookie: _ym_uid=10265171001178589; _ym_d=1214095619; _ym_visorc191282814=w; _ym_isad=2; PHPSESSID=u0vp19oks8iman1hi8m8j1n105
Connection: keep-alive
Pragma: no-cache
Cache-Control: no-cache
If-Modified-Since: *
POST-DATA:
Spoiler header
card=1111-114-089-111&fio=%D0%90%D0%9E%D0%92%D0%A0%D0%90%D0%9B%D0%9E%D0%92%D0%90%D0%A0%D0%BB%D0%BE%D1%80&phone=7(912)345-6789&date=11.11.1990&sex=1&pass=123321q&pass2=123321q
We bring in a convenient type, we adjust under CURL, we hammer in a cycle and we put in a stream. The site will issue:
"НеверРС‹ Р№ номеркР° СЂС‚С ‹»that in
"Invalid card number"We set a condition for the appearance of another answer and find the “buzz” . The simplest brute is ready.
There is no captcha, IP blocking for a large number of requests is not, there is not even a primary check for data entry by the client. Oh, okay. And so come down.
Let's go through one more beast. It is much larger than others, but still vulnerable.
Ribbon ... Just - TAPE
Go to the hetetepes lk.lenta.com/authentication/login/activate-card:

We assume that it was a pre-valid, non-activated card. We are asked to enter a phone number.

Well, we enter our mobile phone , then the rest of the data, including the password. All we are in the dashboard.
Here, as if everything is similar to previous systems. It is only important to catch the necessary requests, then repeat them in the right sequence.
But empirically some bad vulnerabilities were found. When you enter the wrong confirmation code - what was? Nothing, we were not allowed in the LC. This is logical guys.

But by experiment, the following was verified! Were captured requests for confirmation code, in which all the parameters were in full view:
{"Code": "12345667890", "card": "800011999193", "phone": "91234567789"}
I will not chew on how I exploited this vulnerability, but I will say it briefly. With it, you can simply omit the code and we will always get into the LC without confirming the number. This means that we can indicate any number!
( With the support of the TAPE, I'm currently trying to contact )
Why all this? Let's summarize.
There are a lot of loyalty services. You can endlessly search for them and "brutal" points. If I tell you, is it possible for these points to also fly a plane?
In "Aeroflot" and "S7"there is also a bonus system. Miles are points. We can earn them from, for example, partners. Aeroflot, by the way, has about 2 thousand of them. Including, almost all top supermarkets, including our notorious X5 Retail Group. You can redeem points for miles directly in the LC of the same “Crossroads”. Well, and so almost all other services. By the way, this fact of stealing miles from the airline is officially fixed. A resounding business, not without victims.
In the end, things are not as simple as they seem. There are people who live off these points. Well, if these balls formally belong to you, then someone is sitting on your neck. Kulkhatskers can eat, dress, ride cars, fly around cities, and much more.
PS: Thank you for having several security officers from “X5” at once .contacted me. With one, there was more discussion about “whose scores are customers or Crossroads after all” than the issue of system security. But, I think they will fix it, since the whole of the Security Council is already aware. Promptly, then. They should pay tribute. The main thing is to fix it.
Well, here's a poll.
Only registered users can participate in the survey. Sign in , please.
