Memo on the types of phishing
My nephew and I decided to do our bit to counter phishing and prepared a memo. Distributed free of charge. You can download it and, having printed it, hang it in your office; post in social networks, add to booklet or book.
Here is the memo:
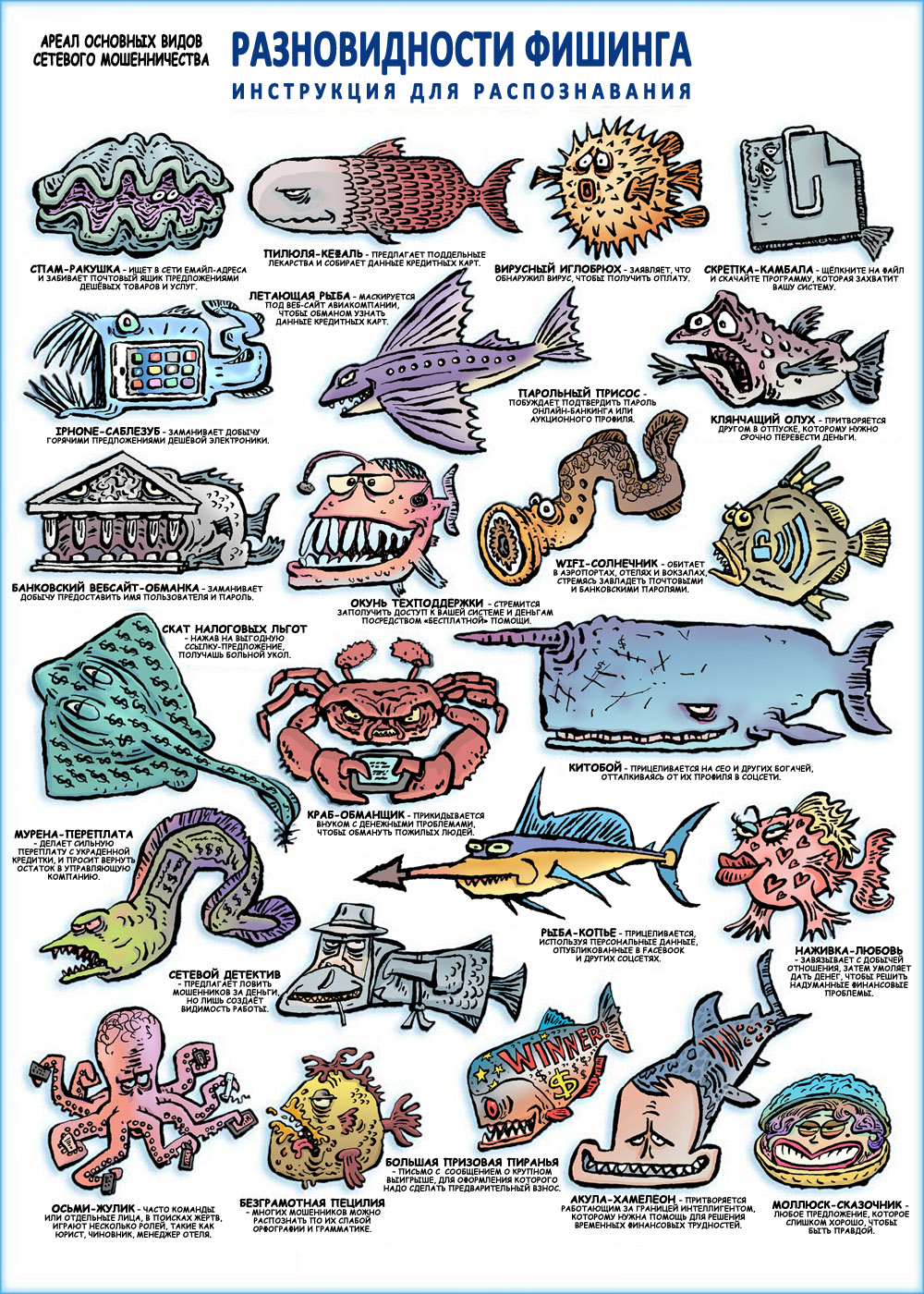
And now the explanation why phishing is still relevant, and why it will remain so in the future.
Phishing and the inevitable "click"
In the 2013 Verizon report, the following figures are given. If a phishing email is sent to six recipients, the probability that at least one of the recipients will click on the malicious link or open the malicious attachment is 80%. For 10 recipients, this probability increases to 90%, and for 20 recipients - to almost 100%.
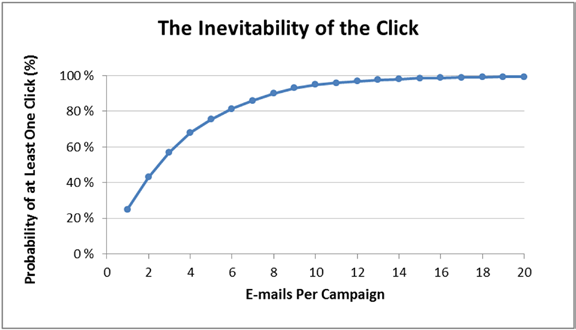
To send several thousand or even millions of phishing emails to employees of a large enterprise is a trivial task for a villain. And even if the security system blocks 95% of them, some of the phishing emails will still reach their potential victim. And some of these potential victims are sure to realize their potential (i.e., they will click on a malicious link or open a malicious attachment), in accordance with the figures just above (from Verizon). As a result, the villain will be able to crack at least one workplace, and so on. prepare yourself a foothold for cyber attack.
The progression of the complication of cyber attack and cyber defense
For each remedy, the potential villain has a special utility, technique, or procedure - allowing this particular remedy to be overcome. The picture (taken from the book “Enterprise Cybersecurity: How to Build a Successful Cyberdefense Program Against Advanced Threats”) shows the progression of the complication of cybersecurity protection — and the corresponding progression of complicating techniques that the villains use to overcome these defenses. "Ideal" and "indestructible" protection does not exist. Protection should be only good enough to put a potential villain in a situation where hacking becomes unreasonably expensive for him.
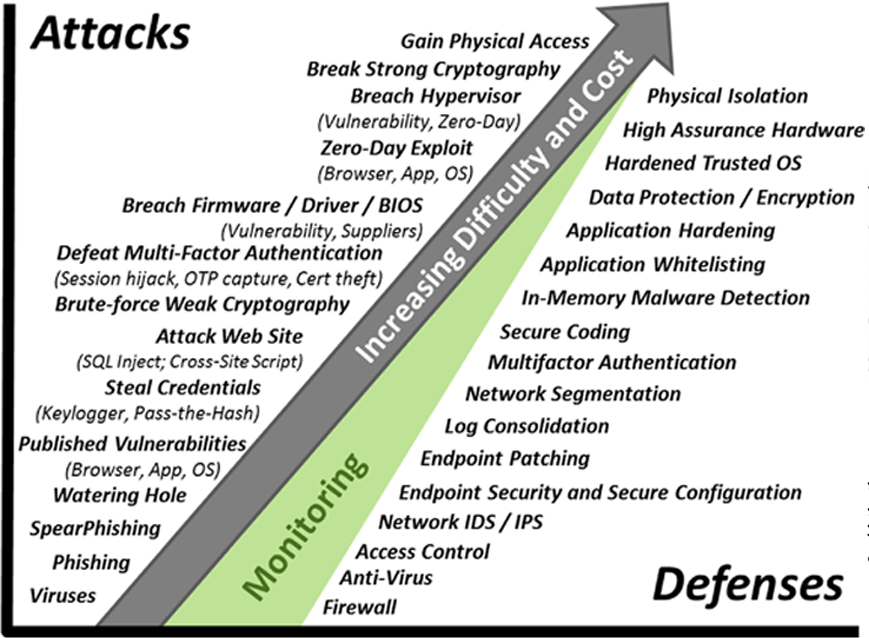
At the same time, it is important to understand that in the overwhelming majority of cyber attacks, villains use a relatively simple arsenal: targeted phishing, published vulnerabilities, theft of logins and passwords, hacking of websites. Advanced arsenal they rarely use. They do not need to burden themselves with such advanced things as zero-day exploits, breaking the hypervisor, breaking into strong cryptography, gaining physical access. Because simpler techniques, which are much simpler and cheaper, are still effective.
Therefore, when designing the cyber defense of an enterprise, before investing in advanced protection tools - such as SKZI and iron with guaranteed safety - be sure to ensure that the basic protection tools are functioning properly. Phishing Protection, above all. Otherwise, these investments will not be confused.
Download a memo on the types of phishing here .
