Software and hardware firewall capabilities
Creating a secure system is a complex task. One of the security measures is the use of firewalls (they are also firewalls and firewalls). As we all know, firewalls are software and hardware. The possibilities of the first and second are not unlimited. In this article, we will try to figure out what both types of firewalls can do and what they cannot do.

First of all, you need to talk about what is software and what is a hardware solution. We are all used to the fact that if you buy some kind of hardware, then this solution is called hardware, and if the box is with software, then this is a sign of a software solution. In our opinion, the difference between hardware and software is rather arbitrary. What is an iron box? In fact, this is the same computer, albeit with a different architecture, albeit with slightly limited capabilities (you can’t connect a keyboard and monitor to it, it is “tuned” to perform one function), on which the software is installed. Software is a variant of a UNIX system with a "web face". The hardware firewall functions depend on the packet filter used (again, this is software) and the “web muzzle” itself. All hardware firewalls can be “flashed”, that is, in fact, just replace the software. And with real firmware (which was done using the programmer in the good old days), the process of updating the “firmware” on modern devices has little in common. It’s just that new software is written to the “flash drive” inside the “hardware”. A software firewall is software that can be installed on an existing computer, but in the case of a hardware firewall, there is no software, and in the case of a software, there is no hardware. That is why the line between these types of firewalls is very arbitrary. but in the case of a hardware firewall - without software in any way, and in the case of software - without hardware. That is why the line between these types of firewalls is very arbitrary. but in the case of a hardware firewall - without software in any way, and in the case of software - without hardware. That is why the line between these types of firewalls is very arbitrary.
The biggest difference between a software and a hardware firewall is by no means even functionality. Nobody bothers to choose a hardware firewall with the necessary functions. The difference in the method of use. As a rule, the software firewall is installed on each PC in the network (on each server and on each workstation), and the hardware firewall does not protect an individual PC, but the entire network at once. Of course, no one will stop you from installing a hardware firewall for each PC, but it all comes down to money. Considering the cost of hardware, you are unlikely to want to protect each PC with a hardware firewall.
The "iron" firewalls have the following advantages:
The benefits of software solutions include:
We will not write about the shortcomings - they follow from the advantages. The advantages of one type of firewall are usually the disadvantages of another type. For example, the disadvantages of hardware solutions include the cost and inability to protect the local network from the inside, and the disadvantages of software are the complexity of deployment and use (although, as noted, everything is relative).
True, there is one drawback of hardware firewalls that is worth mentioning. As a rule, all hardware firewalls have a reset button, by clicking which you can return the default settings. To click this button, you do not need to have any special qualifications. But in order to change the settings of a software firewall, you must, at a minimum, obtain administrator rights. By clicking one button, a disgruntled employee can violate the security of the entire enterprise (or leave the company without access to the Internet, which is even better). Therefore, when using hardware solutions, you need to take a more responsible approach to the physical security of the devices themselves.
Next, we will try to understand which firewall provides the best protection: software or hardware. The hardware will be a firewall built into the router from TP-Link. As a software - Cybersafe Firewall .
For the firewall test, we will use utilities from the site www.testmypcsecurity.com , namely Jumper, DNStester and CPIL Suite (developed by Comodo). We warn you right away: unlike certified tools like XSpider, these utilities use the same methods as the malicious programs that they simulate. That is why at the time of testing (if you want to repeat the results), all anti-virus protection tools must be deactivated.
You could, of course, consider XSpider, but this test would be too boring and uninteresting for the end reader. And who can imagine an attacker who uses a certified scanner?
Briefly about utilities:
All these utilities will be launched from within, that is, directly from the tested computers. But outside we will scan the good old nmap.
So, we have two computers. Both are connected to the Internet. One is connected via a hardware firewall (based on the TP-Link router) and neither a software firewall nor an antivirus is installed on it. The second computer is directly connected to the Internet and is protected by the CyberSafe software firewall. Windows 7 is installed on the first computer, Windows Server 2008 R2 is installed on the second.
Jumper, launched with administrator rights (which is a sin to hide, many users work with such rights), successfully completed its task in Windows 7 (Fig. 1). Nothing could stop him - after all, not a single protection tool, no antivirus, no firewall, no IDS / IPS was installed on our system, and the hardware firewall does not care what happens on client computers. He can not influence what is happening.

Fig. 1. Jumper in Windows 7
For the sake of fairness, it should be noted that if the user did not work as the administrator on the right, then Jumper would not work.
In Windows Server 2008, Jumper did not even start, but this is not due to the firewall, but to the operating system itself. Therefore, there is parity between the firewalls, since protection against this vulnerability can be provided by the operating system itself.
The purpose of this test is to send a recursive DNS query. By default, starting with Windows 2000, the Windows DNS Client service accepts and manages all DNS queries. Thus, all DNS queries from all applications in the system will be sent to the DNS client (SVCHOST.EXE). The DNS query itself makes the DNS client directly. DNStester uses a recursive DNS query to bypass the firewall, in other words, the service accesses itself.
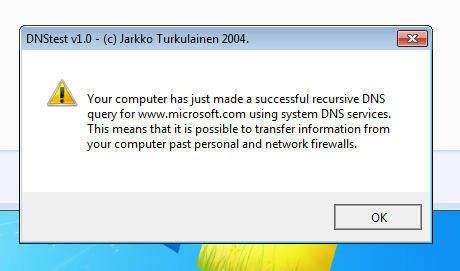
Fig. 2. Test failed
If you leave the firewall settings by default, then neither the software nor the hardware firewall could handle this test. It’s clear that the hardware firewall doesn’t care what happens on the workstation, so you don’t have to rely on it to protect the system from this vulnerability. In any case, with default settings (and they practically did not change).
But this does not mean that the Cybersafe Firewall is a bad firewall. With increasing the security level to the third, the test was completely passed (see. Fig. 3). The program reported an error in the DNS query. To verify that this is not a merit of Windows Server 2008, the test was repeated on a Windows 7 machine

. 3. Test passed (DNStest)
For the sake of justice, it should be noted that if an antivirus is installed on the computer, then most likely this application will be quarantined, but still it will manage to send one request (Fig. 4).

Fig. 4. Comodo Anti-Virus blocked an unwanted application
So, a hardware firewall with default settings failed all three CPIL tests (if you click on the Tell me more about Test text box, a window will appear explaining the principle of the test). But he failed them somehow strange. Passing the test implies the following sequence of actions:

Fig. 5. CPIL Test Suite
After that, a browser should open with the test results. In addition to reporting that the test failed, the results page should have displayed the value we entered, which was passed to the script as a GET parameter (see Fig. 6). It can be seen that the value (2 in the address bar) was still passed, but the script did not display it. Error in Comodo script? Of course, everyone is mistaken, but we have reduced confidence in this test.

Fig. 6. Test result (hardware firewall)
But when using the software firewall, the CPIL tests did not even start. When buttons 1 - 3 were pressed, nothing happened (Fig. 7). Is this really a merit of Windows Server 2008, not a firewall? We decided to check it out. Therefore, a Cybersafe Firewall was installed on a Windows 7 computer protected by a hardware firewall. But in Windows 7, the utility managed to break through the defense of the firewall. The first and third tests were passed, but when we pressed the Test 2 button, we had to contemplate the Chrome browser window, similar to that shown in Fig. 6.

Fig. 7. When you click on the button, nothing happens (you can see that the antivirus is disabled)
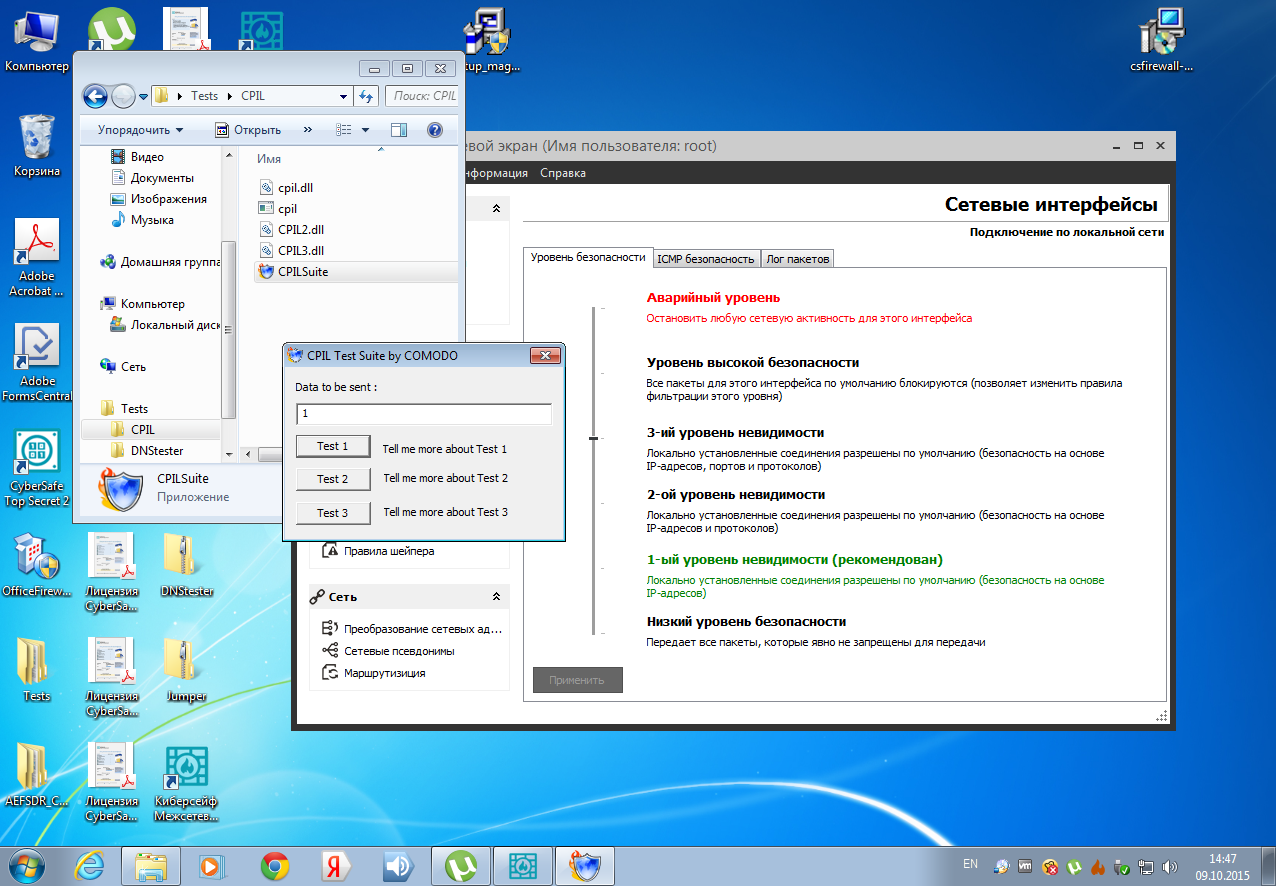
Fig. 8. Tests 1 and 3 passed
Before that, we tried to break through the firewall from the inside. Now let's try to scan the systems protected by the firewall. We will scan the scanner nmap. No one doubted the results of the hardware firewall - everything is closed and it is impossible to even determine the type of system under test (Fig. 9 and 10). In all subsequent illustrations, the IP addresses are hidden, because they are permanent - so that no one would want to repeat the test on our addresses.
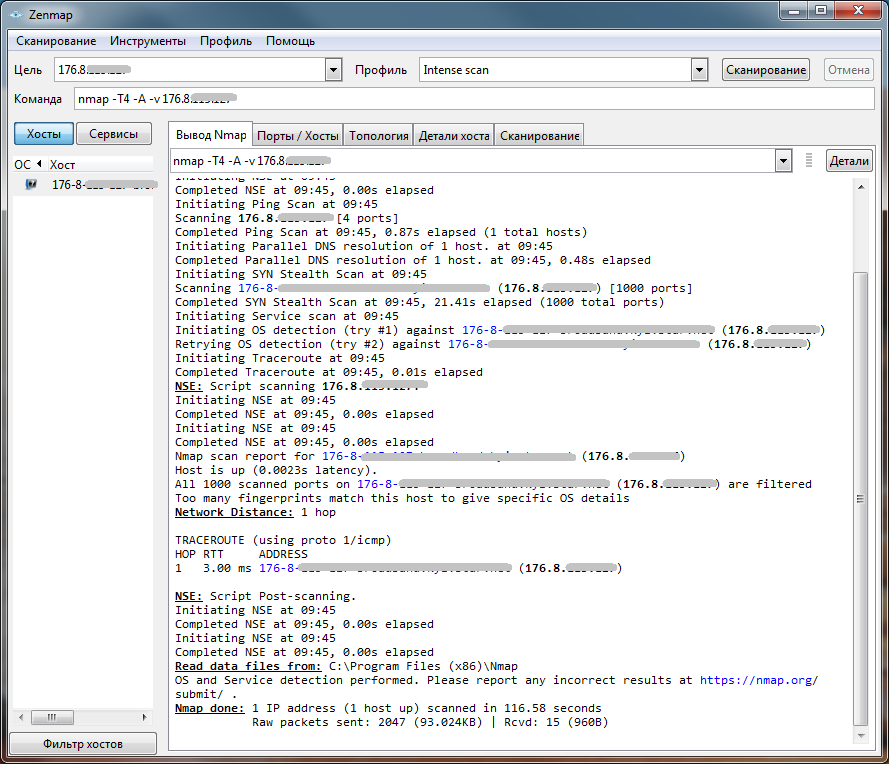
Fig.

Figure 9. Scanning a hardware firewall . 10. Scanning a hardware firewall (host details)
Now let's try to scan a system protected by a software firewall. Of course, by default, the software firewall will skip everything and everyone (Fig. 11).
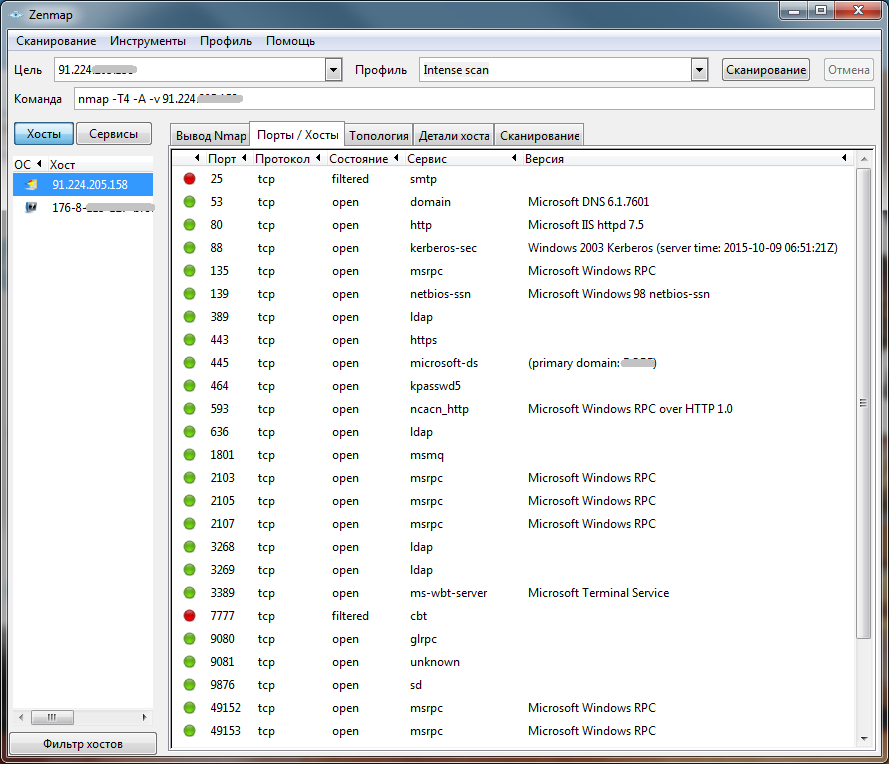
Fig. 11. Open ports (software firewall, default settings)

Fig. 12. The type of system is determined (software firewall, default settings).
When the rules are configured, then everything falls into place (Fig. 13). As you can see, the software firewall ensures the security of the protected system no worse than its "iron" counterpart.
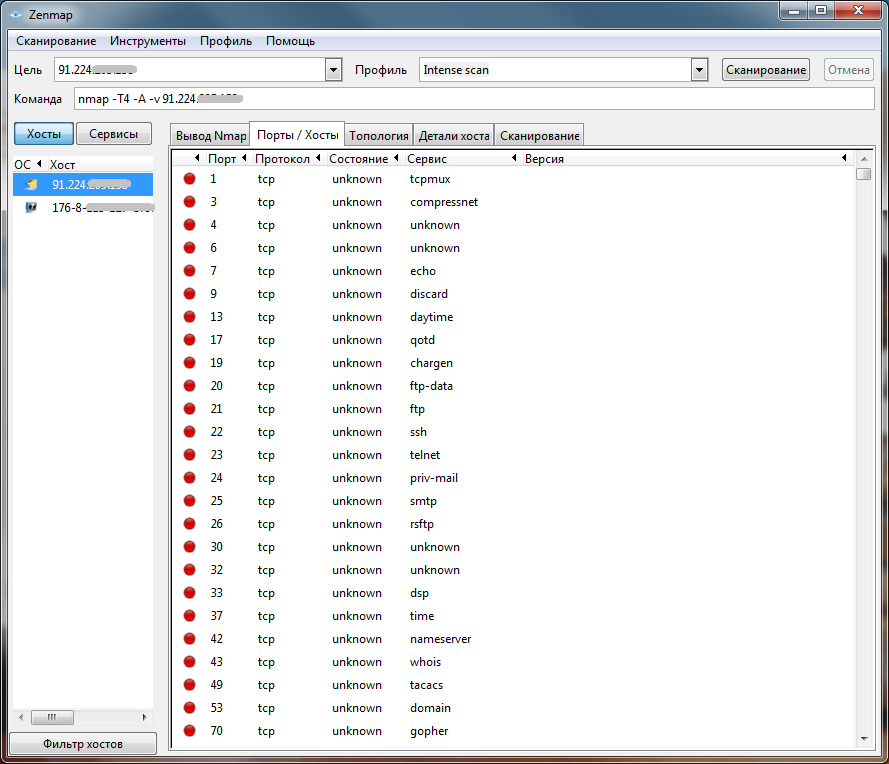
Fig. 13. No open ports
Why is it important to provide protection inside the local network? Many administrators mistakenly do not pay attention to internal protection, but in vain. Indeed, inside the local network, you can implement many attacks. Let's consider some of them.
Before connecting to the network, the computer sends an ARP request to find out if the IP address of the computer is busy. When there are several Windows machines with the same IP address on the local network, the user sees a window with a message that the IP address is busy (used by another computer). Windows learns about IP address occupancy through ARP.
An ARP attack is that an attacker floods machines that are running Windows. Moreover, hundreds of requests will be sent to each computer, as a result, the user will not be able to close constantly pop-up windows and will be forced to at least restart the computer.
The situation is not very pleasant. But the presence of a firewall on the workstation will negate all the efforts of the attacker.
DoS attacks (denial of service attacks) are possible not only on the Internet, but also on local networks. Only the methods of such attacks differ. The nature of DoS attacks can be any, however, it is impossible to deal with them without a firewall that would be installed on each machine on the local network.
One of the types of DoS attacks that can be successfully used on a local network is ICMP flood. CyberSafe Firewall The firewall contains dedicated tools to combat this type of attack (Fig. 14). It also contains a means of balancing the load on the server , which can also help in the fight against DoS attacks.
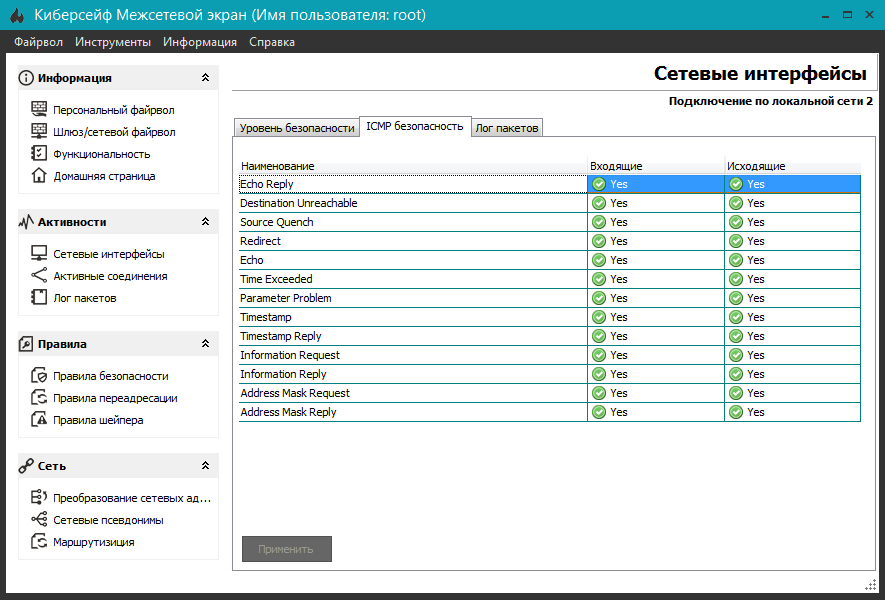
Fig. 14. ICMP security (CyberSafe Firewall)
You can read more about DOS attacks in the article “How to protect yourself from DoS / DDoS attacks” .
On a local network, computers are identified not only by IP address, but also by MAC address. Some administrators allow access to certain resources by MAC address, because IP addresses are usually dynamic and are issued by DHCP. This solution is not very justified, since the MAC address is very easy to change. Unfortunately, it is not always possible to protect yourself against changing the MAC address using a firewall. Not every firewall monitors MAC address changes, as it is usually associated with IP addresses. The most effective solution here is to use a switch, which allows you to bind the MAC address to a specific physical port on the switch. To deceive such protection is almost impossible, but it costs a lot. True, there are software ways to deal with MAC address changes.but they are less effective. If you are interested in a firewall that can recognize MAC address spoofing, then pay attention to Kaspersky Internet Security 8.0 . True, the latter can recognize only the gateway's MAC address spoofing. But then it fully recognizes the substitution of the IP address of the computer and IP flood.
In networks where access to resources is limited by IP addresses, an attacker can change the IP address and gain access to the protected resource. When using the Cybersafe firewall, such a scenario is not possible, since even the firewall itself does not bind to IP addresses. Even if you change the IP address of the computer, it will still not be part of the ISPD, into which the attacker seeks to penetrate.
This type of attack is based on sending fake ICMP packets to the victim. The essence of this attack is in the substitution of the gateway address - an ICMP packet is sent to the victim, reporting a shorter route. But in reality, the packets will not pass through the new router, but through the computer of the attacker. As noted earlier, Cybersafe Firewall provides ICMP security. Similarly, other firewalls can be used.
There are many other attacks on local networks - sniffers, and various attacks using DNS. Be that as it may, the use of software firewalls installed on each workstation can significantly improve security.
Protection of the information system should be comprehensive - this includes software and hardware firewalls, antiviruses, and the proper configuration of the system itself. As for our confrontation between software and hardware firewalls, the former are effectively used to protect each network node, and the latter to protect the entire network as a whole. A hardware firewall cannot provide protection for each individual workstation, is powerless during attacks within the network, and cannot perform ISPD demarcation, which must be performed in the context of personal data protection.

Software and hardware firewalls
First of all, you need to talk about what is software and what is a hardware solution. We are all used to the fact that if you buy some kind of hardware, then this solution is called hardware, and if the box is with software, then this is a sign of a software solution. In our opinion, the difference between hardware and software is rather arbitrary. What is an iron box? In fact, this is the same computer, albeit with a different architecture, albeit with slightly limited capabilities (you can’t connect a keyboard and monitor to it, it is “tuned” to perform one function), on which the software is installed. Software is a variant of a UNIX system with a "web face". The hardware firewall functions depend on the packet filter used (again, this is software) and the “web muzzle” itself. All hardware firewalls can be “flashed”, that is, in fact, just replace the software. And with real firmware (which was done using the programmer in the good old days), the process of updating the “firmware” on modern devices has little in common. It’s just that new software is written to the “flash drive” inside the “hardware”. A software firewall is software that can be installed on an existing computer, but in the case of a hardware firewall, there is no software, and in the case of a software, there is no hardware. That is why the line between these types of firewalls is very arbitrary. but in the case of a hardware firewall - without software in any way, and in the case of software - without hardware. That is why the line between these types of firewalls is very arbitrary. but in the case of a hardware firewall - without software in any way, and in the case of software - without hardware. That is why the line between these types of firewalls is very arbitrary.
The biggest difference between a software and a hardware firewall is by no means even functionality. Nobody bothers to choose a hardware firewall with the necessary functions. The difference in the method of use. As a rule, the software firewall is installed on each PC in the network (on each server and on each workstation), and the hardware firewall does not protect an individual PC, but the entire network at once. Of course, no one will stop you from installing a hardware firewall for each PC, but it all comes down to money. Considering the cost of hardware, you are unlikely to want to protect each PC with a hardware firewall.
Benefits of Hardware Firewalls
The "iron" firewalls have the following advantages:
- Relative ease of deployment and use . Connected, turned on, set parameters via the web interface and forgot about its existence. However, modern software firewalls support deployment via ActiveDirectory , which will not take too long. But, firstly, not all firewalls support ActiveDirectory, and secondly, Windows is not always used in the enterprise.
- Dimensions and power consumption . Typically, hardware firewalls are more modest in size and less power consuming. True, energy consumption does not always play a role, but size is important. A small compact box is one thing, another is a huge "system".
- Performance . Typically, the performance of a hardware solution is higher. If only because the hardware firewall only deals with its immediate function - packet filtering. It does not run any third-party processes and services, as is often the case with software firewalls. Imagine that you organized a software gateway (with firewall and NAT functions) based on a server running Windows Server. It is unlikely that you will allocate the whole server only for firewall and NAT. This is irrational. Most likely, other services will be launched on it - the same AD, DNS, etc. Already I am silent about DBMS and postal services.
- Reliability . It is believed that hardware solutions are more reliable (precisely because they rarely run third-party services). But no one bothers you to select a separate system unit (even if not the most modern one), install the same FreeBSD (one of the most reliable operating systems in the world) on it and configure the firewall rules. I think the reliability of such a solution will not be lower than in the case of a hardware firewall. But such a task requires advanced administrator skills, which is why it was previously noted that hardware solutions are easier to use.
Benefits of Software Firewalls
The benefits of software solutions include:
- Cost . The price of a software firewall is usually lower than the hardware. For the price of an average hardware solution, you can protect the entire network with a software firewall.
- Ability to protect the network from the inside . Threats do not always come from outside. There are many threats inside the local network. Attacks can come from internal computers. Any LAN user can initiate an attack, for example, a dissatisfied company. As already noted, you can, of course, use a separate hardware router to protect each individual node, but in practice we have not seen such solutions. They are painfully irrational.
- Possibility of differentiation of segments of a local network without allocation of subnets . In most cases, computers of different departments are connected to the local network, for example, accounting, finance, IT, etc. These computers do not always have to interact with each other. How to differentiate ISPD? The first solution is to create several subnets (for example, 192.168.1.0, 192.168.2.0, etc.) and properly configure routing between these subnets. This is not to say that the solution is very complex, but still more complicated than using a software firewall. And it’s not always possible to allocate subnets for one reason or another. The second solution is to use a firewall designed specifically to protect ISDN (not all software firewalls can easily distinguish ISDN) In this case, even in the largest network, you will perform ISPDN demarcation in a matter of minutes, and you won’t have to bother with routing settings.
- Ability to deploy to existing servers . It makes no sense to buy another piece of hardware if there is a sufficient computer park. It is enough to deploy a firewall on one of the servers and configure NAT and routing. Typically, both of these operations are performed through the graphical interface of the firewall and are implemented with a few clicks of the mouse in the right places.
- Advanced functionality . As a rule, the functionality of software firewalls is wider than that of their hardware counterparts. So, some firewalls provide load balancing , IDS / IPS and the like useful things that can improve the overall security of the data processing system. Yes, not all software firewalls have such functions, but nothing and nobody prevents you from choosing a firewall that suits your needs. Of course, some hardware systems have such functions. For example, StoneGate IPS - provides the functionality of an intrusion prevention system, but the cost of such solutions will not always please the management of the enterprise. There are also hardware load balancers, but they are even more expensive than hardware IPSs.
We will not write about the shortcomings - they follow from the advantages. The advantages of one type of firewall are usually the disadvantages of another type. For example, the disadvantages of hardware solutions include the cost and inability to protect the local network from the inside, and the disadvantages of software are the complexity of deployment and use (although, as noted, everything is relative).
True, there is one drawback of hardware firewalls that is worth mentioning. As a rule, all hardware firewalls have a reset button, by clicking which you can return the default settings. To click this button, you do not need to have any special qualifications. But in order to change the settings of a software firewall, you must, at a minimum, obtain administrator rights. By clicking one button, a disgruntled employee can violate the security of the entire enterprise (or leave the company without access to the Internet, which is even better). Therefore, when using hardware solutions, you need to take a more responsible approach to the physical security of the devices themselves.
Battle of firewalls
Next, we will try to understand which firewall provides the best protection: software or hardware. The hardware will be a firewall built into the router from TP-Link. As a software - Cybersafe Firewall .
For the firewall test, we will use utilities from the site www.testmypcsecurity.com , namely Jumper, DNStester and CPIL Suite (developed by Comodo). We warn you right away: unlike certified tools like XSpider, these utilities use the same methods as the malicious programs that they simulate. That is why at the time of testing (if you want to repeat the results), all anti-virus protection tools must be deactivated.
You could, of course, consider XSpider, but this test would be too boring and uninteresting for the end reader. And who can imagine an attacker who uses a certified scanner?
Briefly about utilities:
- Jumper - allows you to bypass the firewall using the DLL injection and thread injection methods.
- DNS Tester - Uses a recursive DNS query to bypass the firewall.
- CPIL Suite - test suite (3 tests) from Comodo.
All these utilities will be launched from within, that is, directly from the tested computers. But outside we will scan the good old nmap.
So, we have two computers. Both are connected to the Internet. One is connected via a hardware firewall (based on the TP-Link router) and neither a software firewall nor an antivirus is installed on it. The second computer is directly connected to the Internet and is protected by the CyberSafe software firewall. Windows 7 is installed on the first computer, Windows Server 2008 R2 is installed on the second.
Test 1: Jumper
Jumper, launched with administrator rights (which is a sin to hide, many users work with such rights), successfully completed its task in Windows 7 (Fig. 1). Nothing could stop him - after all, not a single protection tool, no antivirus, no firewall, no IDS / IPS was installed on our system, and the hardware firewall does not care what happens on client computers. He can not influence what is happening.

Fig. 1. Jumper in Windows 7
For the sake of fairness, it should be noted that if the user did not work as the administrator on the right, then Jumper would not work.
In Windows Server 2008, Jumper did not even start, but this is not due to the firewall, but to the operating system itself. Therefore, there is parity between the firewalls, since protection against this vulnerability can be provided by the operating system itself.
Test 2. DNStester
The purpose of this test is to send a recursive DNS query. By default, starting with Windows 2000, the Windows DNS Client service accepts and manages all DNS queries. Thus, all DNS queries from all applications in the system will be sent to the DNS client (SVCHOST.EXE). The DNS query itself makes the DNS client directly. DNStester uses a recursive DNS query to bypass the firewall, in other words, the service accesses itself.

Fig. 2. Test failed
If you leave the firewall settings by default, then neither the software nor the hardware firewall could handle this test. It’s clear that the hardware firewall doesn’t care what happens on the workstation, so you don’t have to rely on it to protect the system from this vulnerability. In any case, with default settings (and they practically did not change).
But this does not mean that the Cybersafe Firewall is a bad firewall. With increasing the security level to the third, the test was completely passed (see. Fig. 3). The program reported an error in the DNS query. To verify that this is not a merit of Windows Server 2008, the test was repeated on a Windows 7 machine

. 3. Test passed (DNStest)
For the sake of justice, it should be noted that if an antivirus is installed on the computer, then most likely this application will be quarantined, but still it will manage to send one request (Fig. 4).

Fig. 4. Comodo Anti-Virus blocked an unwanted application
Test 3. Test suite from Comodo (CPIL)
So, a hardware firewall with default settings failed all three CPIL tests (if you click on the Tell me more about Test text box, a window will appear explaining the principle of the test). But he failed them somehow strange. Passing the test implies the following sequence of actions:
- It is necessary to enter the transmitted data. We introduced values 1, 2, 3 for tests 1, 2, and 3, respectively.
- Then press one of the test call buttons (Fig. 5)

Fig. 5. CPIL Test Suite
After that, a browser should open with the test results. In addition to reporting that the test failed, the results page should have displayed the value we entered, which was passed to the script as a GET parameter (see Fig. 6). It can be seen that the value (2 in the address bar) was still passed, but the script did not display it. Error in Comodo script? Of course, everyone is mistaken, but we have reduced confidence in this test.

Fig. 6. Test result (hardware firewall)
But when using the software firewall, the CPIL tests did not even start. When buttons 1 - 3 were pressed, nothing happened (Fig. 7). Is this really a merit of Windows Server 2008, not a firewall? We decided to check it out. Therefore, a Cybersafe Firewall was installed on a Windows 7 computer protected by a hardware firewall. But in Windows 7, the utility managed to break through the defense of the firewall. The first and third tests were passed, but when we pressed the Test 2 button, we had to contemplate the Chrome browser window, similar to that shown in Fig. 6.

Fig. 7. When you click on the button, nothing happens (you can see that the antivirus is disabled)

Fig. 8. Tests 1 and 3 passed
Test 4. Scanning from the outside
Before that, we tried to break through the firewall from the inside. Now let's try to scan the systems protected by the firewall. We will scan the scanner nmap. No one doubted the results of the hardware firewall - everything is closed and it is impossible to even determine the type of system under test (Fig. 9 and 10). In all subsequent illustrations, the IP addresses are hidden, because they are permanent - so that no one would want to repeat the test on our addresses.

Fig.

Figure 9. Scanning a hardware firewall . 10. Scanning a hardware firewall (host details)
Now let's try to scan a system protected by a software firewall. Of course, by default, the software firewall will skip everything and everyone (Fig. 11).

Fig. 11. Open ports (software firewall, default settings)

Fig. 12. The type of system is determined (software firewall, default settings).
When the rules are configured, then everything falls into place (Fig. 13). As you can see, the software firewall ensures the security of the protected system no worse than its "iron" counterpart.

Fig. 13. No open ports
LAN Attacks
Why is it important to provide protection inside the local network? Many administrators mistakenly do not pay attention to internal protection, but in vain. Indeed, inside the local network, you can implement many attacks. Let's consider some of them.
ARP attack
Before connecting to the network, the computer sends an ARP request to find out if the IP address of the computer is busy. When there are several Windows machines with the same IP address on the local network, the user sees a window with a message that the IP address is busy (used by another computer). Windows learns about IP address occupancy through ARP.
An ARP attack is that an attacker floods machines that are running Windows. Moreover, hundreds of requests will be sent to each computer, as a result, the user will not be able to close constantly pop-up windows and will be forced to at least restart the computer.
The situation is not very pleasant. But the presence of a firewall on the workstation will negate all the efforts of the attacker.
DoS attacks, including various flood attacks
DoS attacks (denial of service attacks) are possible not only on the Internet, but also on local networks. Only the methods of such attacks differ. The nature of DoS attacks can be any, however, it is impossible to deal with them without a firewall that would be installed on each machine on the local network.
One of the types of DoS attacks that can be successfully used on a local network is ICMP flood. CyberSafe Firewall The firewall contains dedicated tools to combat this type of attack (Fig. 14). It also contains a means of balancing the load on the server , which can also help in the fight against DoS attacks.

Fig. 14. ICMP security (CyberSafe Firewall)
You can read more about DOS attacks in the article “How to protect yourself from DoS / DDoS attacks” .
Change MAC Address
On a local network, computers are identified not only by IP address, but also by MAC address. Some administrators allow access to certain resources by MAC address, because IP addresses are usually dynamic and are issued by DHCP. This solution is not very justified, since the MAC address is very easy to change. Unfortunately, it is not always possible to protect yourself against changing the MAC address using a firewall. Not every firewall monitors MAC address changes, as it is usually associated with IP addresses. The most effective solution here is to use a switch, which allows you to bind the MAC address to a specific physical port on the switch. To deceive such protection is almost impossible, but it costs a lot. True, there are software ways to deal with MAC address changes.but they are less effective. If you are interested in a firewall that can recognize MAC address spoofing, then pay attention to Kaspersky Internet Security 8.0 . True, the latter can recognize only the gateway's MAC address spoofing. But then it fully recognizes the substitution of the IP address of the computer and IP flood.
IP address spoofing
In networks where access to resources is limited by IP addresses, an attacker can change the IP address and gain access to the protected resource. When using the Cybersafe firewall, such a scenario is not possible, since even the firewall itself does not bind to IP addresses. Even if you change the IP address of the computer, it will still not be part of the ISPD, into which the attacker seeks to penetrate.
Routing attacks
This type of attack is based on sending fake ICMP packets to the victim. The essence of this attack is in the substitution of the gateway address - an ICMP packet is sent to the victim, reporting a shorter route. But in reality, the packets will not pass through the new router, but through the computer of the attacker. As noted earlier, Cybersafe Firewall provides ICMP security. Similarly, other firewalls can be used.
There are many other attacks on local networks - sniffers, and various attacks using DNS. Be that as it may, the use of software firewalls installed on each workstation can significantly improve security.
conclusions
Protection of the information system should be comprehensive - this includes software and hardware firewalls, antiviruses, and the proper configuration of the system itself. As for our confrontation between software and hardware firewalls, the former are effectively used to protect each network node, and the latter to protect the entire network as a whole. A hardware firewall cannot provide protection for each individual workstation, is powerless during attacks within the network, and cannot perform ISPD demarcation, which must be performed in the context of personal data protection.
