Critical Vulnerability WinRAR

Iranian researcher Mohammad Reza Espargham discovered the RCE (remote code execution) vulnerability in one of the most popular archiving tools - WinRAR. This utility is used by about 500 million users around the world, which makes the vulnerability quite widespread.
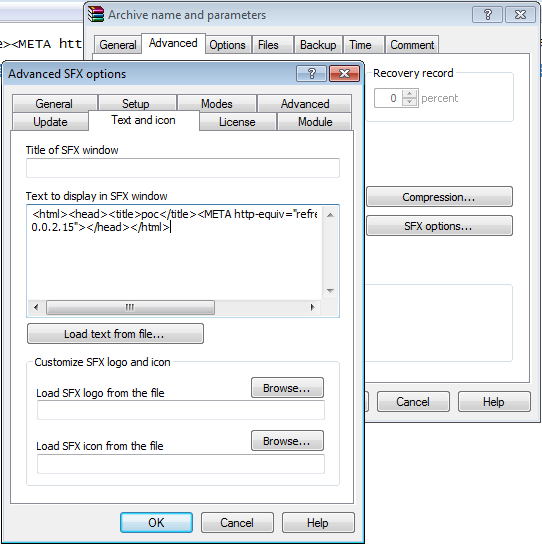
The vulnerability is contained in insufficient processing of data from the panel of the “Text” module, tab “Text to display in SFX window”. An attacker can provide the sfx archive with an additional payload to attack the target system. The danger is that the user, even suspecting and checking the file with an antivirus, most likely will not be able to detect a “hidden surprise” in the archive attachment.
The vulnerability is related to the possibility of modifying WinRAR self-extracting archives (SFX) so that at the time of launch they run executable code.
The description of the vulnerability is quite simple: http://seclists.org/fulldisclosure/2015/Sep/106
- Run perl code: perl poc.pl
- Right Click on any file and select "add to archive ..."
- Select “Create SFX archive”
- Go to the Advanced Menu and select "SFX options ..."
- Go to the “Text and icon” Menu
- Copy this perl output (HTML) and past on "Text to display in SFX window"
- Click OK - OK
- Your SFX file Created
- Just open sfx file
- Your Link Download / Execute on your target
- Successful reproduce of the code execution vulnerability!
Although archives are currently one of the most popular means of delivering malicious code, and WinRAR representatives pointed out that a self-extracting SFX archive is quite dangerous in itself, nevertheless, this kind of vulnerability provides attackers with additional opportunities to compromise information systems.
"We can say that limiting SFX module HTML functionality would hurt only those legitimate users, who need all HTML features, making absolutely no problem for a malicious person, who can use the previous version SFX modules, custom modules built from UnRAR source code, their own code or archived executables for their purpose. "We can only remind users once again to run .exe files, either SFX archives or not, only if they are received from a trustworthy source.”
Demo attack example:
