The study “The Global State of Information Security 2015” (GSISS 2015). Part 1
The PwC study is very voluminous, therefore published in parts.
Today, information security is an integral part of business risks. Now this issue concerns not only information technology and security specialists, but top management and boards of directors are now involved in IS issues. Consumers are also worried and want to keep abreast of potential security incidents and threats.

Media reports of security incidents (a security incident is defined as an undesirable incident that threatens a number of aspects of information security) have become commonplace like weather forecasts, and over the past 12 months, virtually every industry sector around the world has been exposed to some type of cyber threat. With the increasing number of incidents, governments are becoming increasingly active in helping organizations fight cyber crime. For example, the FBI revealed that 3,000 companies, including banks, retailers, and military contractors, were victims of cyber attacks in 2013. Subsequently, the U.S. Department of Justice indicted five Chinese military hackers for conducting economic cyber espionage against US companies in the nuclear, metal, and solar sectors. This was the first time that the United States has accused government officials of economic espionage through external cyber attacks in accordance with section 1831 of the Economic Spying Act. This trend is likely to continue, according to a forecast by Sean Joyce (head of consulting at PwC and former deputy director of the FBI). “I think we will see the Department of Justice and the FBI continue to implement an aggressive strategy against entities that cause significant economic damage to the US economy,” says Joyce. This was the first time that the United States has accused government officials of economic espionage through external cyber attacks in accordance with section 1831 of the Economic Spying Act. This trend is likely to continue, according to a forecast by Sean Joyce (head of consulting at PwC and former deputy director of the FBI). “I think we will see the Department of Justice and the FBI continue to implement an aggressive strategy against entities that cause significant economic damage to the US economy,” says Joyce. This was the first time that the United States has accused government officials of economic espionage through external cyber attacks in accordance with section 1831 of the Economic Spying Act. This trend is likely to continue, according to a forecast by Sean Joyce (head of consulting at PwC and former deputy director of the FBI). “I think we will see the Department of Justice and the FBI continue to implement an aggressive strategy against entities that cause significant economic damage to the US economy,” says Joyce. according to Sean Joyce’s forecast (head of consulting at PwC and former FBI deputy director). “I think we will see the Department of Justice and the FBI continue to implement an aggressive strategy against entities that cause significant economic damage to the US economy,” says Joyce. according to Sean Joyce’s forecast (head of consulting at PwC and former FBI deputy director). “I think we will see the Department of Justice and the FBI continue to implement an aggressive strategy against entities that cause significant economic damage to the US economy,” says Joyce.
Attacks on large retail companies reached incredible proportions last year, resulting in the theft of hundreds of millions of customer payment card entries. This has led to a significant increase in litigation and the urgent introduction of a new payment card standard in the United States. In the UK, an insider at the company stole information on the wages and bank account numbers of 100,000 supermarket chain employees, after which this information was published online. South Korea also reported theft of consumer data on a massive scale, 105 million payment card accounts were attacked. In Verdun, Germany, city officials announced the theft of 18 million email addresses, passwords, and other information.

Following Snowden’s revelations, attacks on retailers have given even greater publicity to information security concerns. Loud revelations in the surveillance prompted international corporations and even governments to revise the list of suppliers of goods and services, excluding companies that may be associated with state bodies. In particular, Symantec reported the discovery of spying on the governments of the main countries of the European Union. Based on the selected goals and extremely non-trivial malware, Symantec concluded that the group coordinated the attacks with the support of one of the states. Geopolitical conflicts, especially between Russia and Ukraine, result in counter-attacks on government sites and the spread of malware on embassy devices.
Other important infrastructure providers are also under attack. A group of hackers successfully infiltrated a U.S. public utility company over the Internet and compromised the control system, although the invasion was stopped before any damage was done. Criminals behind which third states are located use sophisticated malware to infiltrate hundreds of energy companies in the US and Europe into industrial control systems.
The leaders among victims of cyber attacks remain companies in the financial sector. Attacks on stock exchanges have become commonplace. Study46 stock exchanges worldwide conducted by the International Organization of Securities Commissions (IOSCO) and the World Federation of Exchanges showed that more than half (53%) of the sites were subjected to cyber attacks. The banking sector is also not far behind, during one of the attacks, cyber criminals robbed the ATMs of two Middle Eastern banks around the world in the amount of $ 45 million.
We also see an increase in attacks on the so-called “Internet of things” segment - the ecosystem of devices connected to the network, which are gaining momentum, and those designed to make our lives easier, such as baby monitors, home thermostats, new TVs, etc. These devices connected to the Internet are extremely vulnerable to attack, because even basic security systems are not embedded in them, as confirmed by a recent studyHP Fortify on Demand. HP has investigated the 10 most popular connected devices and confirms that 70% of them contain serious vulnerabilities.
IOActive has published a study that demonstrates in detail how hackers can control the electronic control units of specific cars and offers mechanisms for detecting attacks. It is reported that cars that contain dozens of electronic devices that are interconnected, and in some cases connect to the outside world through wireless communication, can be hacked with subsequent monitoring of brakes, steering and even the engine.

Regulators
Some of the world's most respected and popular news organizations, including The New York Times, The Financial Times, CNN, Reuters, were compromised last year. Many of the most famous attacks were carried out by hackers associated with authorities in the Middle East region. This list is far from complete, it is impossible to find out the exact number of companies that have been attacked or compromised, and there are several reasons for this. Firstly, some companies will not know that they were attacked, and secondly, companies are afraid to publicly report incidents in order to avoid reputational or material losses, lawsuits and other checks. Speaking of inspections, regulators around the world are beginning to tighten the rules and requirements for companies in the field of information security.
To confirm the above, we can give an example of the plans of the US Securities and Exchange Commission to conduct information security tests in more than 50 broker dealers and investment consulting companies. In Asia, the Singapore Personal Data Protection Act sets new standards for the collection, use and disclosure of personal data. Organizations that will not comply with the new requirements will be fined up to 1 million SGD or $ 788'995.

The new guidance from the US Securities and Exchange Commission has several new and unique requirements, such as the availability of insurance against cyber attacks and the ability to make a complete inventory of all incidents and violations. Management also requires that enterprises implement risk assessment mechanisms and more effectively evaluate risks and due diligence of vendors.
Leaders of transnational organizations awaiting the adoption of European Union Data Protection Regulation, the final version of which is expected in 2015. Market participants expect tougher requirements for companies that process personal data, in particular, risk assessments and audits of information security systems, and more than a double increase in fines for compromised companies (from 2% to 5% of the company's annual turnover). The new EU requirements for notifications in case of security incidents will make it possible to assess the situation with cyber attacks in Europe more accurately. According to John Woods (one of the leading employees of the cyber security practice department at Baker & McKenzie Law Firm): “In the United States, state laws to notify in cases of security incidents revealed a lot of cases of attacks and compromises, which led to a more serious attitude and closer attention to information security. It will be interesting to observe if European standards have the same result. ”
We are also witnessing a new government effort to help organizations improve their information security on a voluntary basis. In the United States, in 2013, a special order of the president to increase the level of information security created the standard of the National Institute of Standards and Technology (NIST). Version 1.0 of the standard is voluntarily implemented by individual companies to evaluate and improve information security, and also creates a common platform for discussion, cooperation and tactics for responding to cyber threats. Private sector efforts to promote security are represented by the launch of Google's initiative, Project Zero, which aims to promote security by identifying and blocking unknown threats before hackers can take advantage of them. Google says
The market for information security services is growing
As a result of an increase in the number of incidents (by 48% in 2014 compared with 2013) and stricter requirements of regulators, companies and government agencies are forced to increase the level of information security in order to protect their data. This, in turn, provides an impetus for the growth of the number of solutions and technologies in the field of information security.

Research firm Gartner predictsthat global IT security spending will grow 7.9% to $ 71'100'000'000 in 2014, and 8.2% to $ 76'900'000'000 in 2015. The growth of security incidents and their coverage in the media helped to open the flow of venture capital investments in companies that provide information security services. During the first six months of 2014, venture capital funds invested $ 894'000'000 in the US in startups in the information security segment. The amount is almost the same as investment in all startups in 2013. This exceeds all investments in the information security sector over the past 10 years. At the same time, the capitalization of some security firms reached new highs last year.
For example, FireEye, a network security provider, after valuing at $ 304 million during an IPO in 2013, currently has a market capitalization of about $ 4.6 billion. Palo Alto Networks (specializing in corporate sector information security) raised $ 260 million in 2012 for an IPO , and now has a market capitalization of approximately $ 6.2 billion.

At the height of the boom of perpetual capitalism, the valuation of some companies in the information security segment was five to ten of their annual revenues. At the moment, a correction is taking place in the market, everyone understands that the segment has turned into a “bubble”, and to avoid a collapse, investors are gradually reducing the rate of investment in information security. This has led some companies to lose up to half their previous valuations. We believe that the software and information security services market will continue to grow as top management and boards of directors understand that cyber attacks will never stop, and the requirements of regulators will only be tightened.
The market for venture capital in the field of information security is growing in Europe:
- London-based company C5Capital raised a fund focused on information security in the amount of $ 125 million and announced investments in BalaBit 22 in the amount of $ 8 million;
- Index Ventures fund has opened its doors for information security companies from Europe, Israel and the USA, having allocated $ 550 million for this segment. The fund has also been active this year in the field of mergers and acquisitions in the information security segment;
- FireEye acquired Mandiant for about $ 1 billion;
- Cisco Systems acquired Sourcefire for $ 2.7 billion.
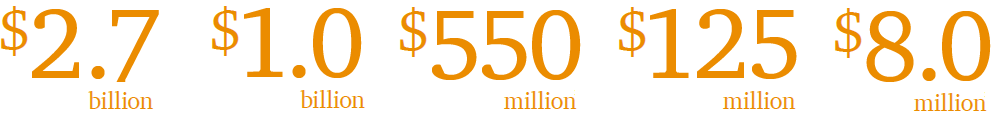
TO BE CONTINUED ...
Today, information security is an integral part of business risks. Now this issue concerns not only information technology and security specialists, but top management and boards of directors are now involved in IS issues. Consumers are also worried and want to keep abreast of potential security incidents and threats.

Media reports of security incidents (a security incident is defined as an undesirable incident that threatens a number of aspects of information security) have become commonplace like weather forecasts, and over the past 12 months, virtually every industry sector around the world has been exposed to some type of cyber threat. With the increasing number of incidents, governments are becoming increasingly active in helping organizations fight cyber crime. For example, the FBI revealed that 3,000 companies, including banks, retailers, and military contractors, were victims of cyber attacks in 2013. Subsequently, the U.S. Department of Justice indicted five Chinese military hackers for conducting economic cyber espionage against US companies in the nuclear, metal, and solar sectors. This was the first time that the United States has accused government officials of economic espionage through external cyber attacks in accordance with section 1831 of the Economic Spying Act. This trend is likely to continue, according to a forecast by Sean Joyce (head of consulting at PwC and former deputy director of the FBI). “I think we will see the Department of Justice and the FBI continue to implement an aggressive strategy against entities that cause significant economic damage to the US economy,” says Joyce. This was the first time that the United States has accused government officials of economic espionage through external cyber attacks in accordance with section 1831 of the Economic Spying Act. This trend is likely to continue, according to a forecast by Sean Joyce (head of consulting at PwC and former deputy director of the FBI). “I think we will see the Department of Justice and the FBI continue to implement an aggressive strategy against entities that cause significant economic damage to the US economy,” says Joyce. This was the first time that the United States has accused government officials of economic espionage through external cyber attacks in accordance with section 1831 of the Economic Spying Act. This trend is likely to continue, according to a forecast by Sean Joyce (head of consulting at PwC and former deputy director of the FBI). “I think we will see the Department of Justice and the FBI continue to implement an aggressive strategy against entities that cause significant economic damage to the US economy,” says Joyce. according to Sean Joyce’s forecast (head of consulting at PwC and former FBI deputy director). “I think we will see the Department of Justice and the FBI continue to implement an aggressive strategy against entities that cause significant economic damage to the US economy,” says Joyce. according to Sean Joyce’s forecast (head of consulting at PwC and former FBI deputy director). “I think we will see the Department of Justice and the FBI continue to implement an aggressive strategy against entities that cause significant economic damage to the US economy,” says Joyce.
Attacks on large retail companies reached incredible proportions last year, resulting in the theft of hundreds of millions of customer payment card entries. This has led to a significant increase in litigation and the urgent introduction of a new payment card standard in the United States. In the UK, an insider at the company stole information on the wages and bank account numbers of 100,000 supermarket chain employees, after which this information was published online. South Korea also reported theft of consumer data on a massive scale, 105 million payment card accounts were attacked. In Verdun, Germany, city officials announced the theft of 18 million email addresses, passwords, and other information.

Following Snowden’s revelations, attacks on retailers have given even greater publicity to information security concerns. Loud revelations in the surveillance prompted international corporations and even governments to revise the list of suppliers of goods and services, excluding companies that may be associated with state bodies. In particular, Symantec reported the discovery of spying on the governments of the main countries of the European Union. Based on the selected goals and extremely non-trivial malware, Symantec concluded that the group coordinated the attacks with the support of one of the states. Geopolitical conflicts, especially between Russia and Ukraine, result in counter-attacks on government sites and the spread of malware on embassy devices.
Other important infrastructure providers are also under attack. A group of hackers successfully infiltrated a U.S. public utility company over the Internet and compromised the control system, although the invasion was stopped before any damage was done. Criminals behind which third states are located use sophisticated malware to infiltrate hundreds of energy companies in the US and Europe into industrial control systems.
The leaders among victims of cyber attacks remain companies in the financial sector. Attacks on stock exchanges have become commonplace. Study46 stock exchanges worldwide conducted by the International Organization of Securities Commissions (IOSCO) and the World Federation of Exchanges showed that more than half (53%) of the sites were subjected to cyber attacks. The banking sector is also not far behind, during one of the attacks, cyber criminals robbed the ATMs of two Middle Eastern banks around the world in the amount of $ 45 million.
We also see an increase in attacks on the so-called “Internet of things” segment - the ecosystem of devices connected to the network, which are gaining momentum, and those designed to make our lives easier, such as baby monitors, home thermostats, new TVs, etc. These devices connected to the Internet are extremely vulnerable to attack, because even basic security systems are not embedded in them, as confirmed by a recent studyHP Fortify on Demand. HP has investigated the 10 most popular connected devices and confirms that 70% of them contain serious vulnerabilities.
IOActive has published a study that demonstrates in detail how hackers can control the electronic control units of specific cars and offers mechanisms for detecting attacks. It is reported that cars that contain dozens of electronic devices that are interconnected, and in some cases connect to the outside world through wireless communication, can be hacked with subsequent monitoring of brakes, steering and even the engine.

Regulators
Some of the world's most respected and popular news organizations, including The New York Times, The Financial Times, CNN, Reuters, were compromised last year. Many of the most famous attacks were carried out by hackers associated with authorities in the Middle East region. This list is far from complete, it is impossible to find out the exact number of companies that have been attacked or compromised, and there are several reasons for this. Firstly, some companies will not know that they were attacked, and secondly, companies are afraid to publicly report incidents in order to avoid reputational or material losses, lawsuits and other checks. Speaking of inspections, regulators around the world are beginning to tighten the rules and requirements for companies in the field of information security.
To confirm the above, we can give an example of the plans of the US Securities and Exchange Commission to conduct information security tests in more than 50 broker dealers and investment consulting companies. In Asia, the Singapore Personal Data Protection Act sets new standards for the collection, use and disclosure of personal data. Organizations that will not comply with the new requirements will be fined up to 1 million SGD or $ 788'995.

The new guidance from the US Securities and Exchange Commission has several new and unique requirements, such as the availability of insurance against cyber attacks and the ability to make a complete inventory of all incidents and violations. Management also requires that enterprises implement risk assessment mechanisms and more effectively evaluate risks and due diligence of vendors.
Leaders of transnational organizations awaiting the adoption of European Union Data Protection Regulation, the final version of which is expected in 2015. Market participants expect tougher requirements for companies that process personal data, in particular, risk assessments and audits of information security systems, and more than a double increase in fines for compromised companies (from 2% to 5% of the company's annual turnover). The new EU requirements for notifications in case of security incidents will make it possible to assess the situation with cyber attacks in Europe more accurately. According to John Woods (one of the leading employees of the cyber security practice department at Baker & McKenzie Law Firm): “In the United States, state laws to notify in cases of security incidents revealed a lot of cases of attacks and compromises, which led to a more serious attitude and closer attention to information security. It will be interesting to observe if European standards have the same result. ”
We are also witnessing a new government effort to help organizations improve their information security on a voluntary basis. In the United States, in 2013, a special order of the president to increase the level of information security created the standard of the National Institute of Standards and Technology (NIST). Version 1.0 of the standard is voluntarily implemented by individual companies to evaluate and improve information security, and also creates a common platform for discussion, cooperation and tactics for responding to cyber threats. Private sector efforts to promote security are represented by the launch of Google's initiative, Project Zero, which aims to promote security by identifying and blocking unknown threats before hackers can take advantage of them. Google says
The market for information security services is growing
As a result of an increase in the number of incidents (by 48% in 2014 compared with 2013) and stricter requirements of regulators, companies and government agencies are forced to increase the level of information security in order to protect their data. This, in turn, provides an impetus for the growth of the number of solutions and technologies in the field of information security.

Research firm Gartner predictsthat global IT security spending will grow 7.9% to $ 71'100'000'000 in 2014, and 8.2% to $ 76'900'000'000 in 2015. The growth of security incidents and their coverage in the media helped to open the flow of venture capital investments in companies that provide information security services. During the first six months of 2014, venture capital funds invested $ 894'000'000 in the US in startups in the information security segment. The amount is almost the same as investment in all startups in 2013. This exceeds all investments in the information security sector over the past 10 years. At the same time, the capitalization of some security firms reached new highs last year.
For example, FireEye, a network security provider, after valuing at $ 304 million during an IPO in 2013, currently has a market capitalization of about $ 4.6 billion. Palo Alto Networks (specializing in corporate sector information security) raised $ 260 million in 2012 for an IPO , and now has a market capitalization of approximately $ 6.2 billion.

At the height of the boom of perpetual capitalism, the valuation of some companies in the information security segment was five to ten of their annual revenues. At the moment, a correction is taking place in the market, everyone understands that the segment has turned into a “bubble”, and to avoid a collapse, investors are gradually reducing the rate of investment in information security. This has led some companies to lose up to half their previous valuations. We believe that the software and information security services market will continue to grow as top management and boards of directors understand that cyber attacks will never stop, and the requirements of regulators will only be tightened.
The market for venture capital in the field of information security is growing in Europe:
- London-based company C5Capital raised a fund focused on information security in the amount of $ 125 million and announced investments in BalaBit 22 in the amount of $ 8 million;
- Index Ventures fund has opened its doors for information security companies from Europe, Israel and the USA, having allocated $ 550 million for this segment. The fund has also been active this year in the field of mergers and acquisitions in the information security segment;
- FireEye acquired Mandiant for about $ 1 billion;
- Cisco Systems acquired Sourcefire for $ 2.7 billion.
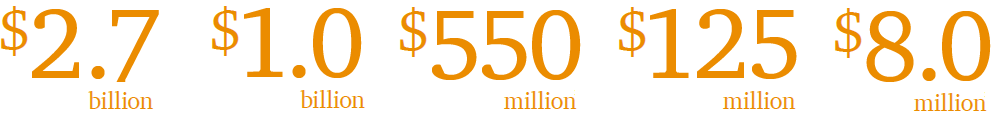
TO BE CONTINUED ...
