Typical corporate security issues that can be detected using Check Point Security CheckUP
All characters are fictional, all matches with real companies are absolutely random!
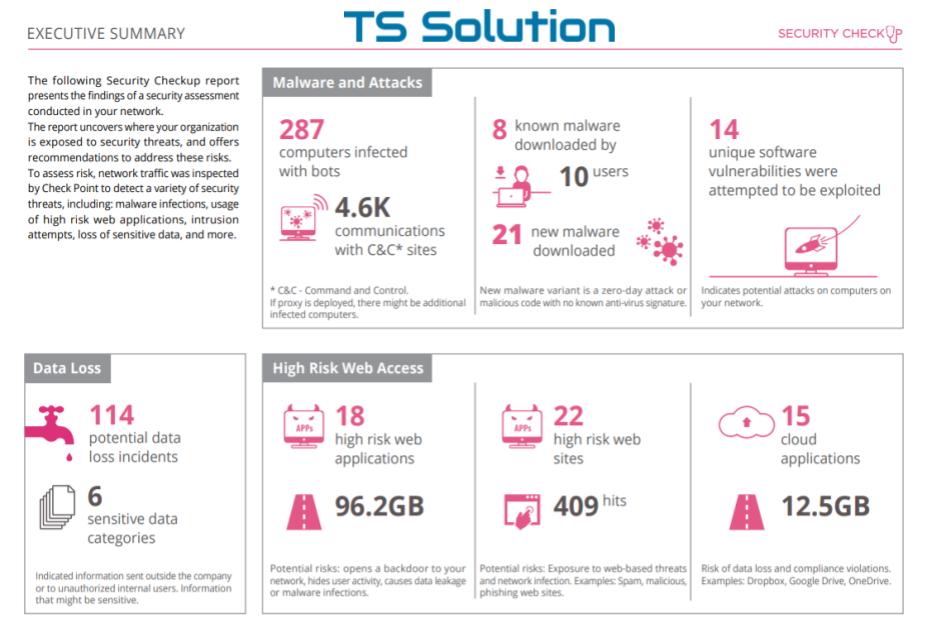
What are the most common corporate security issues? The answer to this question is not so simple. But we can share some statistics that we obtained by conducting network security audits using Check Point Security CheckUP . We have already published a series of articles on what Security CheckUP is and how to conduct it . In the first video tutorial, they even described why you might need it. The number of CheckUPs we have conducted has long exceeded one hundred. For all this time, statistics has accumulated on the most common network security problems that can be detected using Security CheckUP. The threats described below were present in almost all companies (someone more, someone less).
1) Employees use VPN and Proxy
In modern companies, there are almost no “aunts” left who can only use Internet Explorer and walk only through the sites from the bookmarks. Users have become more advanced and will not surprise anyone with the word VPN, Proxy, Anonymizer, and so on. As the results of CheckUP show, almost every company has employees who use Tor, Betternet, Freegate, etc. They are used to bypass Roskomnadzor’s locks, or to bypass locks in the company itself (go play poker or watch adult videos). Block this, without having on the perimeter of the decision class NGFW, is almost impossible.
What is dangerous about using VPN?
The most dangerous thing about using a VPN is not the fact that users can bypass the blocking. The main problem is that encrypted traffic will go through the network perimeter. Even if you have a very good border device with Anti-Virus and IPS functions, you simply cannot check anything. Through the encrypted channel, you can “push through” anything, including virus files (the user himself may not even suspect that he is downloading something bad). Similar problem with HTTPS traffic. We described it in one of the lessons “ Check Point for maximum ”. If you are NOT using SSL inspection at the network edge, then you have a huge hole the size of the bandwidth of the Internet channel.
Report example
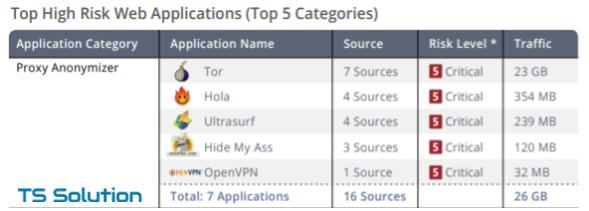
For many security men, it turns out to be a surprise that so many people use anonymizers on their networks, and even so much traffic goes through them. What has passed inside these channels can no longer be known.
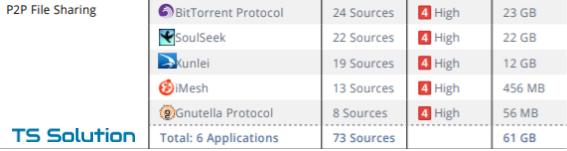
2) Torrents
To be honest, I was surprised when I received such statistics. In almost every company, downloading via torrent (or other p2p applications) was noticed. Moreover, the volume of downloaded traffic just scales. One of our clients found that users had downloaded 2 TB in a week! It would seem that everyone already has a home and very high-speed Internet. Why download torrents at work?
Why is the use of torrents dangerous?
The main problem is the enormous load on the bandwidth of the Internet channel. Often this negatively affects the work of business applications such as ip-telephony, company cloud resources (CRM, Email), etc. In addition, when planning the purchase of a firewall on the perimeter of the network, many select a solution based on the available statistics of the channel load. We saw that over the last month the average load in the region of 400 Mbit / s, which means that the firewall should be taken more powerful, and therefore more expensive. Only here if you block all the "left" traffic, you can significantly save on the purchase of NGFW.
In addition, almost all files downloaded through the torrent, swing parts. And it makes it very difficult to check traffic by such systems as Anti-Virus or IPS.
Report example
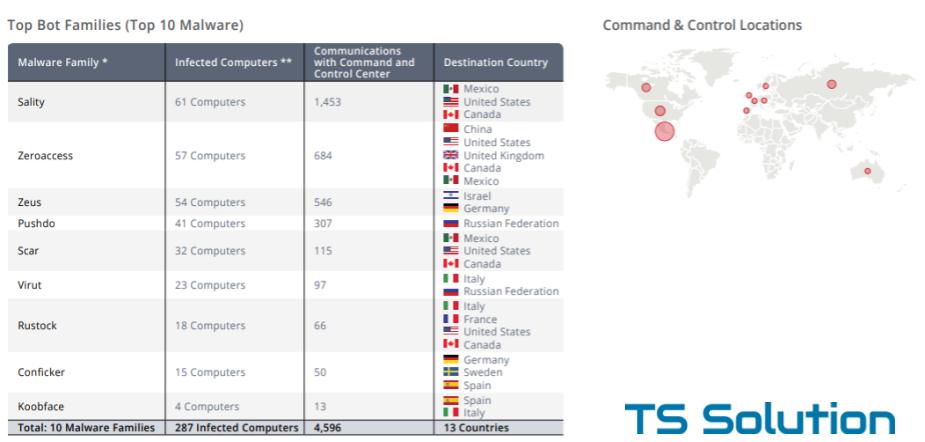
3) Botnets
In 90% of cases, it was possible to detect infected computers that are part of botnets. Formally, an infected computer may not interfere with the user's work. Files are not deleted or encrypted, no information is merged. However, there is a “small” utility on the computer, which “knocks” all the time at the command center and waits for instructions. It is necessary to recognize that there are also false positives, when Check Point defines legitimate traffic as a botnet. Each incident requires careful consideration.
What are the dangerous computers bots?
Infected computers can live on your network for years. They may not harm you, but it is completely impossible to predict what they can do on “one fine day”. They will receive a command to download the encryption virus and infect the entire network.
Report example
4) Remote Access Utilities
Another unpleasant incident. The vast majority of companies find people who use remote access utilities to their work computers (TeamViewer, RDP, LogMeIn, etc.). Although no one guarantees that this remote access is used by the employees themselves. Perhaps this is a former employee or part of a viral company.
How dangerous are remote access utilities?
In addition to the problem of unauthorized access to the network, there is another one - file transfer. It is especially “sad” to see when within these remote sessions decent traffic is pumped - gigabytes! Most remote access utilities encrypt their connections, so it’s impossible to know what is being downloaded or downloaded. But in general, it is a large channel of possible leaks of corporate information.
Report example

5) Porn and other "entertainment"
It may sound surprising, but people really watch adult videos at work. Moreover, the volume of traffic is amazing. In one of the CheckUPs, we found that in two weeks an employee of the company “saw out” 26 GB porn.
What is dangerous porn at work?
The question sounds very funny. If you do not take into account the moral and ethical standards, then there is probably a little different problem - users spend a lot of time for entertainment. YouTube, social networks, instant messengers. All this is clearly not conducive to productivity (although it is also possible to argue here). In general, using CheckUP, you can see who and what spends working time.
Report example
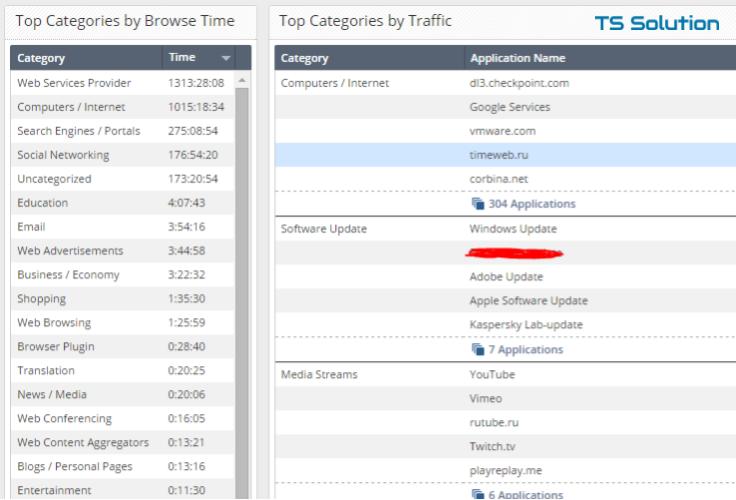
6) Viruses in the mail
CheckUP allows you to check not only user traffic, but all incoming mail. And this is not only checking for spam, but also checking attachments (doc, pdf, zip, etc.) and links in the body of the letter. And it is quite simple to set up the check The mail server is configured to forward copies of all emails directly to Check Point, which is running the Mail Transfer Agent (MTA). On Exchange, this can be done using Blind carbon copy (Bcc). The main advantage of this check is that we check emails after existing Anti-Spam client solutions. And what a surprise this client feels when they discover that malicious emails still pass, and in quite large numbers. Those. in most cases, it is found that the current means of protecting mail traffic are not coping.
What are dangerous viruses in the mail?
Stupid question. According to the latest reports, mail still leads among the ways of delivering viruses to users. Moreover, the malware can be either a file attachment or as a link to some resource (google drive, yandex disk, etc.). Check Point allows you to implement a more in-depth analysis of such things using SandBlast technologies (we will not describe what it is, this is not about that now).
Report example
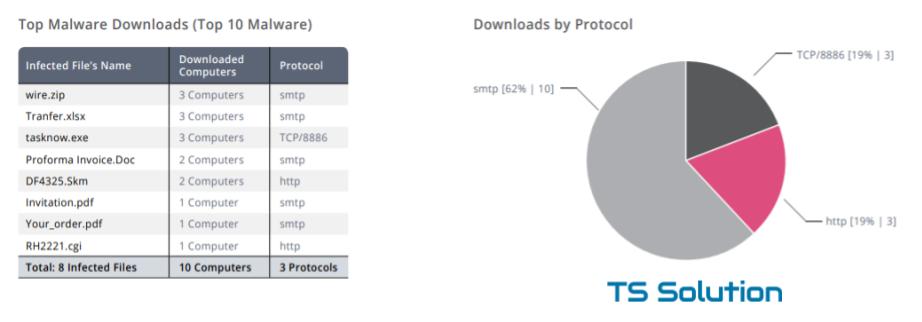
As you can see, SMTP traffic prevails among viruses. Plus viruses are not only exe-files, but also ordinary .doc or .pdf documents that users usually open without fear.
7) Phishing
Almost every CheckUP detects user clicks on phishing links. Office 356, paypai, sbenbank, fasebook, appie, ... Examples of phishing sites are endless. In general, the direction of phishing attacks is experiencing an unprecedented rise. It is understandable why to invent cunning viruses and fight defensive techniques if you can just fool a trusting user. A person will always remain the weakest link in the company's information security.
What is phishing dangerous?
It can be said that phishing is a personal user problem. Well, they will steal money from the card from them, next time they will be smarter. However, as part of phishing, corporate data can be stolen! Postal addresses, passwords, important documents. It is worth noting that users very often like to use corporate passwords for registration on public sites (social networks, torrent trackers, etc.). Why memorize a bunch of passwords when you can use one everywhere?
Report example

8) Upload to the cloud from the corporate network
Another big problem safeguard - cloud storage. Dropbox, GoogleDrive, Yandex disk, etc. All these polls are already using these services. But one thing is to know that someone may use it in the corporate network, and another thing is to see that gigabytes of traffic go through these channels. In 80% of cases we found a similar problem with the audited companies.
Why is this upload dangerous?
It's all obvious. Someone can “merge” corporate data. And if you do not have DLP solutions, then it is impossible to see what exactly “merges”. However, not only upload to these cloud resources is dangerous. No less dangerous and download! Hackers have long been used to using public file storages to spread viruses.
Report example
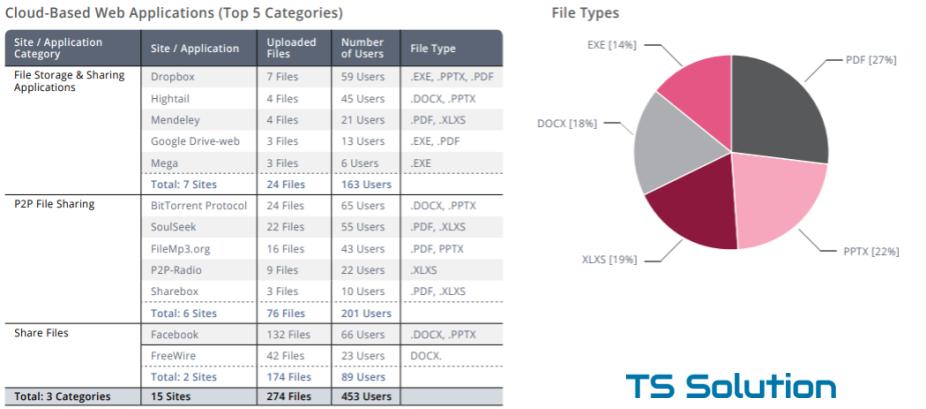
This is just an example. In Russia, things like Yandex.Disk, Cloud.Mail.ru, OneDrive, etc. are more common. The picture above reflects only the number of files, but you can also output volume statistics:

Other problems
We have listed only the most popular issues that can be detected using Check Point Security CheckUP. They are found in almost every audit. But the problems are much more and there are much more serious:
Exploit attacks
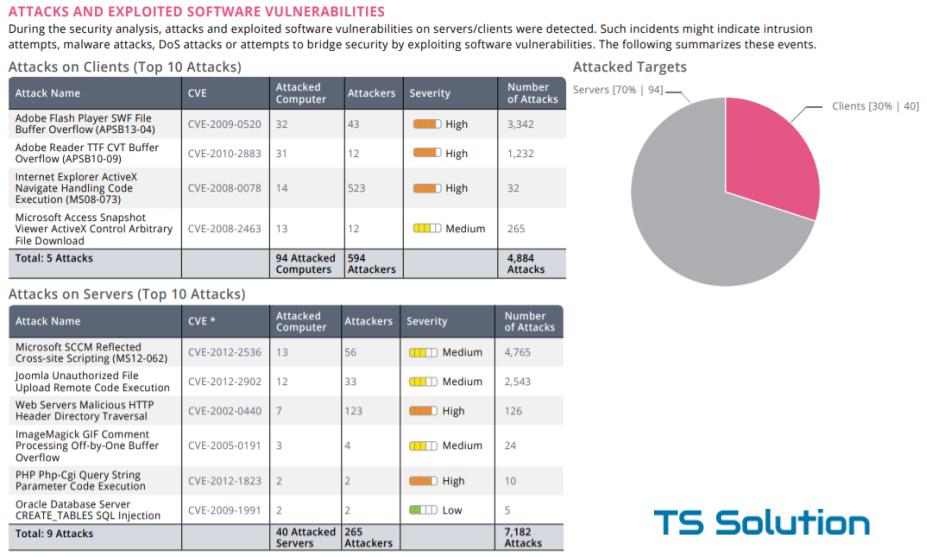
Moreover, not only users' computers can attack, but also company servers.
DDoS on company resources
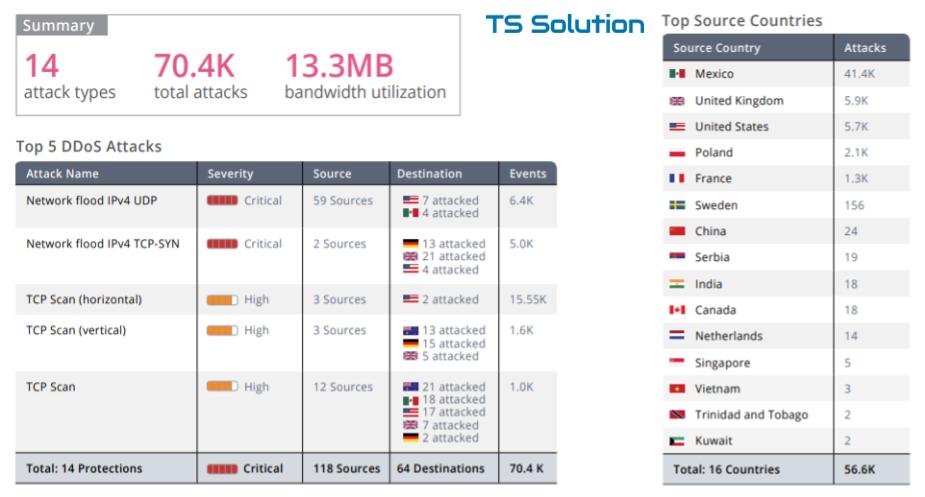
Of course, there are more virus download incidents (including 0-day) that current security tools do not catch. Similar problems are also very common. But they are more complex in their architecture and always require more detailed study (in the end, no one has canceled false alarms).
Conclusion
This concludes our small TOP-8 typical security problems. The main thing to remember is that information security is not a result, but a continuous process . And in this regard, Check Point Security CheckUP provides very good (albeit not complete!) Analytics on your security. And the fact that this audit can be conducted free of charge makes CheckUP almost the best solution in its field.
More information on Security CheckUP.
