Sync, share & secure - three in one with Acronis Access 7
Everything related to corporate security usually contradicts usability. Either users are dissatisfied with complicated content protection schemes, or the IT service is that users are about to spread important data all over the Internet through email services and Dropbox. Loud data leaks are heard by many. Everyone has heard about piquant celebrity photos stolen from iCloud, but when it comes to serious business content, there are more sophisticated schemes. So, Kaspersky recently discovered a case where hackers very selectively hunted top managers of large companies: they infected their devices through seemingly harmless updates that were downloaded when connecting to wi-fi in expensive hotels.
Since we at Acronis are busy with data security, we have for quite some time now a product that allows us to “kill two (or even three) birds with one stone”:
a) get easy access to corporate files from any device from anywhere in the world;
b) make sure that these files remain on the company's servers and under the control of the IT service.
c) make sure that these files remain on the company's servers and under the control of the IT service.
The product - Acronis Access - is well known, and in this post we want to talk about its new version, which is first divided by functionality into two specialized solutions and, by the way, has a completely new interface.

Modern companies have many business needs, and one of the main ones is the ability for employees to work with corporate information, wherever they are. We live in a mobile world, employees are constantly on the move, and the phone and tablet have long been a work tool for many. Many people are familiar with the situation when you have to work with a laptop in an airplane or in a car. At the same time, the standard option when sharing documents, presentations, videos, etc. is to upload them to the cloud (Google drive or the same Dropbox), even if the risks arising from this are well known. On a typical city trip in the backseat of a car, you can hook wi-fi from some cafe where you once sat, which also carries certain - albeit hypothetical - threats.

Of course, the IT department can monitor data security in public clouds, but this will require additional resources and will not eliminate many dangers. In addition, there is content that, in principle, is better not to leave the perimeter of the organization, although you need to work with it remotely. Finally, in some countries - and Russia will soon join them - certain types of content (the same personal information) should be stored domestically, and not travel in transnational clouds.
The problem is compounded by the fact that mobile devices are used for work, primarily by top managers, sellers and marketers, whose data is most valuable to business. They are the ones who need easy-to-use solutions that make security easy.
When we created Acronis Access 7, we tried to take into account all these factors.

For users, the product looks like an application that can be installed on any device - smartphone, tablet, laptop, PC or Mac. To get started, just log in to the application under your name.
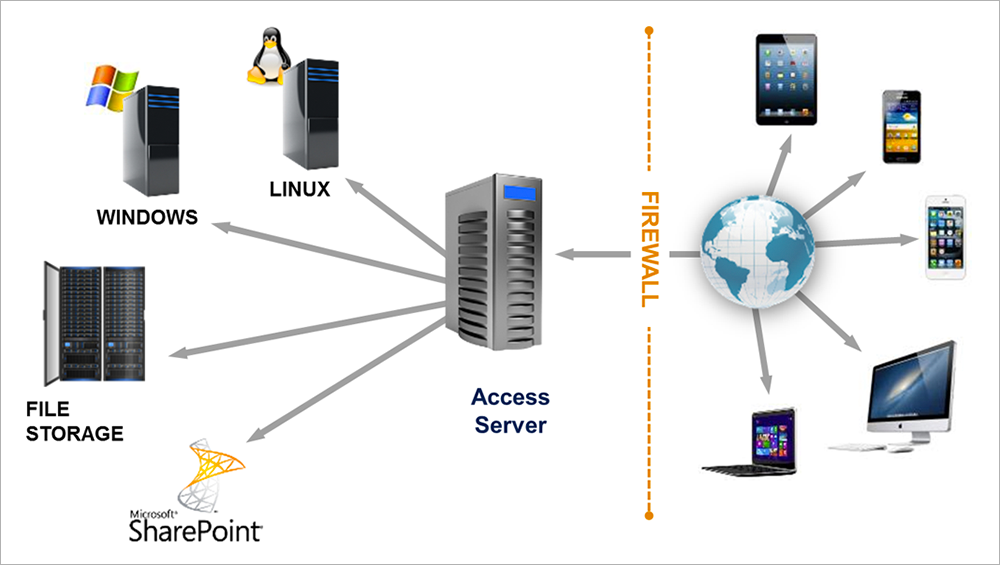
Acronis Access opens files stored on a corporate server: they are transmitted to the device via SSL in an encrypted format, and all changes are also sent back to the server in the form of a cipher (encryption standards on the server are AES-128/256 , as well as GOST 28147-89, which we already talked about in our blog; on iOS devices, data is encrypted using FIPS 140-2). It turns out such a very secure "box". You can safely work with a file from Australia or Japan, and the changes will be saved in the company's infrastructure in Russia - whether it be file servers, Sharepoint, NAS or other depositories.
Inside the application, the user can work with data of almost any format in a secure environment (container). The Open Office editor is built into the application, so Word, Excel or Power point documents are edited inside it; in the same way, you can comment on pdf-files, view videos and pictures.

At all stages, the IT service fully controls the shared data and determines access policies for it. The administrator sees who and when opened the document, what he did with it and under what login.


If the device is stolen or lost, Acronis Access features allow you to remotely erase all business information on it. Since the content leaves the corporate perimeter only in encrypted form, and all access to it is logged, the usual resources of the IT service are sufficient to protect it. The product automatically integrates with Active Directory and other standard account and policy management tools.
The new Acronis Access is fundamentally different from earlier versions in that under the common name two products are released - each for its own target audience. Easy to install and configure, Acronis Access 7 is designed for small and medium-sized businesses, and Acronis Access Advanced 7 with advanced configuration features is designed for companies with a staff of 100 people or more. The basic version differs from advanced in three ways:
But this version will cost significantly cheaper (per user).
Acronis Access Advanced 7 does not limit the number of users and connected servers. In this version, a more flexible access settings system that meets almost any request of large organizations: more than 50 policies are available in total. In addition, the advanced version can be integrated with leading MDM systems (Good Technology, MobileIron, Citrix, etc.). Both solutions are designed so that you can switch from simple to more complex in a few minutes - by purchasing a license and installing a new version on top of the old one.
Both versions of Acronis Access 7 consist of a client application for various platforms and the server side. The latter is a web service and can be installed on any suitable server in a corporate network or perimeter network. A file storage is connected to the server, which are located on the company's internal network and do not leave it without reliable protection. This is the main difference and advantage of the product compared to cloud services, where files go uncontrollably, and where they are also uncontrollably used.

When integrating with the corporate infrastructure, all existing rights, permissions and access policies are retained for existing files. The server side also provides remote access to files through a Dropbox-style web browser, but with nice additions to the interface and built-in tools for secure data sharing. Much attention is paid to transaction logs - all actions with data, users and policies are logged, there is a developed system of notifications for users and administrators.
Previous releases of Acronis Access performed well with large Western organizations - Deutsche Bank, Pfeizer. More modest in scale are the clients of the University of East Anglia and the administration of the Swiss city of Basel: the police, firefighters and the local Ministry of Health work here with a solution.
In the new issue, we tried to adapt the product to the Russian realities as much as possible. Both versions - Acronis Access 7 and Acronis Access Advanced 7 - support encryption according to the GOST standard, which is important for many government and state-owned offices. In the future, support for other specifically Russian formats and requirements. Finally, the basic functions of the application allow companies to solve several issues at once:
Of course, experience suggests that Acronis Access, like any application, can be made even better, more reliable and more convenient. Therefore, we will be happy to receive any feedback from the target audience.
If the product interests you, you can read more about it by clicking on the link .

Since we at Acronis are busy with data security, we have for quite some time now a product that allows us to “kill two (or even three) birds with one stone”:
a) get easy access to corporate files from any device from anywhere in the world;
b) make sure that these files remain on the company's servers and under the control of the IT service.
c) make sure that these files remain on the company's servers and under the control of the IT service.
The product - Acronis Access - is well known, and in this post we want to talk about its new version, which is first divided by functionality into two specialized solutions and, by the way, has a completely new interface.

Background
Modern companies have many business needs, and one of the main ones is the ability for employees to work with corporate information, wherever they are. We live in a mobile world, employees are constantly on the move, and the phone and tablet have long been a work tool for many. Many people are familiar with the situation when you have to work with a laptop in an airplane or in a car. At the same time, the standard option when sharing documents, presentations, videos, etc. is to upload them to the cloud (Google drive or the same Dropbox), even if the risks arising from this are well known. On a typical city trip in the backseat of a car, you can hook wi-fi from some cafe where you once sat, which also carries certain - albeit hypothetical - threats.

Of course, the IT department can monitor data security in public clouds, but this will require additional resources and will not eliminate many dangers. In addition, there is content that, in principle, is better not to leave the perimeter of the organization, although you need to work with it remotely. Finally, in some countries - and Russia will soon join them - certain types of content (the same personal information) should be stored domestically, and not travel in transnational clouds.
The problem is compounded by the fact that mobile devices are used for work, primarily by top managers, sellers and marketers, whose data is most valuable to business. They are the ones who need easy-to-use solutions that make security easy.
Product
When we created Acronis Access 7, we tried to take into account all these factors.

For users, the product looks like an application that can be installed on any device - smartphone, tablet, laptop, PC or Mac. To get started, just log in to the application under your name.
Acronis Access opens files stored on a corporate server: they are transmitted to the device via SSL in an encrypted format, and all changes are also sent back to the server in the form of a cipher (encryption standards on the server are AES-128/256 , as well as GOST 28147-89, which we already talked about in our blog; on iOS devices, data is encrypted using FIPS 140-2). It turns out such a very secure "box". You can safely work with a file from Australia or Japan, and the changes will be saved in the company's infrastructure in Russia - whether it be file servers, Sharepoint, NAS or other depositories.
Inside the application, the user can work with data of almost any format in a secure environment (container). The Open Office editor is built into the application, so Word, Excel or Power point documents are edited inside it; in the same way, you can comment on pdf-files, view videos and pictures.

At all stages, the IT service fully controls the shared data and determines access policies for it. The administrator sees who and when opened the document, what he did with it and under what login.

In the Acronis Access interface, you can specify in great detail the degree of access to data - up to how long the password should be, whether it is possible to copy something to a clipboard, print an open file, send it by mail, or “transfer” it outside the protected container.

If the device is stolen or lost, Acronis Access features allow you to remotely erase all business information on it. Since the content leaves the corporate perimeter only in encrypted form, and all access to it is logged, the usual resources of the IT service are sufficient to protect it. The product automatically integrates with Active Directory and other standard account and policy management tools.
Versions
The new Acronis Access is fundamentally different from earlier versions in that under the common name two products are released - each for its own target audience. Easy to install and configure, Acronis Access 7 is designed for small and medium-sized businesses, and Acronis Access Advanced 7 with advanced configuration features is designed for companies with a staff of 100 people or more. The basic version differs from advanced in three ways:
- You can scale the solution for a very small business (less than 25 employees);
- access settings here are not so thin: for example, there are no group policies;
- no more than three data servers can be connected to the product.
But this version will cost significantly cheaper (per user).
Acronis Access Advanced 7 does not limit the number of users and connected servers. In this version, a more flexible access settings system that meets almost any request of large organizations: more than 50 policies are available in total. In addition, the advanced version can be integrated with leading MDM systems (Good Technology, MobileIron, Citrix, etc.). Both solutions are designed so that you can switch from simple to more complex in a few minutes - by purchasing a license and installing a new version on top of the old one.
Architecture and implementation
Both versions of Acronis Access 7 consist of a client application for various platforms and the server side. The latter is a web service and can be installed on any suitable server in a corporate network or perimeter network. A file storage is connected to the server, which are located on the company's internal network and do not leave it without reliable protection. This is the main difference and advantage of the product compared to cloud services, where files go uncontrollably, and where they are also uncontrollably used.

When integrating with the corporate infrastructure, all existing rights, permissions and access policies are retained for existing files. The server side also provides remote access to files through a Dropbox-style web browser, but with nice additions to the interface and built-in tools for secure data sharing. Much attention is paid to transaction logs - all actions with data, users and policies are logged, there is a developed system of notifications for users and administrators.
Users and Benefits
Previous releases of Acronis Access performed well with large Western organizations - Deutsche Bank, Pfeizer. More modest in scale are the clients of the University of East Anglia and the administration of the Swiss city of Basel: the police, firefighters and the local Ministry of Health work here with a solution.
In the new issue, we tried to adapt the product to the Russian realities as much as possible. Both versions - Acronis Access 7 and Acronis Access Advanced 7 - support encryption according to the GOST standard, which is important for many government and state-owned offices. In the future, support for other specifically Russian formats and requirements. Finally, the basic functions of the application allow companies to solve several issues at once:
- Protect your data, which will be easy and convenient to work in any environment where you can connect a smartphone to the network;
- Save on additional IT support (which is not unnecessary in a crisis)
- Allow employees to work safely with corporate information through their personal devices;
- Comply with the requirements of the law on the storage of personal data, the entry into force of which is not far off.
Of course, experience suggests that Acronis Access, like any application, can be made even better, more reliable and more convenient. Therefore, we will be happy to receive any feedback from the target audience.
If the product interests you, you can read more about it by clicking on the link .
