Competitive Intelligence at PHD 2013

Hello!
I want to tell you about the Competitive Intelligence contest held as part of the Positive Hack Days - 2013 conference. You can read more about it here: www.phdays.ru/program/contests/#16276
In the Competitive Intelligence I participated in the second once, having already had some experience in similar work, and was looking forward to new conditions. One of the reasons why I wrote this article is that I still have not found answers to some questions from last year’s competition. I really hope that in this discussion we will bring together all the answers to the questions that were this year.
I will give answers to questions not in the order given in the terms of the competition, but according to the logical chain that led me to the correct answers. In the end I will describe the questions for which I have not found the answers.
I wrote this article after the closing of the contest, and its developers at that time had already closed some of the competitive sites, so do not be embarrassed if some links will no longer work.
I also note that the right answer at every step was born in agony, was the result of epic brain storms, trial and error, many dozens of tried options. And here I’ll just write about the scenario, close to ideal. Go.
Step 1.
This time it was necessary to answer 16 questions about the Godzilla Nursery Laboratory.
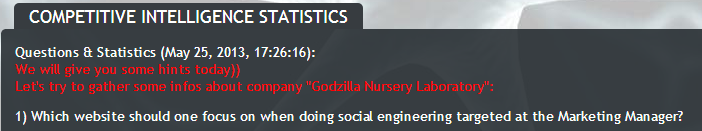
We are looking for the name of the company in Google:
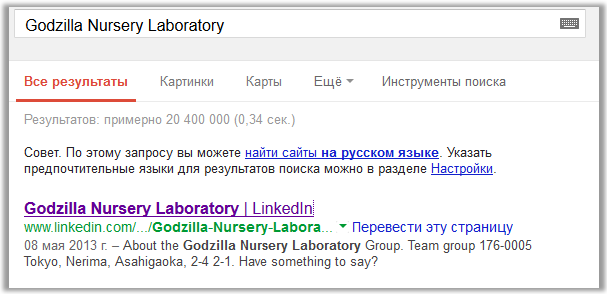
The first link is the Godzilla Nursery Laboratory group of companies on Linkedin, www.linkedin.com/groups/Godzilla-Nursery-Laboratory-5000097 :

We study the links on the group’s main page published by a certain Randi Klinger working in the position of "Marketing manager". They are all abbreviated using the bit.ly service and lead to different, unrelated, articles:
bit.ly/12LtZwC - wonderwall.msn.com/movies/angie-everhart-is-now-cancer-free-1752151. story
bit.ly/12txG8G - movies.msn.com/movie-guide-summer/11-things-we-love-about-original-star-trek-movies/photo-gallery/feature
bit.ly/YuDX4D - now.msn.com/angry-cats-a-photo-gallery-of-ways-to-piss-off-a-cat
bit.ly/13iaUmE - tv.msn.com/personalities-we -love-to-hate / photo-gallery / feature /? photoidx = 12
But hey, all of them are united by the fact that they are located on msn.com . I think it is msn.com that can be used for social engineering against the Marketing manager.
The correct answer is “msn.com”.
Step 2

In the news of the group on Linkedin we see that this group was created by a certain “Amber Lester”.
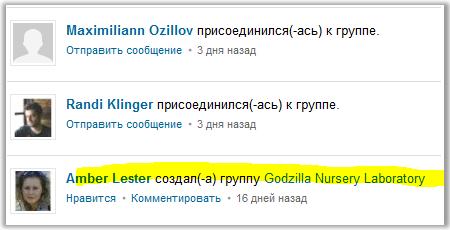
We study her profile. I note that her profile can either be found in Google, or go to her Linkedin page by clicking on the pop-up link on her name in the update feed.

Great, there is a profile, www.linkedin.com/pub/amber-lester/70/595/a1 :
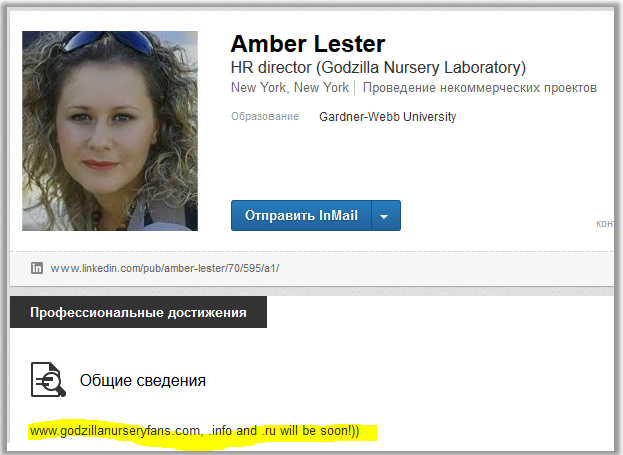
We have the name of HR director, as well as interesting sites indicated in her general information. We break through all these sites at www.whois.sc .
For the domains www.godzillanurseryfans.com and www.godzillanurseryfans.ru we get nothing interesting. And here on the www.godzillanurseryfans.info domain we see the following data:
Yes, Amber Lester mail is: mberlest@gmail.com .
I note that there was a difficulty in the competition, since there was still mail: amber.lester@godzillanurserylab.com , as well as the profile of the same Amber Lester “In contact” attached to it, vk.com/id210561328 . Whether this false trail was made by the creators of the contest on purpose or if it just happened is not clear.
The fact remains: amber.lester@godzillanurserylab.com is the wrong option.
The correct answer is "mberlest@gmail.com".
Step 3

Now we go to the official website of the Godzilla Nursery Laboratory company: www.godzillanurserylab.com . It's easy to find it - at the time of writing, this is the second and third link in Google for “Godzilla Nursery Laboratory”.
We look into robots.txt:

What is hidden for robots is interesting to us, we go to the "test" directory:
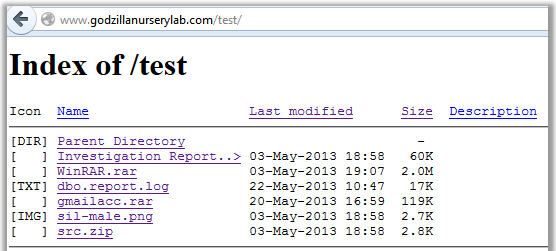
Download all the files. In addition, we get the archive with the password: "gmailacc.rar". We’ll hold other files for now, they will come in handy later.
We put brute: "gmailacc.rar". The * .rar archives are smoothed much slower than the * .zip
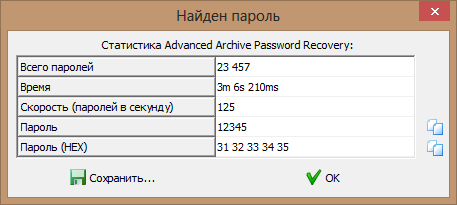
archives , however after 3 minutes we have an extremely complex password: The archive contains the file: gmailacc.PNG. Here is its main part:
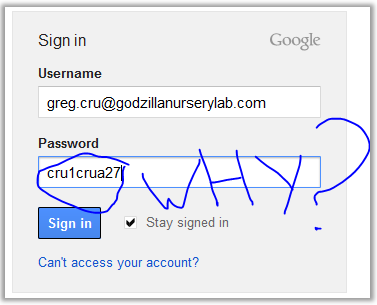
It looks like the mail address:greg.cru@godzillanurserylab.com , belongs to this comrade, which can be found at: www.godzillanurserylab.com/contacts.htm :

We try his email address and password "cru1crua27" to log into Gmail, however, since I wrote the article after the competition was closed, the developers managed to cover some things. I didn’t find the name of the company myself, but I didn’t remember the correct answer:
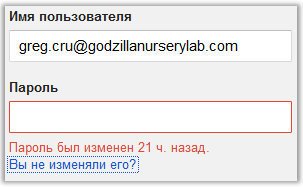
But from this step to the definition of its insurance company you are separated by seconds.
The correct answer: a hacked archive leads to it.
Step 4

By the link: www.godzillanurserylab.com/contacts.htm , we see the CEO:

He’s on Linkedin, www.linkedin.com/pub/maximiliann-ozillov/70/460/54b :
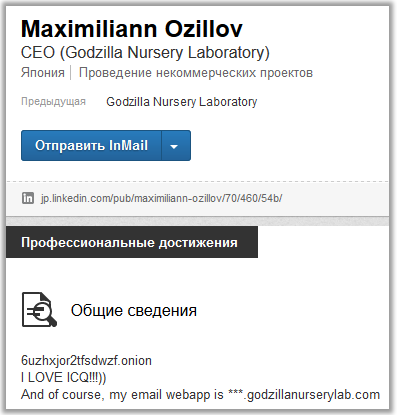
Wow, there is a lot of data about him! It is worth noting that the following data appeared as a hint only on the second day of the competition, on the first day this was not:
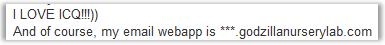
We work with the fact that he loves ICQ. We look in ICQ:
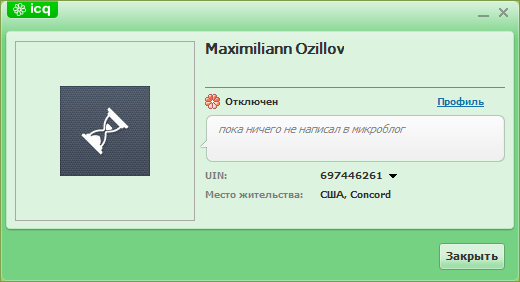
Found, check, maybe it's the same name. Click: "Profile". Yes, this is our object: The
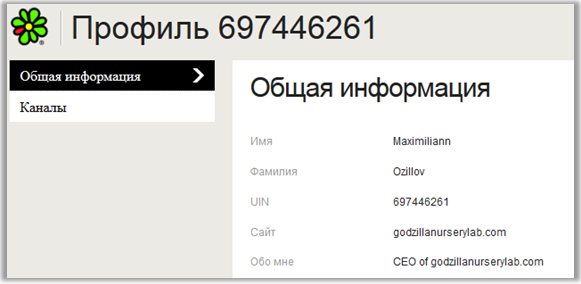
correct answer: "Concord".
Step 5

We turn again to Linkedin, on the CEO page: www.linkedin.com/pub/maximiliann-ozillov/70/460/54b , we see many of his colleagues.

Here, almost the whole friendly company, now we are interested in "Inessa Golubova", "Biological Engineering". We go to her page and, among other things, see:
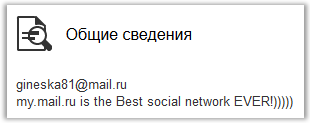
We go to My World, search by mail, find the profile, www.my.mail.ru/mail/gineska81/info :
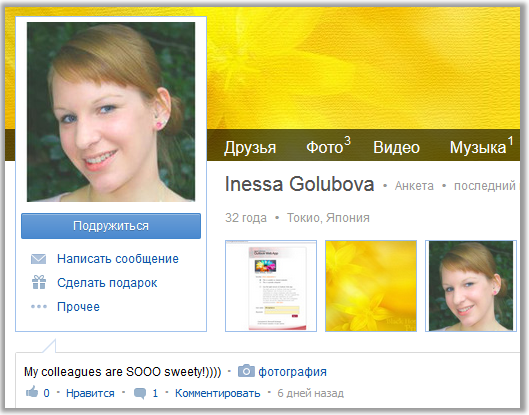
In her photos we see the picture we need:
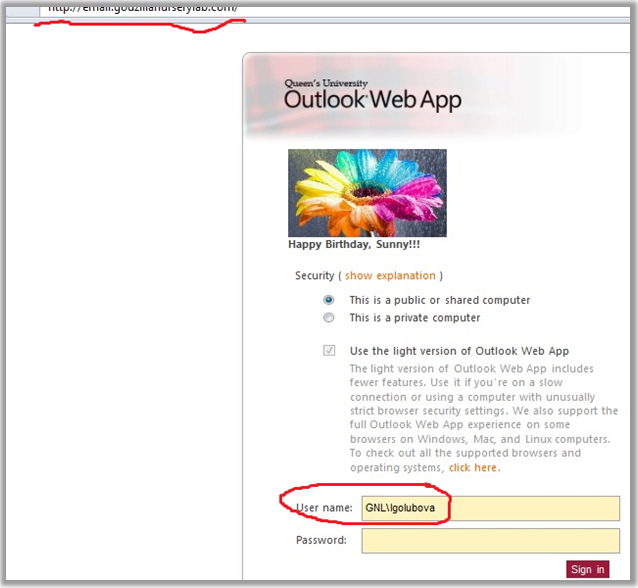
Pay attention to an important detail in the upper left corner of the picture, we see there the lower part of the address of the web version of the company’s mail: www.email.godzillanurserylab.com . This fact is useful to us further.
The correct answer is “GNL \ Igolubova”.
Step 6
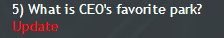
In step 5, we found the address of the web version of the mail: www.email.godzillanurserylab.com . We go to it and see the following form:

Pretend that we are CEO and that we have forgotten our mail password. By clicking on “Forgot your Password?”, We enter the mail: ceo@godzillanurserylab.com .
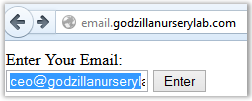
Great, such mail exists. We see the secret question:
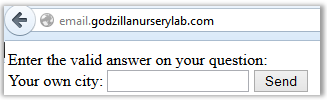
Oh, we already know this from step 4. Enter “Concord” and get a new password.
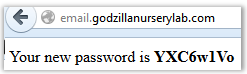
Now we go back to the email login form, www.email.godzillanurserylab.com , enter ceo@godzillanurserylab.com and password, we get into the "debug mode" of the mail. There we see a single letter with a small picture:

We hammer the image into Google image search and in a minute we find that it is "St James Park".
Correct answer: "St James Park."
Step 7

Going further through the list of SEO CEO colleagues on Linkedin. Now we are interested in a certain "Ivanes Inclam".
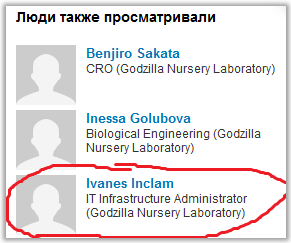
We just ask Google about it and get 3 links at once:

Ivanes Inclam asks for help on filtering settings for the firewall in three forums at once: The
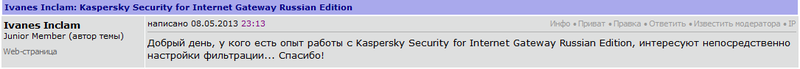
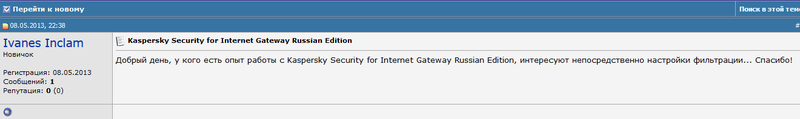
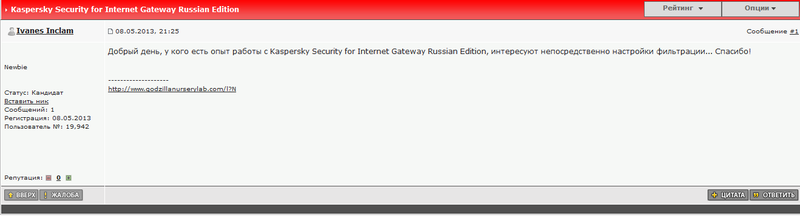
correct answer is “Kaspersky Security for Internet Gateway Russian Edition”.
Step 8

Now remember about the second encrypted archive: “Investigation_Report.zip”. It’s more interesting here. Although the archive is encrypted, you can view its contents:
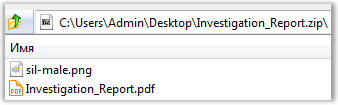
We see two files in it: “Investigation Report.pdf” and “sil-male.png”. It is noteworthy that next to this encrypted archive in the open are two more files:
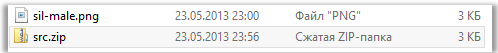
Total. We have:
- an encrypted archive, “Investigation_Report.zip”, containing in addition to the PDF file we need, a file “sil-male.png”
- an open archive, “src.zip”, containing only one file, “sil-male. png "
- the file itself," sil-male.png ":

Hmm, yes this is a hint of plaintext-attack. Its possibility arises when we have plain text and the corresponding ciphertext. More details here:
www.en.wikipedia.org/wiki/Known-plaintext_attack
www.ru.wikipedia.org/wiki/Attack_of_open_texts
I think there are several programs that can perform this attack, but I used the Elcomsoft Advanced Archive Password Recovery application. Specifying the attack type: “Plaintext” as the parameters, as well as the encrypted and open archives containing the same file, I launched the attack:
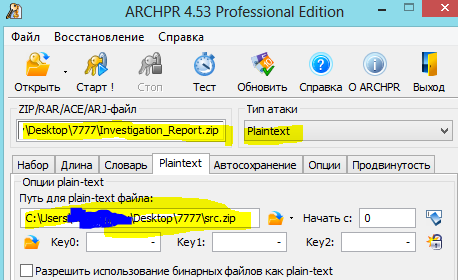
Twenty seconds, and we have an open archive without a password, in this case the password is not found.

The archive contains data on a certain “Robert Craft”:
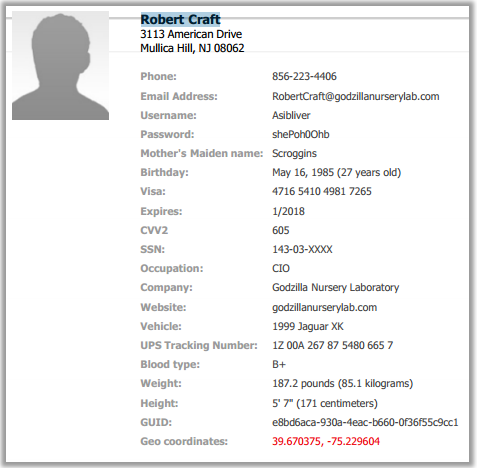
Yes, it turns out to be our CIO.
Correct answer: "Robert Craft."
Step 9
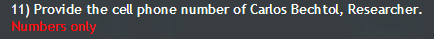
The profile of Carlos Bechtol is also on Linkedin, but it doesn’t give us anything interesting. We found his VKontakte profile: vk.com/id210334624 .
Here I note one more difficulty.
In the picture you see his phone after the first prompt of the organizers. Prior to this prompt, his number looked like this: "+7916 *** 13 **."
Before the tip, we found a profile of a certain “Carlos Bechtol” on Google+. But there was no data on the page. Then we manually picked up his mail: " carlos.bechtol@gmail.com ".
Then we checked that the password recovery form “ Vkontakte ” by e-mail “ carlos.bechtol@gmail.com ” clearly pointed to the page we needed.
We found the last two digits of the phone using the password recovery form for this mail on Google:

There was a question how to find the fifth, sixth and seventh digits of the number: “+7916 *** 1374”. And here we are again faced with a problem. We did not find profiles in other social networks. And the password recovery form “In Contact”, faced with increased interest in this profile, issued the following message:
“The allowed number of attempts has been exceeded. Please try again later. ”
It was a pity to miss a point for a practically found phone. After dozens of our attempts to reset the password, the contest developers gave a hint, after which the phone already looked like this: "791660413 **".
And so, as I think, why the prompt appeared. Everything turned out to be interesting. May 21, 2013, at the time of writing the post of Dmitry Evteev about punching the phone number of a person registered in the social network: www.devteev.blogspot.ru/2013/05/blog-post_21.html , the Vkontakte service when requesting a password reset gave out the whole 7 first digits of the number, and on May 24, on the second day of the competition, only the first three digits (operator code) and the last two digits were issued. Quickly, the guys from Vkontakte fixed this vulnerability.
The correct answer is “+79166041374”.
Step 10
On the CEO page it is indicated that the CEO worked earlier:
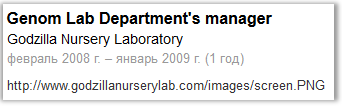
Follow the link, see the picture:

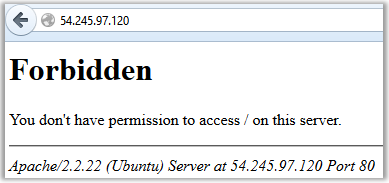
Increase and read the address: 54.245.97.120 and also see that after the last octet "120" there is an explicit colon, which means a specific port is entered. The site itself turned out to be unfriendly:
We recognize its ports using nmap: “nmap -p 1-65535 -v 54.245.97.120”
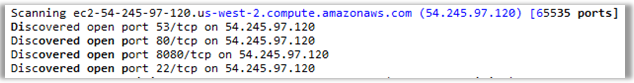
There are 4 open ports in total. The 22nd SSH port does not give anything, accounting is needed there. Brutus both the account and the password are a thankless task. The 53rd DNS port also gives nothing interesting.
We take the 80th port and manually sort through the TOP-10 of the most common directories: “admin”, “test”, “doc”, “upload”, “download”, “images”, etc. Nothing.
We take port 8080, iterate over the same TOP-10 list. Voila:
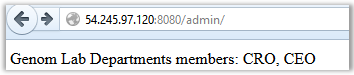
So, there are only two employees at Genom Lab Departmnet: CEO and CRO. We know the CEO mail: ceo@godzillanurserylab.com , and the CRO mail we find here: www.godzillanurserylab.com/contacts.htm The

correct answer is: "ceo@godzillanurserylab.com cro@godzillanurserylab.com"
Step 11
In the contacts on the main site: www.godzillanurserylab.com/contacts.htm , we see the person we need:

We are looking for him on Linkedin:
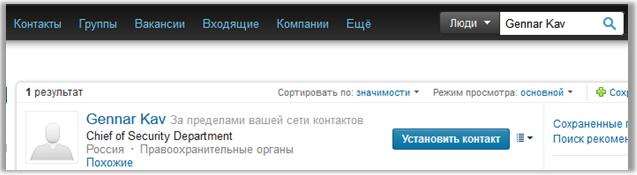
There is one. We get his home address:

We are looking for an address on Google maps, we see a house:
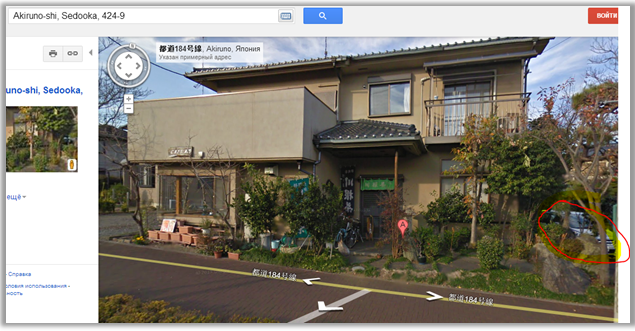
And on the right, behind the bushes, we find a car, we approximate it:

It looks like it's Honda.
The correct answer is Honda.
Step 12
On the CEO page on Linkedin: www.linkedin.com/pub/maximiliann-ozillov/70/460/54b , back to the general information:
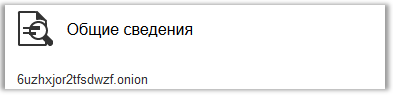
We see the site * .onion, which means we need Tor. Read more here who are interested: www.en.wikipedia.org/wiki/.onion . Download the Tor Browser Bundle and go to the site, or use the Tor gateway like 6uzhxjor2tfsdwzf.tor2web.org and see only one picture: A

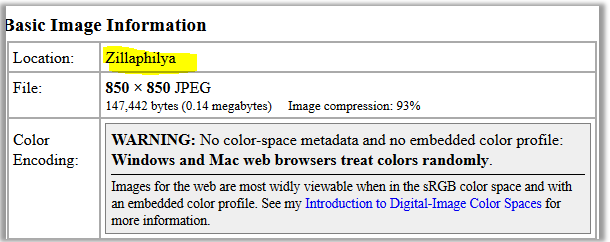
wide flight of imagination from the CEO. Obviously this picture is associated with the word "fetish". We look into EXIF pictures. More details here - www.ru.wikipedia.org/wiki/EXIF . Or open it with any hex editor. We will use the first available EXIF online viewer: www.regex.info/exif.cgi. We load the picture and see the word we need in the “Location” field.
Or in the hex editor we see the same thing: The
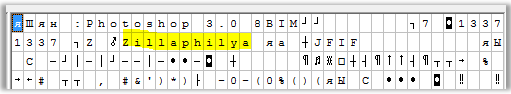
correct answer is “Zillaphilya”.
Step 13

We did not find an answer to this question, but there are clues. In particular, on Linkedin there is a person with the position of “Call center operator”: www.linkedin.com/pub/janice-harrison/70/a06/846 :
But a search on it did not lead us to success.
An unknown signature was also found when nmap scanned the resource previously mentioned in step 10: 54.245.97.120.

Options: "Cisco" and "Sisco", did not fit. This is already now I think that it was necessary to try SISCO TELECOM VOIP.
The correct answer: we will find it together.
Step 14
The clue is in the file: “dbo.report.log”, which we received together with the encrypted archives in step 4. In this file, among other things, there is a line of the form: “N: / DBO ***. GODZILLANURSERYFANS.INFO/www/favicon .ico »
Brute directories for different masks on" dbo ***. godzillanurseryfans.com "and other sites found did not give results.
The correct answer: we will find it together.
Step 15
We did not find this answer, without clues.
The correct answer: we will find it together.
Step 16
We also did not find this answer, without clues.
The correct answer: we will find it together.
Conclusion
At the end of the article, I note that this year the Competitive Intelligence competition has become more “technical”, for example, take the same hacking of archives. Sometimes it was seriously embarrassing in choosing a strategy.
There were also some inconsistencies, like two posts of HR director.
Another peculiarity that aroused a little attention was that the developers of the contest mixed the “Russian” segment of the network (“VK”, “My World”, etc.) with the “more western” direction (“Linkedin”, many places and addresses of objects were abroad). Enough time was wasted searching for people on Western social networks.
Since I wrote the article after the competition was closed, I could have made a mistake somewhere: for example, at the finish of Step 3. If anyone finds a blot, write, I will correct it.
I want to say thank you to “shisha”, with whom we fought together over the contest. You're doing fine! We did not have quite a bit to medals. But it was an important experience. I want to say thanks to the guys who took the first three places with nicknames: “azrael”, “topol”, “Det0” - this is what I clarified some of the answers after the award.
And thanks to the organizers of this competition and the entire conference, it was just a great celebration of information security! Keep it up!
Update : the developers of the contest on June 24, 2013 published its official passage, which can be read here .
