Atlas RIPE Probe
At the ENOG-4 conference, my attention was drawn to a table on which there were boxes with a RIPE NCC sticker, an RJ-45 port and a USB tail. Here are these:

I was not aware of what it was and what it was for, I went over this and asked. It turned out that this is an Atlas RIPE network probe, which you can take with you by registering at atlas.ripe.net . “We must take it!” I thought. After all, you can not pass by such a cute piece of iron.
At home, I started using the device, plugging it, according to the instructions, with a USB cord into the router so that there was power, and in the RJ-45 patch cord to the switch: The

probe almost immediately blinked lightly with fun, indicating that there was a link and packets were coming. What the probe actually does:
The probe itself receives settings via DHCP, does not have an interface, open ports, and nmap does not know anything about it (I changed the MAC address):
The interface is on the website atlas.ripe.net/atlas/myprobes.html . There you can see the status of your probe and the graphs that he drew:
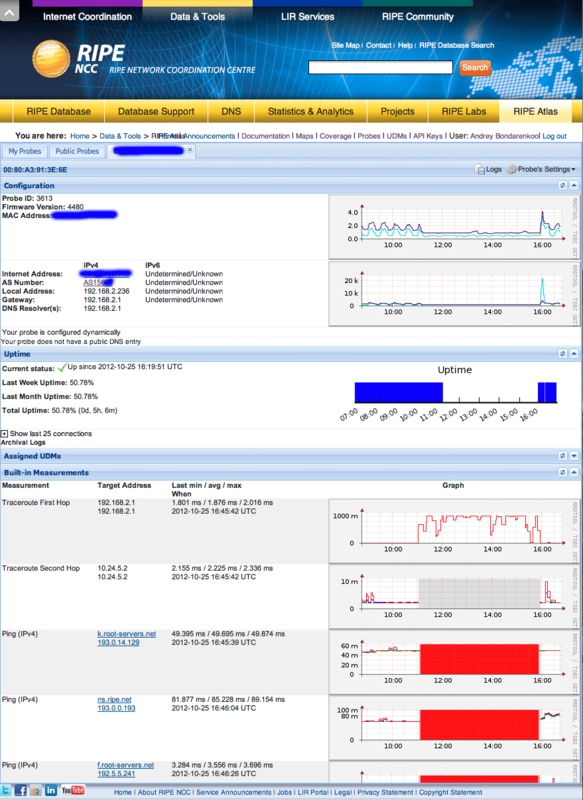
In addition to statistics on your own connection, you can create requests to foreign probes for ping (and some other operations) to the necessary hosts by selecting other people's probes by criterion (for example, country). This, of course, is not free, RIPE credits are spent, which are earned by uptime and participation in other people's requests (for more details, see here: atlas.ripe.net/doc/udm#the-credit-system ).
I did not disassemble the probe, as this would damage beautiful stickers, photos of the disassembled can easily be found on the network. Here's a flickr album on the subject: www.flickr.com/photos/hellercom/6854396415/in/photostream .
That's all!
UPDATE:
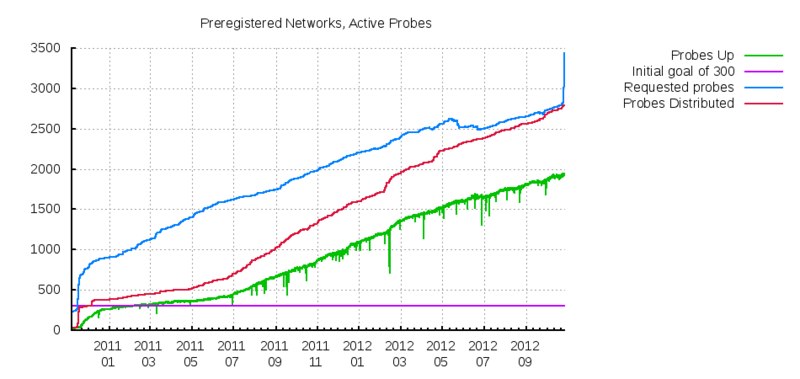
Habraffect in action!

I was not aware of what it was and what it was for, I went over this and asked. It turned out that this is an Atlas RIPE network probe, which you can take with you by registering at atlas.ripe.net . “We must take it!” I thought. After all, you can not pass by such a cute piece of iron.
At home, I started using the device, plugging it, according to the instructions, with a USB cord into the router so that there was power, and in the RJ-45 patch cord to the switch: The

probe almost immediately blinked lightly with fun, indicating that there was a link and packets were coming. What the probe actually does:
- The ping of the first two hop he sees. In my case, this is my router and provider router;
- Ping root DNS'ov;
- Performs pings on a mission
in the name of the moonfor the benefit of society and the owner;
The probe itself receives settings via DHCP, does not have an interface, open ports, and nmap does not know anything about it (I changed the MAC address):
[root@storage ~]# ping 192.168.2.236
PING 192.168.2.236 (192.168.2.236) 56(84) bytes of data.
64 bytes from 192.168.2.236: icmp_req=1 ttl=64 time=0.992 ms
64 bytes from 192.168.2.236: icmp_req=2 ttl=64 time=0.742 ms
64 bytes from 192.168.2.236: icmp_req=3 ttl=64 time=0.736 ms
^C
--- 192.168.2.236 ping statistics ---
3 packets transmitted, 3 received, 0% packet loss, time 2002ms
rtt min/avg/max/mdev = 0.736/0.823/0.992/0.121 ms
[root@storage ~]# nmap -O 192.168.2.236
Starting Nmap 6.01 ( http://nmap.org ) at 2012-10-25 20:47 MSK
Nmap scan report for 192.168.2.236
Host is up (0.0022s latency).
All 1000 scanned ports on 192.168.2.236 are closed
MAC Address: 11:11:11:11:11:11 (Lantronix)
Too many fingerprints match this host to give specific OS details
Network Distance: 1 hop
OS detection performed. Please report any incorrect results at http://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 3.40 seconds
[root@storage ~]#
The interface is on the website atlas.ripe.net/atlas/myprobes.html . There you can see the status of your probe and the graphs that he drew:

In addition to statistics on your own connection, you can create requests to foreign probes for ping (and some other operations) to the necessary hosts by selecting other people's probes by criterion (for example, country). This, of course, is not free, RIPE credits are spent, which are earned by uptime and participation in other people's requests (for more details, see here: atlas.ripe.net/doc/udm#the-credit-system ).
I did not disassemble the probe, as this would damage beautiful stickers, photos of the disassembled can easily be found on the network. Here's a flickr album on the subject: www.flickr.com/photos/hellercom/6854396415/in/photostream .
That's all!
UPDATE:
Habraffect in action!

