5 Free Microsoft Active Directory Health Monitoring Utilities
- Transfer
- Recovery mode
 Gary Olsen, MVP at Directory Services and a solution architect at HP, recently published a review of 5 free Microsoft tools that can be used to evaluate Active Directory health . This review seemed quite useful to us, so we decided to provide a translation here.
Gary Olsen, MVP at Directory Services and a solution architect at HP, recently published a review of 5 free Microsoft tools that can be used to evaluate Active Directory health . This review seemed quite useful to us, so we decided to provide a translation here. Interested parties are welcome to cat.
Health assessment of AD is already a problem in itself, especially for small and medium-sized companies that cannot afford to purchase expensive third-party solutions or hire an administrator who would only deal with AD administration.
The first manifestation of the "sick" Active Directory is an increasing flow of calls to support, which indicates a looming crisis. Fortunately, Active Directory itself can “recover” and even without being 100% healthy, it continues to work. However, precisely because of this, the problems that have arisen can be ignored, and the IT service switches to solving more important problems.
I recall how a couple of years ago, as one of the employees told me that the domain controller does not want to replicate. After analyzing the logs, it turned out that this CD was not replicated for almost three years.
Therefore, I decided to collect here 5 basic tools that help me in conducting a basic health assessment of Active Directory. All of them are free and relatively easy to use.
1. Active Directory Best Practices Analyzer
By releasing the Active Directory Best Practices Analyzer (ADBPA) utility, which is present in Windows Server 2008 R2, Microsoft has opened access to extensive Active Directory health information. Many administrators know Exchange Best Practices Analyzer (ExBPA). I expected from ADBPA the same level of detail in reports and in-depth analysis of AD best practices as from ExBPA, in terms of solving problems. ADBPA, of course, provides useful information, but I would like it to be more. ADBPA is available under the Active Directory Domain Services role in Server Manager, as shown in Figure 1.
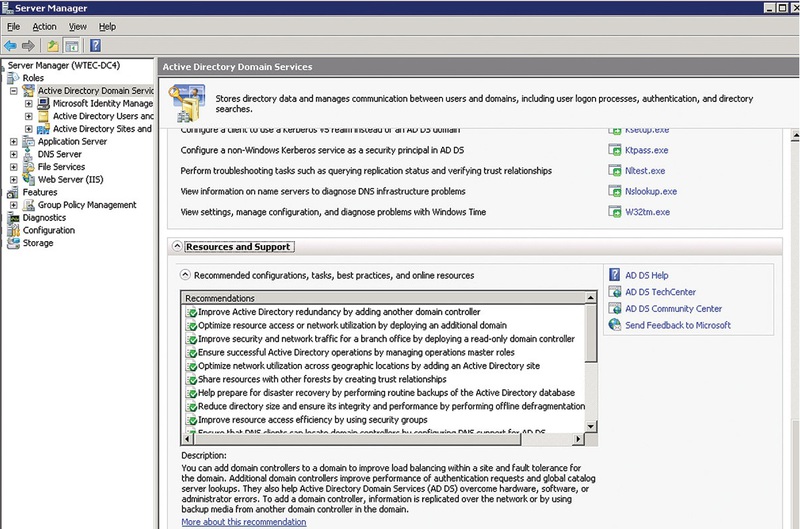
Please note that you can get a description of each entry simply by clicking on it. This example shows that all domain controllers marked in green correspond to the list of AD best practices. Errors and warnings are also shown. What is checked: all the hypervisor domain controllers are configured to a valid time source (? - valid time source), all domains have two functioning CDs, all OUs are protected from accidental deletion when the last backups were made; Are DNS configured correctly? Are Group Policy and FRS replicas working?
ADBPA is suitable for an initial AD health review, but still would like more information. For example, it does not show Active Directory replication information or if there are CDs that have not been replicated for a certain period of time (for example, during the lifetime of tombstone objects). The utility shows whether DNS works in such a way that allows clients to connect, does not indicate that the DNS server may be configured incorrectly.
2. MPS Reports
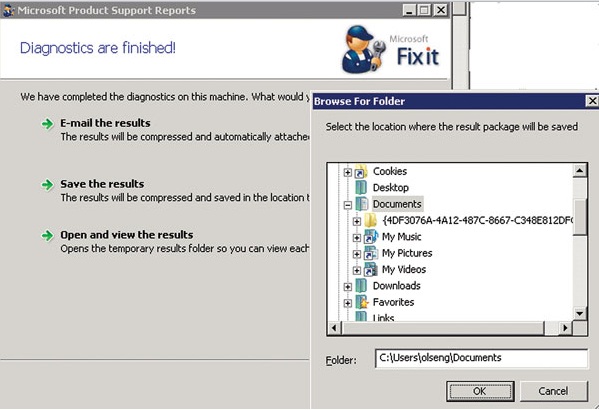
In the old days of Windows 2000, Microsoft released Microsoft Product Support (MPS) Reports, a script for diagnosing AD. First, it was released for Microsoft partners, and then for everyone. For me, this utility is a key tool for assessing AD health or resolving problems. The utility can be downloaded here . You must select either x86 or x64 installer version. When MPSReports.exe starts, the dialog box shown in Figure 2 appears. Note that MPS Reports requires administrator rights to collect the correct information, and requires the following components to be installed: Microsoft .NET Framework 2, Windows PowerShell 1.0, Windows Installer 3.1 and Microsoft Core XML Services 6.0.

Figure 3 shows the running diagnostic menu. Previously, there were several versions of MPS Reports for Networking, SQL, Exchange, Active Directory and other components. Now everything is included in one package and you just choose what you need. For AD issues, check out General, Internet and Networking, Business Networks, Server Components, and Exchange Servers.

Select “Link to more info” and you will see those files into which the utility collects information. Click “Next” to start collecting data for diagnostics - it will take some time.
The usefulness of MPS Reports is that the utility launches a number of command line tools and procedures and displays the results as a simple file in which it is easy to find information. For example, event logs can be collected in txt, ectx and cvs formats. I like the cvs format the most. You can open it in Excel and easily find or sort something, for example, by the error text, event ID, etc. Along with the txt version, cvs displays an event description for applications - so when you read them on your computer, you can see a description of events without loading the application (for example, Exchange and SQL).
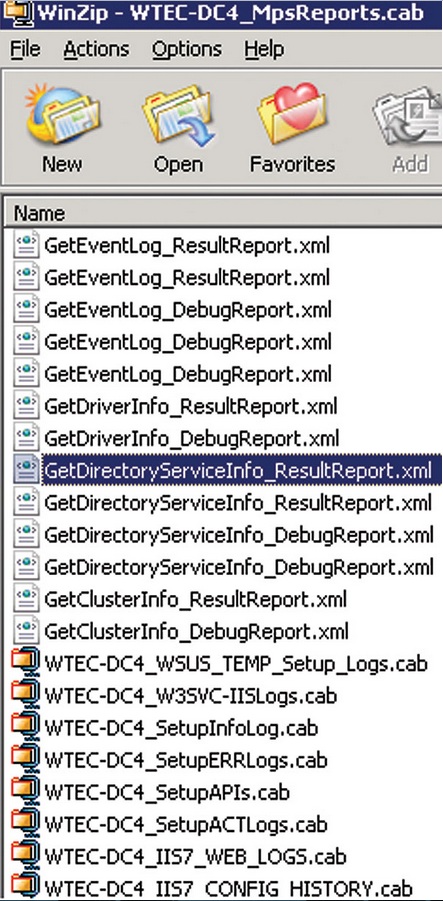
MPS Reports allows you to save the CAB file to any place, or you can open it immediately (Fig. 4). There will be one or several XML files in the CAB file (Fig. 5), which show various reports, so you will not need to run micro-reports one after another.
3. Repadmin and Replsum
Repadmin is a powerful command line tool to solve problems with Active Directory. The Replication Summary option, or the Replsum command, provides information about the replication status of all domain controllers in all domains in the forest. When evaluating the health of Active Directory, it is extremely important to know whether all domain controllers are replicated - and for those that are not, you will undoubtedly go to find out the last time that replication was carried out and why it became unsuccessful.
Repadmin provides quick answers to these questions. Using it can save a ton of time, as opposed to the widely used Repadmin / showrepl, which shows all domain controllers as a long list. The Replsum option analyzes all domain controllers in all domains in the forest and places information about them in a table that is easy to read. Use the following command:
Repadmin / bysrc / bydest sort: Delta> repadmin.txt
There are also other options and formats for this command, but I use only this one and it works great. Table 1 shows an example of what we get at the output.
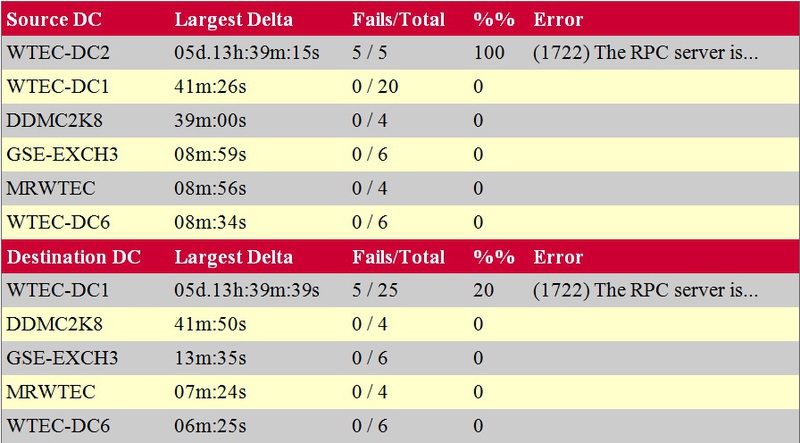
Notice that the Source DC list shows outbound replication and Destination DC shows inbound replication. For example, at the top of the list, WTEC-DC2 is the source domain controller and it has not been replicated for more than five days. This is outbound replication because WTEC-DC2 is the source when we receive the error message. Also, WTEC-DC1 did not perform inbound replication in the lower list, since it is the final domain controller. (Destination DC). The reason for this is indicated by event id 1722: the RPC server is unavailable. This error usually means that there is a communication error at the physical level in this domain controller.
Here is my advice: if replication did not occur during the tomstone lifetime, a record of “the largest delta” will be displayed> 60 days. This means that the domain controller does not have to be returned online, because it can introduce active lingering objects. You must manually lower and then upgrade the domain controller again.
4. DCDiag / Test: DNS
Besides replication, the other most common cause of AD problems is DNS. DNS is often the cause of failed replication. The problem is that in a large number of DNS environments, servers are installed on all AD domain controllers, which leads to an increased likelihood that DNS may fall. The study of each of them can be very time consuming. In Windows Server 2003, / Test: DNS was added to the DC diag command. Run the following command:
DCDiag / Test: DNS / e / v> DcdiagDNS.txt
This command will analyze each DNS server on the network and test the DNS server authentication, basic connection, sender configuration, delegation, dynamic registration and resource record registration. For the latter, DCDiag creates a test resource record and tries to register it. If this fails, new entries cannot be registered (which will lead to other problems).
The command displays three potential outcomes: Pass, Fail, and Warn. Prevention is not yet a problem, but rather an occasion to conduct additional analysis. For example, the Warn in the Dynamic Registration (DYN) column means that secure dynamic updates are not activated. This does not indicate failure, but you must be 100% sure that you want everything to remain as it is.
Table 2 shows typical team results.

Table 2 shows a complete and accurate report for all DNS servers in all domains on the network. In this way, we can check the health of the DNS. This table appears at the end of the DCDiag output. Details of these tests for each server are included in the DCDiag report before the final summary table is displayed. If the user who launched the command does not have privileges in this domain, the tests will fail.
In this case, the EMEA domain tests were unsuccessful because the user who launched DCDiag did not have the necessary rights. “N / A” appears when previous tests failed, so the remaining tests will depend on this “failure”. For example, in the EMEA-DC03 domain, Auth and Basc tests failed. The remaining texts are shown as N / A. DCDiag does not carry out further tests, but only puts N / A on each column. The Ext column is the fifth test to test external connectivity. DCDiag / Test: DNS does not check it by default.
Therefore, advice: List of domains and CDs in the table - convenient display of all domains in the forest and all CDs (which are DNS servers) in each domain. Thus, we get a map of the structure of domains and CD. In most environments, all CDs are DNS servers, so this is a convenient way to see the domain and CD structures.
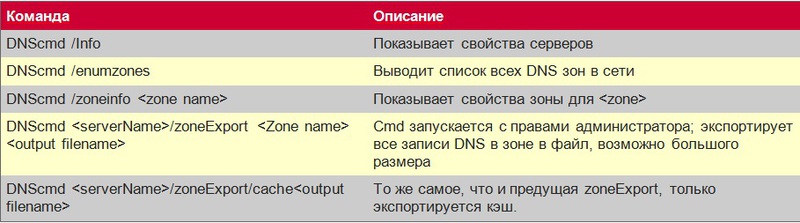
5. DNSCMD command line tool
If you are working on a remote system in an environment that you are not familiar with, or if you just want to get information about the DNS environment you are working with, the DNSCMD command will give you all the necessary information. Please note that I need this level of detail because I diagnose problems without access to the environment, and therefore I depend on reports that could give me the big picture. Those commands that I use are presented in Table 3. I would recommend using them even if you can access the DNS server - after all, sometimes it is much easier to see the necessary information in the report than to “wander” through the DNS interface. Also, these reports are periodically saved to files, so you can analyze the changes - especially if someone changed the config, and you want to know what parameters were before that. And of course,
There are other tools, such as the Group Policy Management Console (GPMC), which is great for analyzing group policies. GPMC also allows you to save a report on group objects as HTML, so that you can subsequently send it to the support service for analysis. GPMC is not included in MPS Reports.
Staying healthy!
The above tools allow you to quickly generate Active Directory health reports, and indicate problems. Of course, the administrator must make some efforts to run them, but the process itself is simple - especially if you use MPS Reports. In conclusion, my advice:
1. Use ADPBA as the tool for the broadest look at AD health
2. Download and run MPS Reports to delve deeper into solving the problem
3. Launch DCDiag / Test: DNS, Repadmin and Replsum as described above, to get a quick and easy-to-understand snapshot of DNS replication and configuration for all Active Directory health and highlight problem areas.
4. Use DNSCMD to get detailed DNS configuration information for offline analysis and comparison with previous configurations.
Nobody says that managing Active Directory is easy. But applying the recommendations described should provide better monitoring and management of Active Directory, providing a more secure environment for administration.
Source: redmondmag.com/Articles/2012/07/01/5-Free-Microsoft-Tools-for-Top-Active-Directory-Health.aspx?Page=1
P.S. Want to keep up with Active Directory changes? Our NetWrix AD Change Reporter program allows you to receive notifications and reports of any changes in AD. Find out more about the features of the program by downloading the 20-day trial version orby registering for a regular webinar .
