Problem solving with pwnable.kr 01 - fd. File descriptors and processes

In this article we will analyze: what is a file descriptor, how do processes access certain input / output streams, and solve the first task from the site pwnable.kr .
Organizational Information
Especially for those who want to learn something new and develop in any of the areas of information and computer security, I will write and talk about the following categories:
In addition to this, I will share my experience in computer forensics, analysis of malware and firmware, attacks on wireless networks and local area networks, conducting pentests and writing exploits.
So that you can find out about new articles, software and other information, I created a channel in Telegram and a group to discuss any issues in the field of ICD. Also, I will personally consider your personal requests, questions, suggestions and recommendations personally and will answer everyone .
All information is provided for educational purposes only. The author of this document does not bear any responsibility for any damage caused to anyone as a result of using knowledge and methods obtained as a result of studying this document.
- PWN;
- cryptography (Crypto);
- network technologies (Network);
- reverse (Reverse Engineering);
- steganography (Stegano);
- search and exploitation of WEB vulnerabilities.
In addition to this, I will share my experience in computer forensics, analysis of malware and firmware, attacks on wireless networks and local area networks, conducting pentests and writing exploits.
So that you can find out about new articles, software and other information, I created a channel in Telegram and a group to discuss any issues in the field of ICD. Also, I will personally consider your personal requests, questions, suggestions and recommendations personally and will answer everyone .
All information is provided for educational purposes only. The author of this document does not bear any responsibility for any damage caused to anyone as a result of using knowledge and methods obtained as a result of studying this document.
File descriptors
A file descriptor is a non-negative number that is the identifier of an input / output stream that may be associated with files, directories, or sockets.

The system file table (SFT - System File Table) and the inode table (INode Table) contains the information necessary for the process to access the file data. If several processes request access to the same file, then each of these processes will receive its own element of the system file table, despite the fact that they will work with the same file.
The kernel provides the file descriptor for the process when it accesses the file. We can say that a file descriptor is an index of an array of open files, which is unique for each process. But the first three indices are firmly fixed:
- 0 - standard input (stdin);
- 1 - standard output (stdout);
- 2 - standard error stream (stderr).
So the gets () and printf () functions from the C standard library use stdin and stdout, which allows shells to properly redirect process input and output.
Fd job solution
We click on the first icon with the signature fd, and we are told that we need to connect via SSH with the password guest.
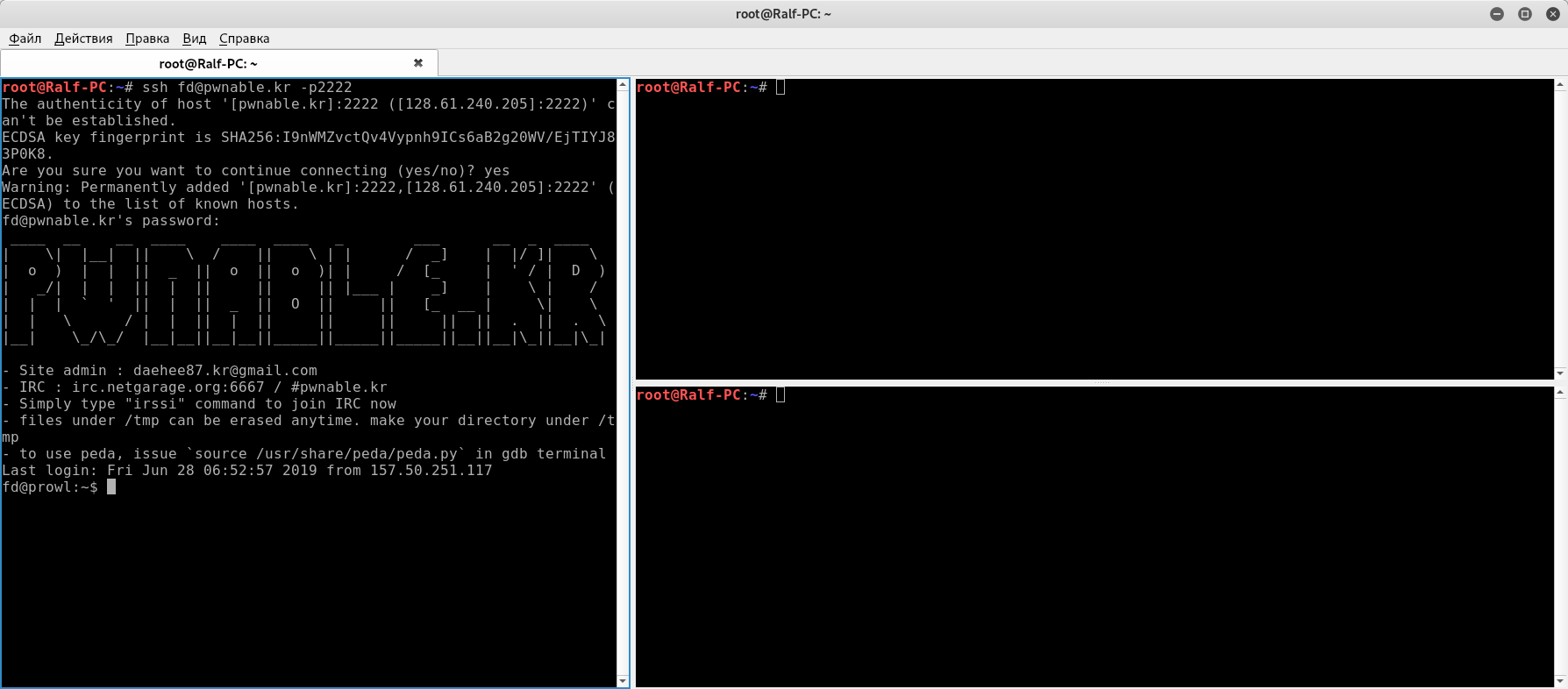
When connected, we see the corresponding banner.
Let's find out what files are on the server, as well as what rights we have.
ls -l
Thus, we can read the source code of the program, as there is a right to read for everyone, and execute the fd program with the rights of the owner (sticky-bit is set). Let's look at the source code.

It follows from the code that the program takes a number as a parameter, subtracts 0x1234 from it and uses it as a descriptor to get a string that should be equal to “LETMEWIN”.
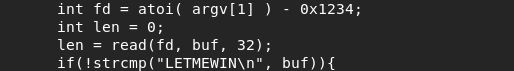
Thus, we need to send the program the string “LETMEWIN” through the standard input stream (stdin). For this, the descriptor that is passed to the read () function must be 0. That is, the number 0x1234 must be used as the program parameter. Convert it to decimal.
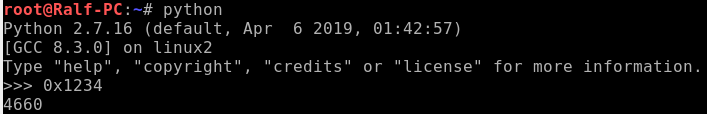
Now run the program with parameter 4660, drop the desired line and pick up the flag.
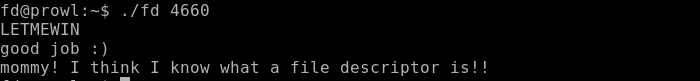
As a result, we get the first point.

Pwnable.kr begins with such an easy task, thanks to which it was necessary to deal with descriptors. See you in the following articles!
We are in a telegram channel: a channel in Telegram .
