Check Point Dashboards - That's What I Love
- Why are you rubbing me about a convenient interface? It doesn’t matter at all. I'm only interested in functionality! (from a conversation with a client)
When choosing NGFW (or UTM) most often they look exclusively at the device’s functionality . It is difficult to argue with this approach (and it is not necessary). The safety device must protect in the first place! Moreover, the quantity and quality of protection mechanisms is very important! For this, various reports of Gartner and NSS Labs are published. However, another important aspect of any NGFW is the integrated reporting and quality of its visualization . Below I will try to explain why this is important and why Check Point is really cool in this.
Why dashboards at all?
“ Information security is not a result, but an ongoing process .” I am sure that everyone remembers this axiom. In different literature, this process is described in different ways, but it necessarily contains 5 main stages:
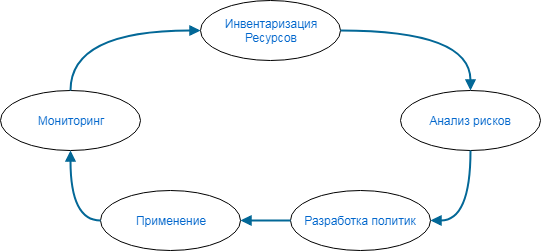
Today we will focus on Monitoring . Many are dismissive of this particular point. However, this is a big mistake. In this process, there are no more important or, on the contrary, lower priority stages. The degree of security of your network is determined by the weakest link. If you remove any of the elements, then the entire IB system collapses and all other “works” multiply by zero.
You supplied NGFW. Maybe even well-tuned in accordance with developed policies. But how to adequately evaluate its work? Are you attacking? Are users downloading malicious files? Do viral resources visit? Are email attachments safe? How often does this happen and is it worth paying attention to these issues? Maybe you should think about training users so that they do not open the first links that come across?
It is here that Monitoring is needed. And this is where SIEMs or Log-management systems are usually remembered . Using these tools, you can quantify the security of your network. You must understand what you have now and what indicators you want to come to. This helps to set goals for security. Examples of goals:
- Reduce incidents with bot activity on the corporate network - “cure” infected computers, think about changing / installing desktop antiviruses).
- Reduce by 2 times the number of events associated with visits to malicious sites. Most likely through user training.
- Reduce by 30% the number of downloaded virus files - for example, by blocking the download of executable files for most users or by blocking the category of resources from where they are most often downloaded.
- Eliminate incidents involving the detection of “dangerous” applications like Tor, Teamviewer, Torrent, etc. on the network. (user training + group policies).
- Optimize your IPS settings by eliminating triggering on signatures that are irrelevant to your infrastructure. Perhaps 30% of all hits are attacks on Wordpress, which you do not have in principle. Such logs strongly “rustle” the real picture.
- Get rid of events with the same type of attacks from the same nodes. There are a huge number of hosts on the Internet that can automatically scan your network. You should not spend resources on them processing this traffic with the IPS, it is better to add their IP addresses to the black list and block them at the firewall level. There was already an article on how to do this .
It is here that we will need various dashboards, which in numbers will show what is happening on the network in terms of security.
And then Check Point or any other NGFW? We ourselves said that SIEM or Log-management systems are usually used for monitoring and analysis. Yes, but do they all have? Are everyone ready to spend money on this? Does everyone have a trained specialist? If the answers to the questions are negative, then the presence of a “SIEM type” function in NGFW becomes a fat plus . Built-in reporting enables a continuous protection process. And this is a prerequisite for information security.
Ready Check Point dashboards
The Smart Event blade is responsible for reporting and data visualization at Check Point . This functionality can be safely called SIEM, but only for Check Point products! Technically, on Smart Event, you can wrap logs from other systems (cisco, microsoft, etc.), but this is not a good idea. In practice, this is very problematic. But SmartEvent does an excellent job with checkpoint logs. It can correlate, summarize, average and much more. Of course, there are ready-made dashboards for displaying the most important information. In Check Point they are called Views :

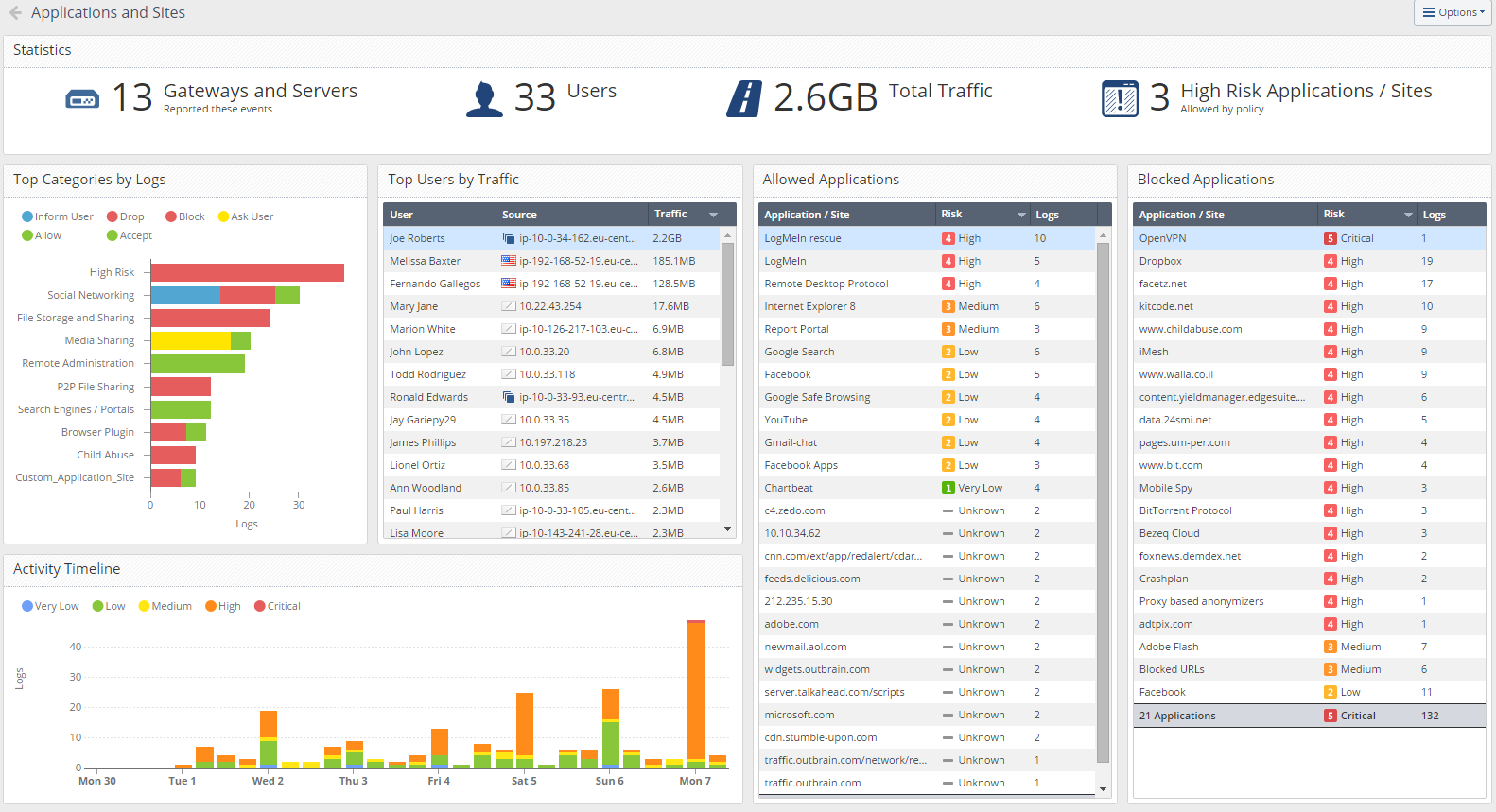
As you can see, there are dashboards here not only related to information security, but also reports on user traffic. Example dashboard Applications and Sites :
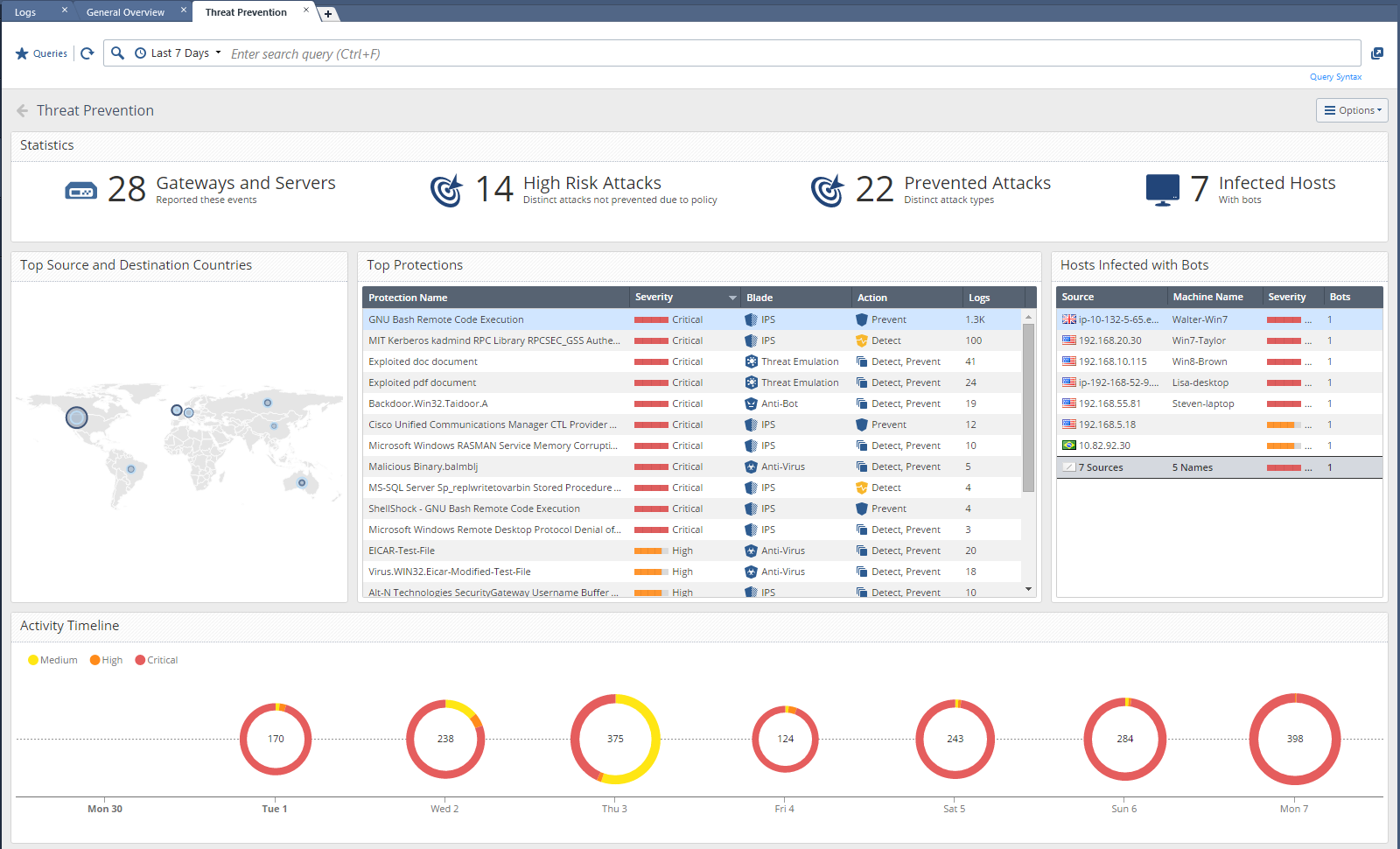
And here is an example of the Important Attacks dashboard :
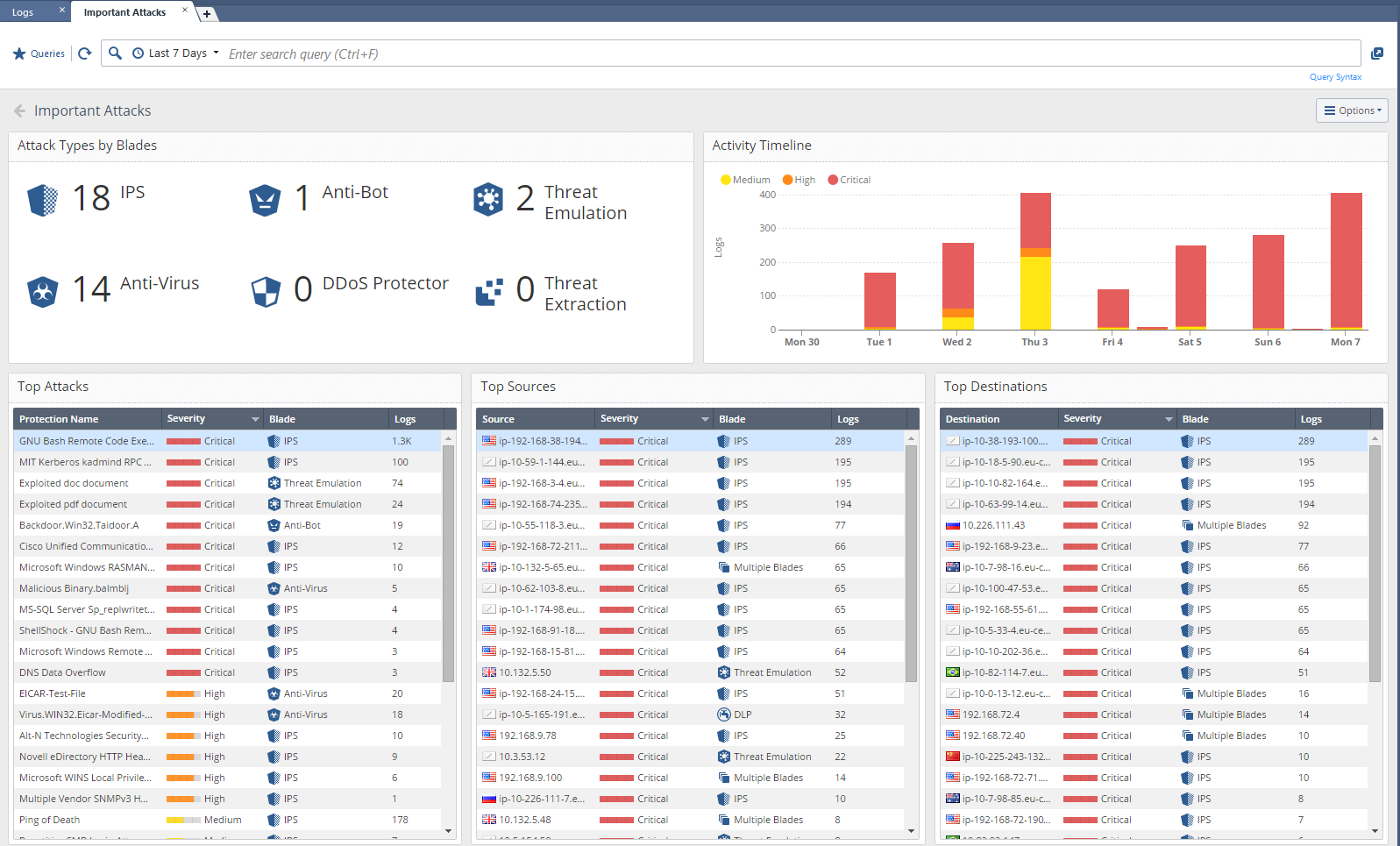
On one screen we see the most important information security events. It can be seen which blades were triggered (IPS, AV, Anti-Bot, Threat Emulation), all the trials are divided into categories with a total of logs. There is also a timeline. Absolutely all fields are “clickable” and if we want to look at the information on Anitivirus in more detail, then just double-click on it. We immediately fell into the logs associated with this blade:
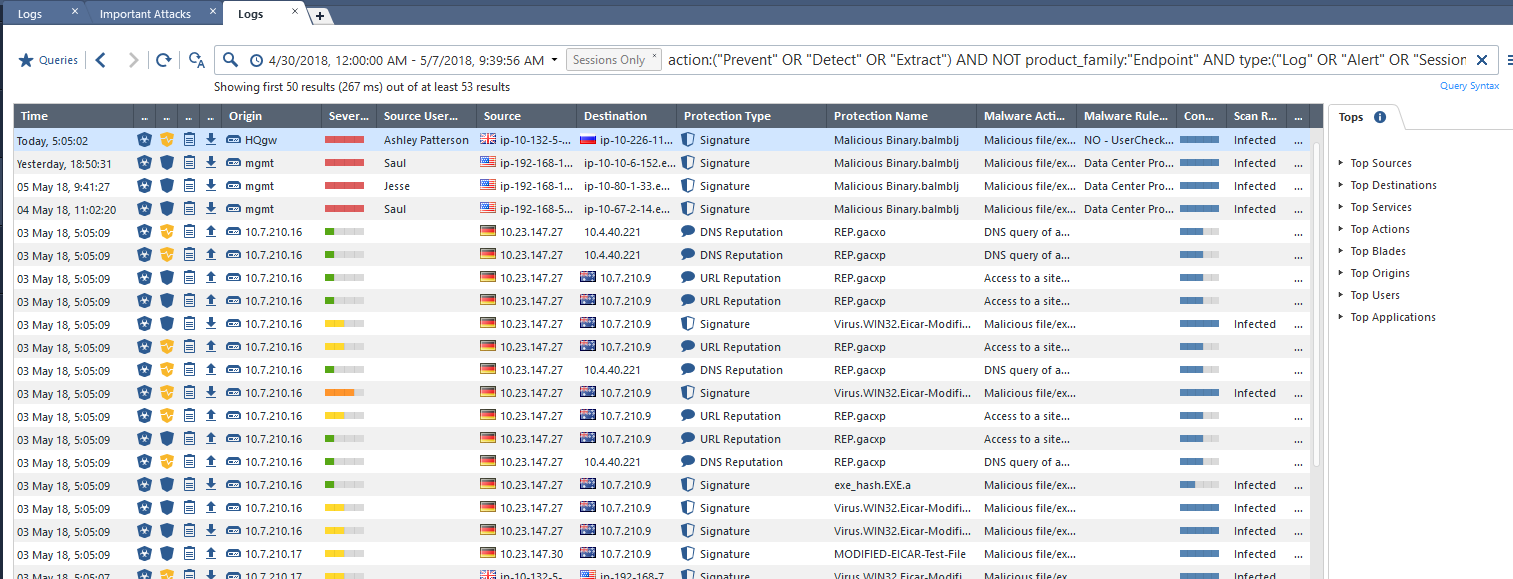
I will not talk in detail about the convenience of working with logs. But the search and filtering is really convenient here. Here is a link to the Logging and Monitoring R80.10 Administration Guide . This is a comprehensive guide.
The most commonly used dashboards can be added to Favorites for quick access:

Another plus that appeared in R80.10 is the ability to access dashboards and logs directly from the browser, without the need to install SmartConsole. To do this, in the browser, go to https: // management-ip-address / smartview. As a result, we will see about the same thing:
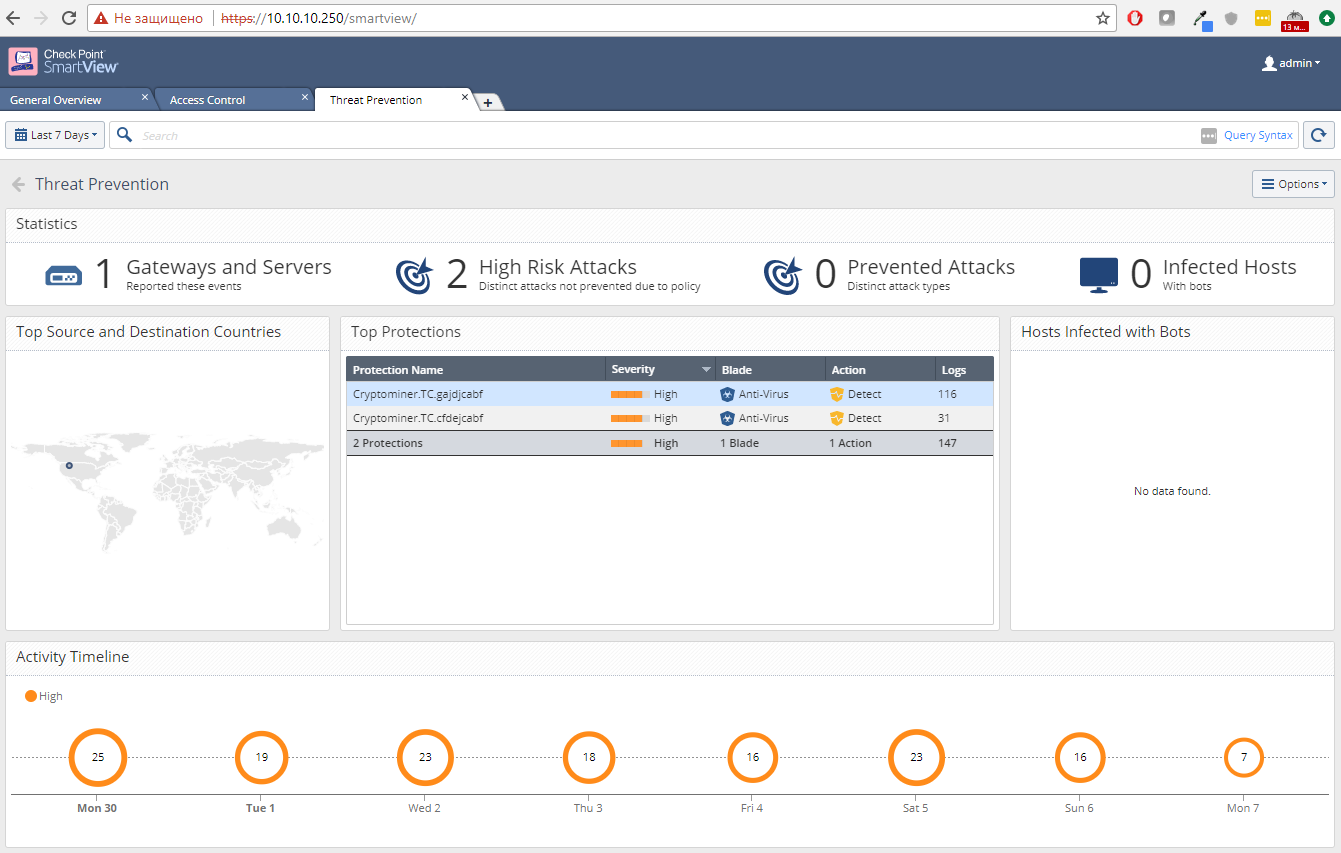
This is very convenient when you need to give your boss access to the dashboard. And of course, this allows you to watch reports from under Linux and MacOS (a full-fledged SmartConsole is available only for Windows).
Create your own dashboards
But the coolest thing about Smart Event is not the presence of built-in dashboards, but the ability to create your own! Moreover, it is implemented very simply, no code, everything is done through a graphical interface. The process of creating your dashboard is as follows:
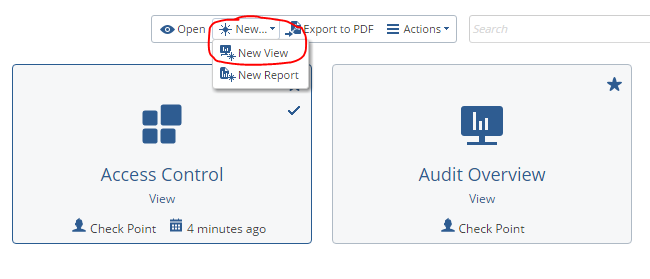
1. Create a new dashboard New - New View
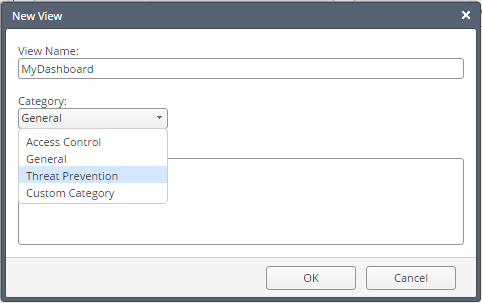
2. Give a name and define a category
3. Add a new Widget
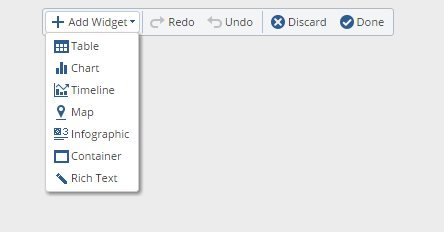
As you can see here several options are available at once. We will select a table.
4. Let's create a plate in which file types will be displayed and the number of antivirus operations for them. To do this, first add the File Type :
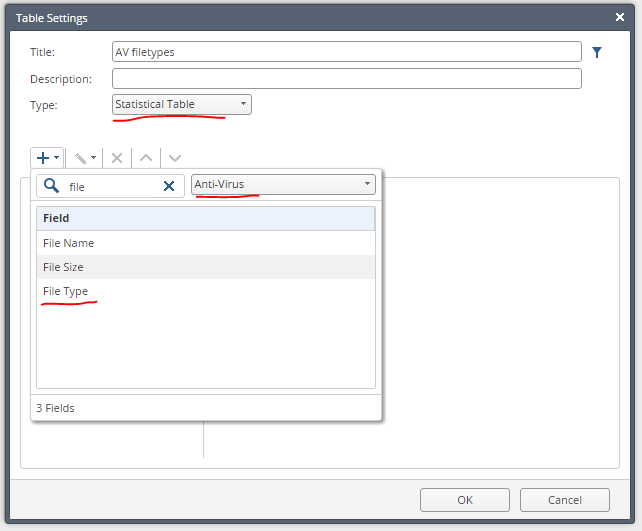
5 field. Add the Action :
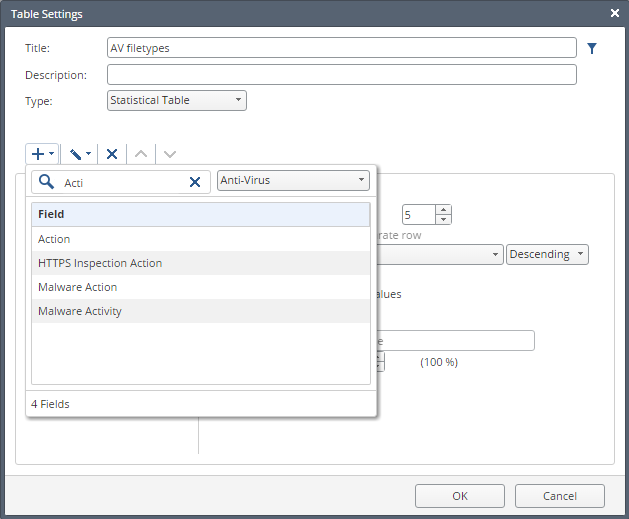
6 field . And add the Logs field.to see the number of responses:

7. It will turn out something like this:
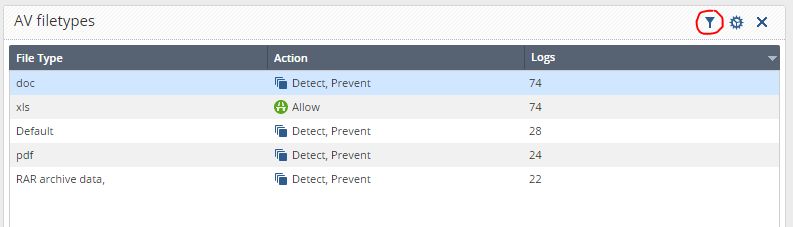
As you can see, the events of Allow, Detect and Prevent are displayed here. And we are only interested in Prevent .
8. Add a filter by clicking on the icon (circled in red circle):
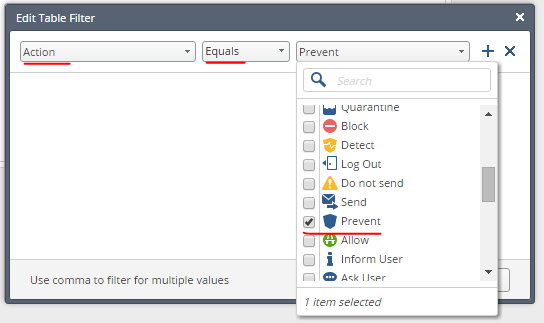
9. Applying the filter, we get the final result - file types and number of antivirus triggered by them:

The same statistics can be obtained in the form of infographics. Using these widgets, you can create dashboards for virtually everyone.
Import and export dashboards
Another big advantage of these dashboards is that they can be imported and exported.
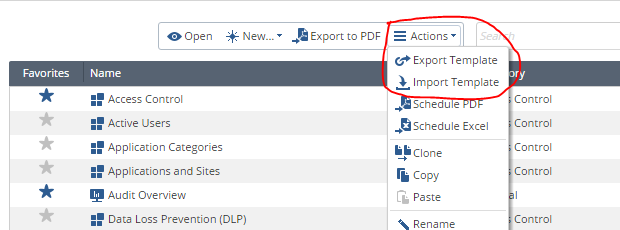
Those. You can create a dashboard and share it with a friend. Or vice versa, install a dashboard developed by someone. For example, most recently, the official Check Point ( CheckMates ) community published a new dashboard in the public domain - the Threat Prevention Cyber-attacks dashboard . It looks like this:

There are still many pictures, I will not duplicate, better look in the original .
Conclusion
In conclusion, I would like to clarify again that I in no way wanted to say that embedded analytics is the most important in information security tools. Of course not. The quality of information security functionality (Anti-Virus, IPS, etc.) is much more important here. But if excellent analytics and convenient dashboards are still attached to this, then this is a good plus.
In general, good reporting can always be obtained using third-party and even free solutions. These are various SIEM or Log-management systems. Splunk, ELK, MaxPatrol, ArcSight, of your choice. For example, for Splunk, we have already developed our own Check Point dashboard. You can read about how to do this here , or simply contact us by mail .
In order not to miss other lessons, subscribe to ourYouTube channel, VK group and Telegram .
PS You can play with dashboards in demo mode. How to do this, see here .
PSS Get a trial license and test the solution you are interested in here
Only registered users can participate in the survey. Please come in.
What tools do you use to analyze logs from firewalls?
- 31.2% I use the built-in analytics 5
- 31.2% I use paid SIEM / Log management systems 5
- 25% I use OpenSource system 4
- 25% Don't use anything 4
