Securely sign Android builds from Jenkins
- Tutorial
Translation https://www.detroitlabs.com/blog/2017/05/24/securely-signing-jenkins-android-builds/

The secure signature of Android assemblies in Jenkins CI (Continuous Integration, hereinafter simply CI) is a common problem. We tried several options for the whole time of development and each of them looked a little dirty ... except for one.
First, a small introduction: CI is a very significant tool for the development team. When used correctly and frequently, it can significantly reduce the time spent debugging and resolving conflicts. The problems are visible to the whole team and can be quickly resolved, assembly results help determine the root of the problem, and testing helps prevent regression errors. CI also automates the delivery of your builds, so testers or customers instantly get the latest work results.
So, our options are:
Include the signing certificate for the assembly directly in the repository itself: Bad!
Only if you do not use a private repository, do you actually open your certificate to the whole world. Even if you use a closed repository, you place the certificate on the machine of each developer, which greatly increases the chances that the certificate will leak.
Download the signing certificate to the Jenkins file system and reference it from Gradle: Not bad ...
This is not bad because it allows us to use the minimum number of places and can be protected by the same means that regulate access to Jenkins. One caveat is that you still have to save your password and key name somewhere in the file system. Finding a way to do this safely can be tricky. This solution may also turn out to be not the easiest to use if you have several projects and several assemblies and each of them needs a certificate.
Using the plug-in for signing Android applications (Android Signing Plugin): Great!
This is a great, clean solution for storing and signing applications on your Jenkins. The plugin uses the standard Jenkins store to work with your certificates. This limits the number of developers who need to know passwords, helps securely store certificates, and allows all assemblies to easily access the certificate.
How to configure and use Jenkins Android Signing Plugin:
The first thing you need to do is make sure Credentials Plugin is installed on your Jenkins .
This can easily be checked by looking at the left panel in your Jenkins. If you see the "Credentials" section as shown below, then it is installed.
If you don’t have the Credentials section, you need to remember to install the Credentials Plugin, this can be done at the same time as installing the Android Signing Plugin.
Installing the plugin takes place in a few easy steps:
Select the “Manage Jenkins” section as shown below.
Select "Manage Plugins."
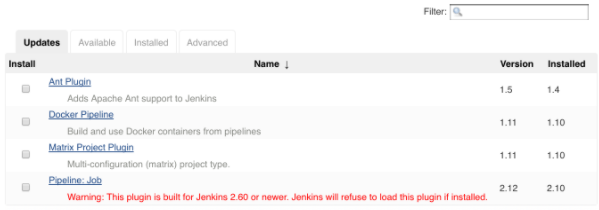
You will need to see the available updates for the current plugins. At the top of the screen, select the "Available" tab.
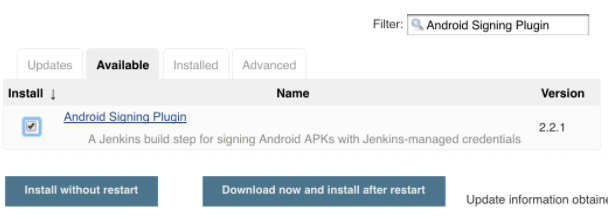
- Now you can use the search in the upper right corner to find "Credentials Plugin" (if it is not installed) and "Android Signing Plugin". Check the boxes on the left side for each plugin, then click "Download now and install after restart" at the bottom of the screen.
Excellent!
Now that everything is installed, you can add at least one certificate for signing applications. Detailed instructions for using the Credentials Plugin are not the subject of this article, but can be easily found on the Internet . You need to add one new certificate as shown below.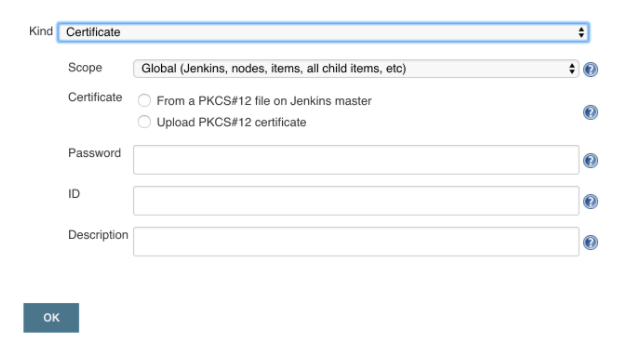
As you can see, the plugin only supports PKCS12 certificates. Unfortunately, the latest version of Android Studio issues JKS certificates, which turn out to be incompatible with the plugin.
It’s good that we have a convenient command line utility “keytool” that can turn our “JKS” into “PKCS12”.
keytool -importkeystore -srckeystore {REPLACE_WITH_JKS_FILE} -srcstoretype JKS -deststoretype PKCS12 -destkeystore ConvertedCertificate.p12Once you have the "PKCS12" file, you can download it. Be sure to enter the password before uploading the certificate, otherwise Jenkins will not be able to download the file. Now you are ready to use this certificate for any Android builds.
The only requirement for the source code is that you need to leave " signingConfig " empty for the "buildType", which will be used when building Jenkins'om. Then an unsigned APK will be created, which can be signed by the plugin. Keep in mind that a standard debug build is signed with an automatically generated certificate.
Now everything is ready for signing applications, you need to add the "Sign Android APKs" step to your assembly. Below is a simple example, first we run the Gradle command to build an unsigned release build. After that, in the next step we can sign the build. You must select the certificate that you would like to use from the certificate store, specify the key alias and path to the unsigned APK.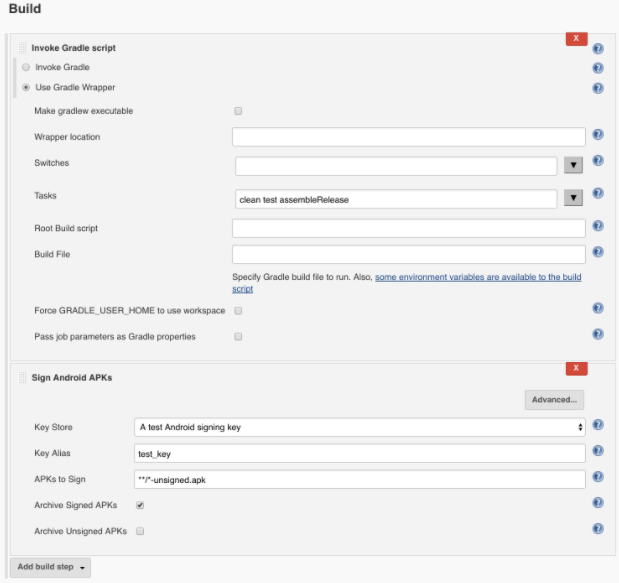
It's all! You now have a signed build, ready for distribution immediately after the build.
By the way, Google has its own certificate store , which partially solves the problem of secure key storage.
Only registered users can participate in the survey. Please come in.
Where do I keep a certificate backup
- 42.5% In Cloud Storage 17
- 12.5% Locally by car 5
- 17.5% on a flash drive. I gave the flash drive to my grandmother for storage. 7
- 10% Sent to the manager, customer, all developers and testers. One may ask, if that, anyone. 4
- 17.5% Why do I need a backup? 7
