Configure information backup to the Microsoft Azure Backup cloud
This article contains instructions for setting up backup of information to the Microsoft Azure Backup cloud encrypted using CryptoPro EFS and accessing this information via USB tokens and smart cards, for example, JaCarta manufactured by Aladdin R.D. .
CryptoPro EFS software is designed to protect confidential information when it is stored on a PC. Also, the CryptoPro EFS software is intended for use with the CryptoPro CSP CIP version 3.0 (ZHTYA.00015-01 30 01) and CryptoPro CSP version 3.6 (ZHTYA.00050-01 30 01) in Microsoft Windows XP / 2003 / Vista / 2008 / W7 / 2008 R2.
USB tokens and smart cards JaCartaDesigned for strong authentication, electronic signature and secure storage of keys and digital certificates.
In general, the essence of implementing two-factor authentication in Microsoft Cloud is to increase trust in the Microsoft cloud provider and the general level of security by providing single sign-on and implementing enhanced two-factor authentication on ALL cloud services and local resources using external devices - smart cards (or USB tokens) .
The EFS organization has three servers based on Windows Server 2012 R2:
Employees of the organization connect to RDS.EFS.LOCAL to access applications and store their working documents on it.
It is necessary to ensure data security by encrypting and backing up to Microsoft Azure geo-distributed cloud storage. Data is accessed using a private key, which is safely stored on a USB token or smart card.

CryptoPro PRO CSP in this example must be installed on:
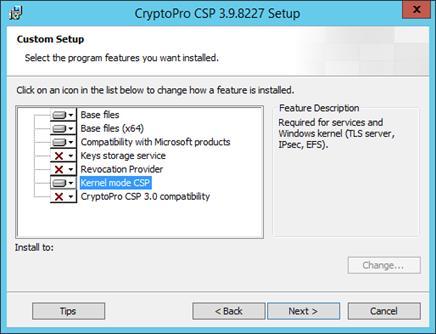
During installation, select Custom and select the Kernel mode CSP component for installation .
On all PCs and servers where you plan to use smart cards, install the JaCarta Single Client software .
Install with the default settings.
On the users PC and Remote Desktop Server, install the CryptoPro EFS software (version no lower than 1.0.1318).
Install with the default settings.
Installation should only be done after installing CryptoPro CSP .
In this example, 3 accounts and 2 groups are used. The following accounts will be required for demonstration.
Accounts:
Groups:
The group of EFSComputers must include computers that will use EFS encryption using the GOST algorithm. In the present example, it will be RDS.EFS.LOCAL .
This example uses a simplified installation of a Certification Authority (hereinafter CA) using only the root CA.
On the CA.EFS.LOCAL server , add the CA role: Server Manager -> Management -> Add Roles and Features .
Using the Add Roles and Features Wizard, select the Active Directory Certificate Services role to install .
When choosing a role service, you must select a Certificate Authority .
After the certificate service installation is complete, you must configure it.
From the Server Manager, open the service settings dialog.
After entering an arbitrary sequence for generating a key, a dialog for entering a PIN code will be displayed. Set the PIN code for the container ZK.
Export the CA certificate to a file that is accessible to the domain controller. To do this, use the Certificates snap-in (local computer) .
Specify a custom certificate name, for example efs_root_ca.cer .
You must initialize three keys for users: DCAdmin, efsRA, K.Sobchak .
In this example, the DCADmin account is used as the registration agent .
Log in as a DCAdmin user to CA.EFS.LOCAL and from the Certificates snap-in -> current user request a GOST certificate . Registration Agent .
Use a smart card as a container (for DCADmin ).
After the certificate of registration agent is issued, it becomes possible to issue certificates for other users on behalf of DCADmin .
From the DCAdmin user , using the Certificates → snap-in snap- in, complete the GOST certificate request for the EFS Recovery Agent for the efsRA user .

Issue the certificate on a smart card designed for efsRA .
Export this certificate to a file.
Similarly, issue a GOST Certificate Login with a smart card .
It is carried out similarly to the previous one, only it is necessary to use the GOST templates Basic encryption and GOST Login with a smart card .
And on the Certificates tab, uncheck Allow EFS to create self-signed certificates if the Certificate Authority is unavailable .
You must add the CA certificate to the list of trusted Certificate Authorities.
To do this, create the Trusted Certificates policy in the Computer Configuration → Policies → Windows Settings → Security Settings → Public Key Policy → Trusted Root Certificate Authorities → Import section . Select the certificate efr_root_ca.cer .
Issue a service, self-signed certificate using the CryptoPRO EFS Management Console utility .
My certificates → All tasks → Create a self-signed certificate.
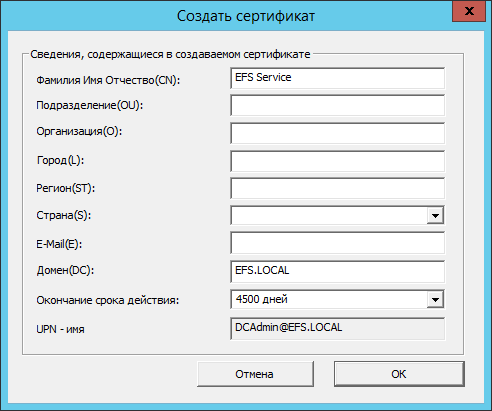
Next, export the certificate from the Certificates snap -in, the current user in two formats: with export of the private key (.pfx) and without export of the private key (.cer).
Import the certificate with the private key .pfx into the Personal store of the computer, and the certificate without the private key .cer into the store Trusted persons of the computer.
Leave the PIN code blank when importing.
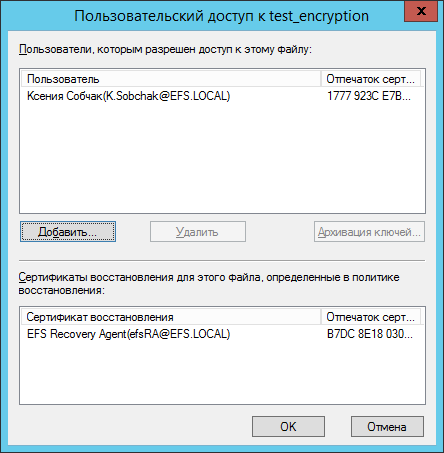
Now you can check file encryption on RDS.EFS.LOCAL . To do this, connect using a smart card to the RDS server.
In the Documents directory, create a file and encrypt it by setting Other → Encrypt contents to protect data in the file properties .
Click the Details button . If everything went smoothly, the following window will be displayed.
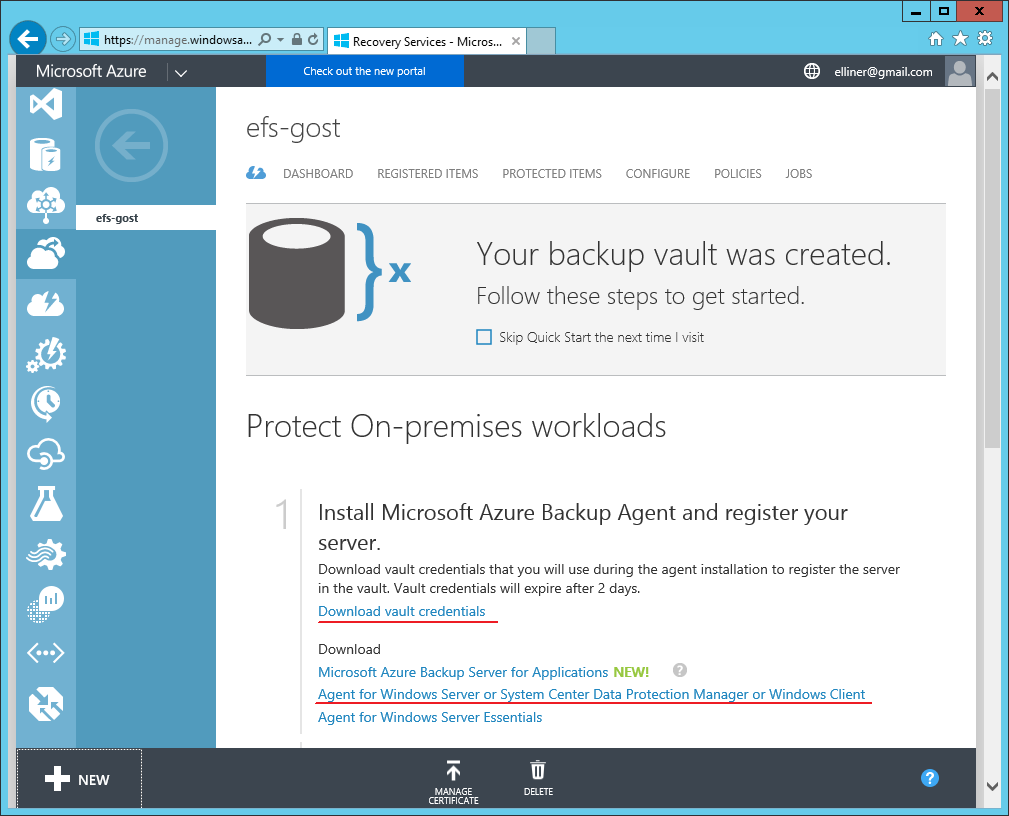
To start the backup, you need to register a new storage in Azure.
To do this, go to http://manage.windowszure.com . Next, log in with your Microsoft account to the Recovery Services menu item . Go to NEW → Recovery Services → Backup Vault → Quick Create .

Specify the name of the repository, for example, efs-gost . And select a storage region, for example, North Europe .
After creating the vault, download the credential file and the Azure Backup client using the provided links.
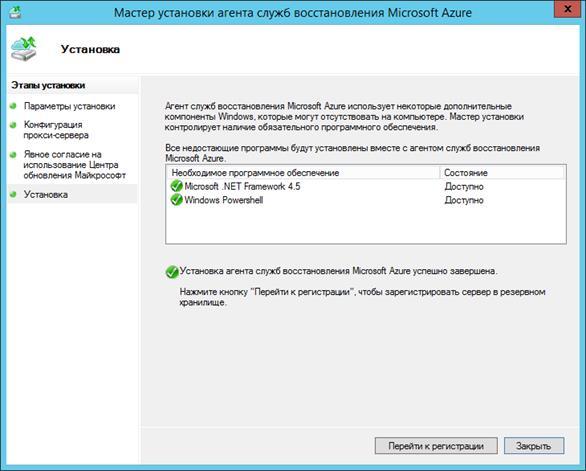
Install the downloaded Azure Backup Agent with the default settings. During the installation, if necessary, the missing components (.Net Framework, Powershell) will be installed.
When the installation is complete, click the Go to registration button .
The following window will appear, select the credential file downloaded earlier.
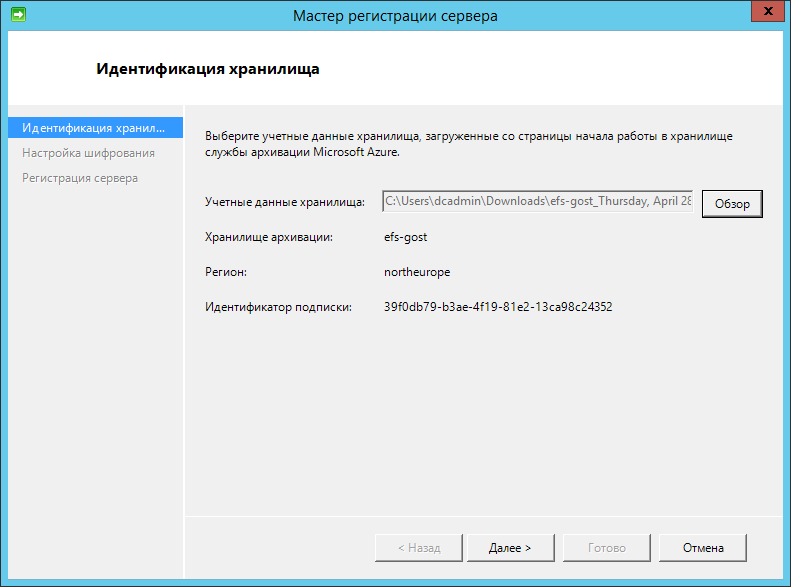
Create a passphrase and specify the path to its recovery file.
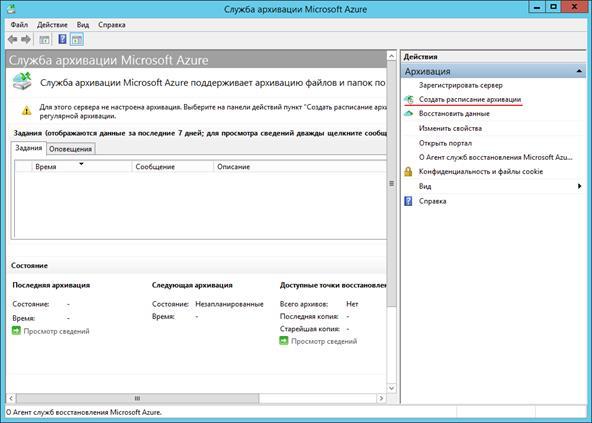
When registration is complete, the Microsoft Azure Backup Service window opens . Create a backup schedule in it.
In the selection of items for archiving, specify the folder with user profiles.

Leave the rest of the settings by default.
To check the settings, click Perform Instant Backup .
Restoring from a backup is similar.
Call the data recovery dialog by clicking the Restore data button .
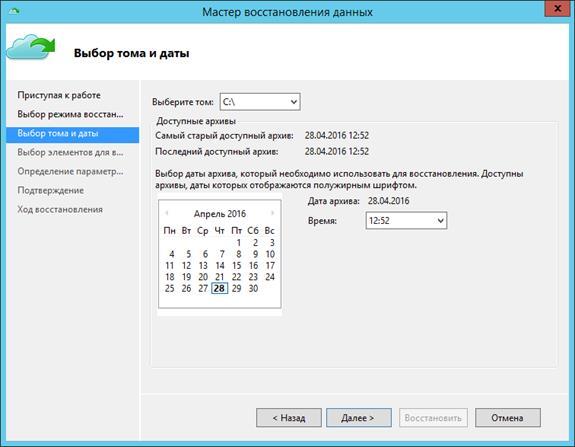
Choose This server → Browse files → Select volume and image date and time .
Next, select the files to restore.
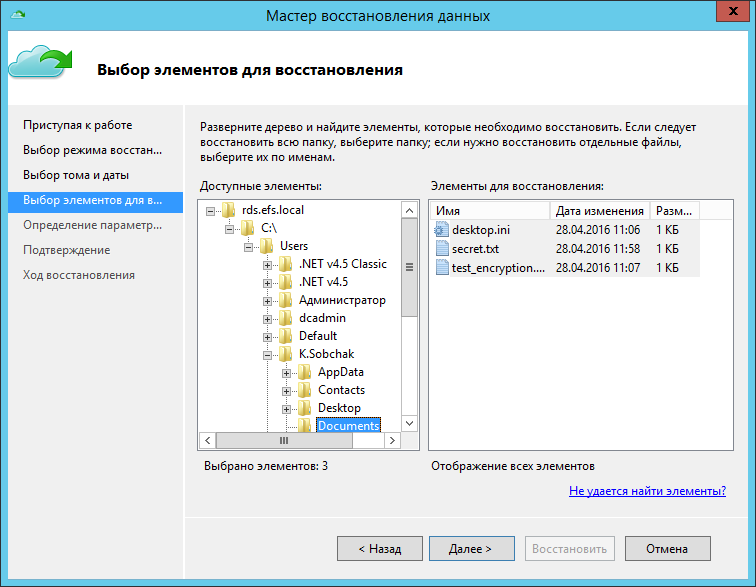
Select a location for the recovered files.
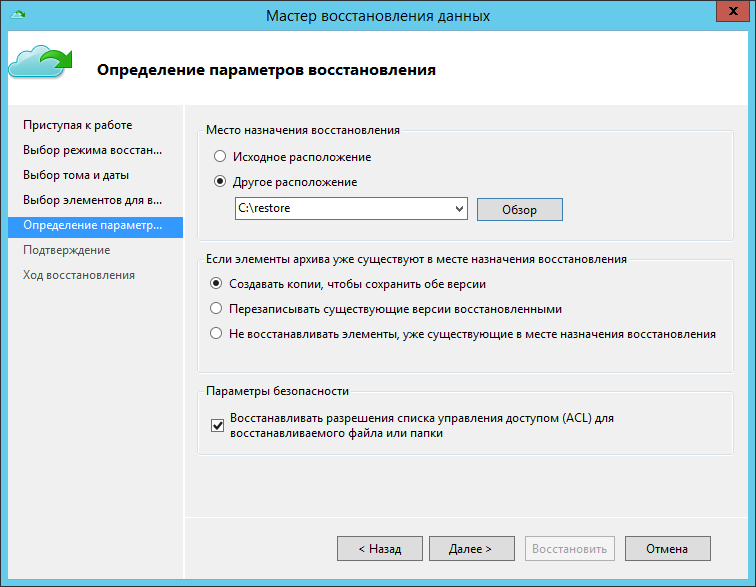
Files can be scanned by the user who encrypted them or using the efsRA recovery agent .
CryptoPro EFS software is designed to protect confidential information when it is stored on a PC. Also, the CryptoPro EFS software is intended for use with the CryptoPro CSP CIP version 3.0 (ZHTYA.00015-01 30 01) and CryptoPro CSP version 3.6 (ZHTYA.00050-01 30 01) in Microsoft Windows XP / 2003 / Vista / 2008 / W7 / 2008 R2.
USB tokens and smart cards JaCartaDesigned for strong authentication, electronic signature and secure storage of keys and digital certificates.
In general, the essence of implementing two-factor authentication in Microsoft Cloud is to increase trust in the Microsoft cloud provider and the general level of security by providing single sign-on and implementing enhanced two-factor authentication on ALL cloud services and local resources using external devices - smart cards (or USB tokens) .
Description of demo infrastructure
The EFS organization has three servers based on Windows Server 2012 R2:
- DC.EFS.LOCAL - Active Directory Domain Controller;
- RDS.EFS.LOCAL - Remote Desktop Server;
- CA.EFS.LOCAL - Future Certification Authority and Certificate Issuing Center.
Employees of the organization connect to RDS.EFS.LOCAL to access applications and store their working documents on it.
It is necessary to ensure data security by encrypting and backing up to Microsoft Azure geo-distributed cloud storage. Data is accessed using a private key, which is safely stored on a USB token or smart card.

Installing the necessary software
CryptoPro CSP Installation
CryptoPro PRO CSP in this example must be installed on:
- DC.EFS.LOCAL domain controller;
- desktop server RDS.EFS.LOCAL;
- CA.EFS.LOCAL Certificate Authority server;
- client machines PC.EFS.LOCAL.
During installation, select Custom and select the Kernel mode CSP component for installation .

Installing JaCarta Single Client
On all PCs and servers where you plan to use smart cards, install the JaCarta Single Client software .
Install with the default settings.
Installing CryptoPro EFS
On the users PC and Remote Desktop Server, install the CryptoPro EFS software (version no lower than 1.0.1318).
Install with the default settings.
Installation should only be done after installing CryptoPro CSP .
Preparing Accounts and Groups
In this example, 3 accounts and 2 groups are used. The following accounts will be required for demonstration.
Accounts:
- DCAdmin - enterprise administrator account;
- efsRA - account of the EFS recovery agent;
- K.Sobchak is an ordinary user account.
Groups:
- EFSUsers - users who will use EFS encryption;
- EFS Computers - computers on which EFS encryption will be enabled.
The group of EFSComputers must include computers that will use EFS encryption using the GOST algorithm. In the present example, it will be RDS.EFS.LOCAL .
Configure Certificate Authority
Installing a Certificate Authority Role
This example uses a simplified installation of a Certification Authority (hereinafter CA) using only the root CA.
On the CA.EFS.LOCAL server , add the CA role: Server Manager -> Management -> Add Roles and Features .
Using the Add Roles and Features Wizard, select the Active Directory Certificate Services role to install .
When choosing a role service, you must select a Certificate Authority .
Configure CA service
After the certificate service installation is complete, you must configure it.
From the Server Manager, open the service settings dialog.

- Enter the credentials of a user who is a member of the Enterprise Admins group .
- For the configuration service, select Certificate Authority .

- Specify the option to install the Certification Authority - CA Enterprises .
- Specify the type of CA - Root CA .
- Specify the type of private key - Create a new private key .
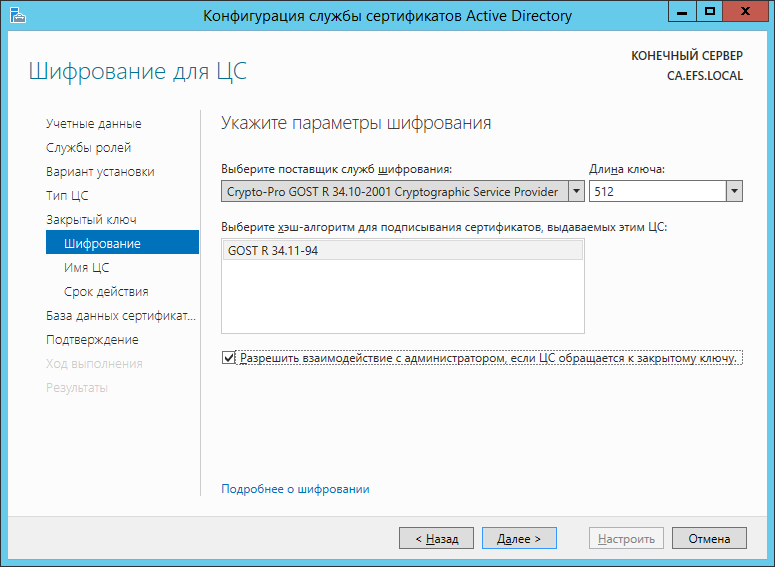
- Set the encryption parameters as shown.

- The CA name can be left at the default value.
- Set validity period - 5 years.
- The location of the databases can be left at the default value.
- Click the Configure button. Next, a request appears to select the location of the private key container (hereinafter referred to as SC).
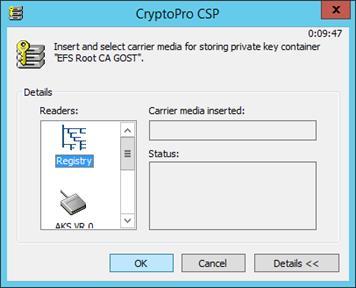
- Select Registry .

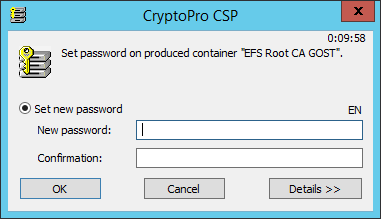
After entering an arbitrary sequence for generating a key, a dialog for entering a PIN code will be displayed. Set the PIN code for the container ZK.

- The initial configuration of the CA is now complete.
Export CA certificate
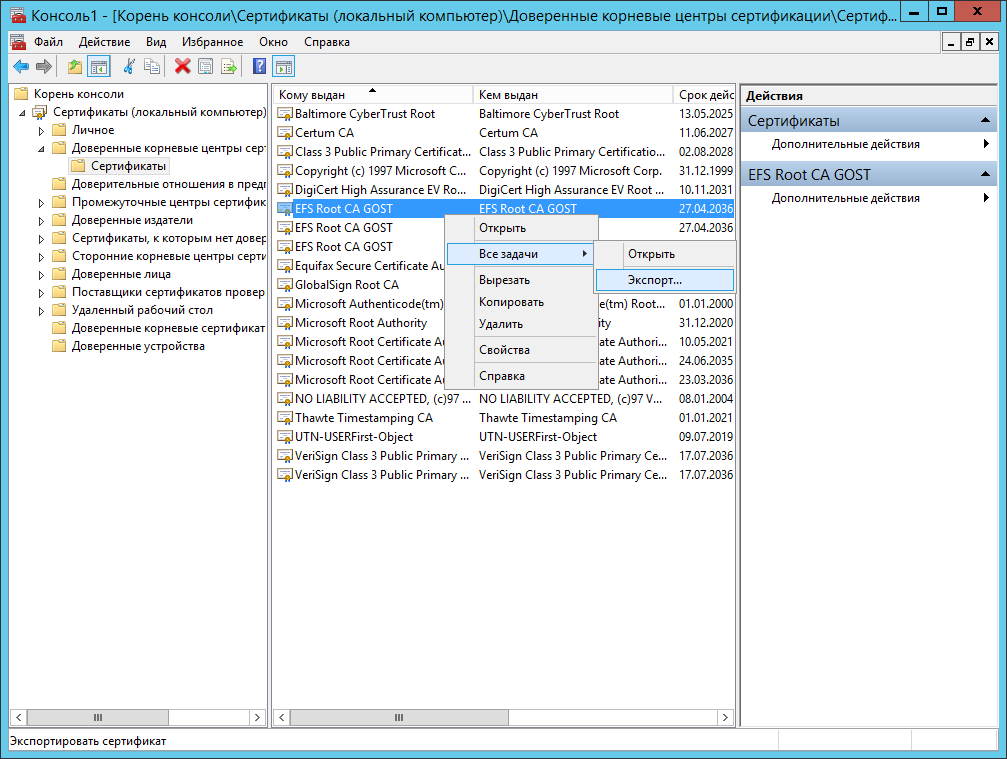
Export the CA certificate to a file that is accessible to the domain controller. To do this, use the Certificates snap-in (local computer) .

Specify a custom certificate name, for example efs_root_ca.cer .
Configuring Certificate Templates
- Open the Certificate Authority snap-in from Server Manager -> Tools .
- Next Certificate Templates → Action → Management .
- Copy the EFS Recovery Agent template , in the window that appears, rename the Template display name field .

- Check the box Publish certificate to Active Directory .
- On the Request Processing tab, uncheck the Allow exporting private key checkbox .
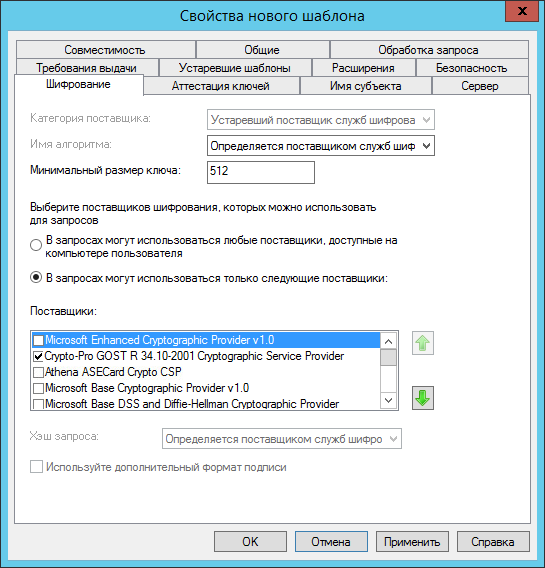
- On the Encryption tab, set the parameters as shown in the figure.

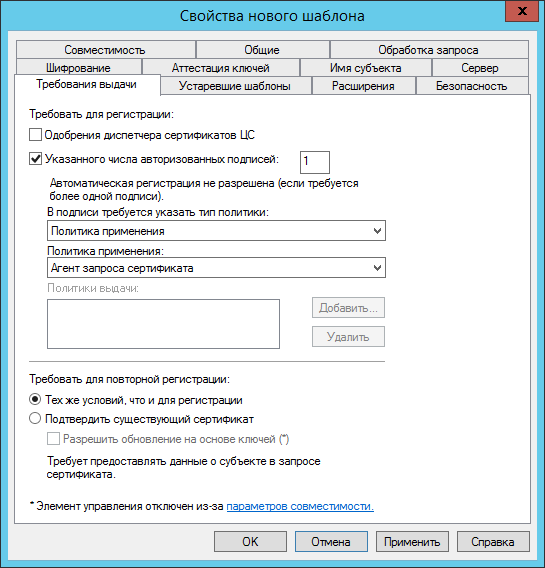
- On the Issue Requirements tab, set the following settings.

- On the Security tab , add a user who will issue keys to other users.
- Allow this user to Read, Write, and Submit .
- Similarly, the configuration of the EFS Basic Encryption, Smart Card Login, and Registration Agent templates is performed .
Publishing Templates
- In the list of certificate templates, remove the EFS Recovery Agent and Basic EFS Encryption templates.
- Instead, add the templates you just created: Certificate Templates -> Action → Create → Issued certificate template.
Key initialization and release
Key Initialization Procedure
You must initialize three keys for users: DCAdmin, efsRA, K.Sobchak .
Registration Agent Certificate Issue
In this example, the DCADmin account is used as the registration agent .
Log in as a DCAdmin user to CA.EFS.LOCAL and from the Certificates snap-in -> current user request a GOST certificate . Registration Agent .
Use a smart card as a container (for DCADmin ).
After the certificate of registration agent is issued, it becomes possible to issue certificates for other users on behalf of DCADmin .
EFS Recovery Agent Certificate Issue
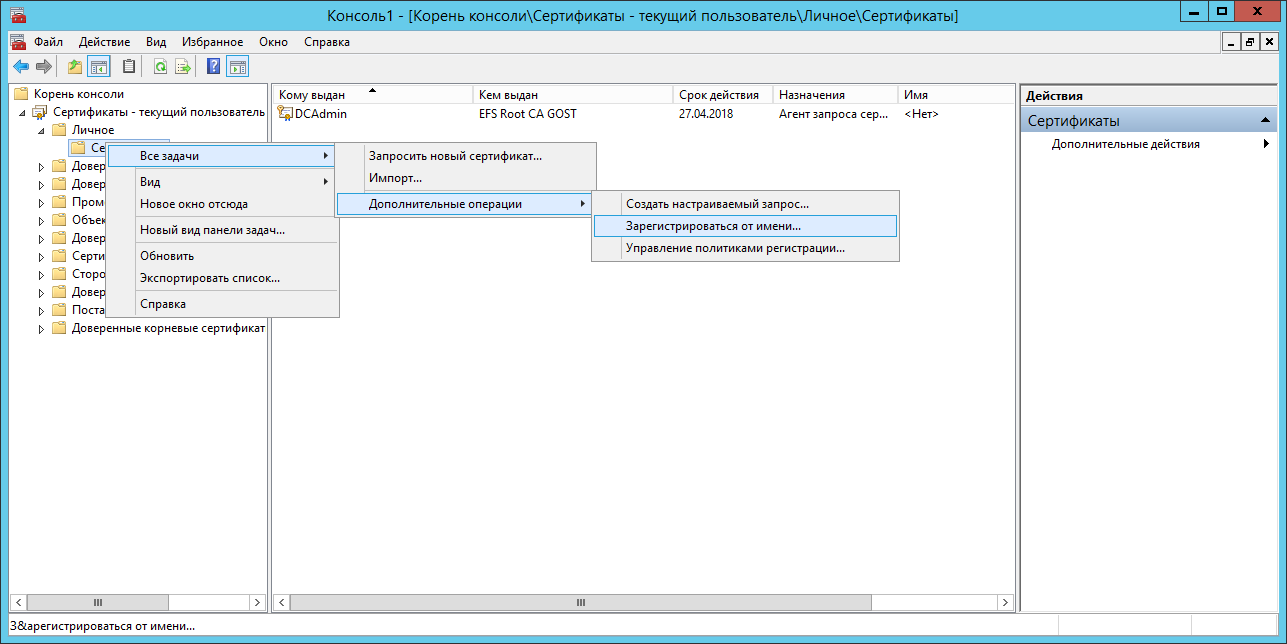
From the DCAdmin user , using the Certificates → snap-in snap- in, complete the GOST certificate request for the EFS Recovery Agent for the efsRA user .


Issue the certificate on a smart card designed for efsRA .
Export this certificate to a file.
Similarly, issue a GOST Certificate Login with a smart card .
User Certificate Issue
It is carried out similarly to the previous one, only it is necessary to use the GOST templates Basic encryption and GOST Login with a smart card .
Group Policy Setting
Configure Recovery Agent
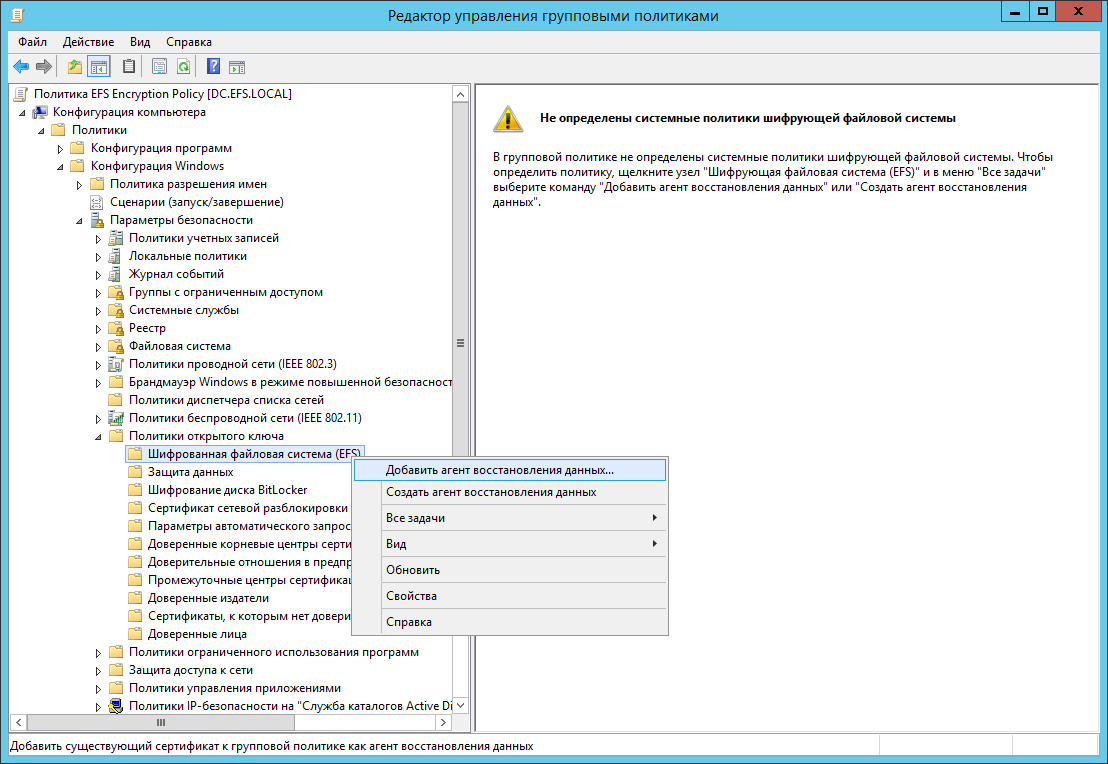
- Create the EFS Encryption Policy group policy that applies to the EFSComputers group .
- In the computer policy Windows Configuration → Security Settings → Public Key Policies → Encrypted EFS File System → Add Data Recovery Agent .

- Add certificate efsra.cer .
- In the properties of the Encrypted File System (EFS) on the General tab , select Allow Encryption of Files Using Encrypting File System (EFS).
And on the Certificates tab, uncheck Allow EFS to create self-signed certificates if the Certificate Authority is unavailable .
Adding a CA certificate to a trust store
You must add the CA certificate to the list of trusted Certificate Authorities.
To do this, create the Trusted Certificates policy in the Computer Configuration → Policies → Windows Settings → Security Settings → Public Key Policy → Trusted Root Certificate Authorities → Import section . Select the certificate efr_root_ca.cer .
Configure RDS Server
Issue a service, self-signed certificate using the CryptoPRO EFS Management Console utility .
My certificates → All tasks → Create a self-signed certificate.

Next, export the certificate from the Certificates snap -in, the current user in two formats: with export of the private key (.pfx) and without export of the private key (.cer).
Import the certificate with the private key .pfx into the Personal store of the computer, and the certificate without the private key .cer into the store Trusted persons of the computer.
Leave the PIN code blank when importing.
File encryption
Now you can check file encryption on RDS.EFS.LOCAL . To do this, connect using a smart card to the RDS server.
In the Documents directory, create a file and encrypt it by setting Other → Encrypt contents to protect data in the file properties .
Click the Details button . If everything went smoothly, the following window will be displayed.

Configure Azure Cloud Backup
Register Azure Storage
To start the backup, you need to register a new storage in Azure.
To do this, go to http://manage.windowszure.com . Next, log in with your Microsoft account to the Recovery Services menu item . Go to NEW → Recovery Services → Backup Vault → Quick Create .

Specify the name of the repository, for example, efs-gost . And select a storage region, for example, North Europe .
After creating the vault, download the credential file and the Azure Backup client using the provided links.

Install Azure Backup Agent
Install the downloaded Azure Backup Agent with the default settings. During the installation, if necessary, the missing components (.Net Framework, Powershell) will be installed.
When the installation is complete, click the Go to registration button .

The following window will appear, select the credential file downloaded earlier.

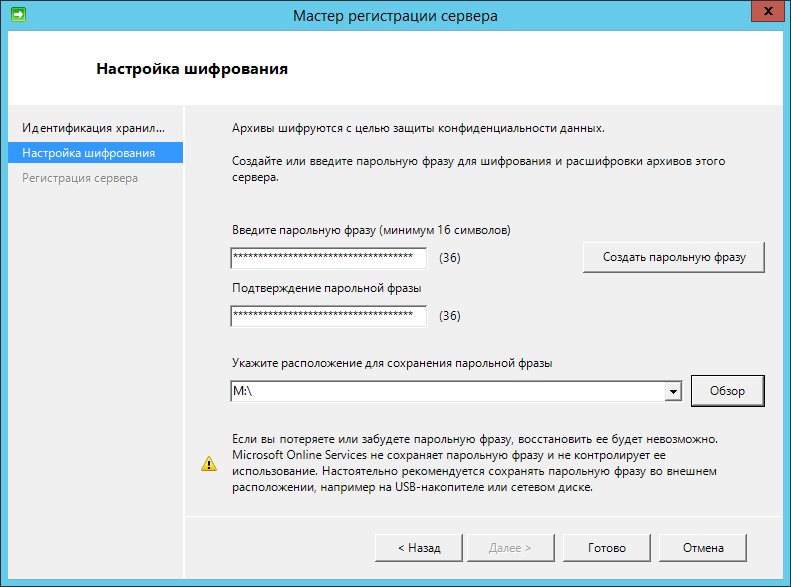
Create a passphrase and specify the path to its recovery file.

Setting up a reservation schedule
When registration is complete, the Microsoft Azure Backup Service window opens . Create a backup schedule in it.

In the selection of items for archiving, specify the folder with user profiles.

Leave the rest of the settings by default.
To check the settings, click Perform Instant Backup .
Data recovery
Restoring from a backup is similar.
Call the data recovery dialog by clicking the Restore data button .
Choose This server → Browse files → Select volume and image date and time .

Next, select the files to restore.

Select a location for the recovered files.

Files can be scanned by the user who encrypted them or using the efsRA recovery agent .
